This post will describe how to setup the Identity Cloud Service (IDCS)/OCI Identity Domains App Gateway to support Multi-Factor Authentication (MFA). However, before I get into the use case, if you need a refresher or just want to understand how App Gateway works and how it is configured, please refer to the following documentation and blog posts.
Oracle Documentation:
Blog Posts:
Use Case
A web application has multiple entry points (URLs) and one of those entry points has some sensitive data to be protected. The customer wants to setup an additional factor (MFA) during authentication for this endpoint only.
Configuration
Let’s look at an example, I have created a simple html application on my HTTP server. It has four URLs; “/appgateway”, “/appgateway/public”, “/appgteway/private” and “/appgateway/mfa”.
Within the IDCS Console, you can specify any prefix URL to map to your back-end HTTP server. In my case I will be using root (/) to map to the root of my application which is “/appgateway/”.
Here is a list of resources that I have defined. This includes root and everything under root and the three sub-directories:
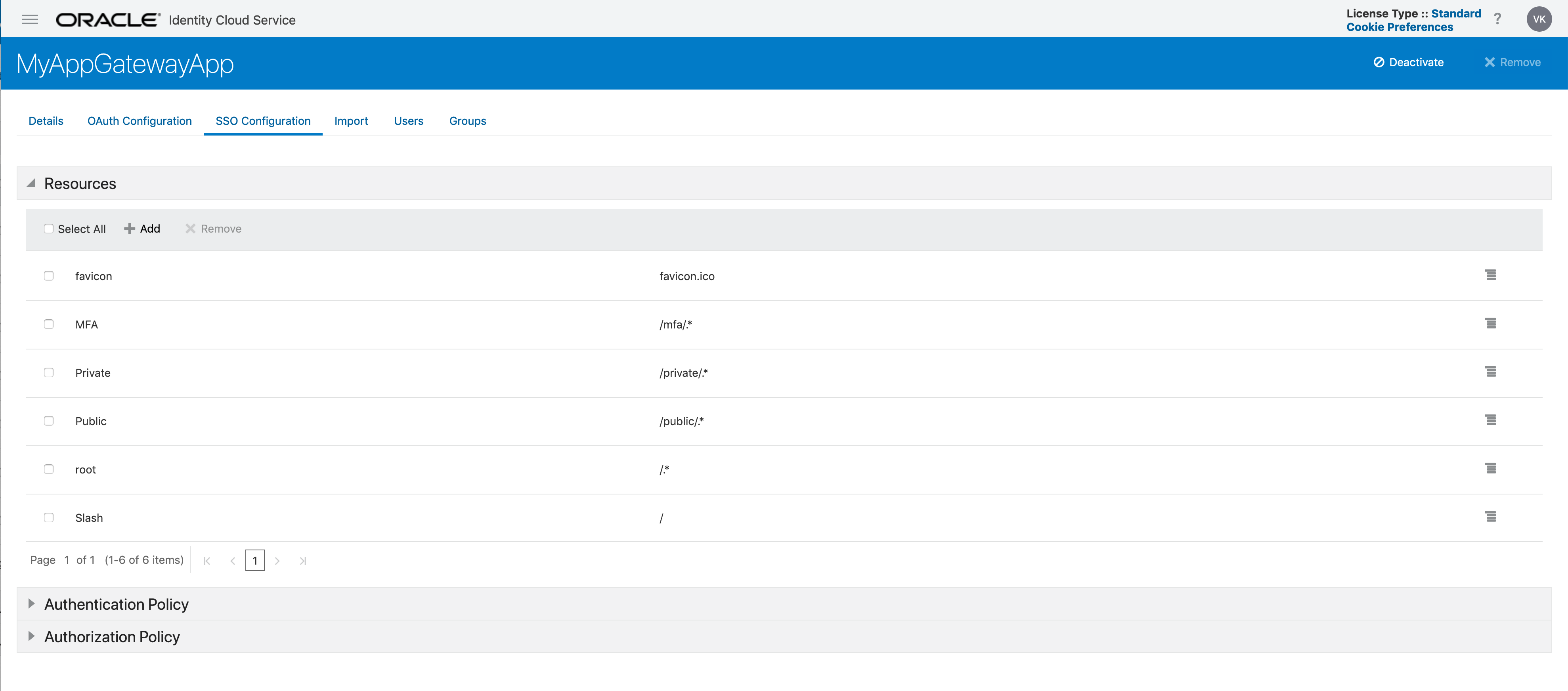
The /appgateway (or root), “/private/.*” and “/mfa/.*”are all protected and require the user to authenticated. “/public/.*” is set to public. The authentication type is defined under the Authentication Policy:
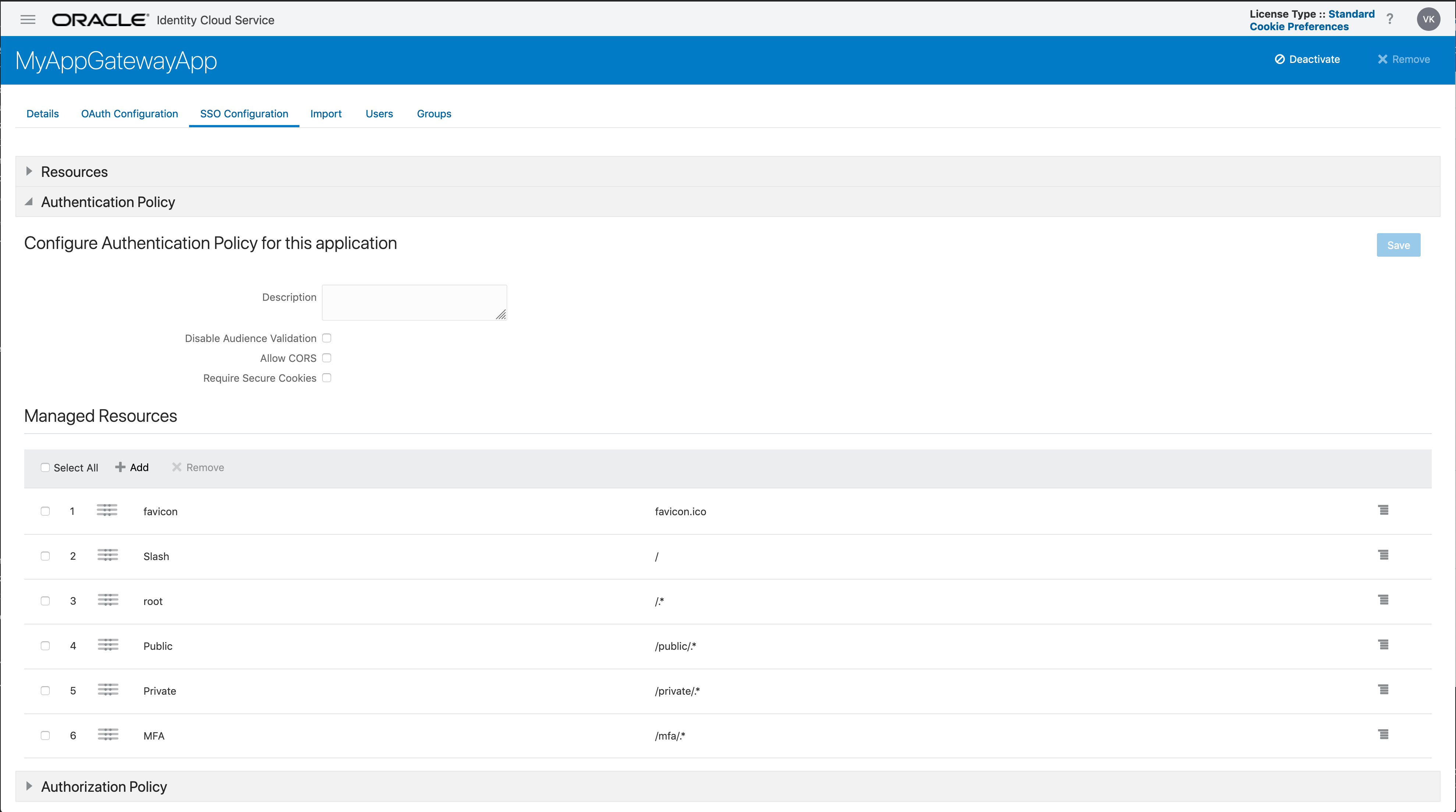
You may have noticed that the resources defined in Enterprise Application configuration has all the resources defined including the “/mfa/.*” URL. However, when configuring IDCS to a specific sign-on policy it is based on the application. Since “/mfa” is defined within the Enterprise Application, there is no way to distinguish which policy to use between say “/private/” and “/mfa/”. They both will use the username-password Sign-on Policy which is the default in IDCS.
In order to support MFA for only the “/mfa/” URL, we must create another Enterprise Application for that URL. That is the secret sauce!
So lets do that, here is the definition of my new MFA Enterprise Application:
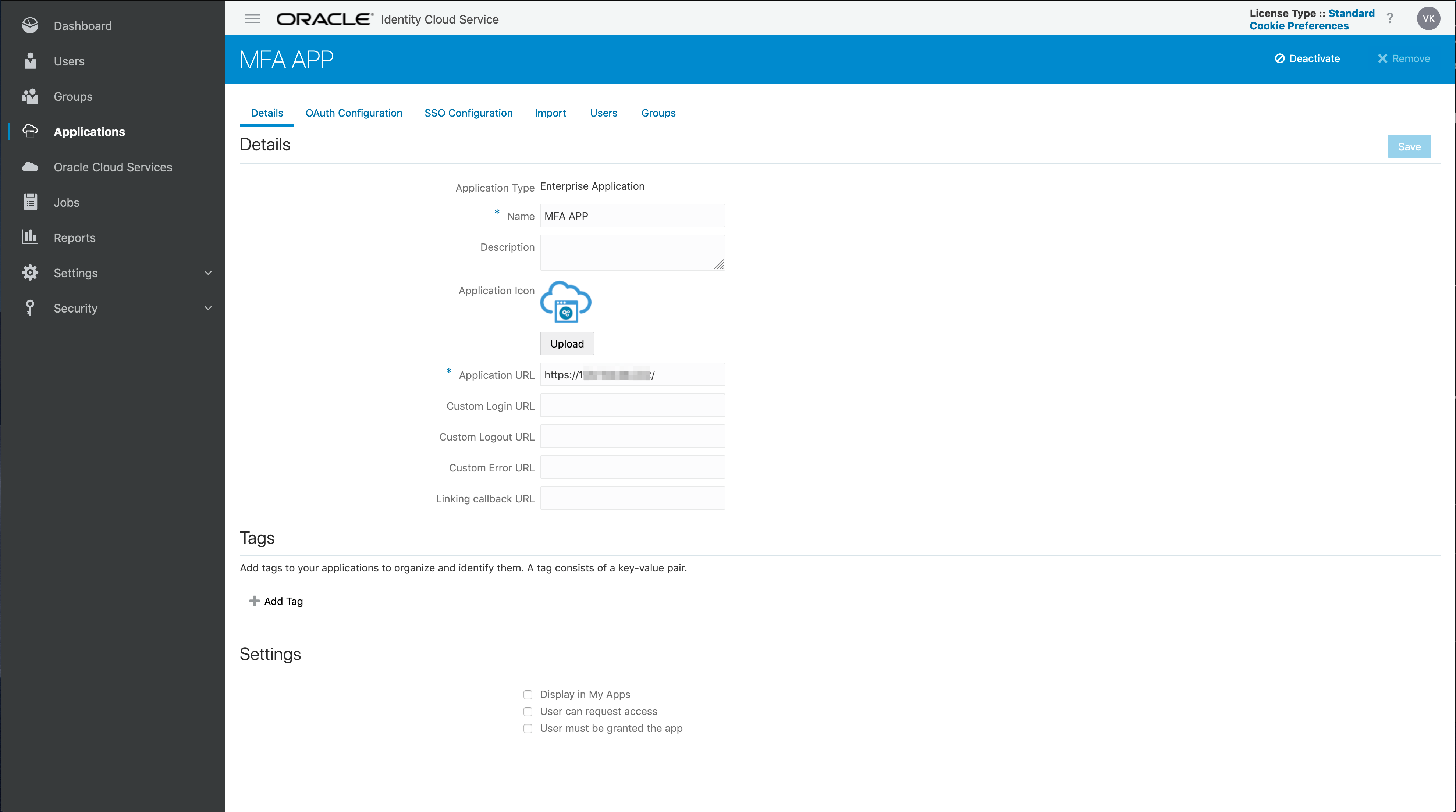
The Application URL will remain the same. We just need to add the “/mfa/.*” URL in our new MFA App.
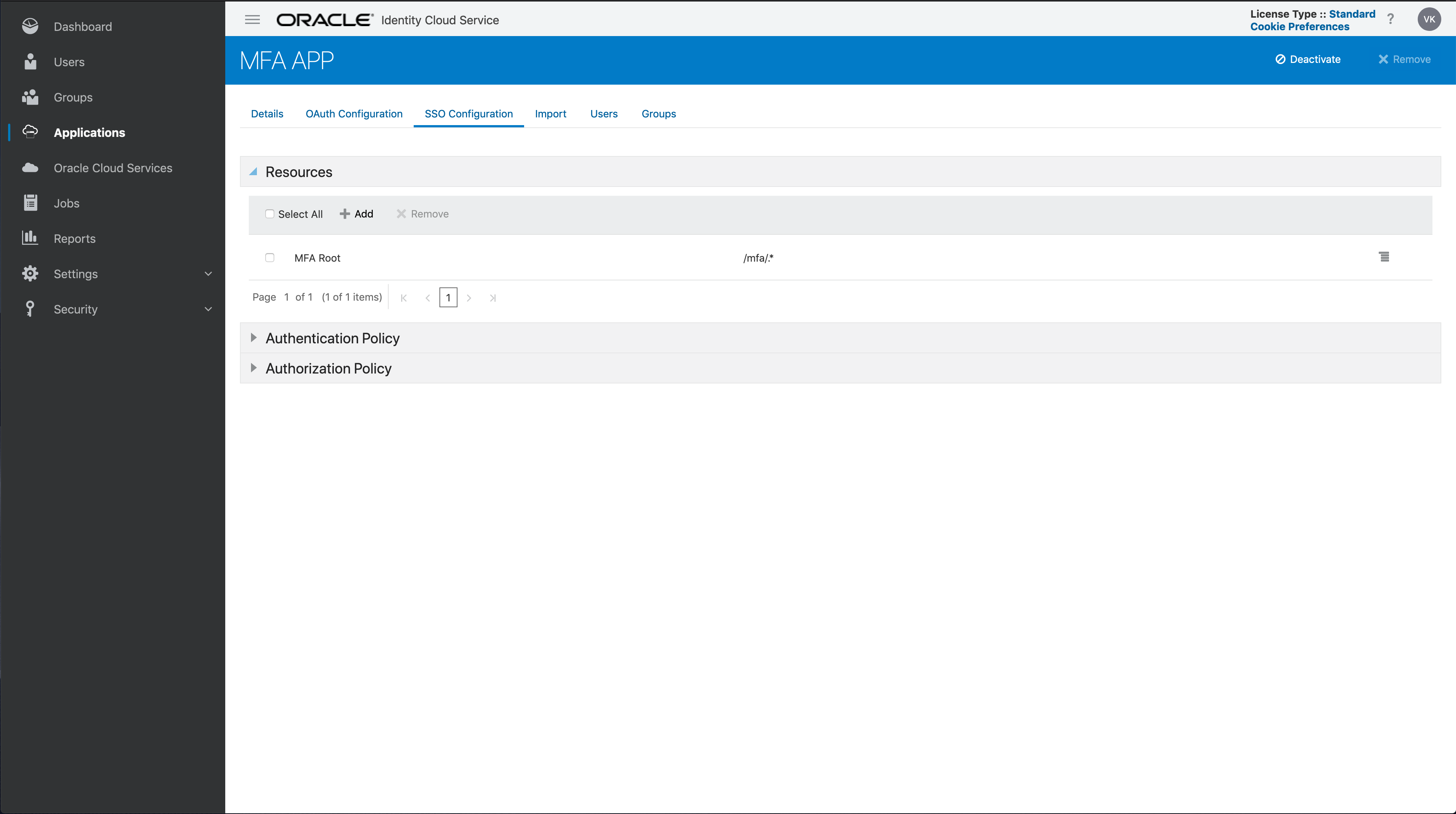
Don’t forget to remove all references to the “/mfa/.*” URL from the original enterprise application. It will no longer be protected by the sign-on rule defined for this app.
Now that have have a new MFA Application, I need to do two additional steps:
-
Add the application to the app gateway and
-
Add the application to a new sign-on policy that requires MFA.
Here is what my config looks like; adding the new MFA application to the App Gateway:
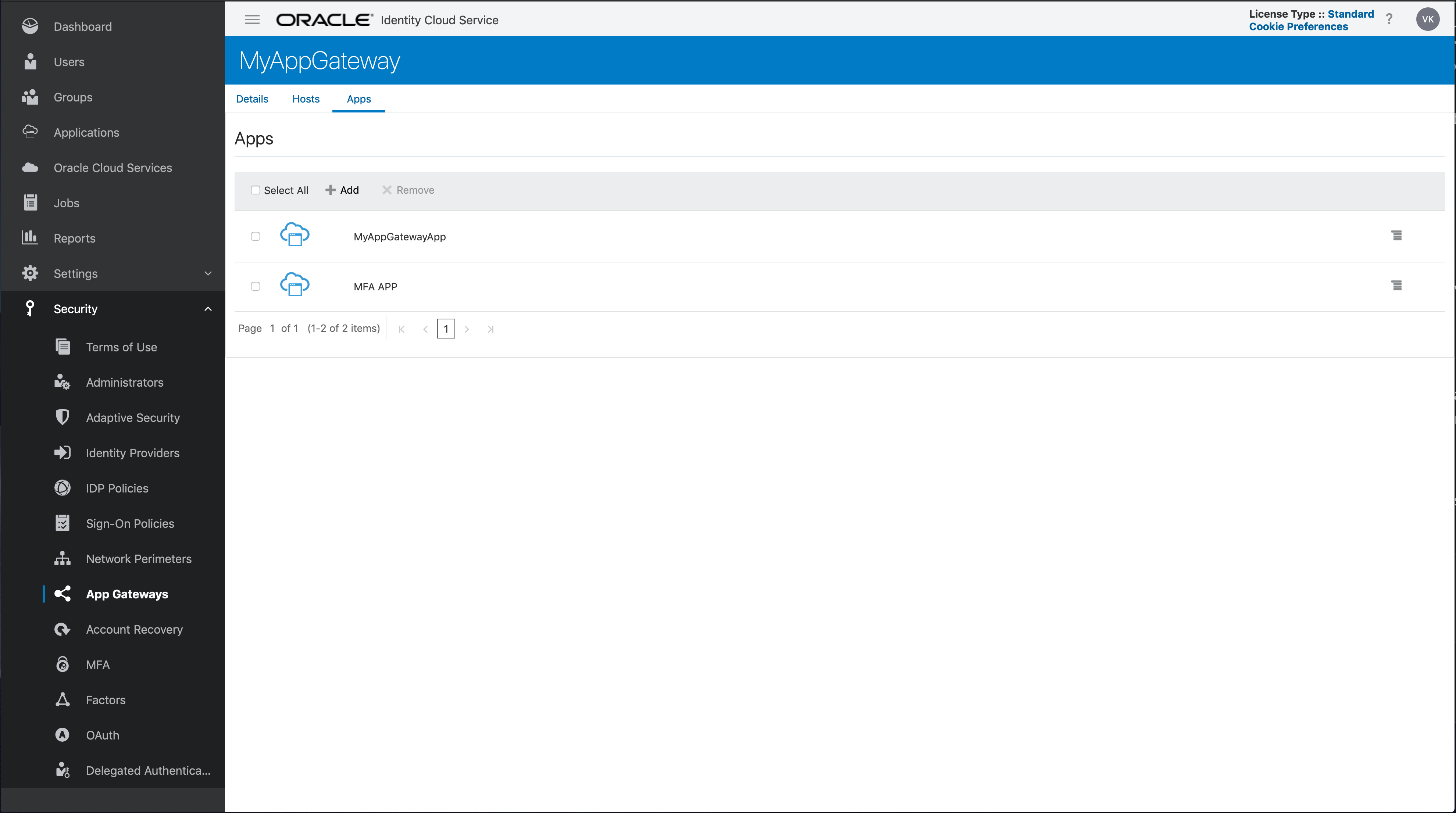
I have basically split my original application into two different enterprise applications. The “/mfa” endpoint is now represented by the new MFA App application. This allows me to now define a new sign-on policy specific to my new MFA App and configure it for MFA.
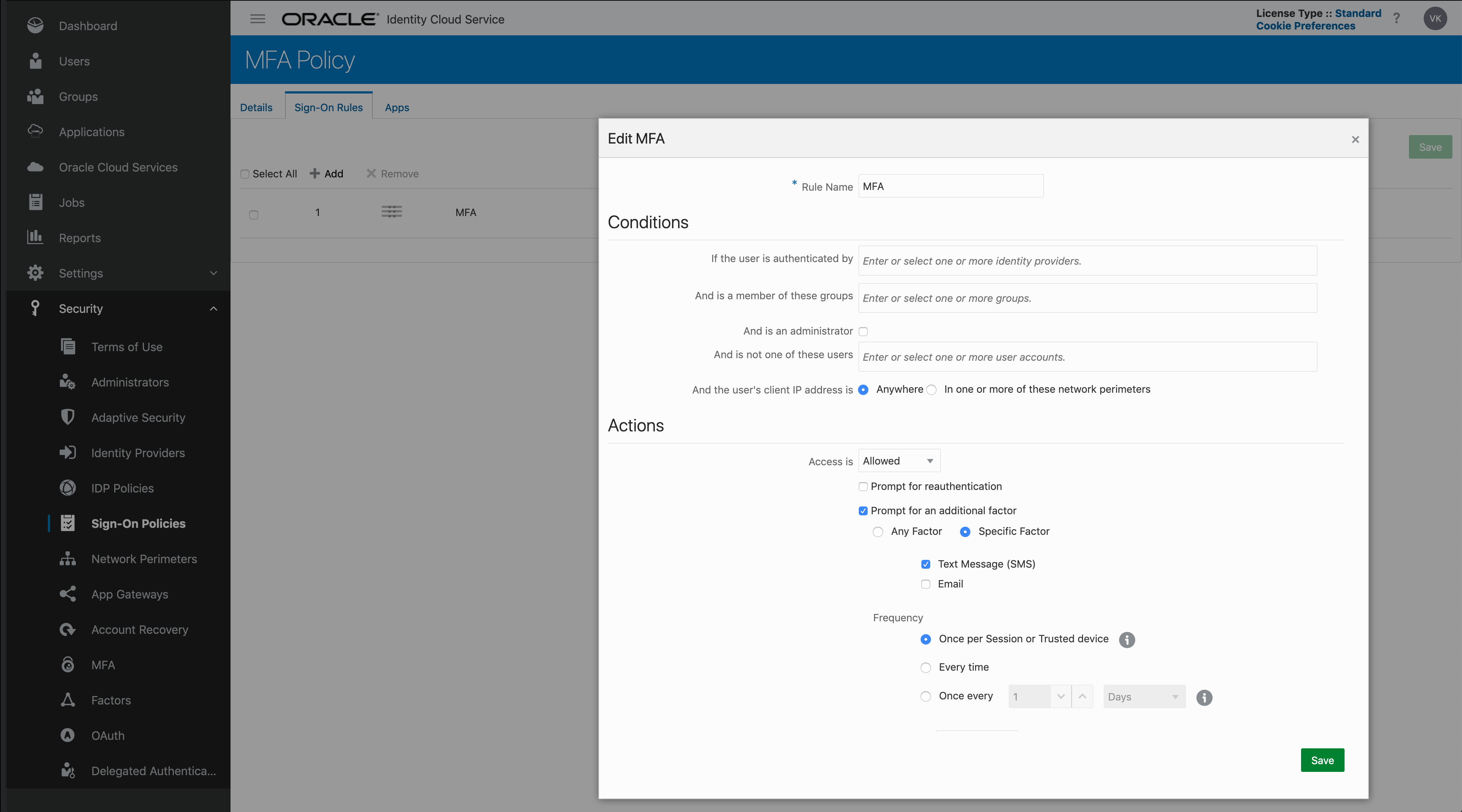
Here is the MFA (Sign-on) Policy with the Sign-On Rule you need to specify at minimum:
Don’t forget to add the application you created above to the Apps tab in the MFA (Sign-On) Policy:
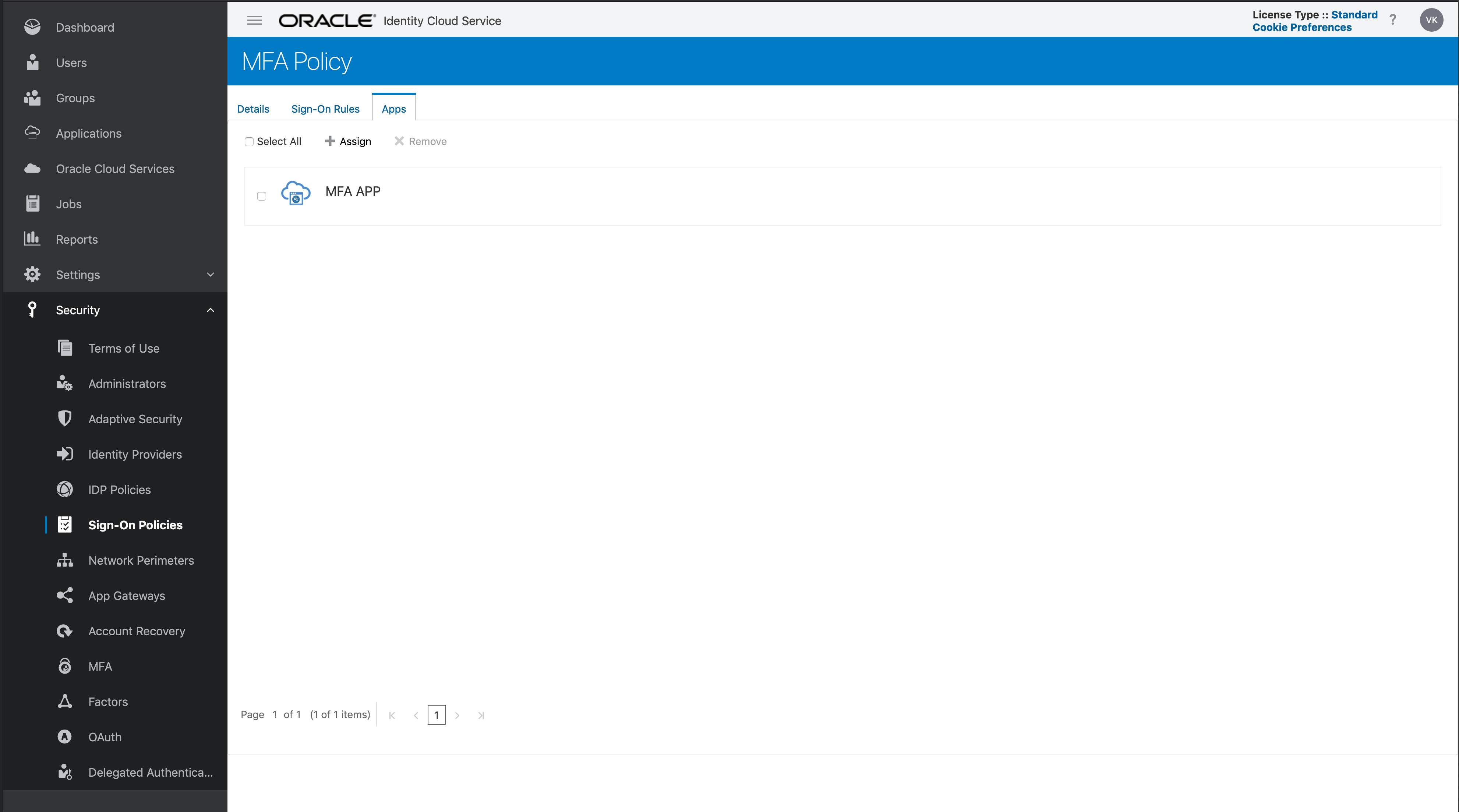
This completes the configuration. Now when I go to “/mfa” directly or after accessing “/private”, I will be prompted for MFA!
