- The CIS compliance checking script is not impacted. Users should continue using it to determine tenancy compliance with the CIS OCI Foundations Benchmark.
- Users looking for a deployment experience similar to CIS Landing Zone should now use OCI Core Landing Zone, where the same features are available. OCI Core Landing Zone evolves CIS Landing Zone and complies with CIS OCI Foundations Benchmark.
- Users looking for a deployment experience based on fully declarable and customizable templates should use the Operating Entities Landing Zone or the OCI Landing Zones Modules in the OCI Landing Zones GitHub organization.
CIS OCI Landing Zone quick start template provides OCI customers a quick, easy and secure way of designing their tenancy that complies with CIS OCI Foundations Benchmark v1.1 and follows OCI best practices for architecting a tenancy. The quick start template is provided in the form of sample terraform and Python code. Depending on what best fits your use-cases and development practices, it could be used as provided, extended and built upon or also as a guide to build something similar. If you are new to OCI Landing Zone, this blog post by Andre and this reference architecture are great resources to get started.
We continue to add new features to OCI Landing Zone. In this blog post, I would like to describe a recently added feature that allows for enabling Oracle Cloud Guard.
Oracle Cloud Guard is a native OCI service and is provided free of cost for OCI security posture monitoring. I highly recommend that customers enable and use Cloud Guard in their tenancies for maintaining a strong security posture.
In this blog post, I am not going to go into the details of what Cloud Guard is all about. However, at a very high level, Cloud Guard uses Detector recipes to monitor Targets, which are OCI Compartment hierarchies, for mis-configurations and risky actions by users and emits findings known as Problems in Cloud Guard terminology. Responder recipes could be used to address these Problems as shown in the figure below:
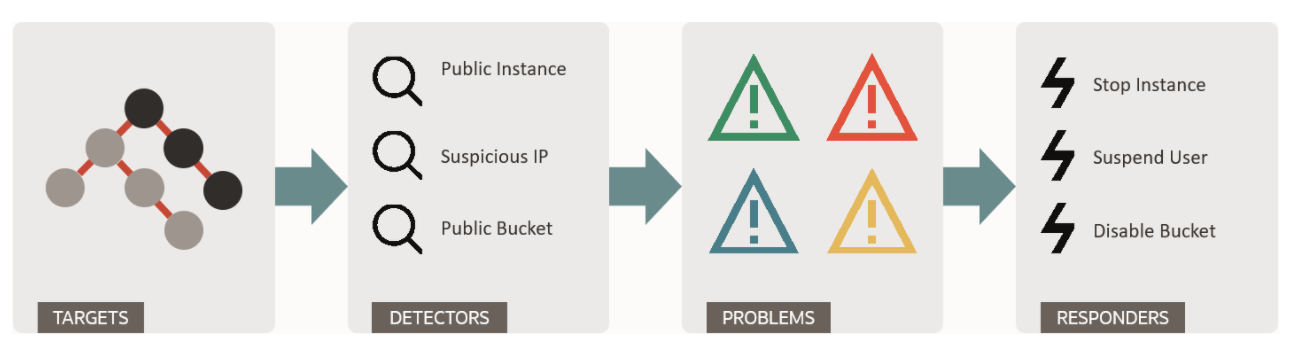
Customers can use Cloud Guard service to examine their OCI resources for security weakness related to configuration, and operators’ and users’ risky activities. Upon detection, Cloud Guard can suggest, assist, or take corrective actions, based on the configuration.
OCI Landing Zone enables Cloud Guard monitoring in a tenancy by default. Specifically, it looks for an existing Cloud Guard target for the root compartment. If it doesn’t find one, it provisions a Cloud Guard target for the root compartment, attaching the out-of-box Configuration and Activity detector recipes and Responder recipe. If for some reason you prefer having Cloud Guard disabled (again, this is not recommended), set the variable cloud_guard_configuration_status to “DISABLED” when running the Landing Zone terraform.
At any moment you can customize Cloud Guard configuration to meet specific security posture monitoring use-cases. You can also tune the detector and responder recipes to reduce the noise to signal ratio. Please refer to this blog post and Cloud Guard documentation for more information.
Customers who want to consolidate Cloud Guard Problems into their preferred SIEM and SOAR systems or take actions based on them can make use of the integration capabilities provided by the Event Service or Cloud Guard APIs and OCI SDKs for their favorite programming languages. OCI Service Connector Hub also provides rich integration capabilities to achieve various integration use-cases.