In this blog post, we will explore the possibility to create an IPSec tunnel (or redundant IPSec tunnels, if we configure two separate VPN Connections) using the built-in VPN Services offered by the two Cloud Providers.
OCI is not offering the possibility to update a particular VPN Connection by changing the CPE (Customer-premises Equipment) used. AWS can update the CPE used for a given VPN Connection and thus, we will rely on this function to be able to create the IPSec tunnel to OCI.
In order for a better reading of the blog, we need to be familiar with VPN Connections implemented by OCI and AWS, even if the step-by-step procedure will be listed in the following sections.
VPN Service offered by OCI: https://docs.oracle.com/en-us/iaas/Content/Network/Tasks/managingIPsec.htm
VPN Service offered by AWS: https://aws.amazon.com/vpn/
Network Topology
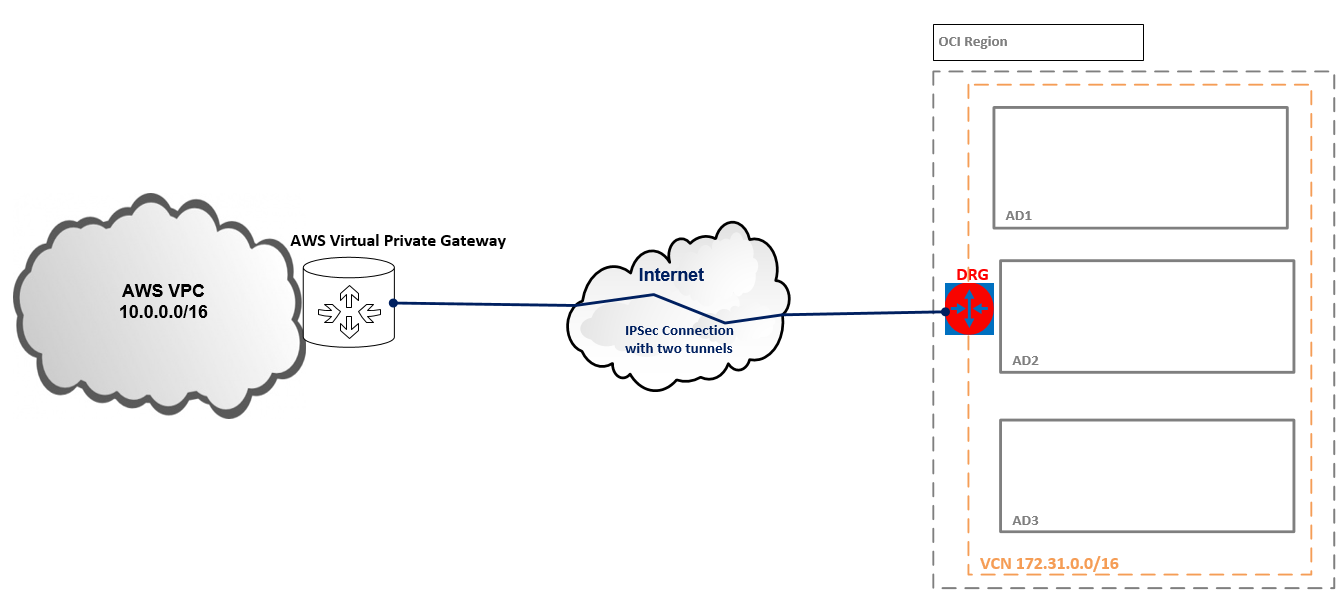
As we know, an IPSec Connection is formed by two IPSec tunnels. When both IPSec tunnels in the same IPSec Connection are configured and in the UP state, redundancy is achieved. In our example, we will be able to configure just one IPSec tunnel in the Connection. In order to have redundancy, a new IPSec Connection needs to be created and configure another IPSec tunnel between AWS and OCI.
A normal question at this step would be, why I can configure just one IPSec tunnel in the connection and not both? The answer is the following, when defining a CPE in either OCI or AWS and creates an IPSec Connection, two public IP addresses will be delivered to the CPE to configure the two IPSec tunnels. So, the CPE will be able to create two IPSec tunnels with the two public IP addresses delivered by the two Cloud Providers for redundancy. In our case, the remote end will not be a real CPE, but another Cloud Provider having the same approach of building the VPN Connections. Actually the CPE created in OCI defining the AWS CPE and vice-versa will represent a public IP from the two public IPs forming the VPN Connection and not standalone CPE as we will have On-Premise.
Let’s see the configuration in action and how we can achieve an IPSec tunnel in the UP state.
AWS Configuration
Note: In this example, we will configure one IPSec tunnel using static routes. BGP over IPSec is also supported on both, OCI and AWS.
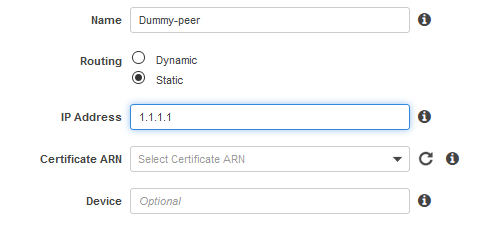
1. Define a dummy IPSec peer – this will not be the real OCI peer, it will help us obtain the public IPs from the AWS side to define the CPE in OCI and create the IPSec Connection. Later, we will define the real OCI peer IP address in AWS once we will obtain the public IP address from OCI.
Navigate to Customer Gateways and create the IPSec dummy peer, below I used 1.1.1.1 as a public IP address (AWS is not accepting private IPs for defining the IPSec CPEs):
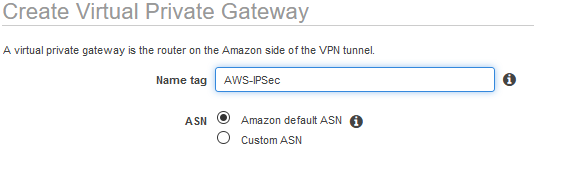
2. Navigate to Virtual Private Gateways and create the Virtual Private Gateway:
3. Attach the VPG to the VPC you are using:
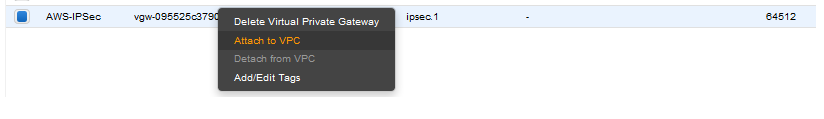
4. Navigate to Site-to-Site VPN Connections and create the IPSec connection between the VPG at step 2 to the Dummy-peer at step 1:
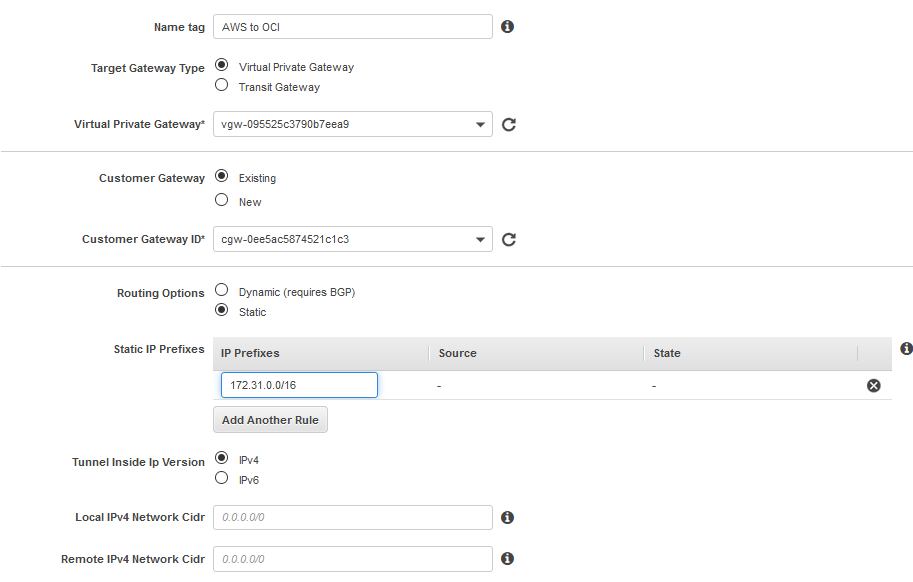
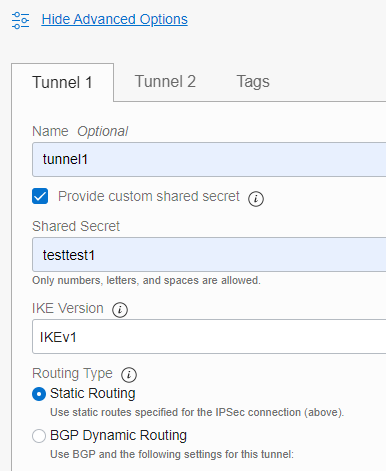
AWS is letting you create your own IPSec pre-shared-key. For the sake of simplicity, I used for the IPSec tunnel that we will configure testtest1 as a pre-shared-key. Please make sure in your production IPSec tunnels you are using a strong pre-shared-key.
Under Edit Tunnel 1 Options, pick the parameters you want for Phase 1 and Phase 2 based on OCI is supported parrameters (https://docs.oracle.com/en-us/iaas/Content/Network/Reference/supportedIPsecparams.htm) :
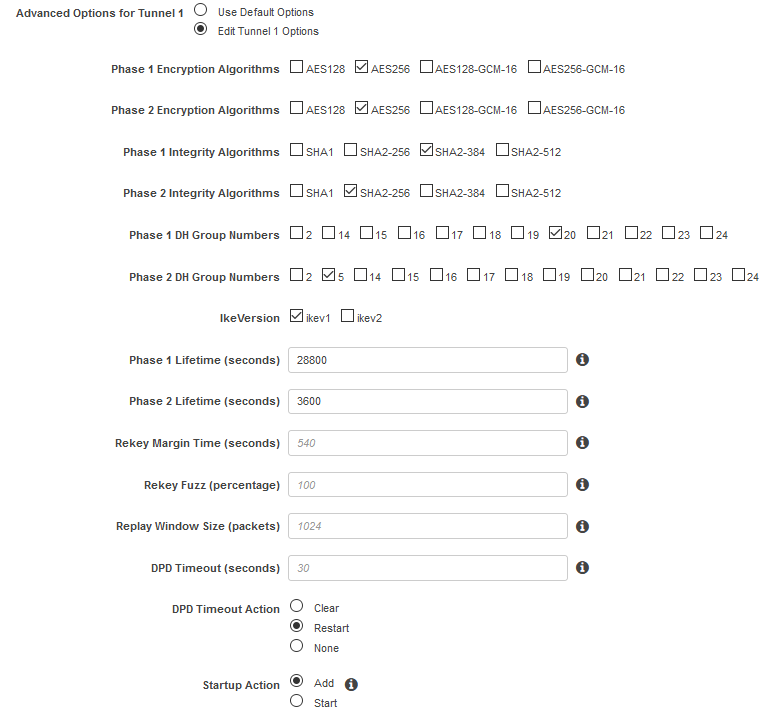
Note: Startup Action set to Add means that AWS will wait for the IPSec tunnel to be initiated by the peer. In our example, we will let OCI initiate the IPSec tunnel negotiation once the configuration is done.
5. Wait for the VPN Connection to enter the available state and download the configuration:
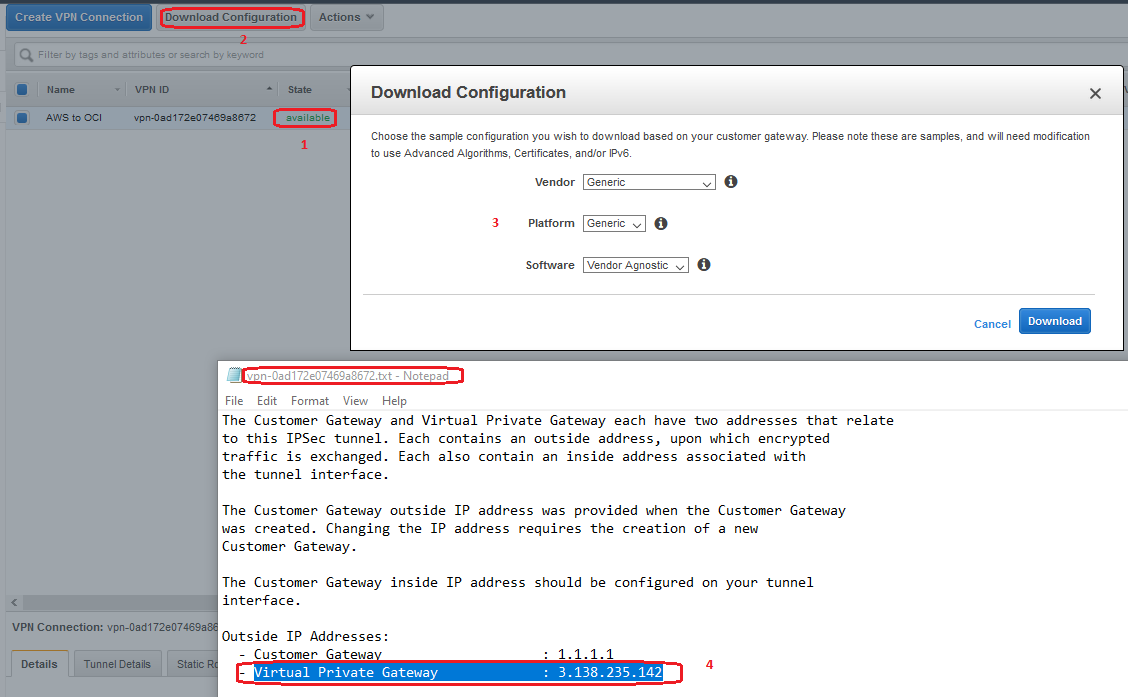
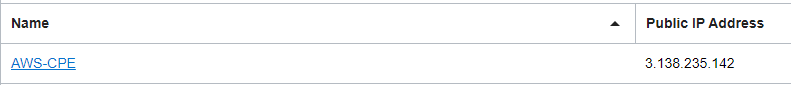
Downloading the configuration, we can find the two public IP addresses of the IPSec tunnels forming the IPSec Connection. Using 3.138.235.142 we will define the CPE on the OCI side and create the IPSec Connection.
6. This step will be performed ONLY after OCI Configuration is completed
Define the IPSec peer with the correct public IP address:
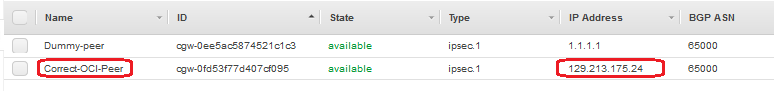
7. This step will be performed ONLY after OCI Configuration is completed
Modify the VPN Connection to peer with the OCI public IP address defined at step 6:
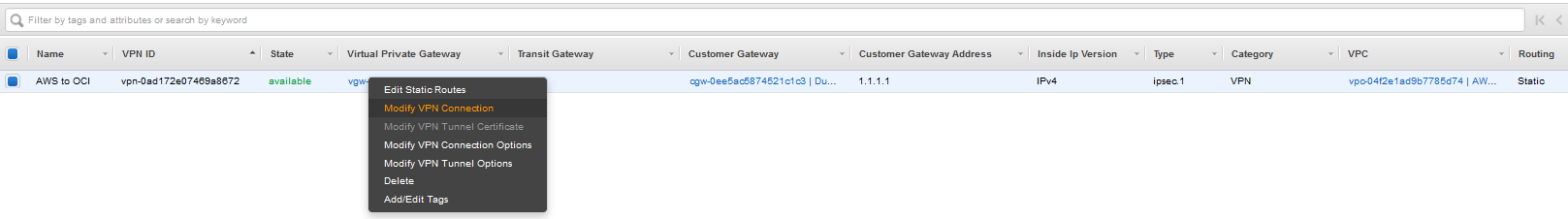
Under Change Target pick Customer Gateway and select the OCI peer CPE:
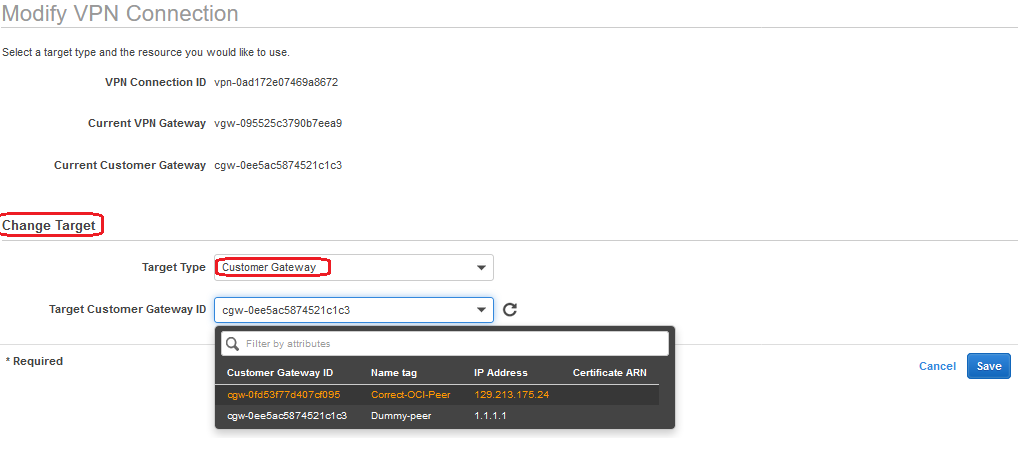
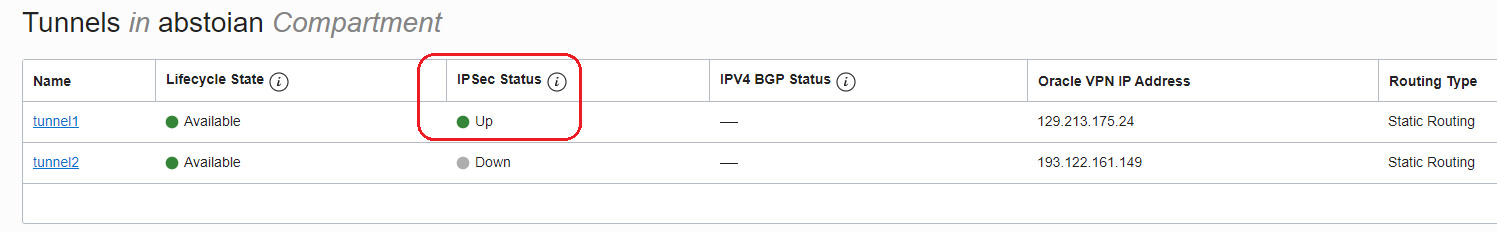
After saving the configuration wait for the VPN Connection to return to available state. At this moment your IPSec tunnel should reach the UP state.
OCI Configuration
1. Navigate to Networking -> Customer-Premises Equipment and define the CPE:
2. Create the IPSec Connection between the DRG you have attached to the VCN and the above CPE:
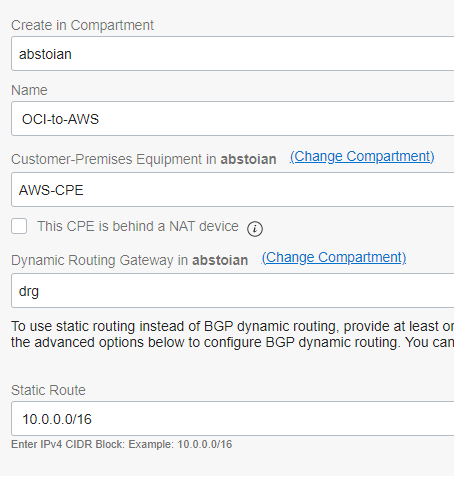
Define the pre-shared-key to be identical with the pre-shared-key on the AWS side:
The IPSec Connection that results from the configuration:
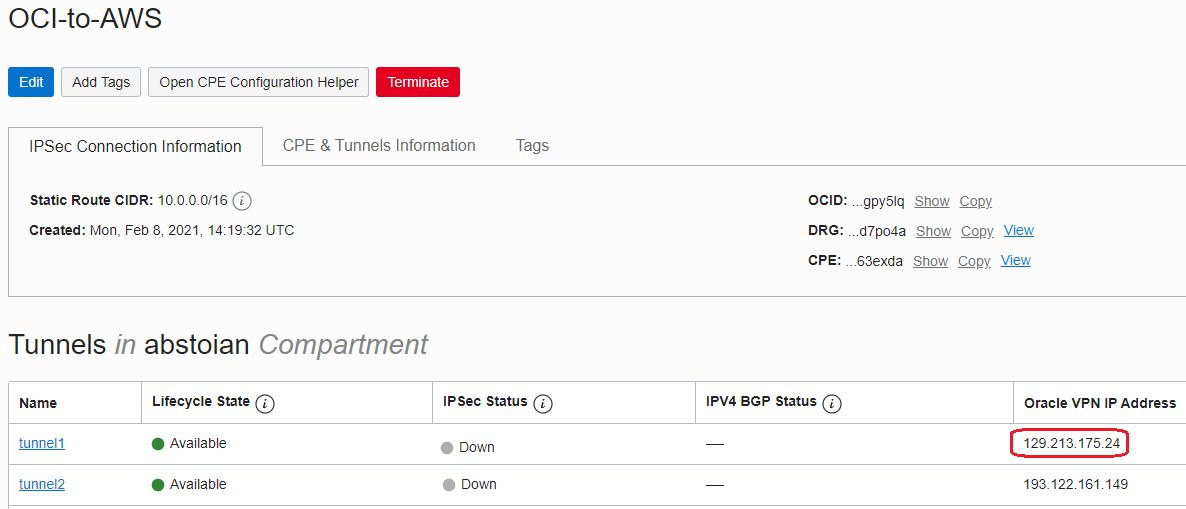
We will return in the AWS console now to configure the correct VPN peer at 129.213.175.24 and update the VPN Connection in AWS to peer with OCI.
IPSec Tunnel status verification
AWS
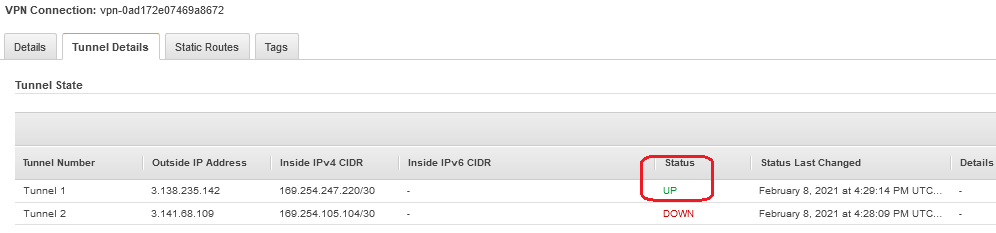
OCI