The Kubernetes Control Plane and runtime are inherently complex and often misunderstood. They defy standardization especially when you consider all the plug-ins and deployment options that are available to implementers.
Having been in architecture and leadership roles with input regarding the security posture of Kubernetes deployments for various DevOps teams, I’ve seen designs and implementations that are all over the board. The good news is that there are some standards available to help drive Best Practices driven security posture such as the CIS Kubernetes Benchmarks for cloud provider implementations and stand-alone deployments. But even with this level of guidance for stand-alone deployments there are many knobs to turn and plenty of areas where configurations may deviate not to mention the level of constant oversight required to ensure consistent security posture.
The Kubernetes Attack Surface
A quick look at some of the moving parts of the Kubernetes framework shows the breadth of the attack surface of the platform.
- The kube-api server
- Kubelets on the nodes
- The master node itself
- The cluster and it’s respective compute nodes
- etcd database.
Kubernetes Misconfiguration
It is well reported that many stand-alone Kubernetes deployments both in cloud environments and on-premise have been and continue to be compromised by way of misconfiguration.
A stand-alone deployment would be a manual installation of the Kubernetes framework on physical or virtual machines managed entirely by the installer/implementer. By taking on the full responsibility of the managing the platform its security posture is the complete responsibility of the implementer.
- Etcd database protection and encryption.
- Kubernetes key management
- Container image scanning, signing and verification.
- Appropriately configuring Kubernetes Audit capabilities.
- Configuring Kubernetes to adhere to the principle of least privilege.
- Pod Security Policy configurations
- Secure Namespace configuration
- HA and DR configurations and administration.
With Kubernetes still being relatively new to many shops and with all the deployment options that are available it can introduce significant risk.
Figure 2 –
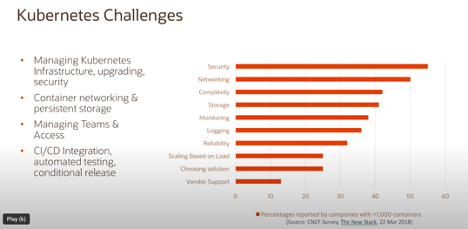
Aside from stand-alone deployments various cloud providers have PaaS oriented Managed Services offerings for Kubernetes deployments. In OCI there are a few offerings to consider including:
- OCI OKE (Oracle Container Engine for Kubernetes)
- OCI Container Instances (Oracle Serverless Kubernetes)
By outsourcing the administration of the Kubernetes framework the risk associated with deploying, running and managing the Kubernetes platform is now transferred to the cloud provider. In Oracle’s case that would be by way of OCI OKE and/or OCI Container Instances.
Let’s take a quick look at the two.
Figure 3 – Oracle Kubernetes Engine Shared Responsibility Model
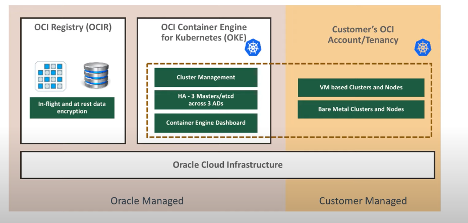
As you can see in the diagram above, Oracle takes on the management of the Kubernetes control plane in the OKE model. The customer is only responsible for managing the individual nodes within the cluster. Oracle also provides a managed and secure container registry which can be used to deploy container images across the managed environment. The OCI Container Registry supports native vulnerability scanning in OCI.
Figure 4 – OCI Container Instances Shared Responsibility Model
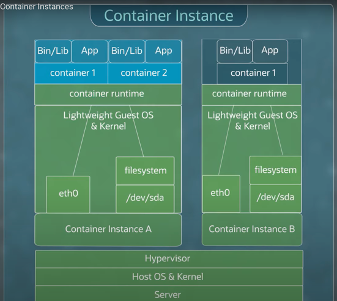
In the OCI Container Instances deployment model Oracle takes on administration of the Kubernetes Server Nodes as well making deploying containers a completely serverless and “Kubernetes-less” process thus offloading those security and administration responsibilities to the provider.
- Private clusters and node pools
- Network security at multiple levels –
- Security Groups
- Security Lists
- Network Policy
- VCN Native Pod Networking
- Persistent data encrypted at-rest and in-transit
- Container image vulnerability scanning, signing and verification
- CIS Benchmarks and STIG guidelines for cluster hardening
- Enable zero trust with OCI Service Mesh.
So, as you and your teams consider the use of Kubernetes you should consider managed Kubernetes services. By doing so your developers and security teams can focus more on business benefits as opposed to the “undifferentiated heavy lifting” and risk associated with managing the Kubernetes platform itself.
