I decided to write this blog post because I received multiple customer requests asking for differences between NSGs and SLs, where and when to use one or another or both and the best practices.
NSGs stands for Network Security Groups, a security mechanism that we have added to OCI few time back.
NSGs can be more granular in terms of security and can be used with or without Security Lists, You can follow the link from OCI public documentation to find more about NSGs vs SL: https://docs.cloud.oracle.com/iaas/Content/Network/Concepts/securityrules.htm
In the next part of the blog a case will be presented and includes both the NSGs and SLs implementing different security postures.
The Case
We have three servers in the same subnet in OCI: A (129.213.96.139), B (129.213.102.85), C (129.213.39.46). The request is:
a) All there servers to permit SSH on port TCP 22;
b) Only server A to allow ICMP;
Using only Security Lists is not possible to accomplish the above points because the ingress security entries from the Security List will be activated on all the vnics from the subnet. So, let’s introduce the NSGs.
The Security List associated with the subnet containing A,B,C servers has an entry to permit the SSH (all three servers will be served by this security entry):
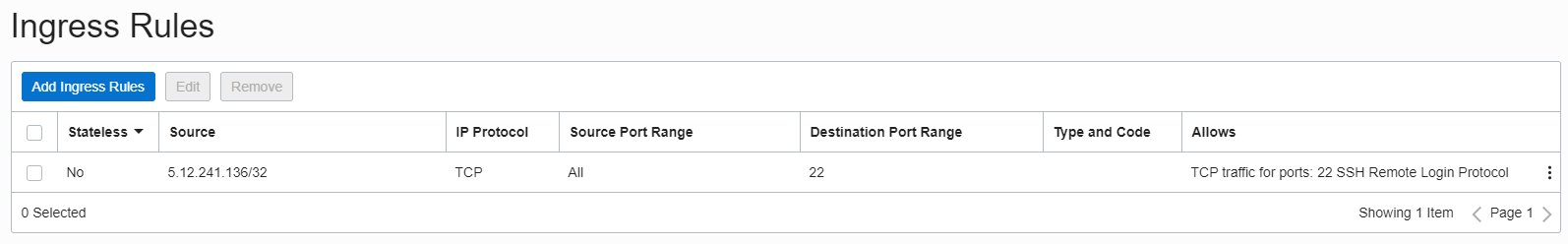
5.12.241.136 is the IP address permitted to access the three servers via SSH:
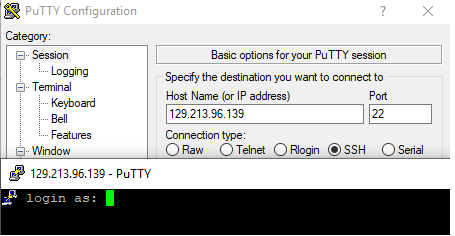
SSH to server A – connection accepted:
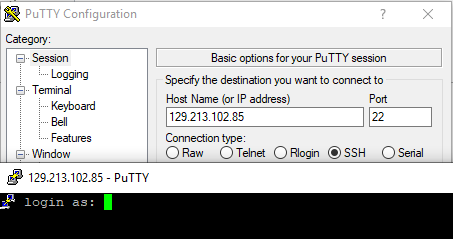
SSH to server B – connection accepted:
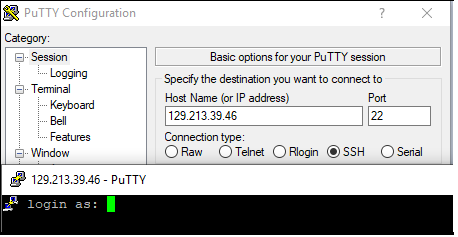
SSH to server C – connection accepted:
Using the security entry from the Security List associated with the subnet we have accomplished point a).
For point b) a Network Security Group is needed and include only the vnic of server A. In this NSG an ingress rule will be added to permit the ICMP from 5.12.241.136:
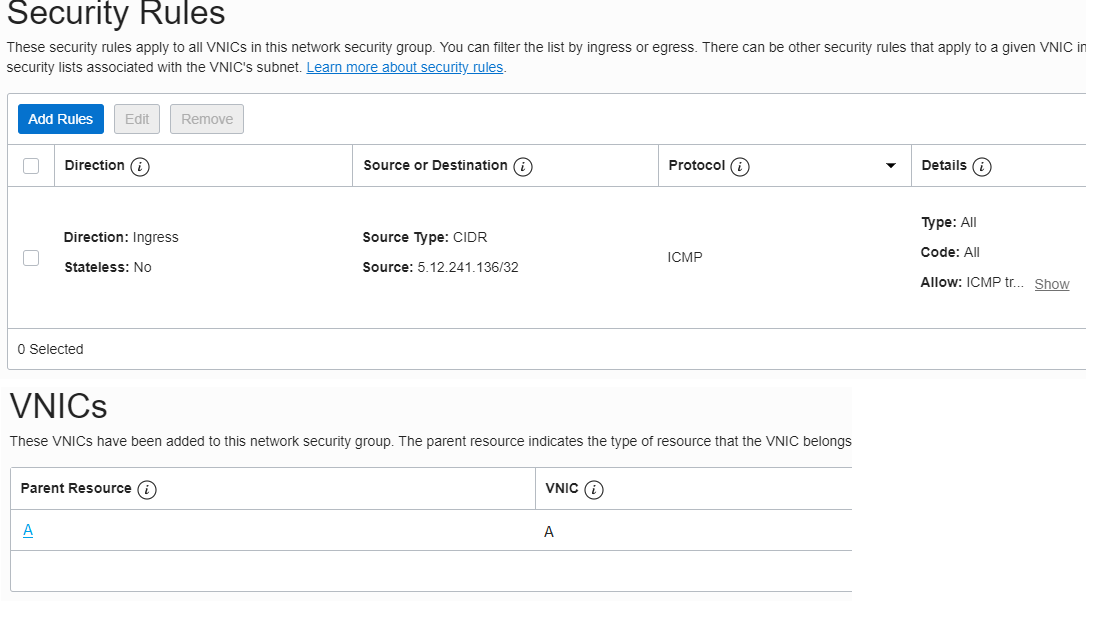
If we try to ping all the three servers the ICMP will be successful only to server A:
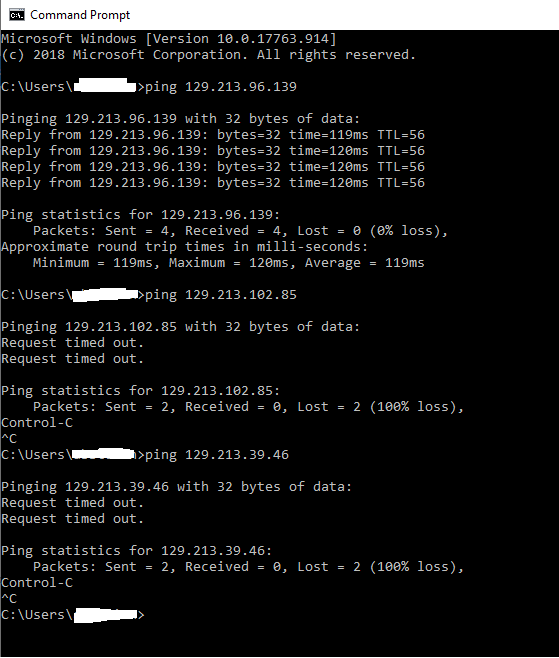
We have accomplished also point b) and we have solved the case.
There is not an issue if we used Security Lists in the first place. We can add NGS in the picture with the observation that if we want to have a granular filtering we need to make sure that a specific security entry that needs to be applied on a specific server or group of servers in the same subnet exists only as a rule in the NSG and not in the Security List associated with the subnet.
On the other hand the NSGs can be used also between subnets or matching a specific service like OCI Object Storage or all services from Oracle Services Network.
NSGs will give the ability create a more granular security between On-premise and OCI or inside the cloud VCN and from this reason the preferred method is to use the NSGs as much as possible.
