As security practitioners, we all understand the importance of enabling Multi-Factor Authentication (MFA) for critical users. MFA is a vital security measure for safeguarding your OCI IAM domain. By implementing MFA, you establish a strong first line of defense against unauthorized access and significantly enhance the overall security posture of your cloud infrastructure. Enforcing MFA for all users, regularly reviewing and updating MFA settings, and educating users about best practices are essential steps in maintaining a secure OCI environment.
All new OCI tenancies and existing tenancies now come with MFA enabled by default for cloud administrators. OCI includes a “seeded” policy to enforce the use of MFA through a default Oracle Cloud Console policy. However, existing tenancies might still have administrators or users who have access to sensitive resources without MFA enabled.
This blog presents a programmatic approach that an administrator can use to list users who have MFA enabled and those who do not. Additionally, there is a Cloud Guard detector recipe that lists local OCI IAM users without MFA. Once enabled this rule alerts you when a user is authenticated with only a single authentication factor, such as a password.
Coming back to our apporach, here is a sample code that checks if the user has a local password or if they are federated and lists if the users have MFA Enrolled or not.
import oci
import json
from oci.identity import IdentityClient
from oci.exceptions import ServiceError
import logging
config = oci.config.from_file("~/ListDomainUsers/config")
identity_domains_client = oci.identity_domains.IdentityDomainsClient(config,"https://idcs-xxxxxx.identity.oraclecloud.com:443") # Pass the identity domain URL
users_list = [] # Initialize a list to hold user details
def list_MFAusers_in_domain():
try:
list_users_response = identity_domains_client.list_users ()
while True:
users_list.extend(list_users_response.data.resources)
if list_users_response.has_next_page:
list_users_response = identity_domains_client.list_users(page=list_users_response.next_page)
else:
break
print("Formatted MFA User List in this domain:") # Print formatted user details canUseConsolePassword
for user in users_list:
if user.urn_ietf_params_scim_schemas_oracle_idcs_extension_capabilities_user.can_use_console_password == True or user.urn_ietf_params_scim_schemas_oracle_idcs_extension_user_user.is_federated_user== False : # # check if the user has a ConsolePassword and add additional checks if required
if user.urn_ietf_params_scim_schemas_oracle_idcs_extension_mfa_user and hasattr(user.urn_ietf_params_scim_schemas_oracle_idcs_extension_mfa_user, 'mfa_status'):
print(f"{'|User Name':<20} {user.user_name:<40} "f" {'User ID':<20} {user.id} "f" {'MFA Status':<20} '{user.urn_ietf_params_scim_schemas_oracle_idcs_extension_mfa_user.mfa_status}'")
else:
print(f"{'|User Name':<20} {user.user_name:<40} "f" {'MFA Status':<20} 'MFA status information is not available.'")
except ServiceError as error:
print(f"Error getting users: {error}")
return [] # Return empty list on error
list_MFAusers_in_domain()
Note: We are providing a sample, as per your requirements edit and modify the code
Here is the script output:
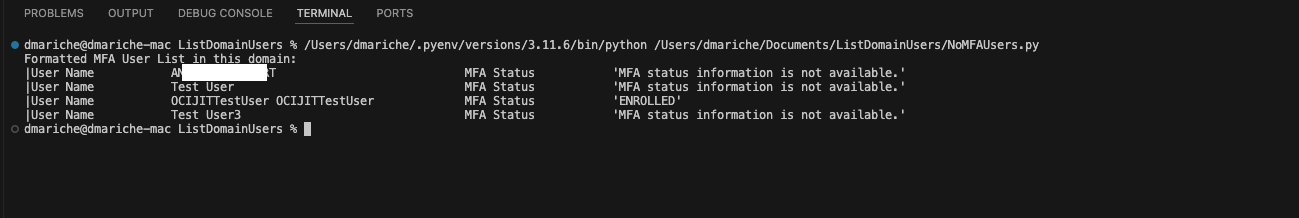
Regularly listing and reviewing MFA-enabled users is a critical aspect of managing and securing an OCI IAM domain. It helps in maintaining strong security practices, ensuring compliance, and managing user access effectively.
In conclusion, we should enable MFA for all users, especially those with elevated privileges or access to sensitive data, is crucial for enhancing security in OCI IAM, this tool would help us in understanding how all have MFA enabled and who doesn’t.
