Oracle Identity Cloud Service (IDCS) serves as the identity plane of the Oracle Cloud. Oracle PaaS services such as Analytics Cloud are tightly integrated with IDCS. IDCS can also serve as the Identity and Access Management (IAM) solution for an enterprise’s on-premise as well cloud services including Oracle SaaS products. However, IDCS does not preclude using an enterprise’s existing identity solutions such as Azure AD. In such scenarios, IDCS can federate with other IDPs using standard federation protocols such SAML 2.0 and OIDC/OAuth 2.0.
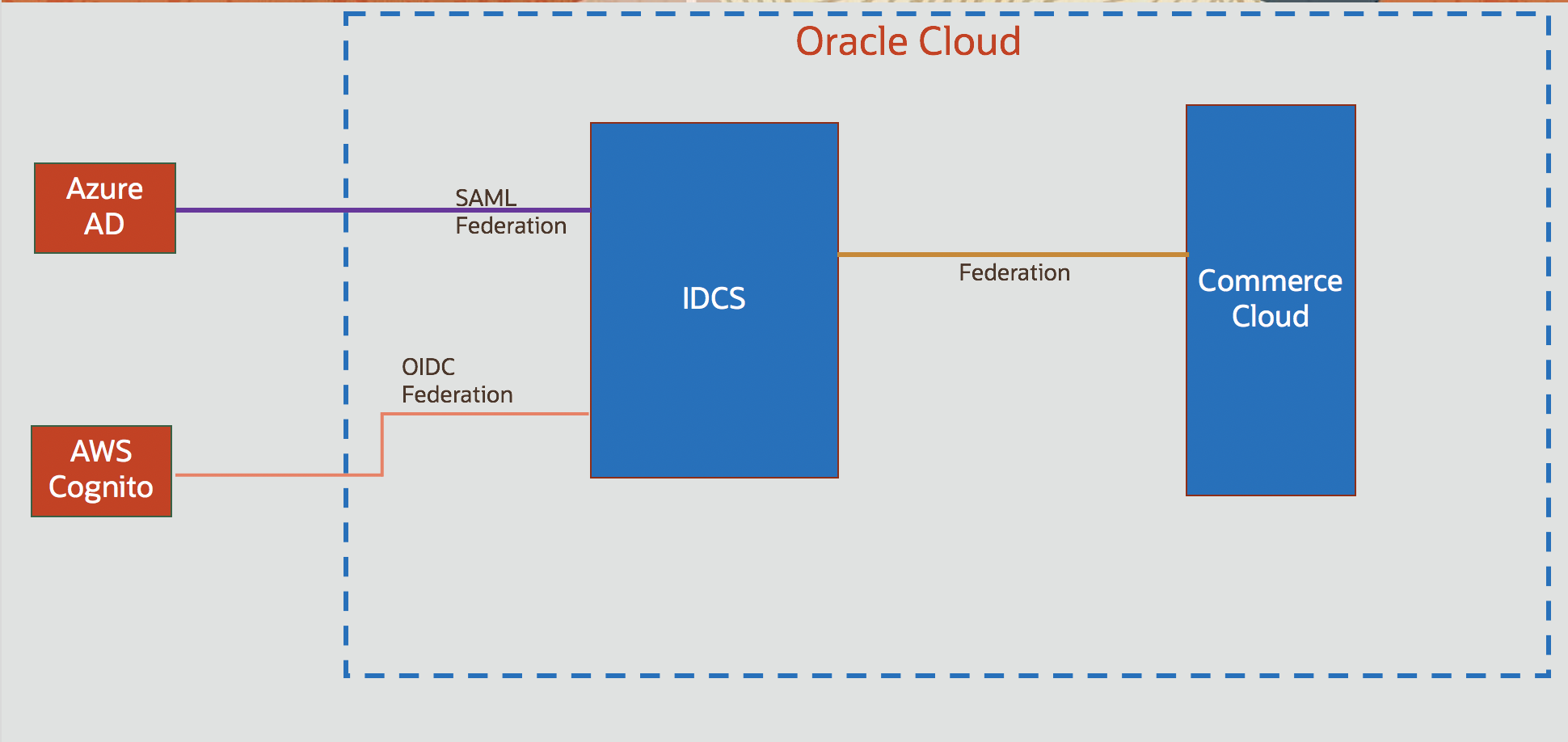
In this blog post, we will look into the federation partnership between IDCS and AWS Cognito.
Cognito Configuration
Cognito configuration starts with creating a “User Pool“, which is essentially a user directory. Use the documentation to create a user pool. As part of creating a user pool, user attributes need to be defined.
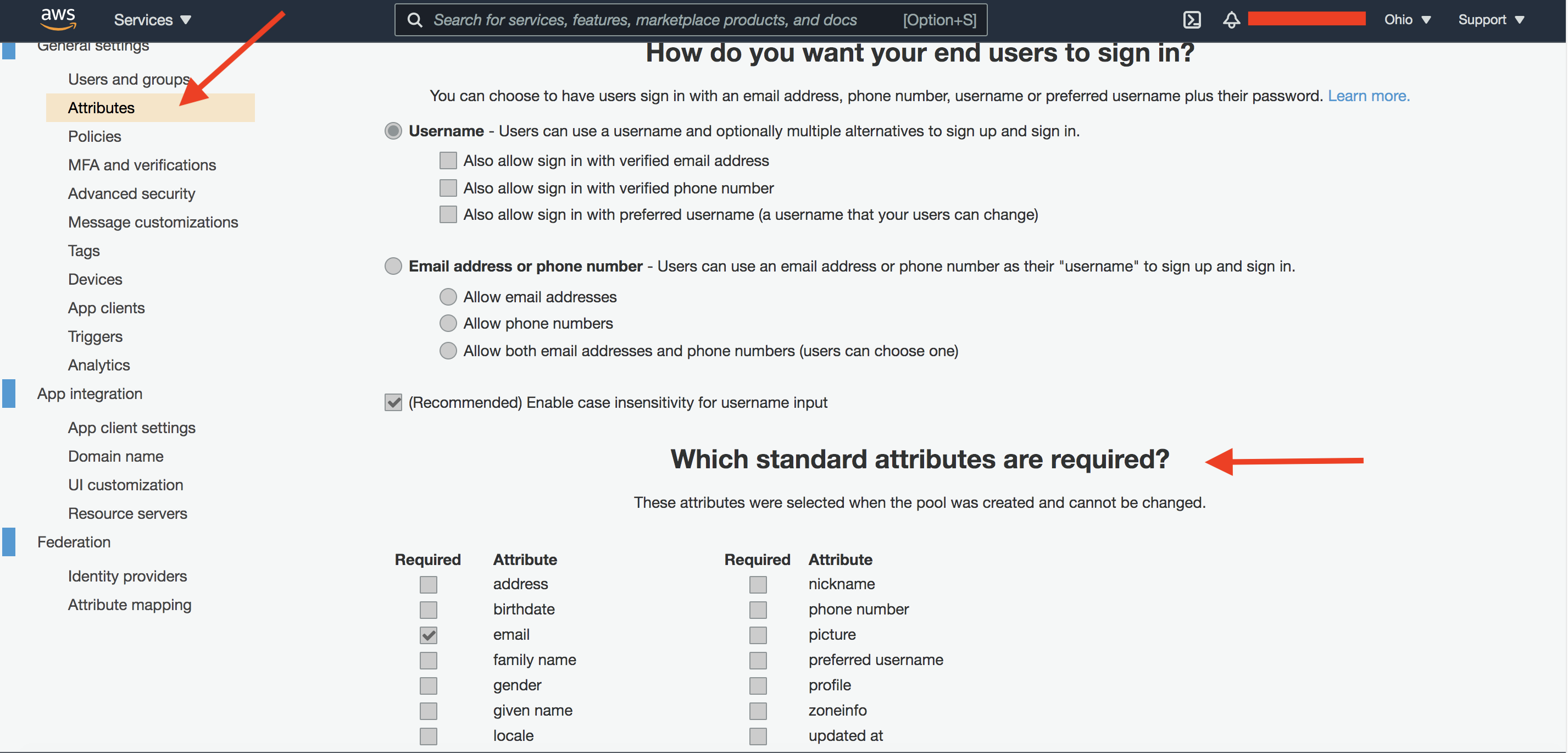
Fig 1
Cognito, as an Identity Provider (IDP) supports only OpenID Connect (OIDC) for federation. The user attributes list above is a subset of the OIDC standard claims. The selected attributes will be returned as part of the OIDC User Info response. In the above figure, only email is selected. Hence the User Info response will include only one standard claim, i.e., email.
Fig 2
The next important configuration setting is defining an “App Client” as shown below. This is an OAuth 2.0 application and represents the (OIDC) Relying Party which in our case is IDCS.
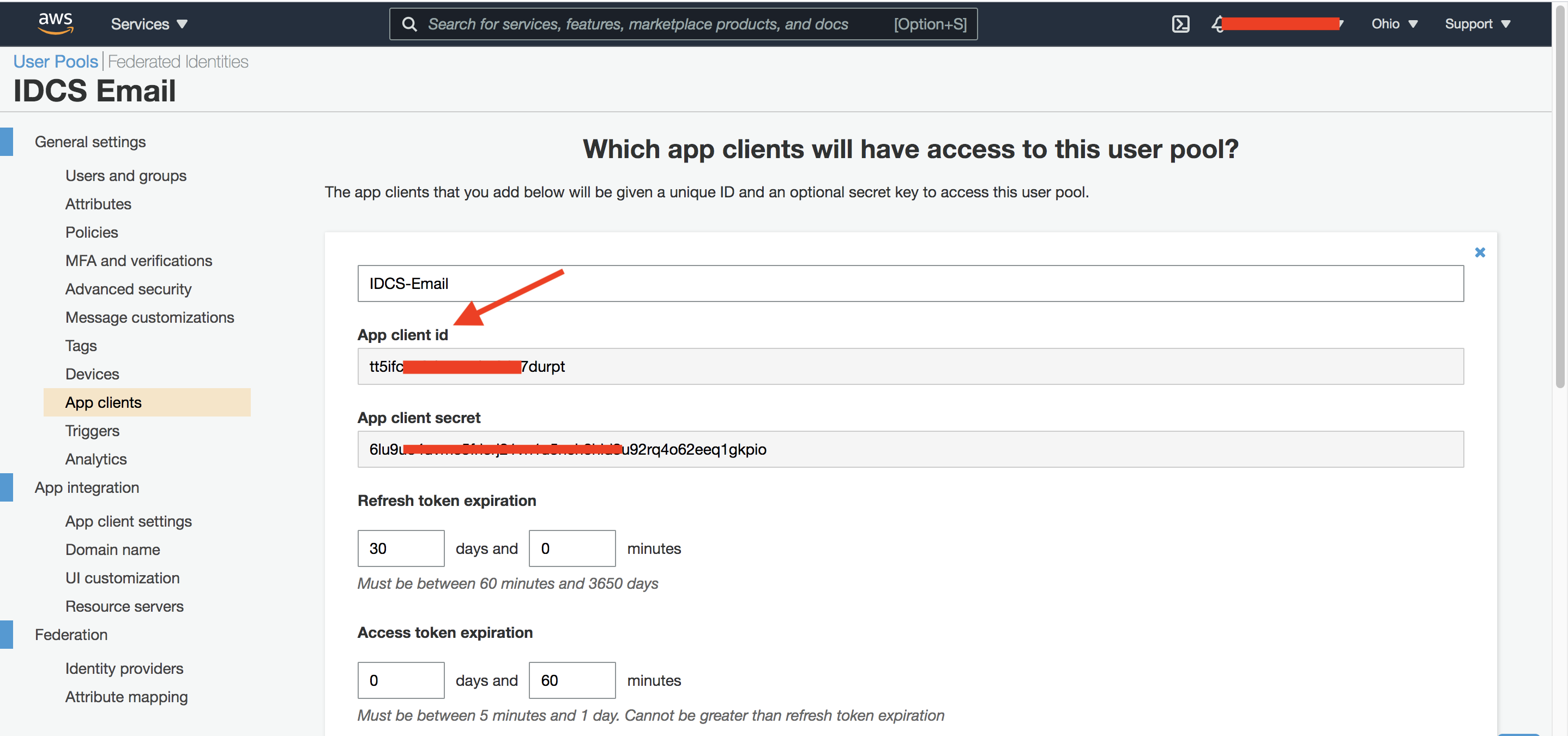
Fig 3
The App client id and App client secret above will be used in the IDCS setup later. Next, configure the OAuth 2.0 settings for the above application.
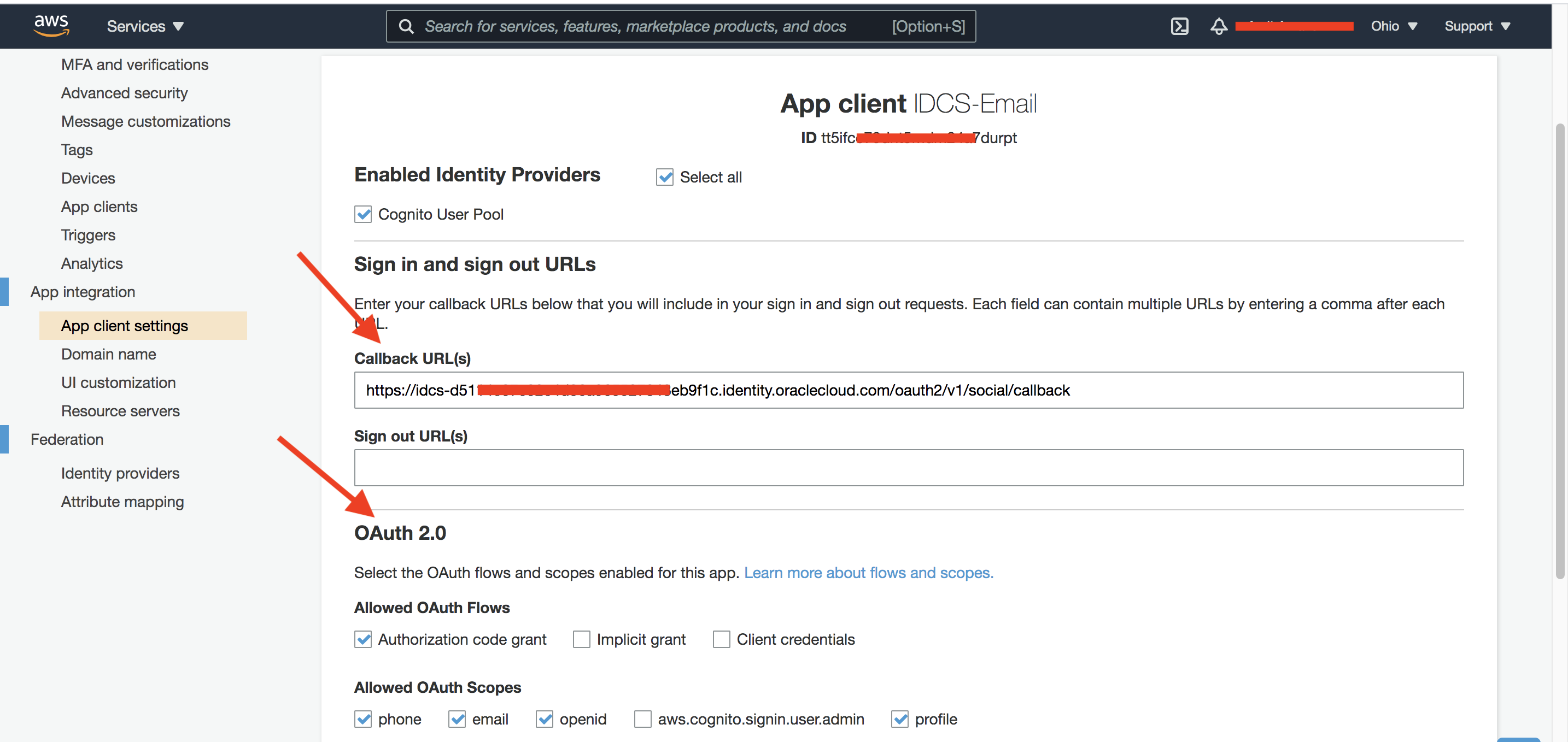
Fig 4
The Callback URL is from IDCS. It has the format of:
https://<IDCS tenant base URL>/oauth2/v1/social/callback
Finally create a user in Cognito who will use the federated flow.
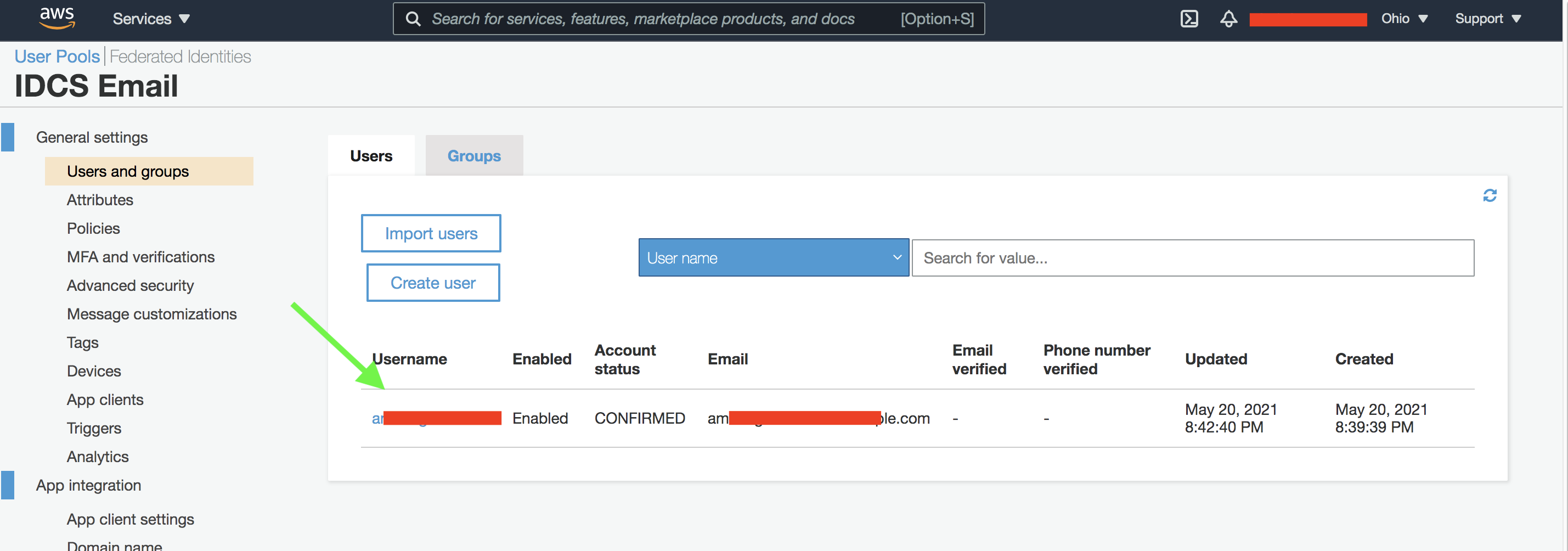
Fig 5
After creating the user pool, note down the Pool Id as shown below.
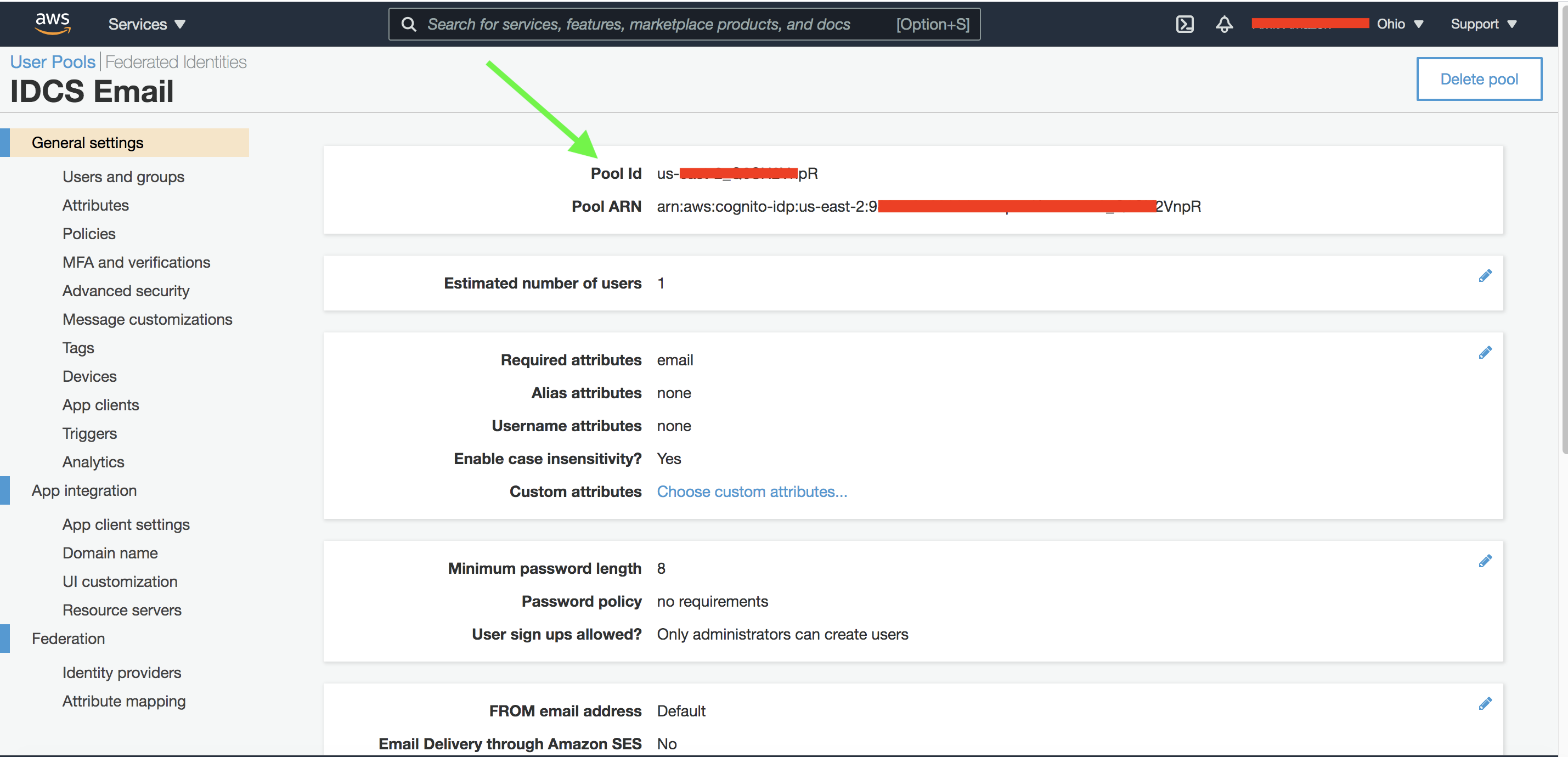
Fig 6
The Pool Id will be used to construct the Cognito OIDC Discovery URL, which returns all the OAuth 2.0 endpoints. IDCS will require it as explained below.
IDCS Configuration
In IDCS, create an IDP of type “Social”. Social IDPs typically reflect social platforms such as Google, Facebook, etc. These social providers use OIDC for federation. AWS Cognito, although not a social platform, uses OIDC for federation while acting as the IDP. IDCS includes templates for popular social providers such as Google, Facebook, etc. It also includes a generic OIDC template which can be used to define an OIDC Provider such as Cognito.
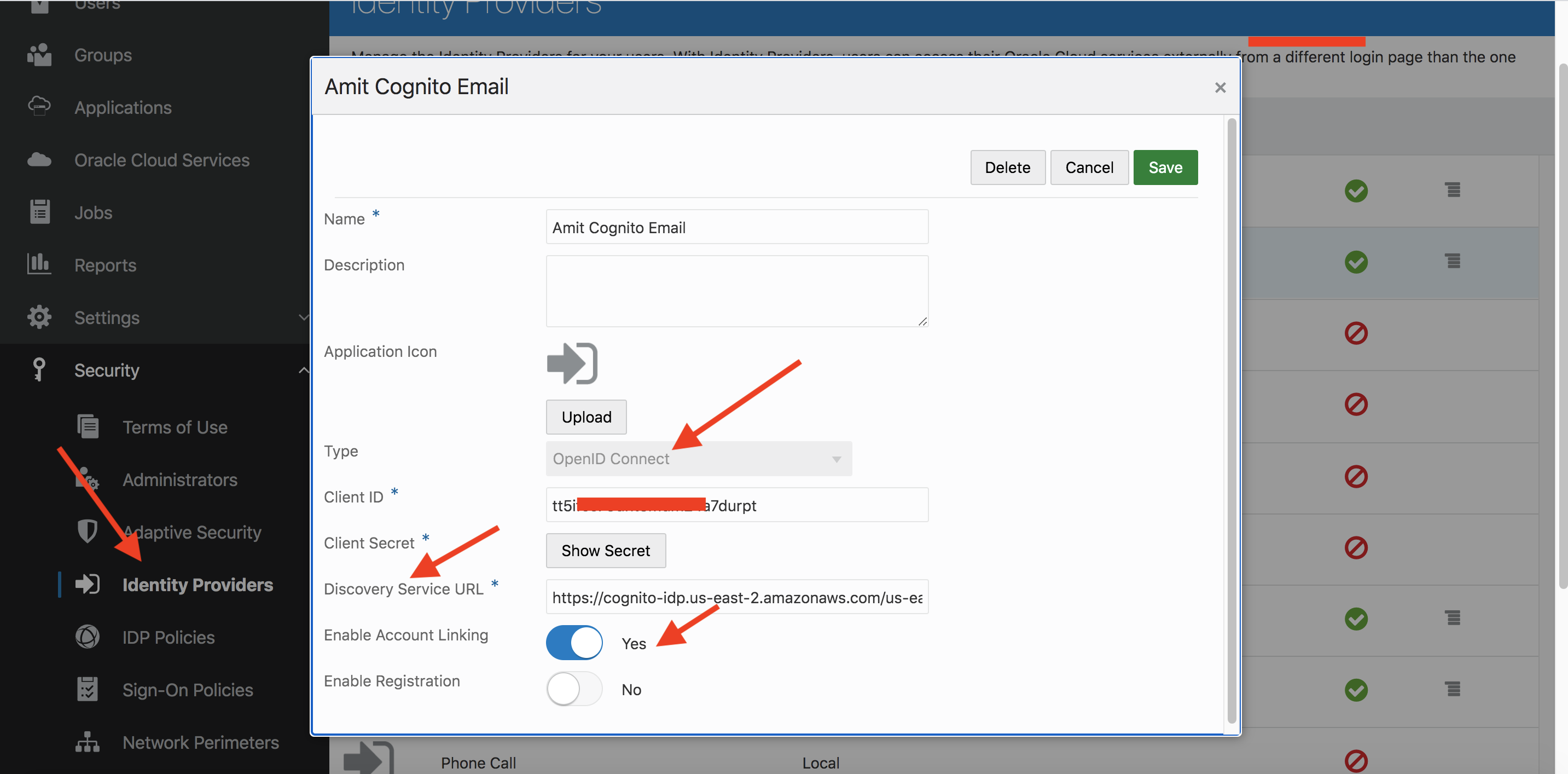
Fig 7
The name of the IDP is “Amit Cognito Email”. The Client ID and Client Secret are the App client id and secret from Cognito (Fig 3). The Cognito Discovery URL is constructed as follows:
https://cognito-idp.{REGION_ID}.amazonaws.com/{POOL_ID}
where REGION_ID is the AWS region (e.g. us-east-2) and POOL_ID is the Cognito user pool id (Fig 6).
IDCS fetches Cognito’s configuration using the Discovery URL.
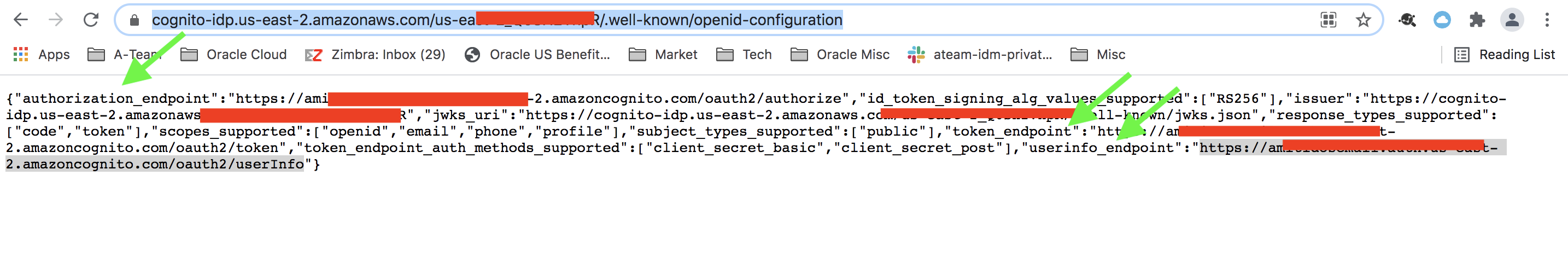
Fig 8
The authorization, token and the user info endpoints are included in the response as shown in the figure above. IDCS uses these endpoints for the OIDC flows.
Enable Account Linking and activate the IDP, including it in an IDP Policy (Default here) to make it appear on the IDCS sign-in UI.
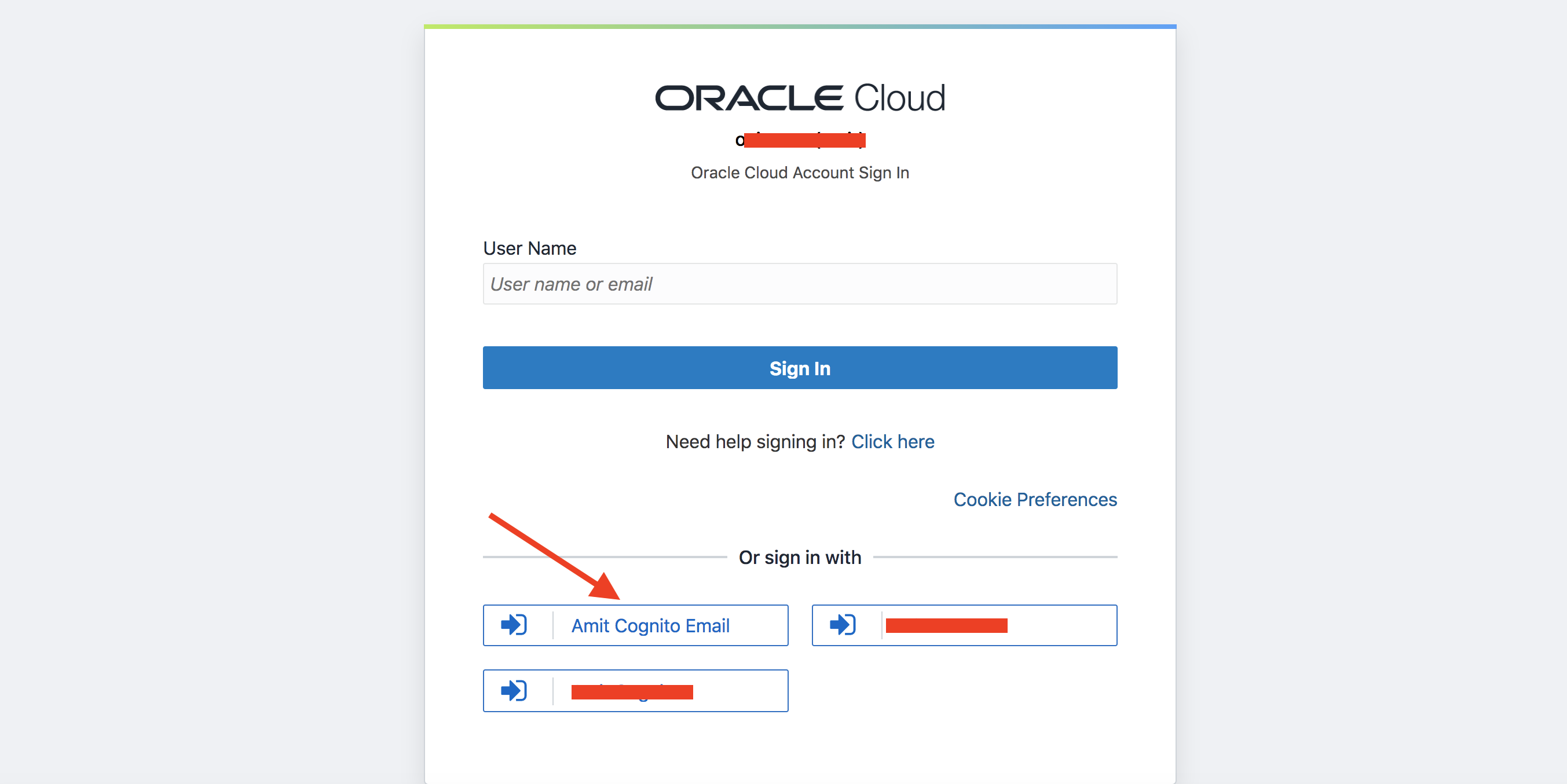
Fig 9
Create a user in IDCS with the username as the email id of the Cognito user (Fig 5).
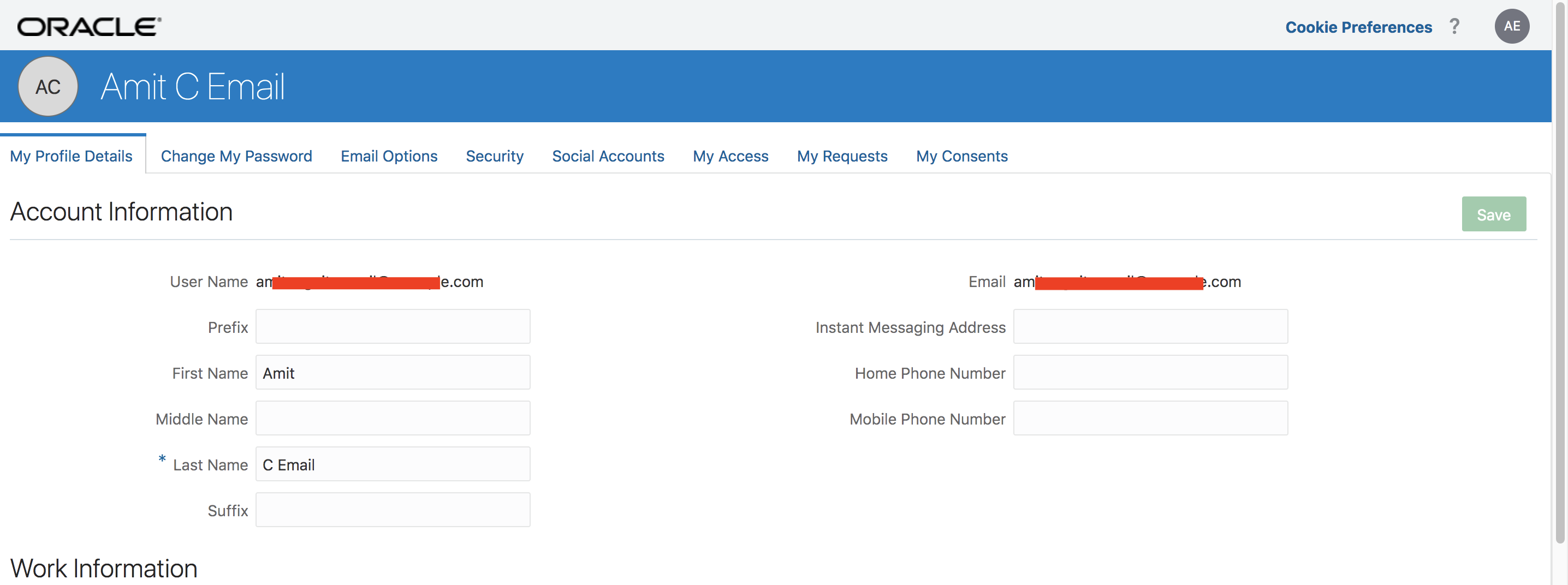
Fig 10
Selecting Amit Cognito Email as the IDP in the IDCS Sign-in page (Fig 9) will redirect you to Cognito. IDCS starts an OAuth 2.0 authorization code flow and the Cognito login UI will get displayed.
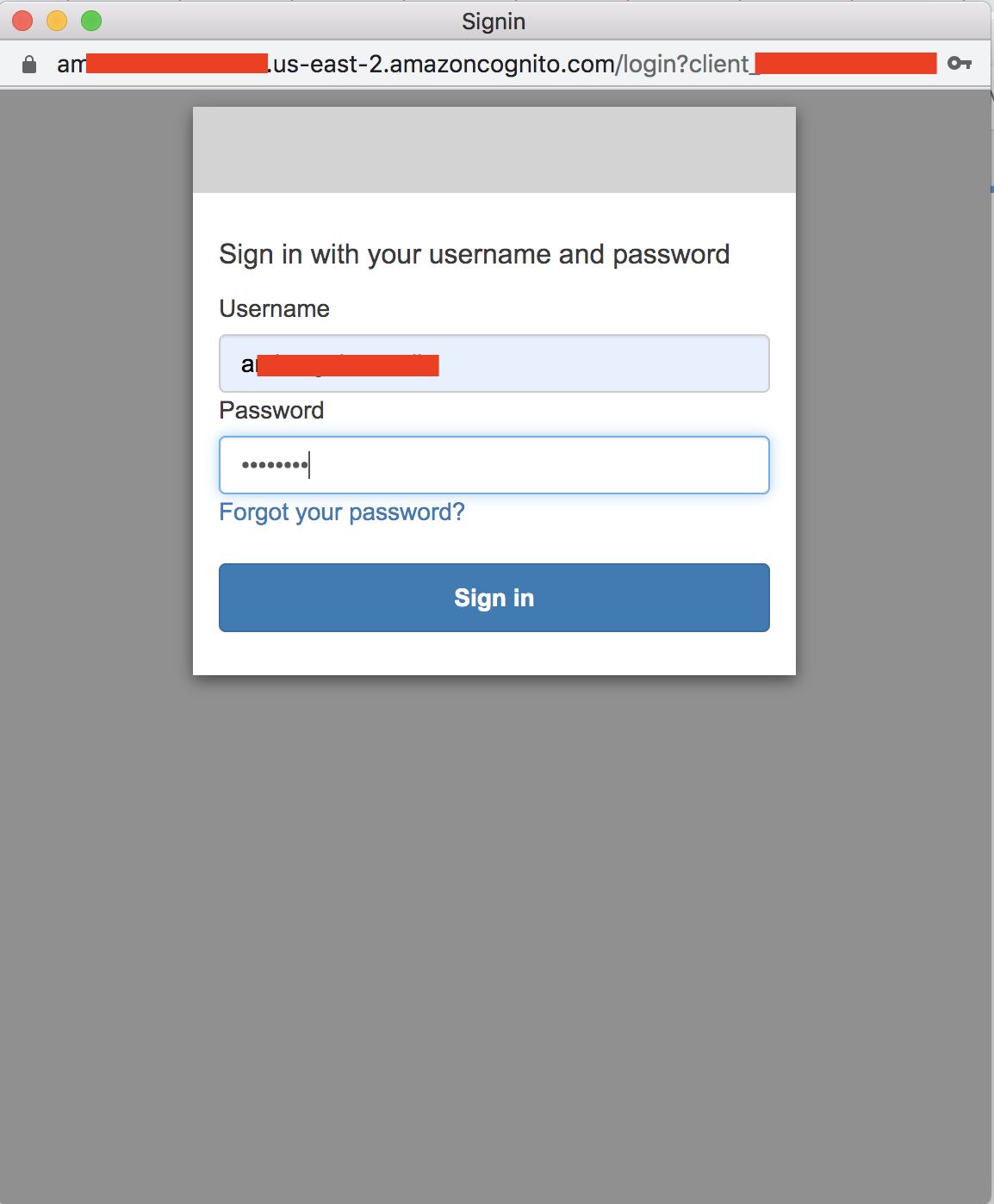
Fig 11
Provide the user name and password of the user created in the Cognito user pool (Fig 5). After successful authentication, Cognito will redirect the user back to IDCS using the Callback URL of the Cognito App Client (Fig 4). IDCS completes the OIDC flow and logs in the user.
Fig 12
Choose the user’s Social Accounts and it will show that that Cognito IDP account has been linked to the IDCS user.
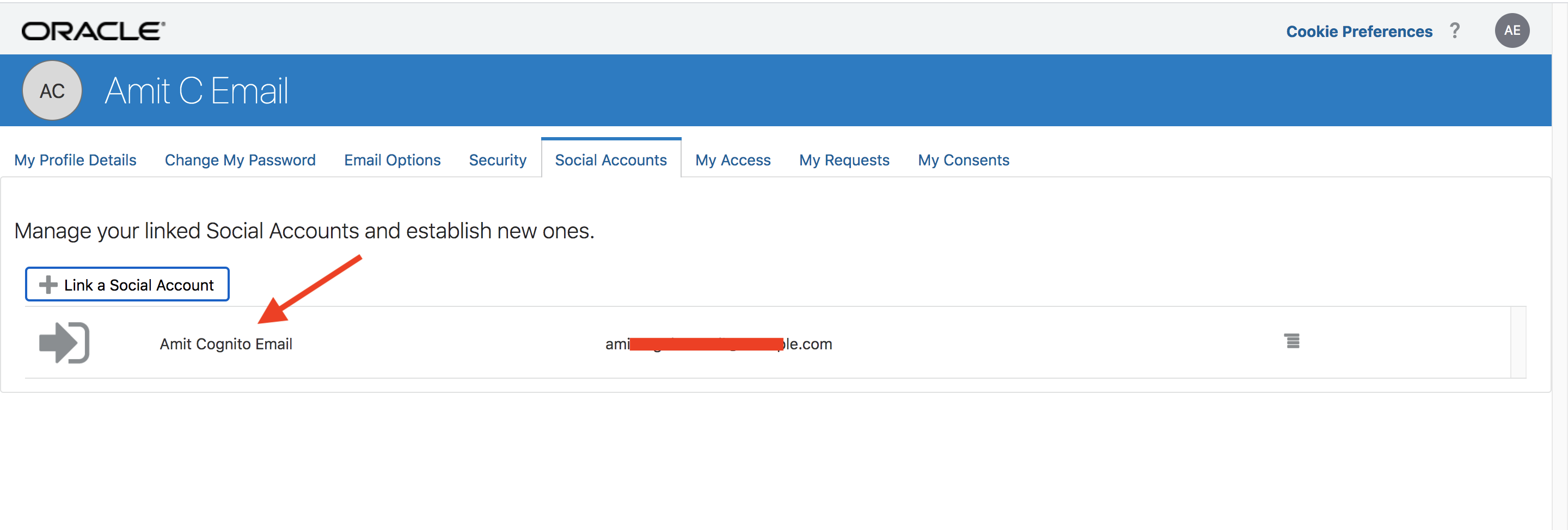
Fig 13
Summary
IDCS is a versatile Identity as a Service solution. It not only provides identity domain services to various Oracle cloud services but also can federate with existing corporate identity services. In the blog post, we looked into the federation between IDCS and AWS Cognito using OIDC protocol.