Overview
The purpose of this document is to describe the requirements and general information for building a Hub & Spoke architecture using FortiGate-VM on Oracle Cloud Infrastructure (OCI). Basic OCI and FortiGate-VMexperience are recommended.
This configuration was validated using FortiGate-VM version 6.2.3.
For more details on how to use the FortiGate-VM product, please visit Fortinet official website – https://www.fortinet.com.
Caveats and Limitations
FortiGate-VM on OCI Marketplace
We recommend using the latest FortiGate-VM version with support for SR-IOV.
The license model for FortiGate-VM on OCI changed with version 6.0.2. The number of vCPUs indicated by the license does not restrict the FortiGate-VM from working on a compute shapes with a greater number of VCPUs. The rest of the VCPUs are not used.
https://docs2.fortinet.com/vm/oci/FortiGate-VM/6.0/about-FortiGate-VM-for-oci/6.0.0/43335/models
This new license model works only on version 6. An active FortiGate-VM license can work on both version 5 and 6.
A trial or permanent license needs to be used to be able to configure FortiGate-VM using GUI.
For installing FortiGate-VM on OCI read this page https://www.ateam-oracle.com/fortinet-FortiGate-VM-oci-installation.
Step 1. Solution description.
Step 2. Prerequisites for FortiGate-VM and OCI.
Step 3. Pros and Cons for different network architectures.
Step 1. Solution description.
Some customers want to use 3rd party firewall vendors instead of using native cloud firewall capabilities. There are multiple reasons for wanting this, like more advanced features that are not available at this moment, or they already use that specific vendor in their own Data Centers. For this document, we will cover Fortinet and its FortiGate-VM solution.
There are different network topologies and each client chooses the right one based on their need. In this document, we will cover the Hub & Spoke network topology.
This topology it’s used for different scenarios, like:
- FastConnect or IPSec VPN from on-prem to OCI.
- Private access to Oracle Service Network (OSN).
- WAN access.
- North-South or East-West traffic filtering.
OCI provides a native solution for a Hub & Spoke network topology by using a feature called Transit Routing.
This will allow to do the following:
- Access to multiple VCNs in the same region: . This scenario enables communication between your on-premises network and multiple VCNs in the same region over a single FastConnect private virtual circuit or VPN Connect.
- Private access to Oracle services: This scenario gives your on-premises network private access to Oracle services, so that your on-premises hosts can use their private IP addresses and the traffic does not go over the internet.
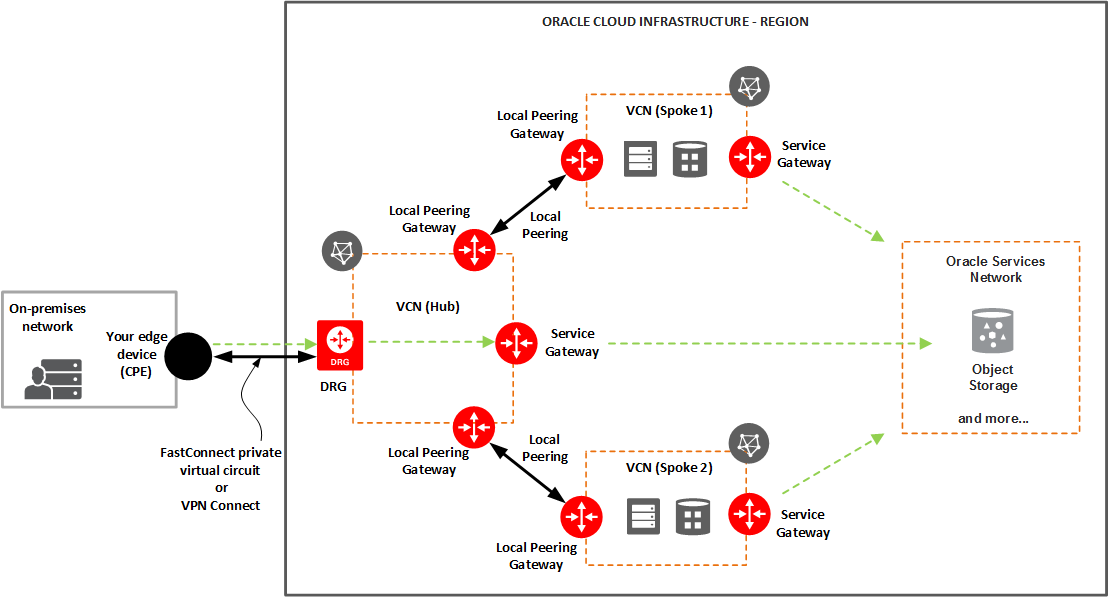
Diagram 1 – General representation. Access to multiple VCNs in the same region and to OSN
For more information about Transit Routing feature check OCI website – https://docs.cloud.oracle.com/en-us/iaas/Content/Network/Tasks/transitrouting.htm and https://docs.cloud.oracle.com/en-us/iaas/Content/Network/Tasks/transitroutingoracleservices.htm.
We will use the network topology above (Diagram 1) to integrate FortiGate-VM as a firewall appliance.
In the end, the entire solution will accomplish the following:
- Dedicated Management interface.
- Control traffic in and out for WAN or on-prem.
- Control traffic from Spoke to Hub.
- Control traffic from Spoke to Spoke.
- Control traffic from Hub or Spoke to OSN.
- Control traffic from Spoke to On-prem.
Step 2. Prerequisites for FortiGate-VM and OCI.
Keep in mind that there are multiple ways to create a Hub & Spoke networking topology. As an example, we ca use LPGs between VCNs and use fewer network interfaces on FortiGate-VM.
Another example can be to use FortiGate VNICs between VCNs. This approach will use multiple VNICs but will allow the traffic to be segregated between multiple interface and increase the network performance.
We will discuss later the pros and cons of each implementation.
Here are some network diagrams using FortiGate-VM with or without LPGs:
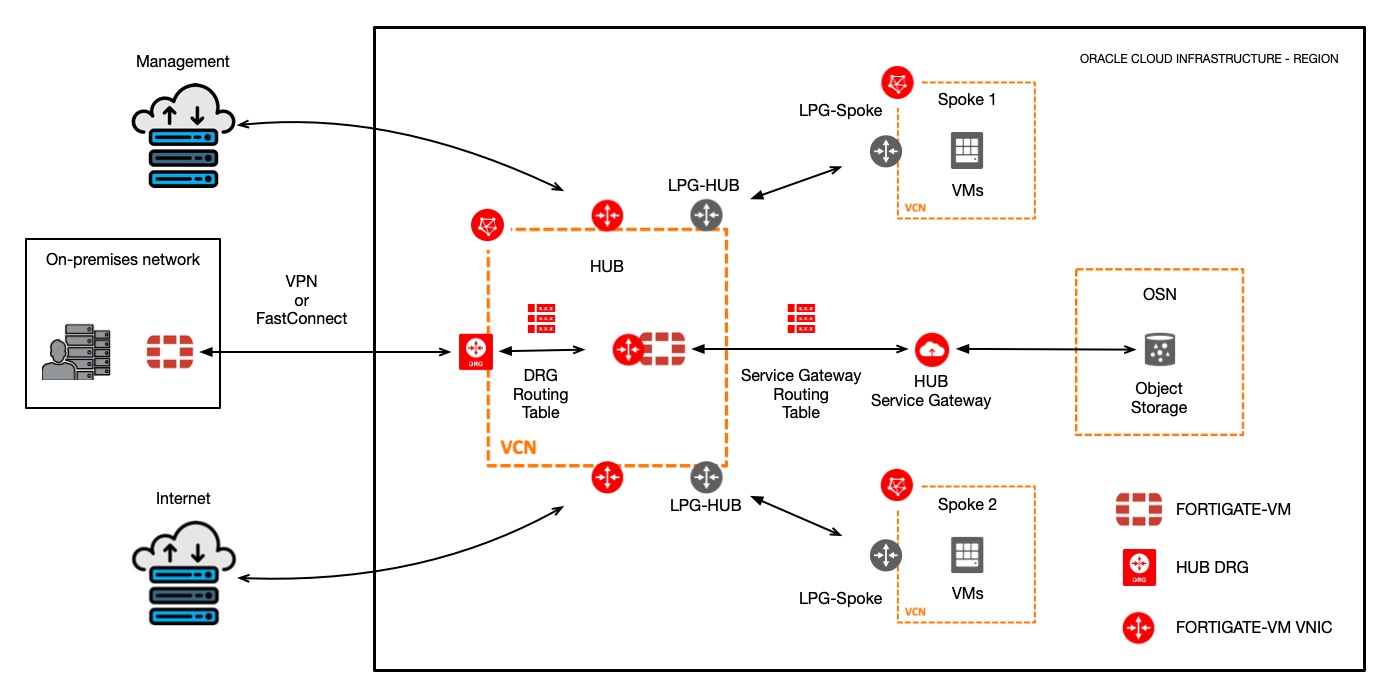
Diagram 2 – General representation. FortiGate-VM using LPGs
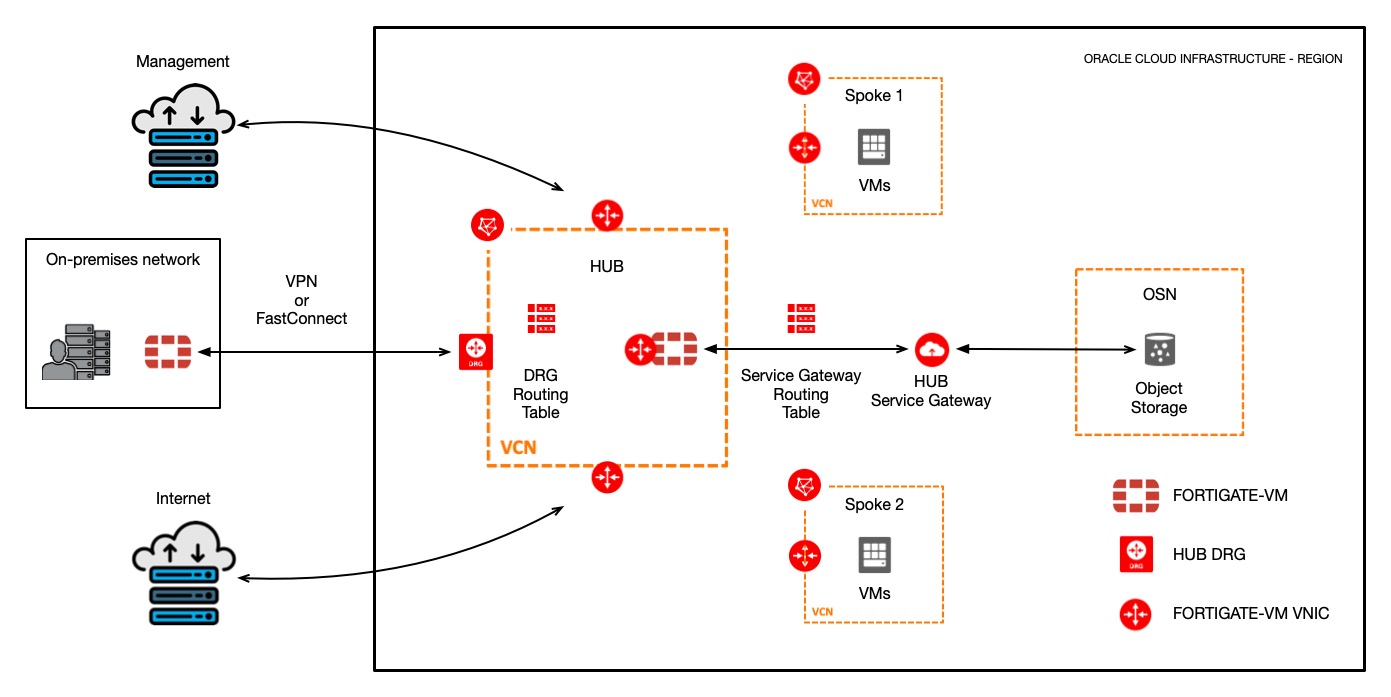
Diagram 3 – General representation. FortiGate-VM without using LPGs
Based on the network diagrams above, here are the prerequisites for both solutions:
1. FortiGate-VM with LPGs:
FortiGate-VM prerequisites:
For this configuration we will need 3 VNICs attached to FortiGate-VM. Interfaces will be used for the following:
1. Management interface
2. Internet interface
3. OSN, On-premises interface and Spoke 1 & 2
OCI prerequisites:
For this configuration we will need the following:
- 3 VCNs (HUB, Spoke 1, Spoke 2)
- HUB VCN will contain the following objects:
- 1 DRG
- 1 Service Gateway
- 1 Internet Gateway
- 3 Subnets
- 1 Subnet for Management access
- 1 Subnet for Internet access
- 1 OSN, On-premises interface and Spoke 1 & 2
- 6 Routing Tables
- 1 Routing Table for Management access
- 1 Routing Table for Internet access
- 1 Routing Table for OSN, On-premises and Spoke 1 & 2
- 1 Routing Table for LPG-Hub
- 1 Routing Table for DRG
- 1 Routing Table for Service Gateway
- Spoke 1 & 2 VCN will contain the following objects:
- 1 Subnet for each VCN
- 1 Routing Table for each VCN. This routing table will have as next-hop the LPG-Spoke allocated to that specific Spoke.
2. FortiGate-VM without LPGs:
FortiGate-VM prerequisites:
For this configuration we will need 5 VNICs attached to FortiGate-VM. Interfaces will be used for the following:
- Management interface
- Internet interface
- OSN & On-premises interface
- Spoke 1 interface
- Spoke 2 interface
OCI prerequisites:
For this configuration we will need the following:
- 3 VCNs (HUB, Spoke 1, Spoke 2)
- HUB VCN will contain the following objects:
- 1 DRG
- 1 Service Gateway
- 1 Internet Gateway
- 3 Subnets
- 1 Subnet for Management access
- 1 Subnet for Internet access
- 1 Subnet for OSN & On-premises access
- 5 Routing Tables
- 1 Routing Table for Management access
- 1 Routing Table for Internet access
- 1 Routing Table for OSN & On-premises access
- 1 Routing Table for DRG
- 1 Routing Table for Service Gateway
- Spoke 1 & 2 VCN will contain the following objects:
- 1 Subnet for each VCN
- 1 Routing Table for each VCN. This routing table will have as next-hop the IP address allocated to the VNIC for that specific Spoke.
When implementing a Hub & Spoke network architecture, the intent is to filter everything using FortiGate-VM policy security rules and IPS/IDS engine. However, you also have the option to add additional security by filtering at FortiGate-VM instance and the OCI level.
For building a HA environment using FortiGate-VM, check this blog page – https://www.ateam-oracle.com/fortinet-fortigate-ha-on-oci.
Step 3. Pros and Cons for different network architectures.
Pros and Cons to consider when using FortiGate-VM with or without LPGs:
| item |
FortiGate-VM with LPGs |
FortiGate-VM without LPGs |
| VNICs used |
minimum 3* (MNGM, WAN, LAN) |
minimum 3* + n (MNGM, WAN, LAN + nr. of Spokes) |
| VM Cost |
Low (less VNICs**) |
High (more VNICs**) |
| Bandwidth |
Based on the VM Shape*** |
Based on the VM Shape*** |
| Traffic type |
North-South traffic |
East-West traffic |
| Network links HA |
OCI Native |
Multiple FortiGate-VMs in HA |
| Simplicity |
Simple |
More complex |
* 4 VNICs in case HA is needed.
** In OCI the number of VNICs is equal to the number of OCPUs.
*** The VM Shape used will have a total bidirectional bandwidth available. Doesn’t matter how many VNICs the specific VM will have.
