Introduction
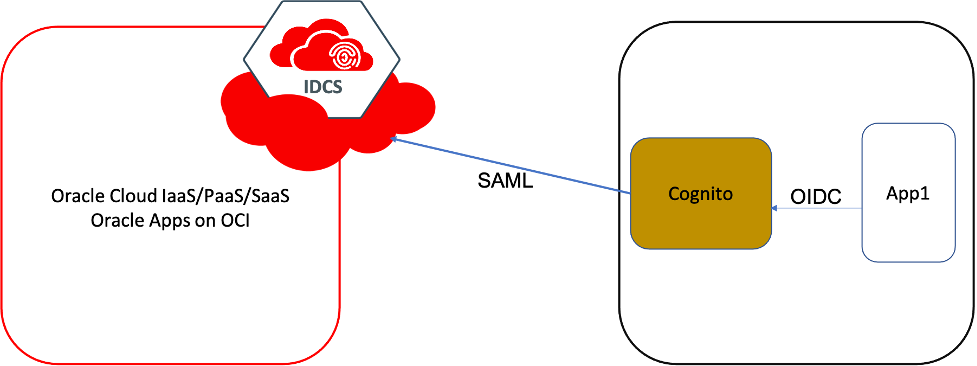
Enterprises that have heavily used Oracle Applications for years and are transitioning to the cloud will typically have Oracle IDCS as the Identity provider for their Oracle IaaS, PaaS, and SaaS or even the other apps that run on-premise or in OCI.
Adding more applications running on other clouds to this architecture and bringing those under the same SSO umbrella has become much easier because the cloud identity systems support SSO standards/protocols like SAML 2.0 and OIDC.
This post shows how to configure SSO between AWS Cognito and IDCS where IDCS acts as the Identity provider (IDP) for custom apps running on AWS protected with Cognito.
Architecture
Configure AWS Cognito
For testing purposes, the default settings will work just fine.
 I chose email as a required attribute.
I chose email as a required attribute.
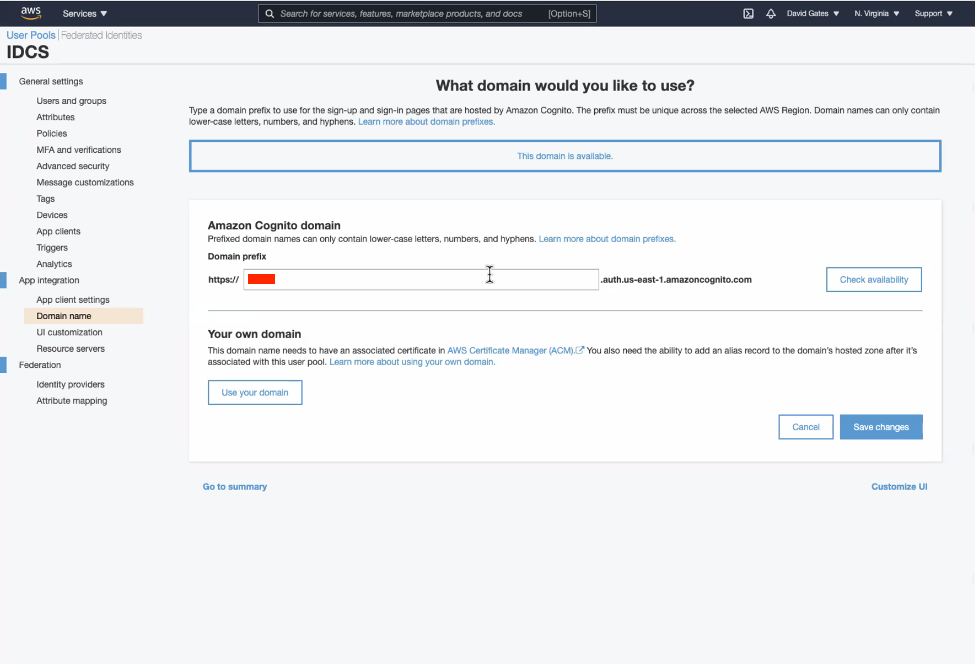
2. We will be using Amazon Cognito Hosted UI. So, create a domain for the new pool.
3. Navigate to the user pool -> Identity Providers.
IDCS supports SAML 2.0 and OIDC web SSO protocols.
In this post, I want to show how to add IDCS as a “SAML” identity provider.
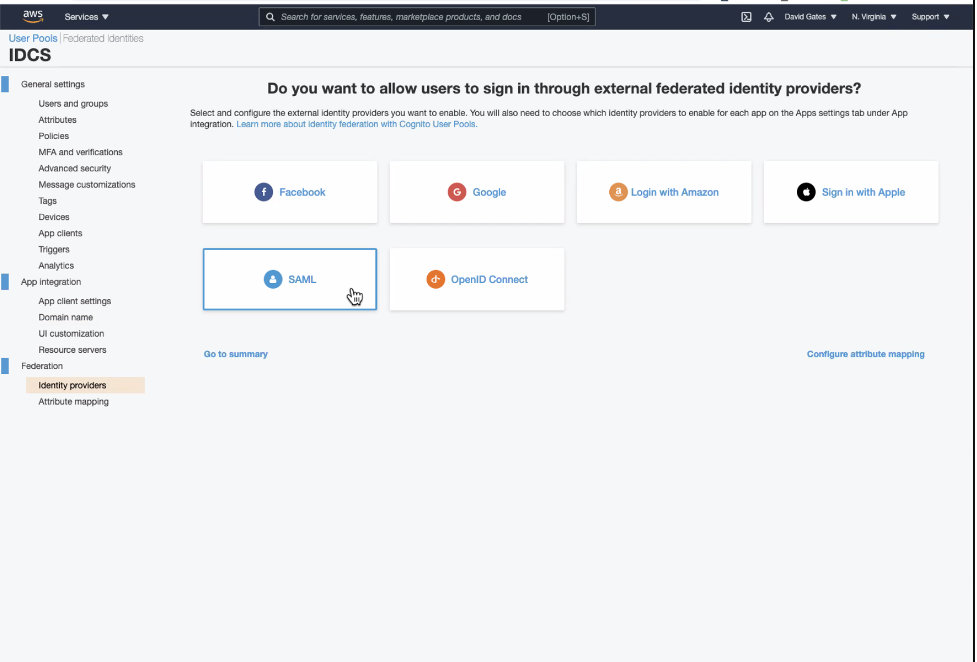
Choose SAML. Provide SAML Metadata URL in the format of – https://idcs-<your_instance>.identity.oraclecloud.com/fed/v1/metadata and hit Create Provider
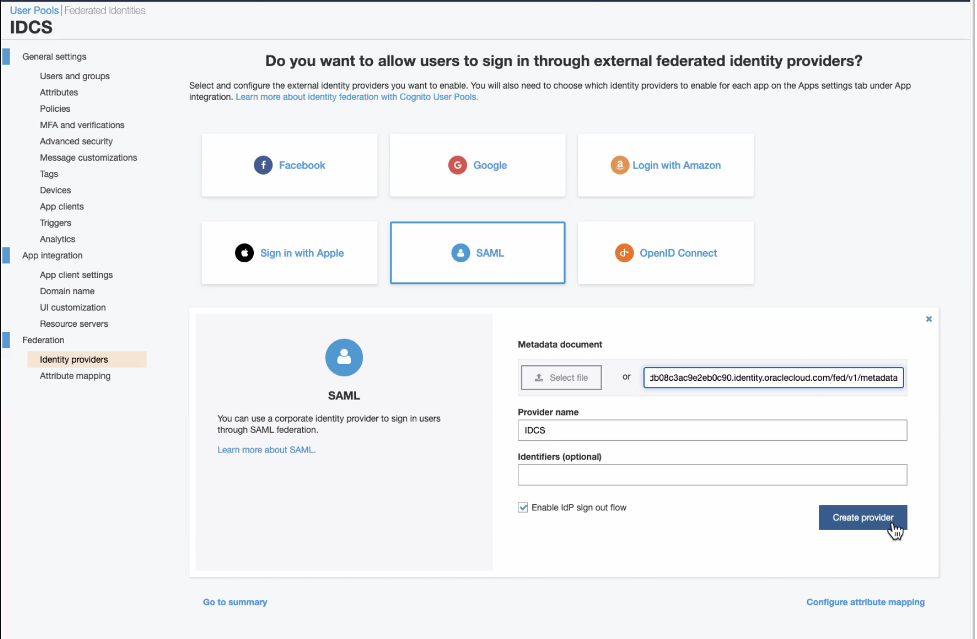
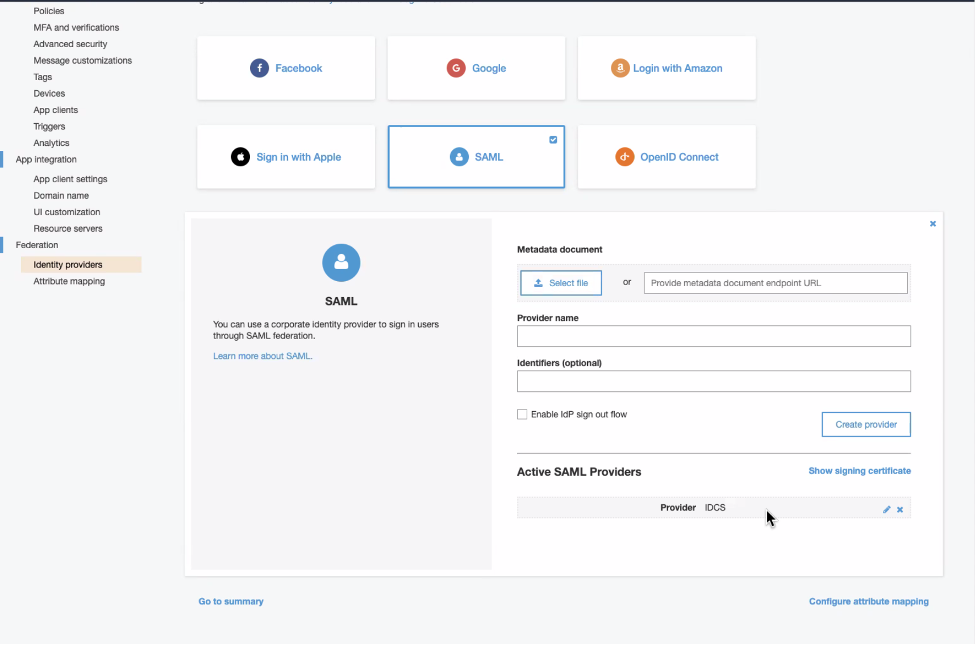
A new SAML provider will be created. Open the newly created provider and copy the service provider signing certificate. Wrap the certificate in PEM format and save it in a file before you could upload it to IDCS.
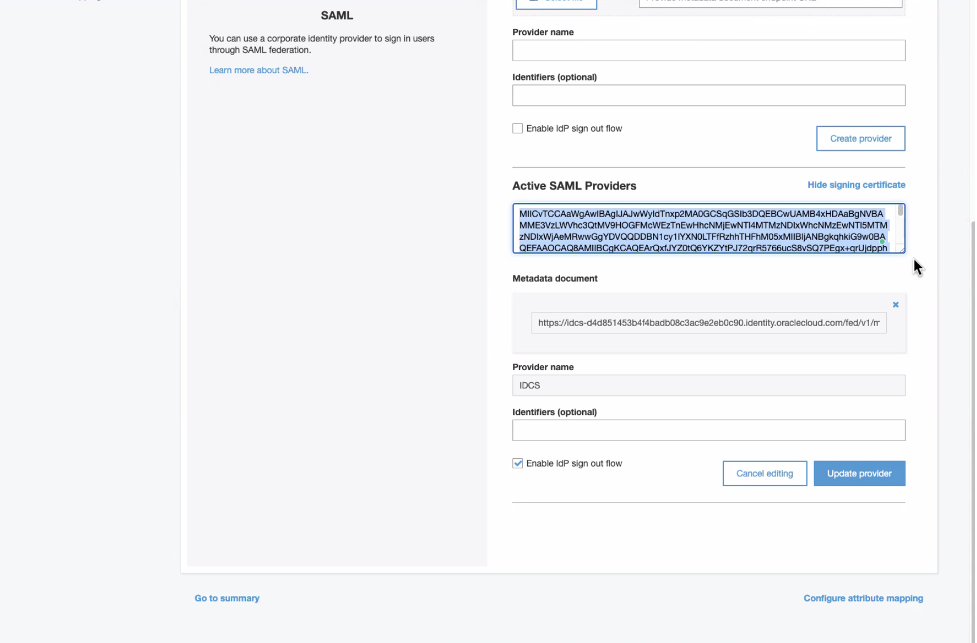
—–BEGIN CERTIFICATE—–
Paste certificate content
—–END CERTIFICATE—–
4. Create a test application that will use IDCS provider for authentication.
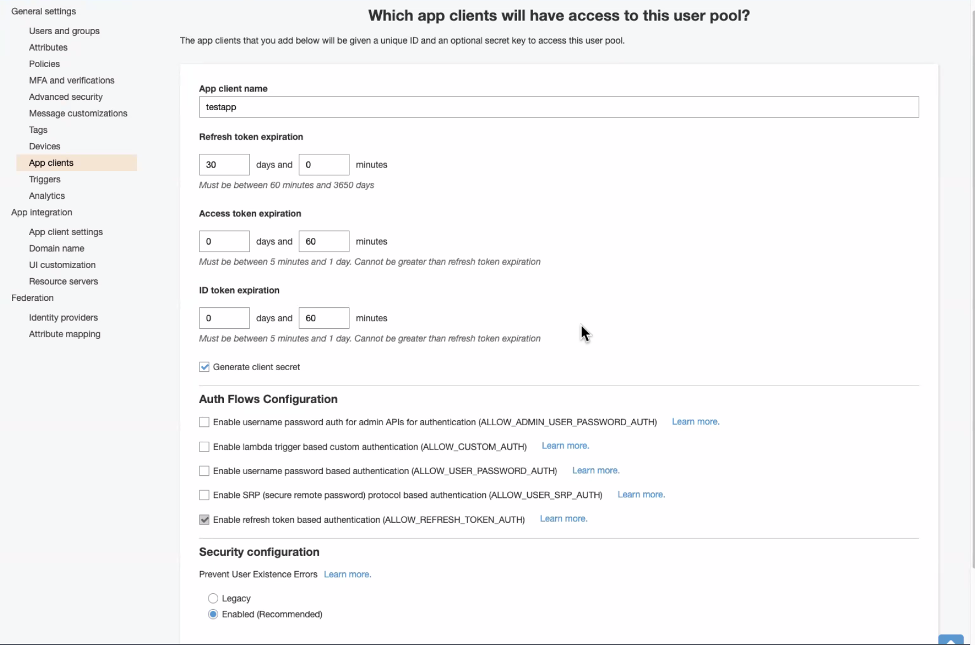
Choose the IDCS SAML identity provider created in the previous step.
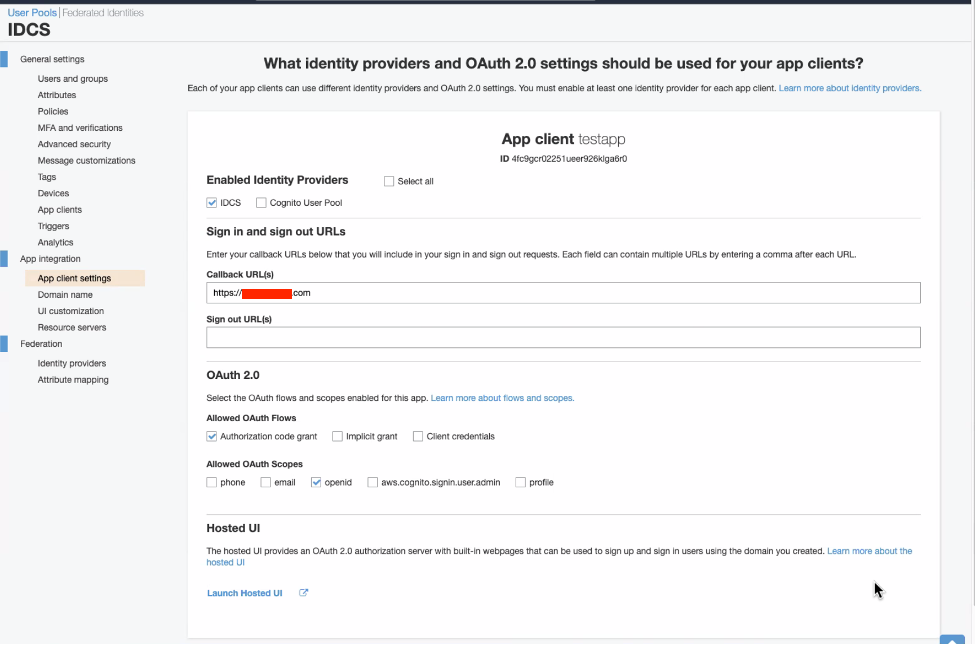
Callback URL is your test application URL
5. SAML Just In Time Configuration
A user that is not present in Cognito User Pool gets created on-demand during SSO slow.
Choose the SAML assertion attributes to map to the User Pool Attributes. Add as many user attributes as your end application needs.
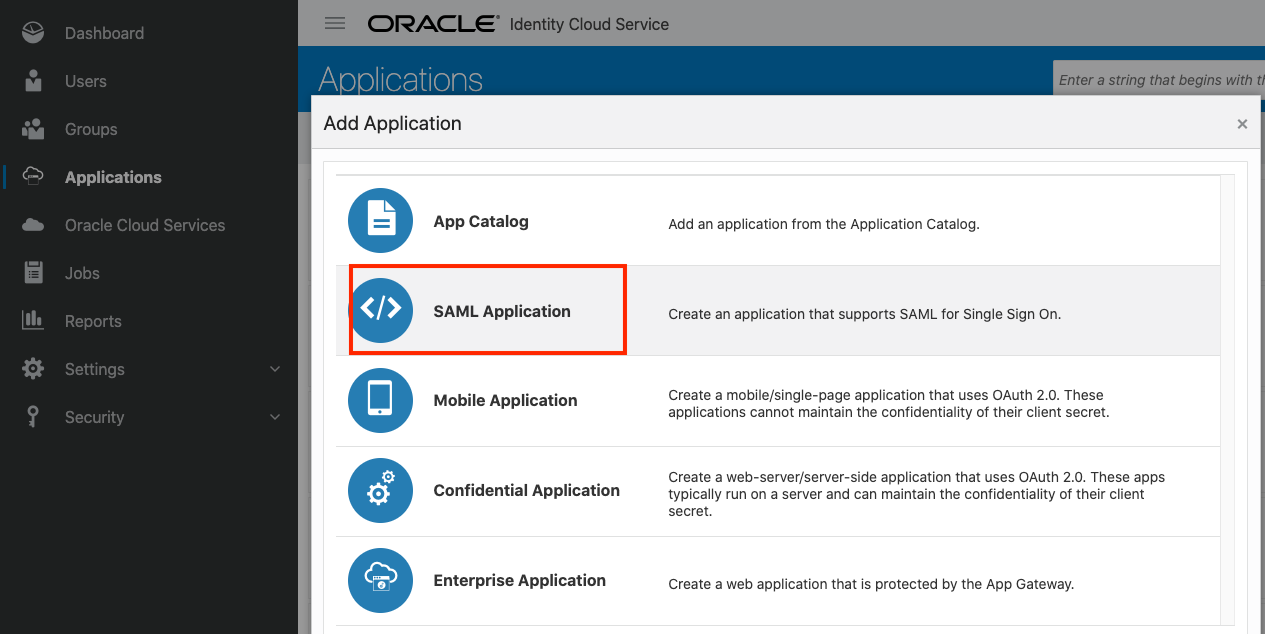
Add a SAML service provider application in IDCS
- Login to IDCS Admin console and navigate to Applications -> Add a new application
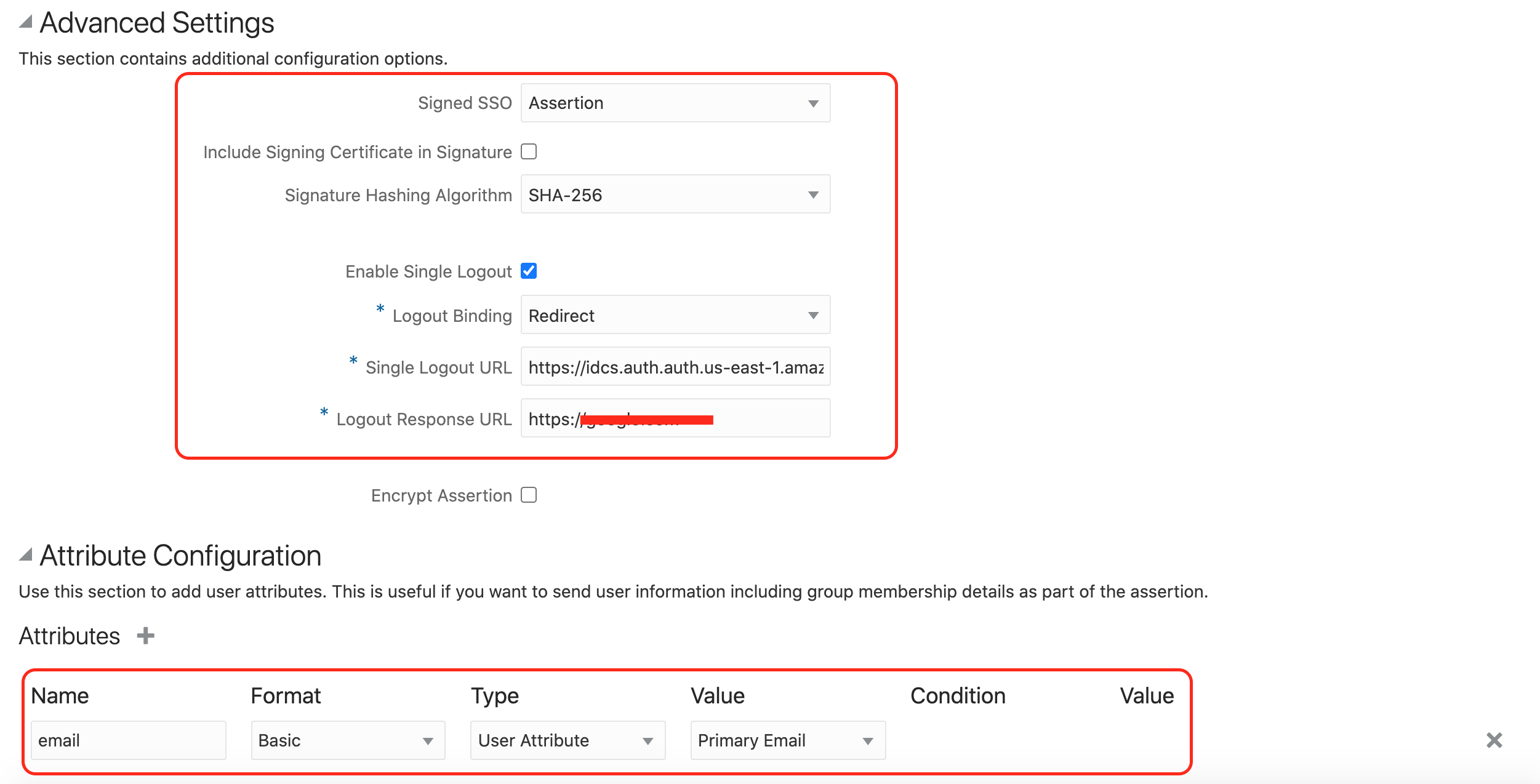
Provide Entity ID, Assertion consumer URL, and the signing certificate
Entity ID – urn:amazon:cognito:sp:<yourUserPoolID>
You can find your user pool ID on the General settings tab in the Amazon Cognito console.
Assertion Consumer URL Format – https://<yourDomainPrefix>.auth.<region>.amazoncognito.com/saml2/idpresponse
Signing certificate – Use the certificate downloaded and saved in Cognito Configuration Step -3
2. Assign a test user or a group to the application, save and activate the application.
Test your custom application
Login to the custom application via Cognito login URL. This will kick-start SAML flow with IDCS. upon successful authentication, If a user is not present in Cognito, a user gets created in the user pool of the application and then the user gets redirected to the end application.
The starting URL looks like this –
https://<your_domain_url> /login?redirect_uri=<URL encoded app url> &response_type=code&client_id=<your_app_client_id>
You could also launch this from Cognito console -> Manage User Pools -> your pool -> App Integrations -> Choose App client settings and under Hosted UI, click Launch Hosted UI
The login page of hosted UI opens in a new browser
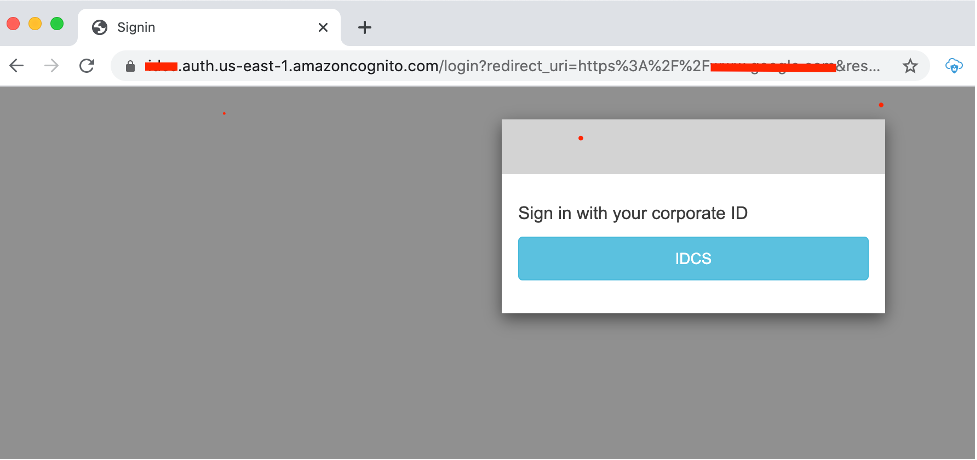 The user is taken to IDCS to login and upon successful login, redirected to the custom app with an authorization code.
The user is taken to IDCS to login and upon successful login, redirected to the custom app with an authorization code.
You can also see the user getting created in the user pool at the first successful login.
Summary
IDCS can be the enterprise identity provider and integrates with other cloud providers or service providers easily using Web SSO standards like SAML and OIDC. This post showed how one can easily integrate AWS Cognito as a service provider with IDCS acting as the Identity Provider.
