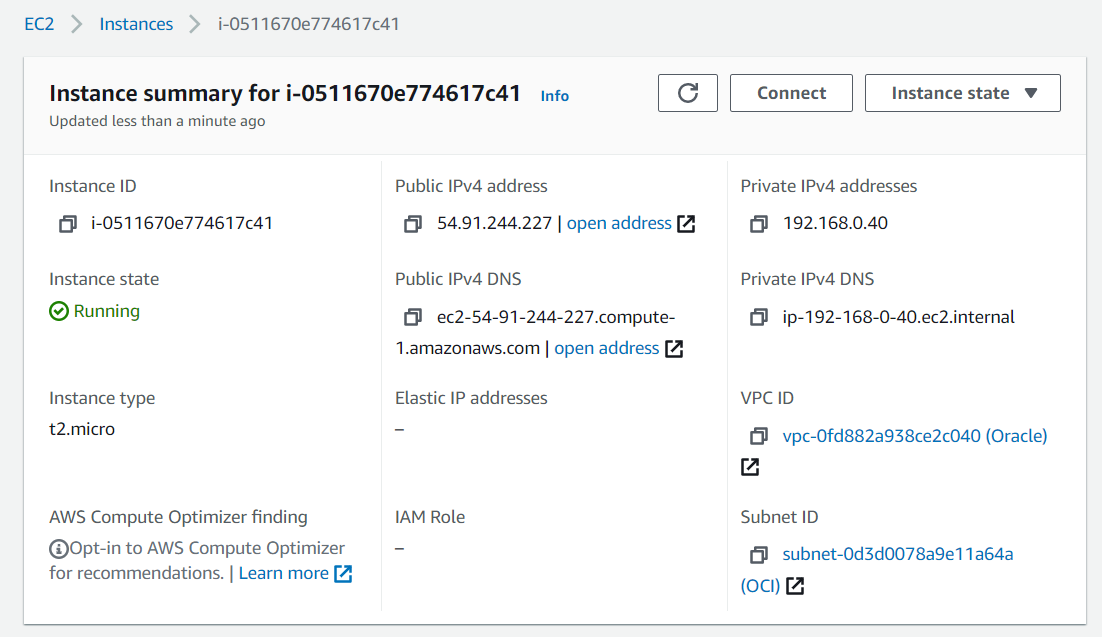
Introduction
Earlier this year my colleague Andrei Stoian (Bogdan) published a blog post that highlights the steps for interconnecting OCI and AWS via native VPN services from both vendors. Once you have the tunnel up and running, and the respective route and security rules are in place, the next logical step is to leverage the internal DNS services of the Virtual Networks. In this post I will provide step by step details for configuring the Internal DNS resolver on both Clouds.
The connectivity between OCI and AWS can be over IPSec or FastConnect, in this case I am using a 1 Gbps FastConnect digital circuit, already configured to completion. In this post an engineer at Equinix and I detail OCI to AWS FastConnect interconnectivity via Equinix Cloud Exchange Fabric. Familiarity with both OCI and AWS consoles, and foundations knowledge of cloud networking is required for this post.
CIDR Prefixes
On the OCI side, we are using a Virtual Cloud Network (VCN) with a CIDR prefix of 172.17.0.0/16.
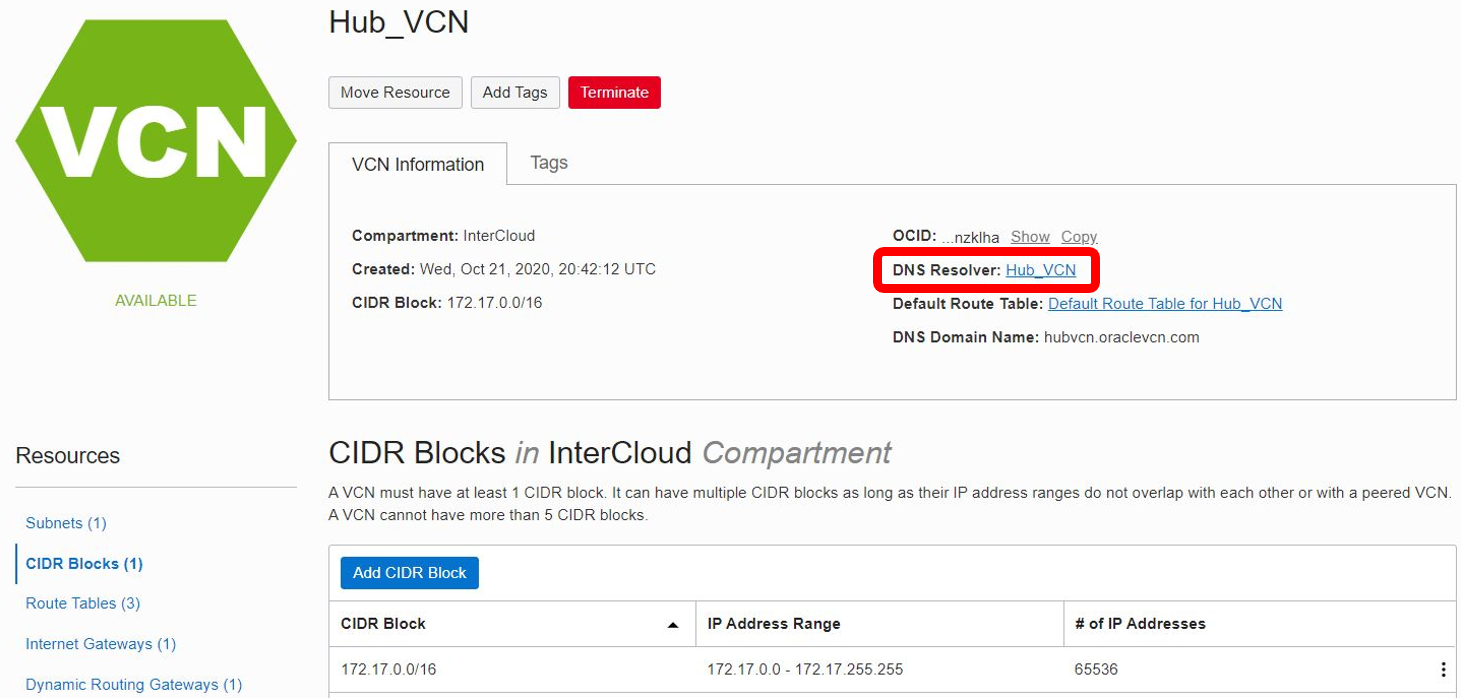
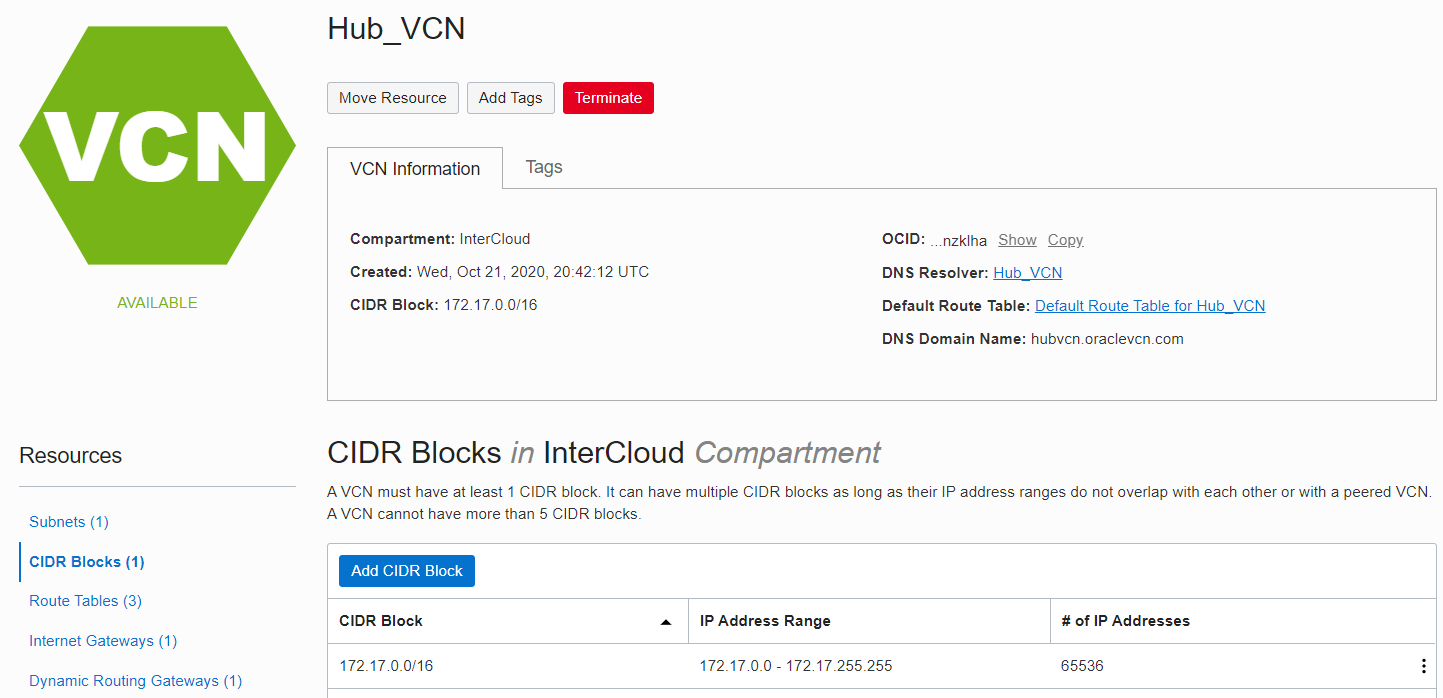 Notice that the DNS Domain Name for the VCN is: hubvcn.oraclevcn.com.
Notice that the DNS Domain Name for the VCN is: hubvcn.oraclevcn.com.
On The AWS side, we’re using a Virtual Private Cloud (VPC) with a CIDR prefix of 192.168.0.0/16.
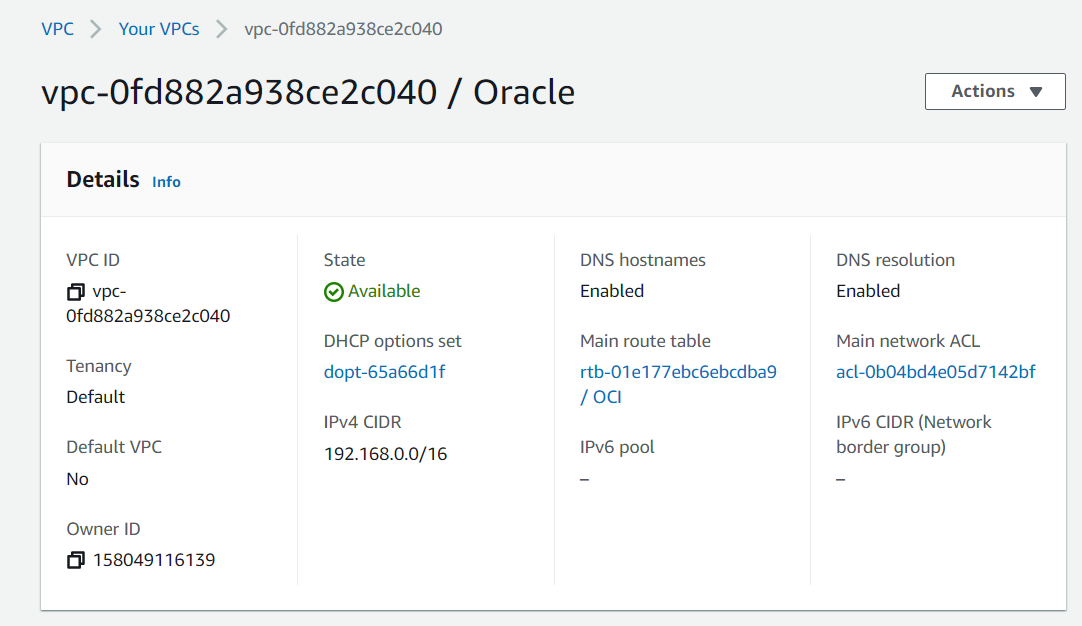
To retrieve the internal DNS Domain Name click on the link under DHCP options set (dopt-65a66d1f).
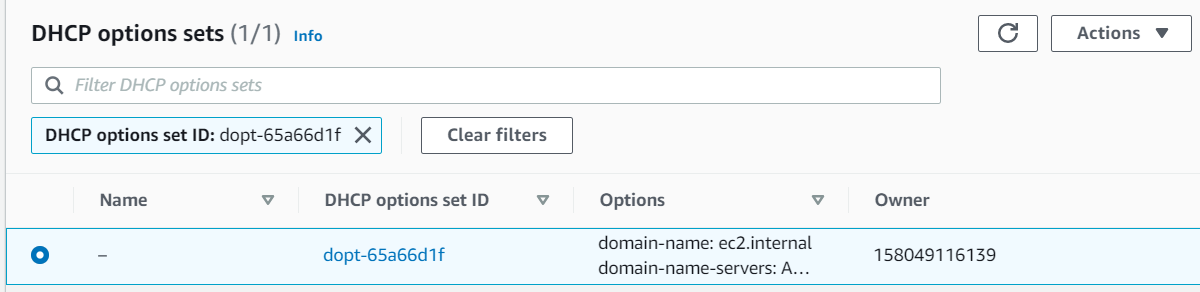 The DNS Domain Name for the VPC is: ec2.internal.
The DNS Domain Name for the VPC is: ec2.internal.
Compute
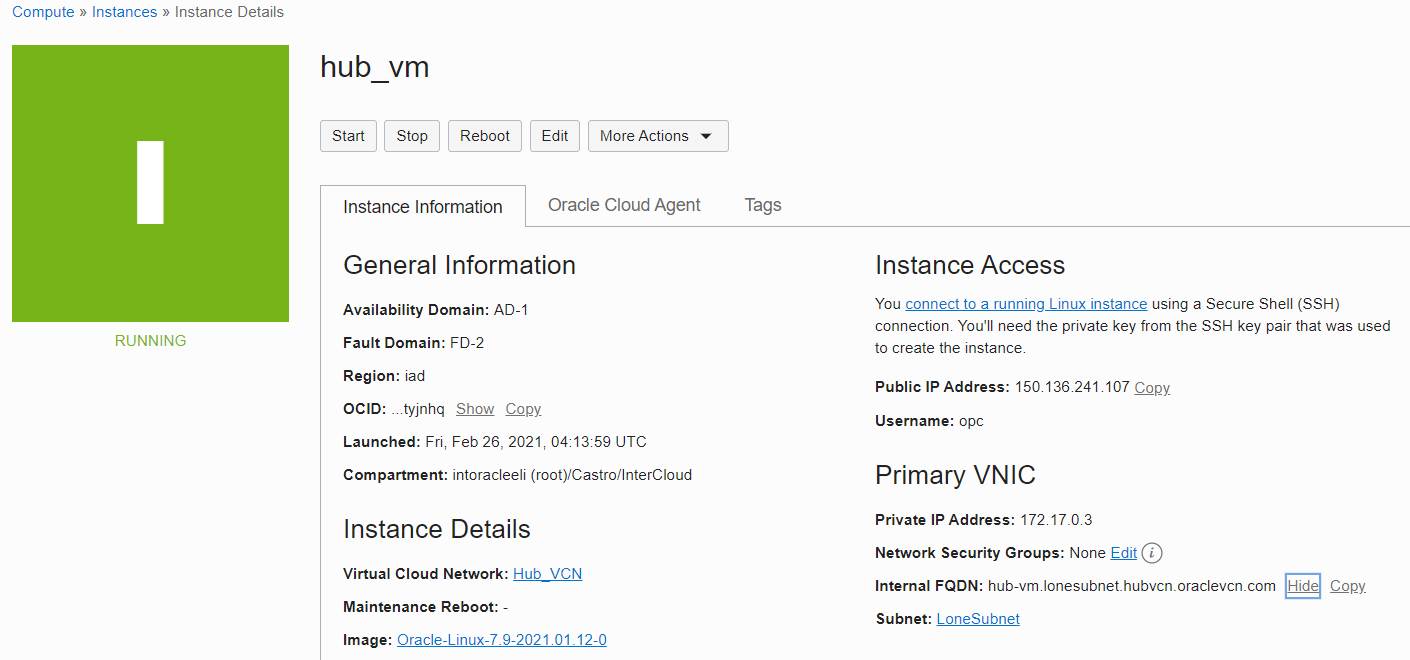
The Virtual Machine (VM) instance on OCI has a private IP Address of 172.17.0.3, and the Internal FQDN is: hub-vm.lonesubnet.hubvcn.oraclevcn.com:
The Elastic Cloud Compute (ec2) instance on AWS has a private IP Address of 192.168.0.40, and the internal FQDM is: ip-192-168-0-40.ec2.internal:
Verifying connectivity via the private channel
I mentioned earlier that the connectivity was previously configured to completion. Let’s login to both compute instances to verify connectivity with ICMP.
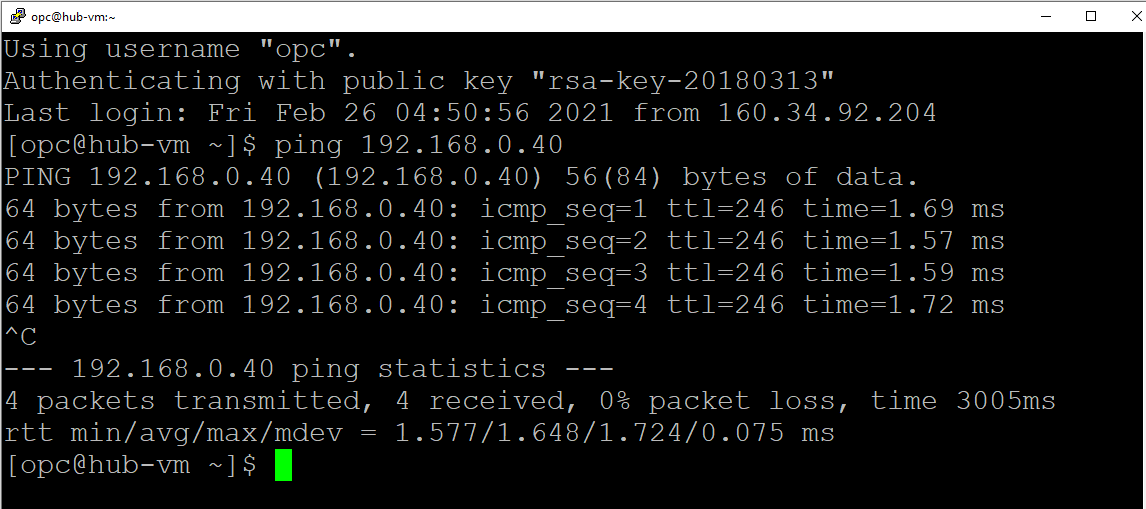
Pinging from OCI to AWS using the IPv4 address:
Pinging from AWS to OCI using the IPv4 address:
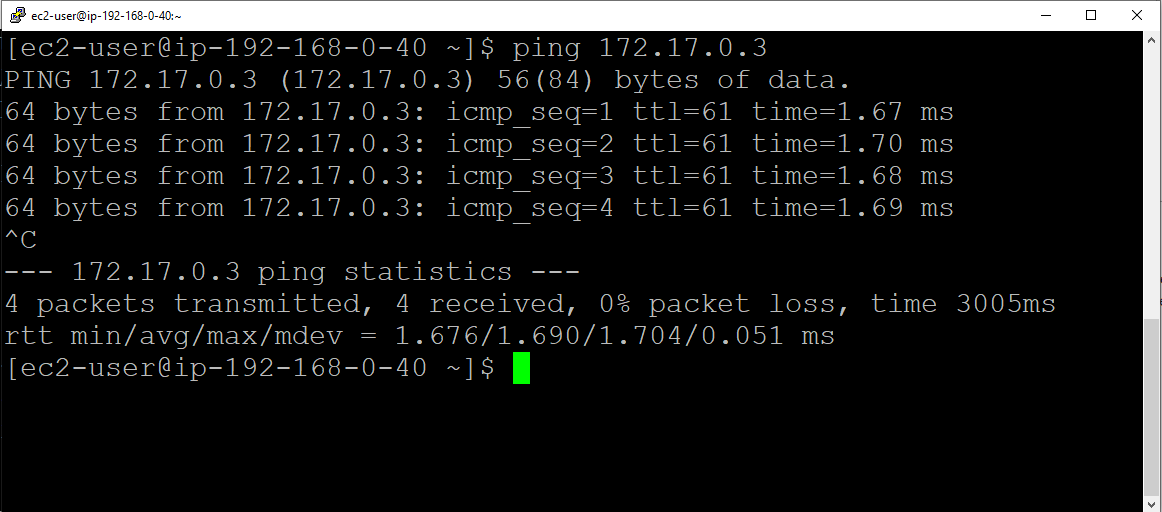
It works, as expected. Now, let’s try pinging the FQDN of both instances.
Pinging from OCI to AWS using the FQDN:
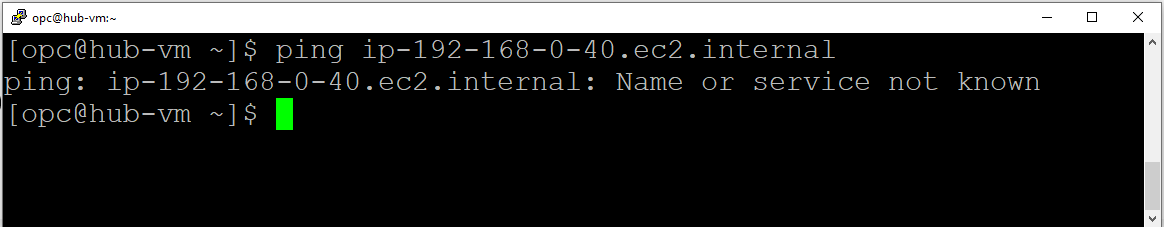
Pinging from AWS to OCI using the FQDN:
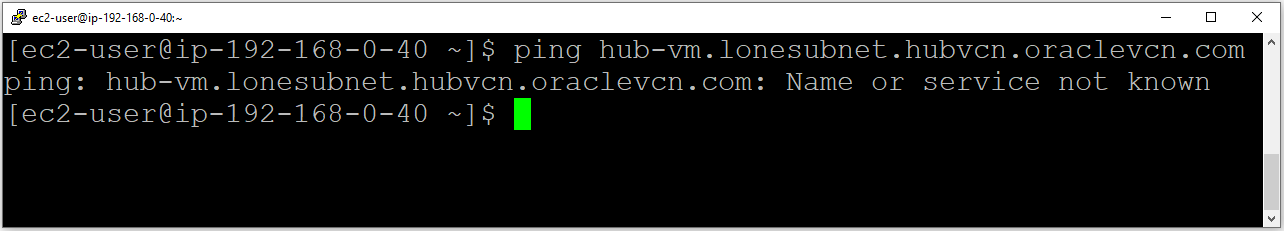
It doesn’t work.
DNS Resolver on OCI
To make it work, on the OCI side we will use the DNS Resolver, accessible directly from the VCN. On AWS we will use Route 53’s Resolver feature.
On the OCI console navigate to networking and open your VCN, click on the link to the right of the DNS Resolver field, Hub_VCN in this example.
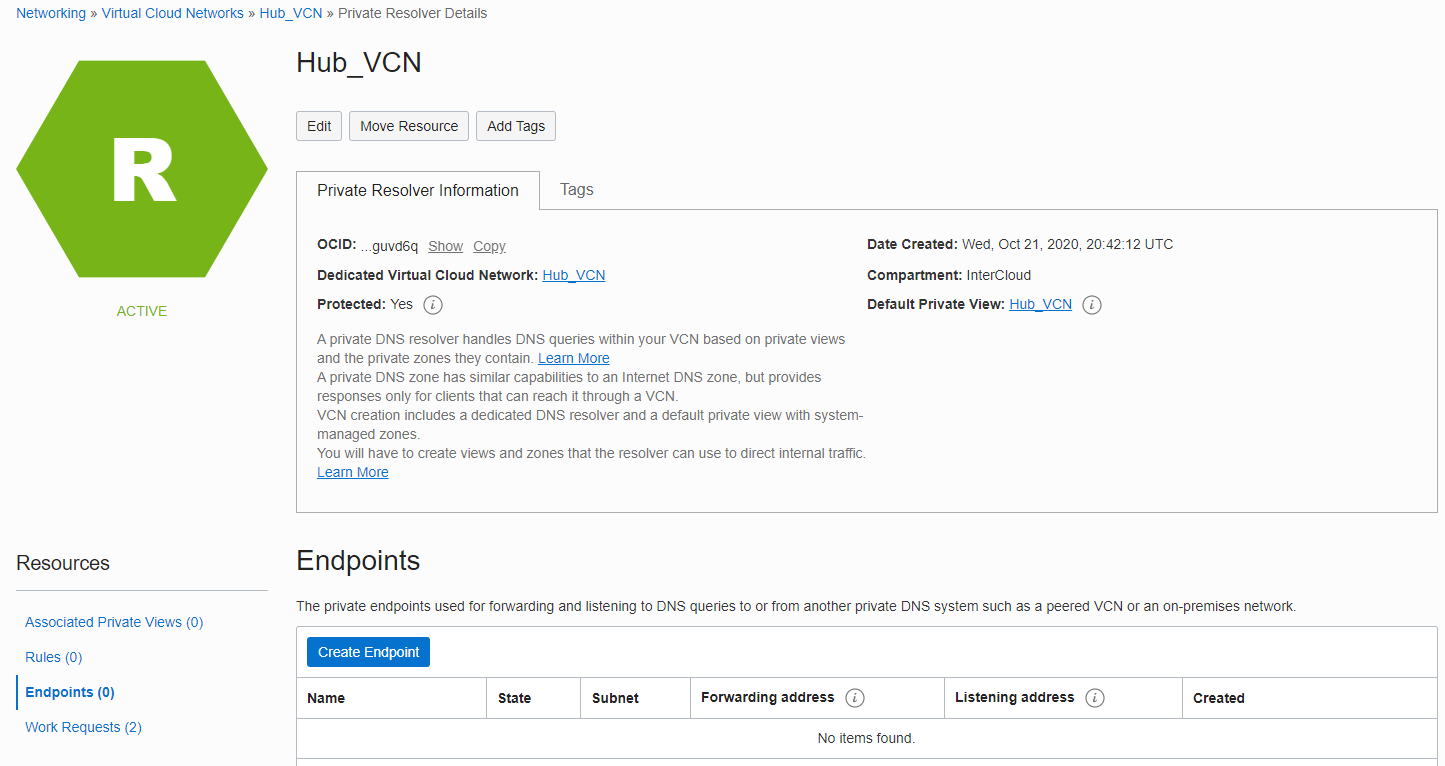
Click on Endpoints (0), and then click on the Create Endpoint button.
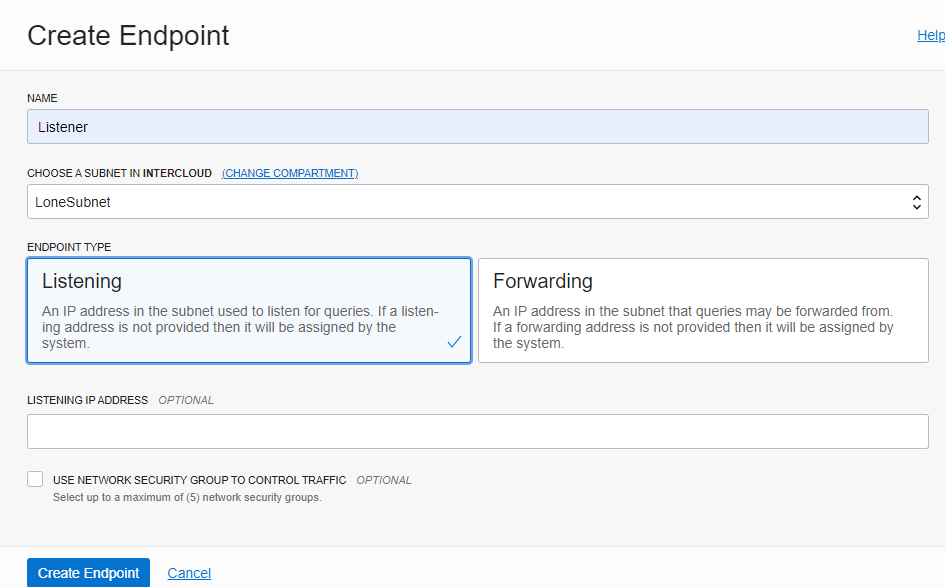
Here we will create two endpoints on the subnet where the OCI compute instance resides; one endpoint, titled Listener, will be for listening to external requests for the VCN’s Private DNS Domain Name, and the other endpoint, titled Forwarder, is for forwarding requests from internal resources to external Private DNS Domain Names. Create them.
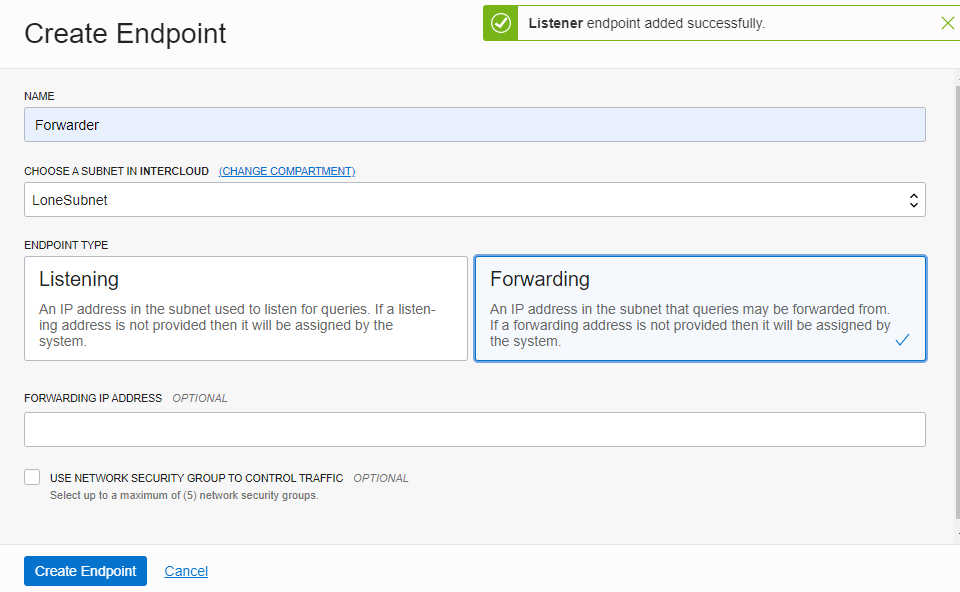
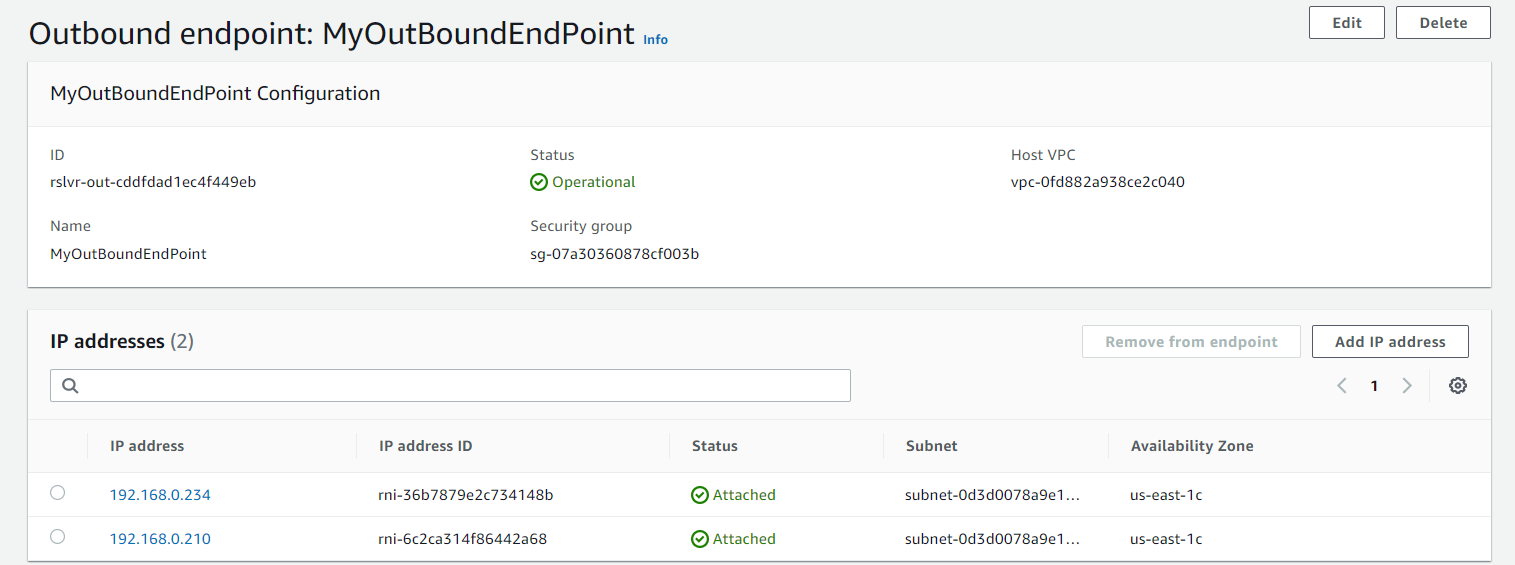
Now we have the endpoints on OCI.
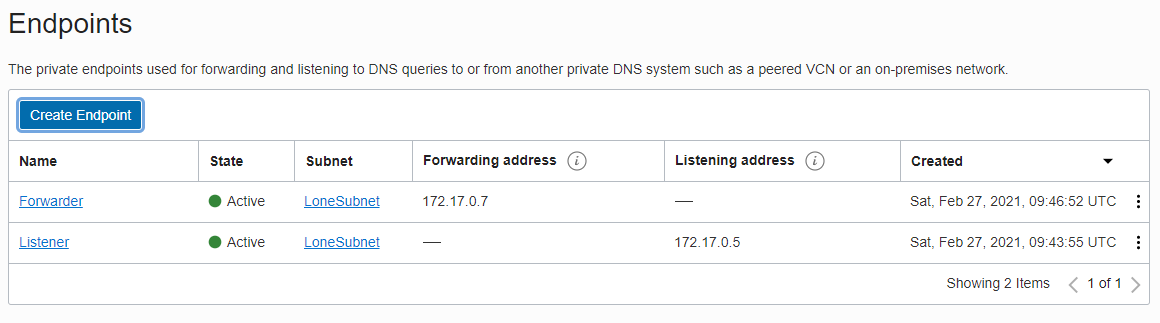
DNS Resolver on AWS
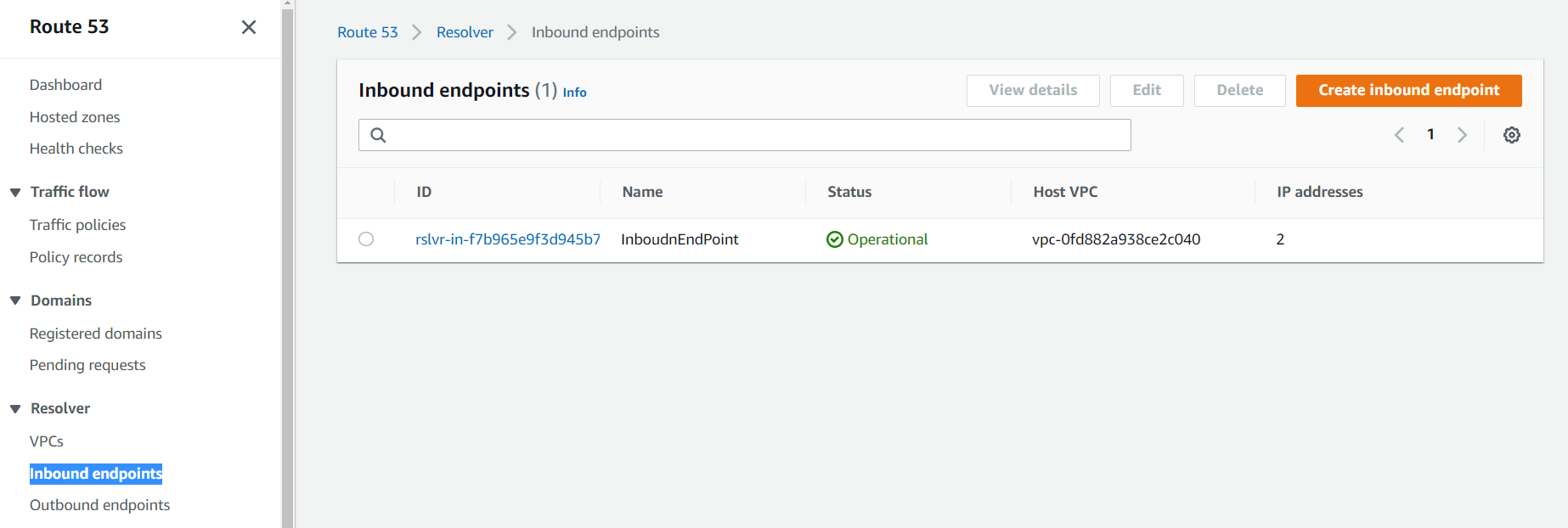
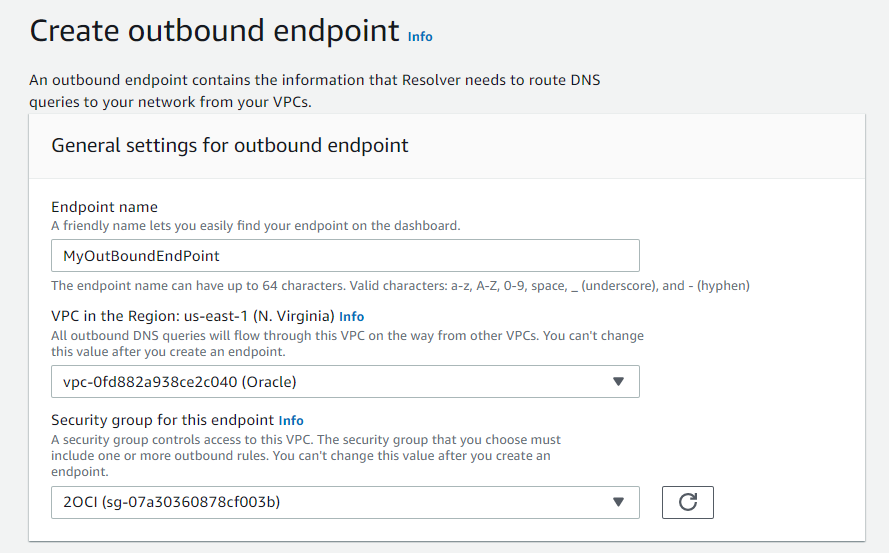
The next set of steps is for configuring endpoints on AWS. Navigate to Route 53, and under Resolver click on Inbound endpoints, then click on the Create Inbound Endpoint button.
On the AWS side, you will need to provide the details for the VPC where your ec2 instance reside; including Subnet(s), Security Group, and Availability Zone of the Subnet(s).
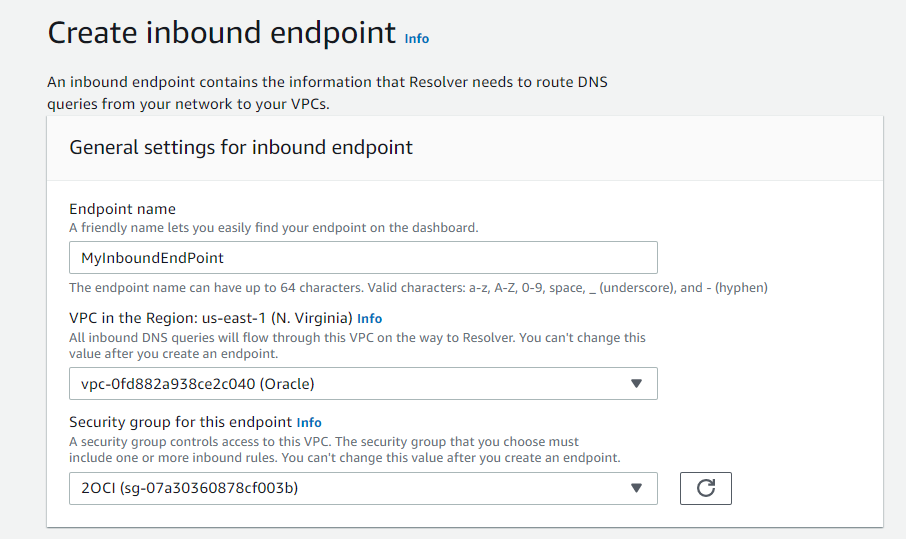
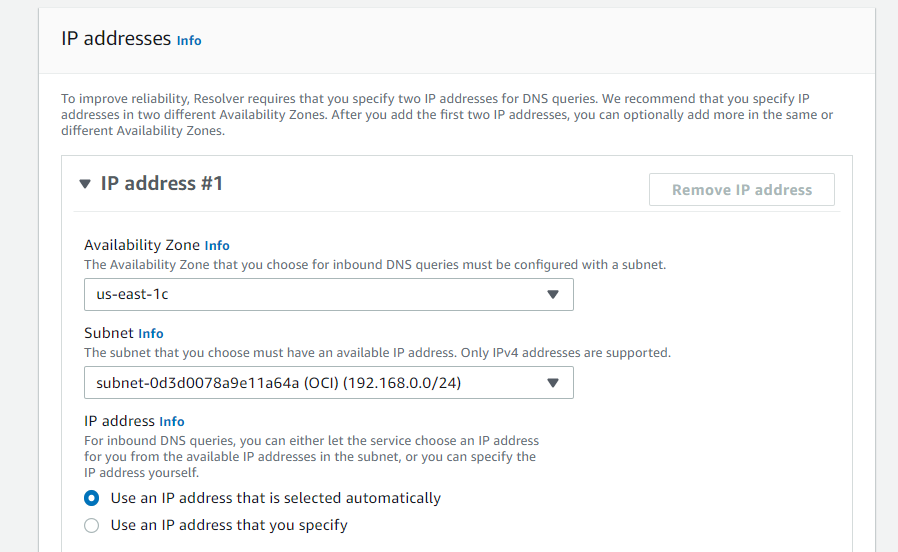
Submit and repeat these steps for the Outbound Endpoint.
For viewing the details of your endpoint, click on the link to the left of the name you assigned it, under ID.
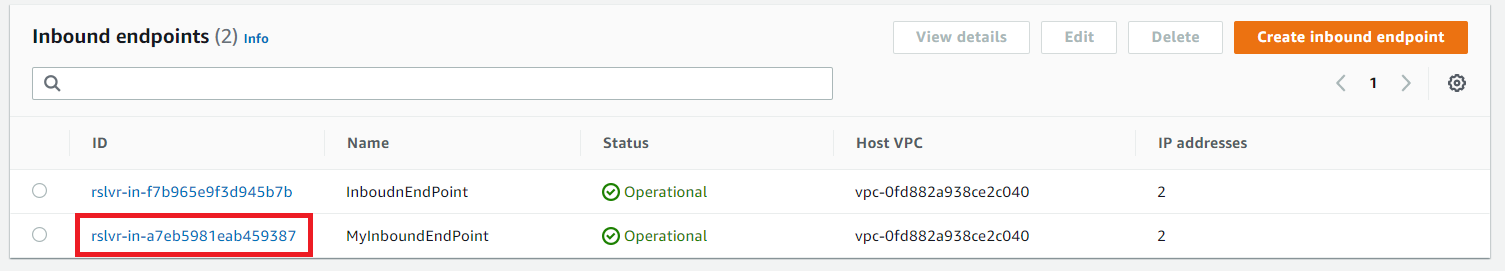
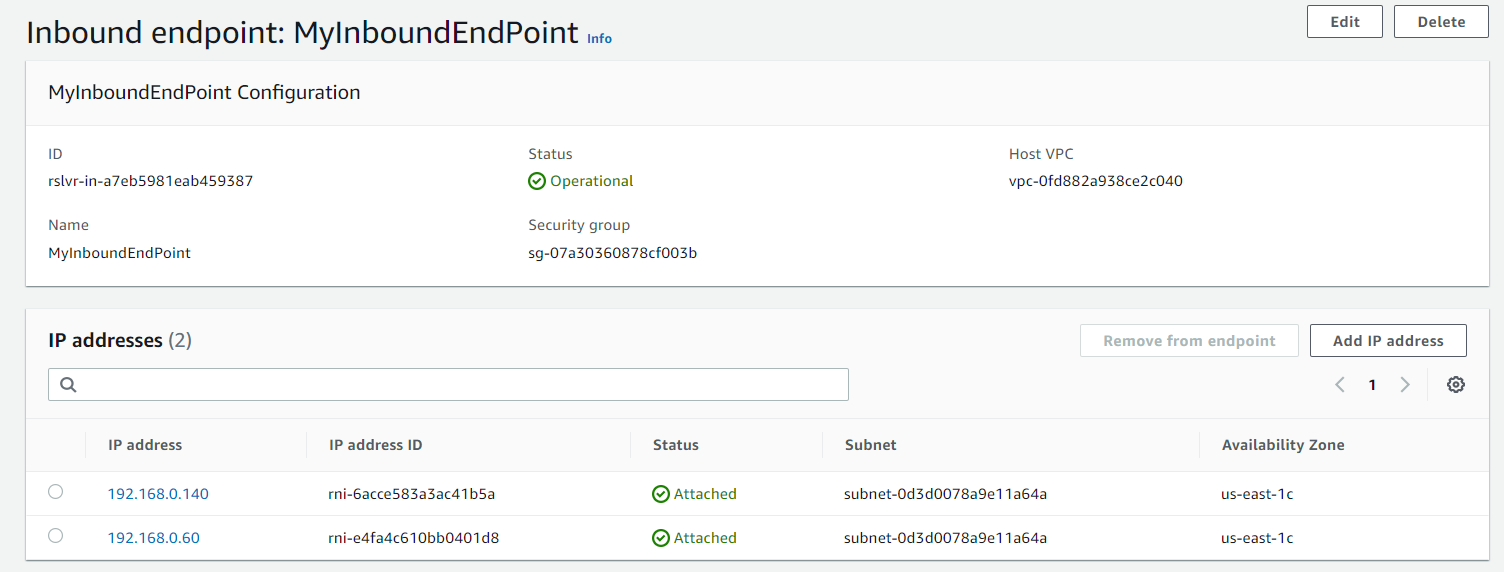
Repeat the step for the outbound endpoint.
Private DNS Rules on OCI
Now that we have these endpoints; on OCI we will add rules that will map them to the AWS VPC FQDN.
Open your OCI Console, select Networking, select the appropriate VCN, click on DNS Resolver, then on Rules (0), and finally Click on the Manage Rules button.
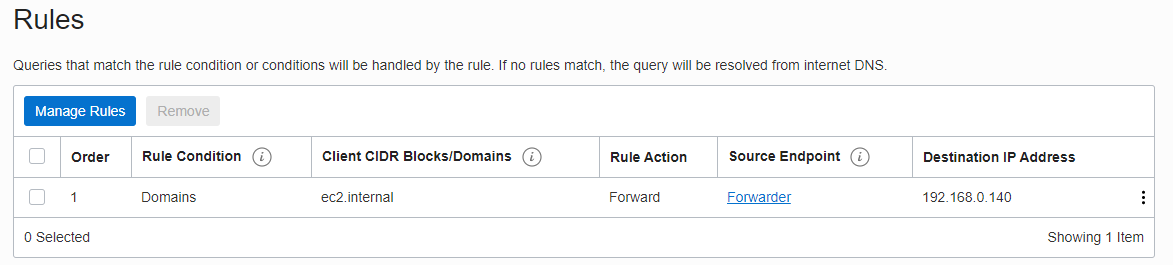
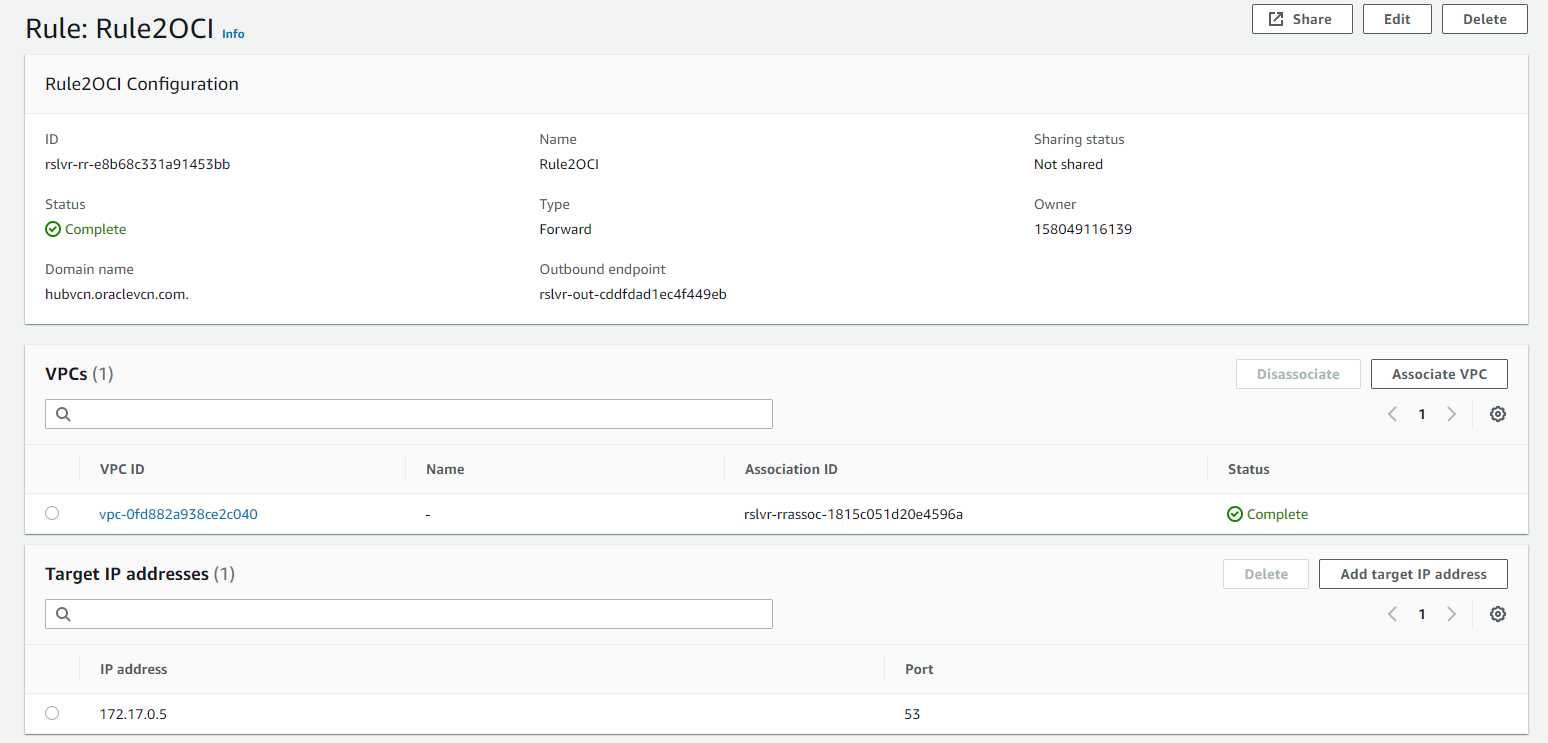
For RULE CONDITION select Domains. For DOMAINS enter the AWS VPC’s FQDN, ec2.internal in this case. For RULE ACTION select Forward, for SOURCE ENDPOINT select Forwarder and for DESTINATION IP ADDRESS enter the AWS Inbound endpoint address, in this case it is 192.168.0.140. Click Submit.
Private DNS Rules on AWS
Next, we will configure rules on AWS’ Route 53. Open your AWS Console, select Route 53, under Resolver select Rules, and click on the Create Rule button. Fill the fields. Enter a name for your Rule, for Rule Type select Forward, for Domain Name enter the OCI VCN FQDN, hubvcn.oraclevcn.com in this example, choose the appropriate VPC for this rule. And for Outbound Endpoint select the one we just created. For Target IP Address enter the OCI Listener Endpoint IP Address, 172.17.0.5 in this case.
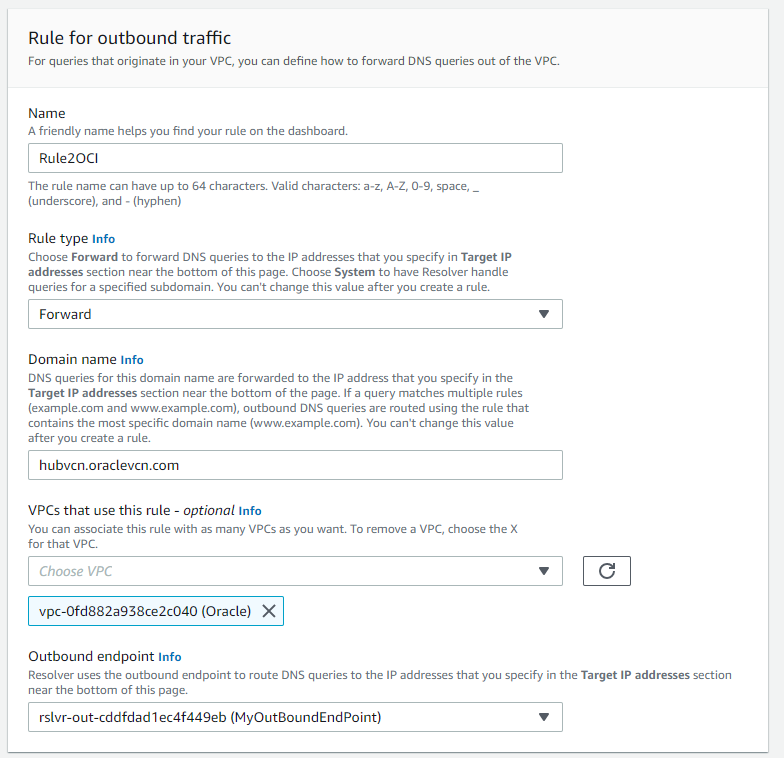
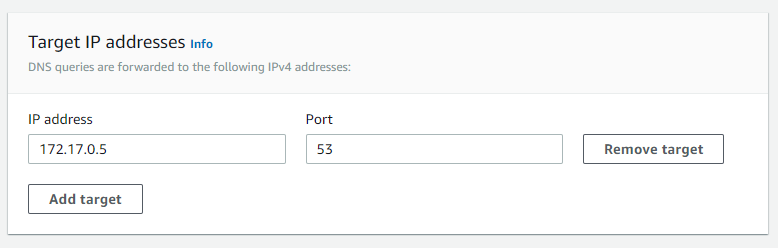
Click Submit.
Port 53
The one thing pending, which is very important, is opening port 53 on OCI Security List, and on AWS Security Groups, for both UDP and TCP. Once these are configured, ping your FQDNs.
Test your configuration
Pinging from AWS to the OCI Compute Instance FQDN:
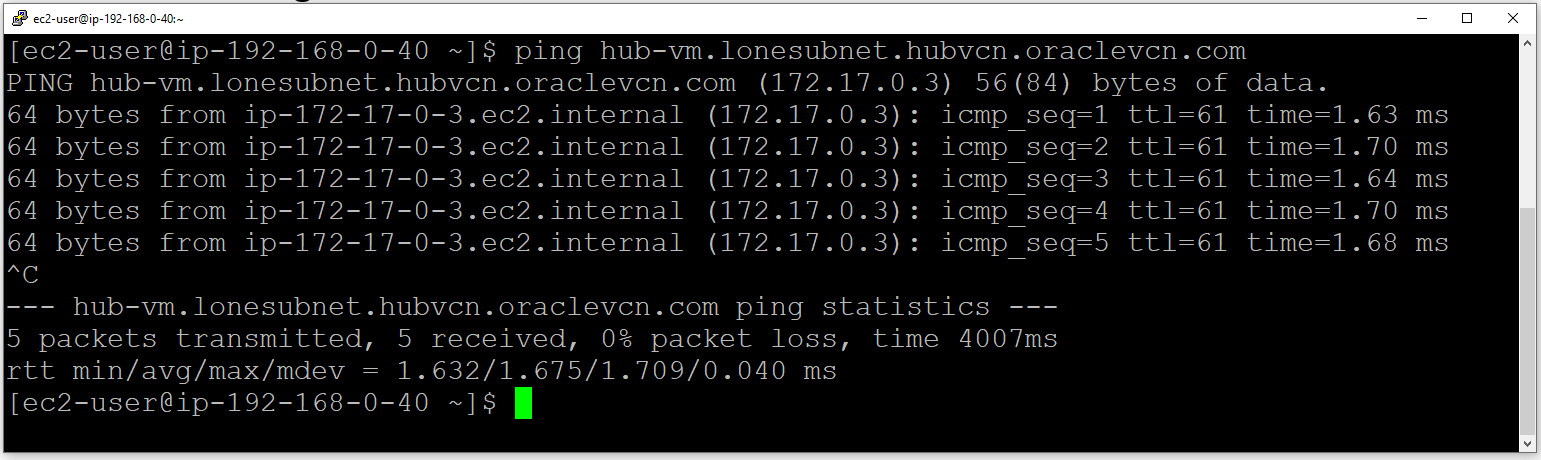
Pinging from OCI to AWS:
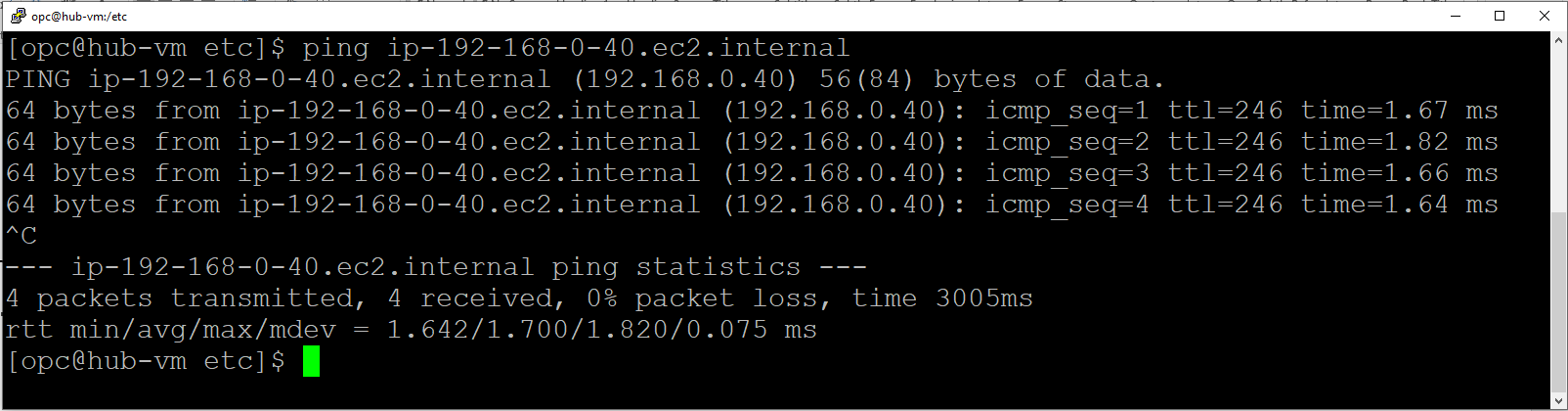
Success!
References:
