Palo Alto – Hub & Spoke architecture – Part 1/2
Overview
The purpose of this document is to help in configuring Palo Alto for a Hub & Spoke architecture on Oracle Cloud Infrastructure (OCI). Basic OCI and Palo Alto experience is recommended. This document will not cover how to install Palo Alto from OCI Marketplace. This document will contain 2 parts.
This configuration was validated using Palo Alto version 9.1.1.
For more details on how to use Palo Alto products, please visit Palo Alto official website – https://docs.paloaltonetworks.com.
Palo Alto VM in Hub & Spoke architecture – Configuration
Step by step
Step 1. Solution description.
Step 2. Prerequisites for Palo Alto and OCI.
Step 3. Configuring OCI.
Step 1. Solution description.
There are customers that want to user 3rd party firewall vendors instead of using native cloud firewall capabilities. There are multiple reasons for wanting this, like more advanced features that are not available at this moment or they already use that specific vendor in their own Data Centers. For this document, we will cover Palo Alto and their Palo Alto Networks VM-Series solution.
There are different network topologies and each client choses the right one based on they need. In this document, we will cover the Hub & Spoke network topology.
This topology it’s used for different scenarios, like:
- FastConnect or IPSec VPN from on-prem to OCI.
- Private access to Oracle Service Network (OSN).
- WAN access.
- North-South or East-West traffic filtering.
OCI provides a native solution for a Hub & Spoke network topology by using a feature called Transit Routing.
This will allow to do the following:
- Access to multiple VCNs in the same region: The scenario covered in this topic. This scenario enables communication between your on-premises network and multiple VCNs in the same region over a single FastConnect private virtual circuit or VPN Connect.
- Private access to Oracle services: This scenario gives your on-premises network private access to Oracle services, so that your on-premises hosts can use their private IP addresses and the traffic does not go over the internet.
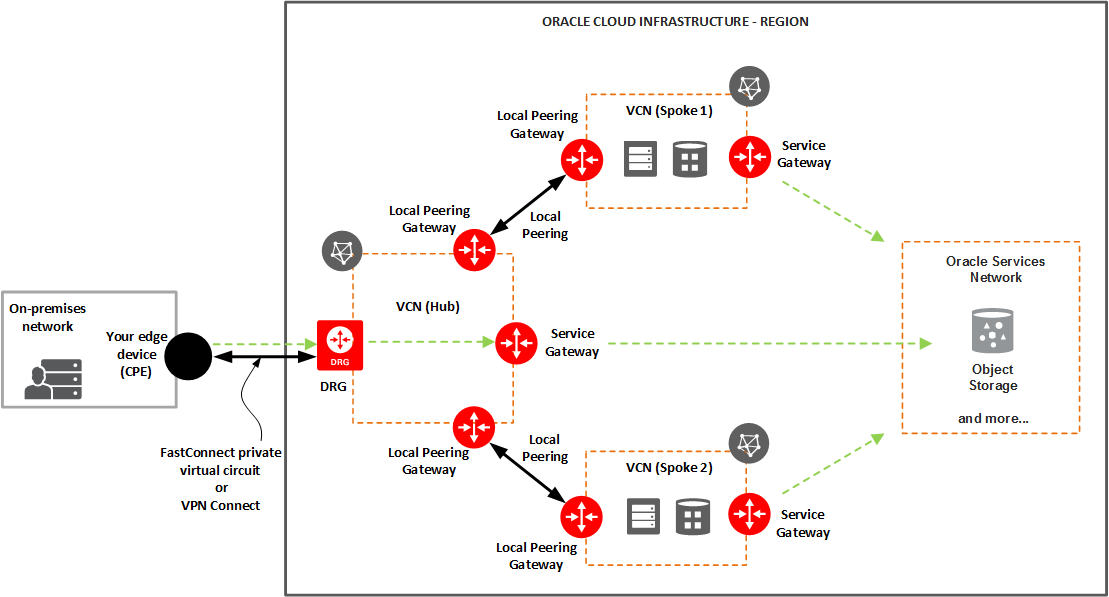
Diagram 1 – Access to multiple VCNs in the same region and to OSN
For more information about Transit Routing feature check OCI website – https://docs.cloud.oracle.com/en-us/iaas/Content/Network/Tasks/transitrouting.htm and https://docs.cloud.oracle.com/en-us/iaas/Content/Network/Tasks/transitroutingoracleservices.htm.
We will use the network topology above (Diagram 1) to integrate Palo Alto Networks VM-Series as a firewall appliance.
In the end, the entire solution will accomplish the following:
- Dedicated Management interface.
- Control traffic in and out for WAN or on-prem.
- Control traffic from Spoke to Hub.
- Control traffic from Spoke to Spoke.
- Control traffic from Hub or Spoke to OSN.
- Control traffic from Spoke to On-prem.
Step 2. Prerequisites for Palo Alto and OCI.
Based on Diagram 1, the final solution using Palo Alto Networks VM-Series will look like this:
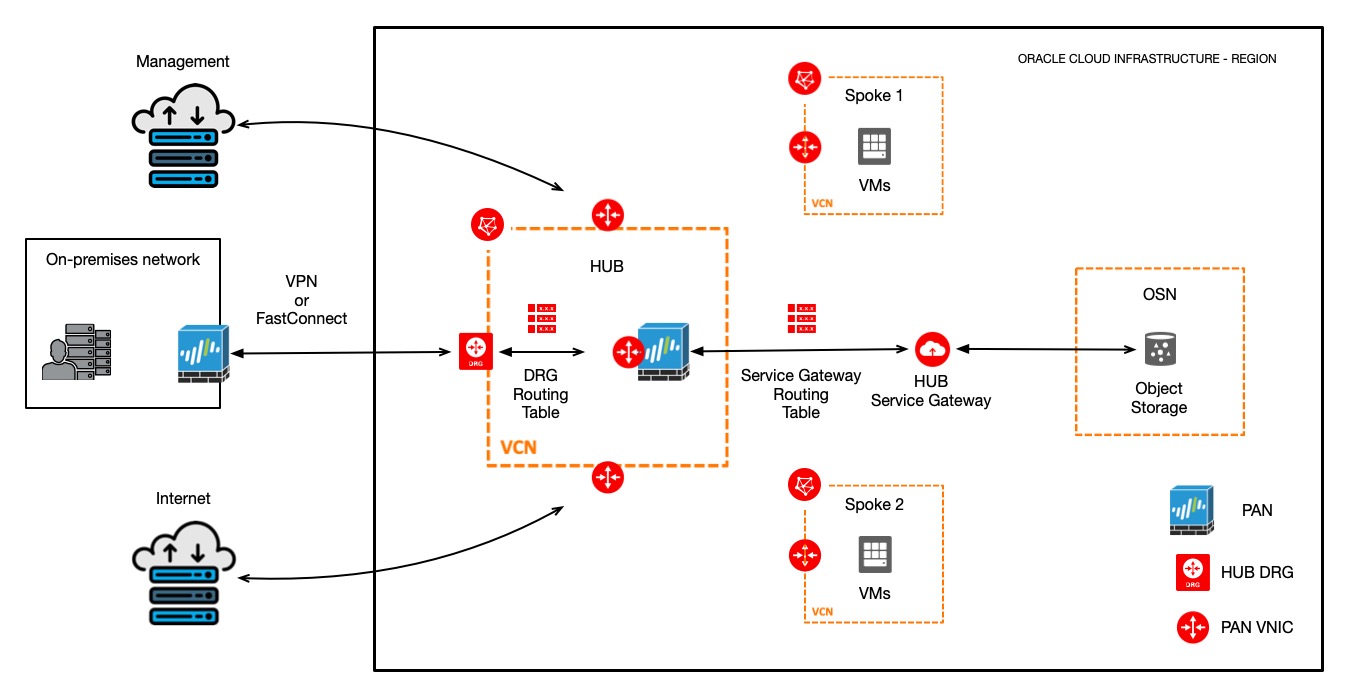
Diagram 2 – Final solution using Palo Alto Networks VM-Series
Keep in mind that there are multiple ways to create a Hub & Spoke networking topology. As an example, we can use LPGs between VCNs and use fewer network interfaces on Palo Alto Networks VM-Series.
For building a HA environment using Palo Alto Networks VM-Series, please check this blog page – https://www.ateam-oracle.com/palo-alto-vm-series-ha-deployment-in-oci.
Our scenario covers Palo Alto Networks VM-Series using multiple network interfaces, eliminating the need to use an LPG. This can involve a bigger cost associated (licensing + multiple OCPUs) but can improve the overall performance.
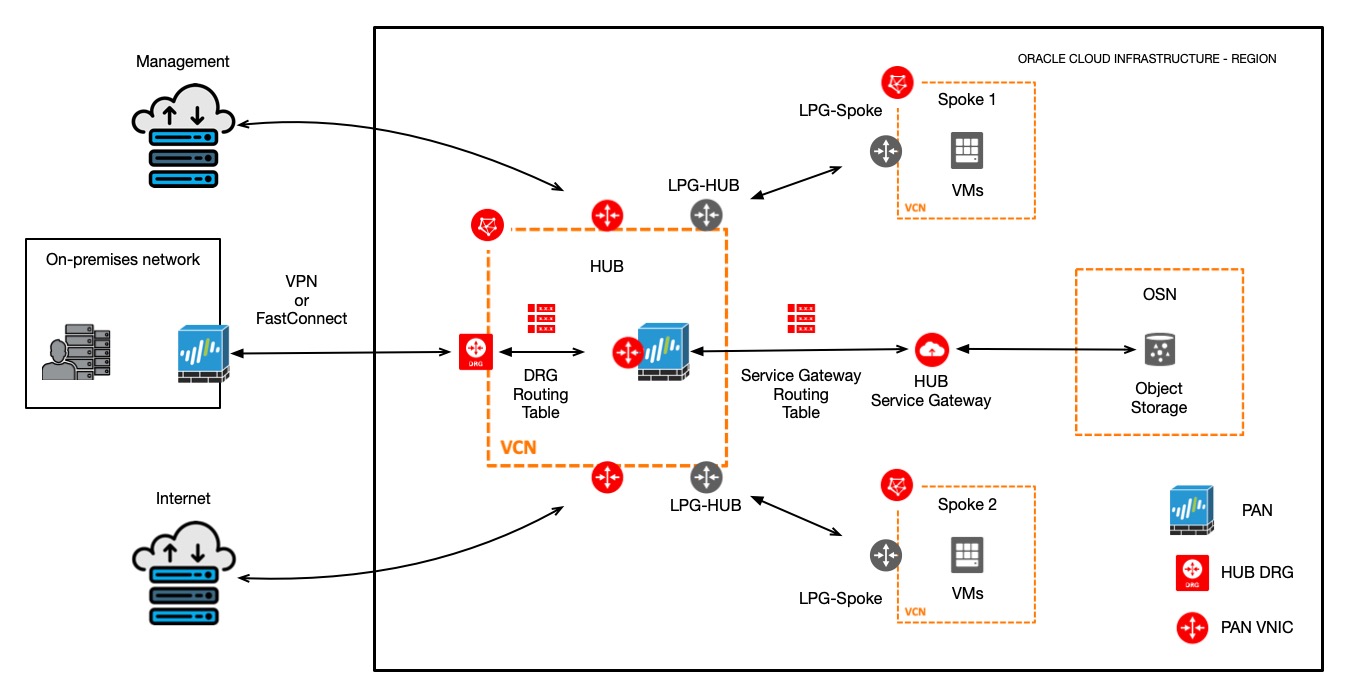
Diagram 3 – Palo Alto Networks VM-Series using LPGs
Palo Alto Networks VM-Series prerequisites:
For this configuration we will need 5 VNICs attached to Palo Alto Networks VM-Series. Interfaces will be used for the following:
- Management interface
- Internet interface
- OSN & On-premises interface
- Spoke 1 interface
- Spoke 2 interface
OCI prerequisites:
For this configuration we will need the following:
- 3 VCNs (HUB, Spoke 1, Spoke 2)
- HUB VCN will contain the following objects:
- 1 DRG
- 1 Service Gateway
- 1 Internet Gateway
- 3 Subnets
- 1 Subnet for Management access
- 1 Subnet for Internet access
- 1 Subnet for OSN & On-premises access
- 5 Routing Tables
- 1 Routing Table for Management access
- 1 Routing Table for Internet access
- 1 Routing Table for OSN & On-premises access
- 1 Routing Table for DRG
- 1 Routing Table for Service Gateway
- Spoke 1 & 2 VCN will contain the following objects:
- 1 Subnet for each VCN
- 1 Routing Table for each VCN
For this exercise, we will use the default security lists created with the VCNs. These will contain only one stateful rule for ingress and egress with 0.0.0.0/0 permitting All protocols. The intent is to filter everything using Palo Alto Networks VM-Series policy security rules. You also have the option to add additional security by filtering at Palo Alto Networks VM-Series instance and at the OCI level.
Step 3. Configuring OCI.
3.1 Create VCNs
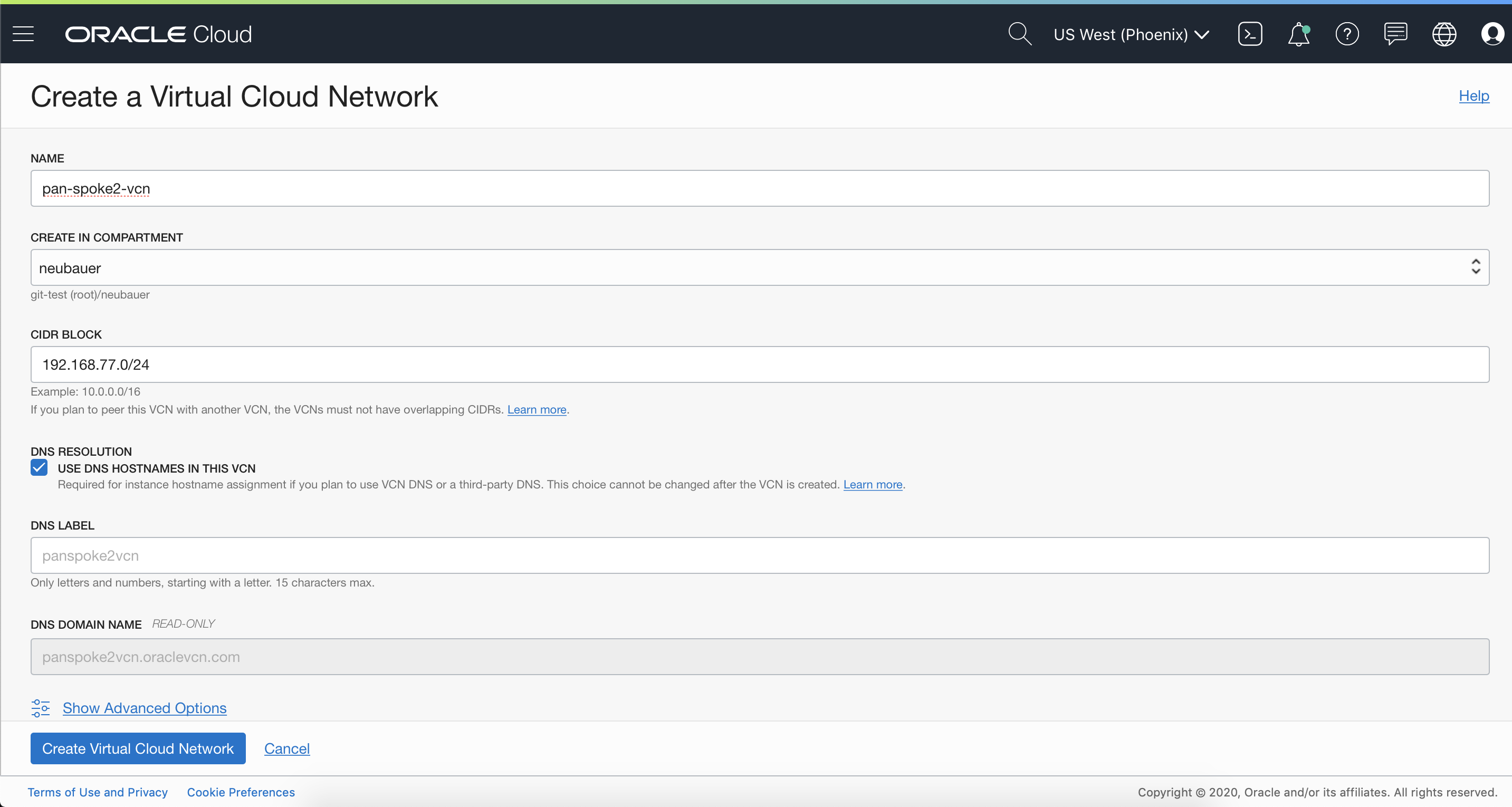
Before starting and installing the Palo Alto Networks VM-Series VM appliance, we need to create the networking infrastructure based on the requirements above. From the OCI Console, go to Networking and select Virtual Cloud Networking. Select “Create a Virtual Cloud Network” button. Add the necessary details for creating the VCN. Example:
3.1.1 HUB-VCN

3.1.2 Spoke 1 VCN

3.1.3 Spoke 2 VCN
3.2 Create 3 subnets in the HUB VCN
Inside the VNC, click on the “Create Subnet” button. Add the necessary details for creating the Subnet. Example:
3.2.1 HUB-Management Subnet
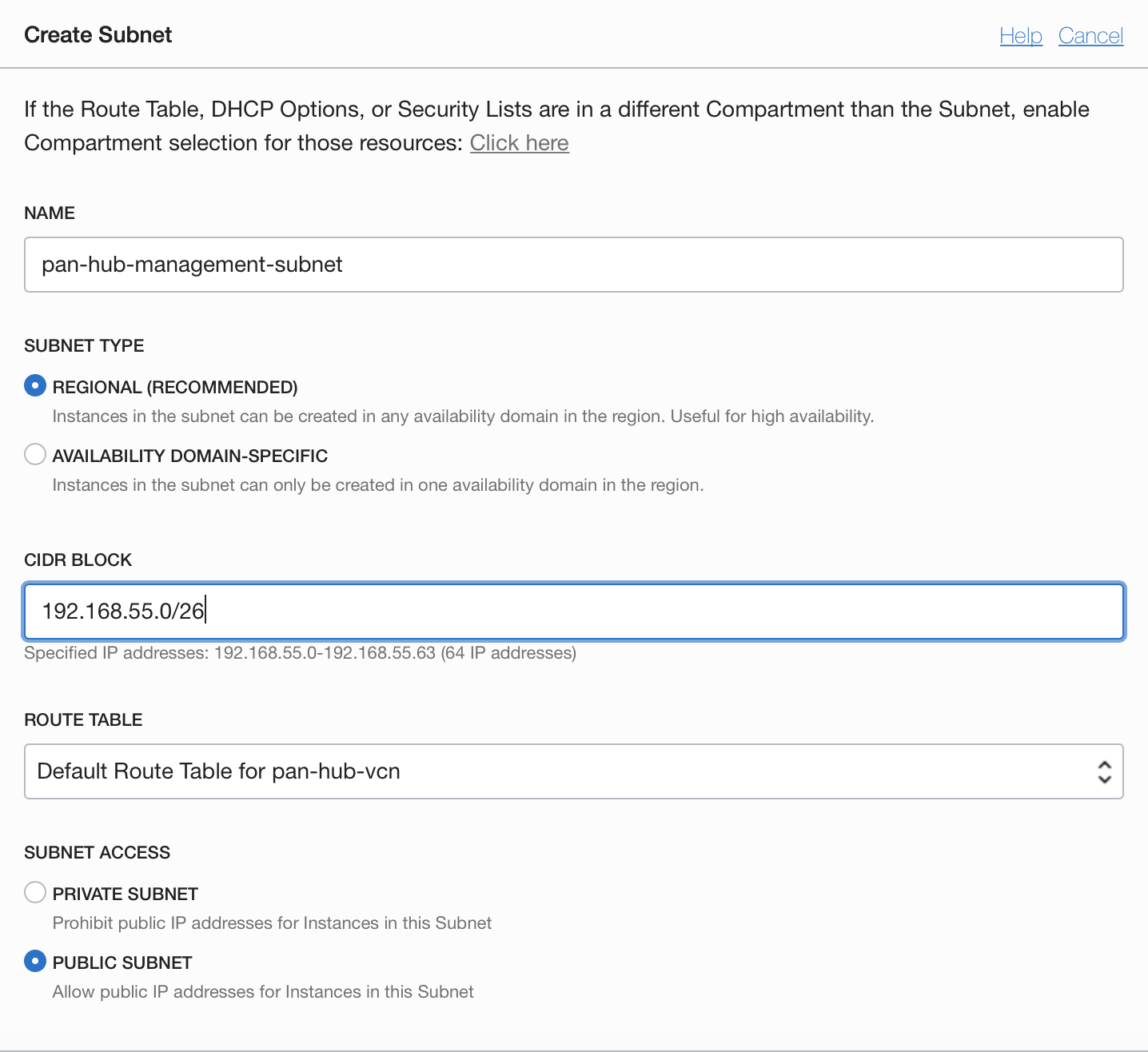
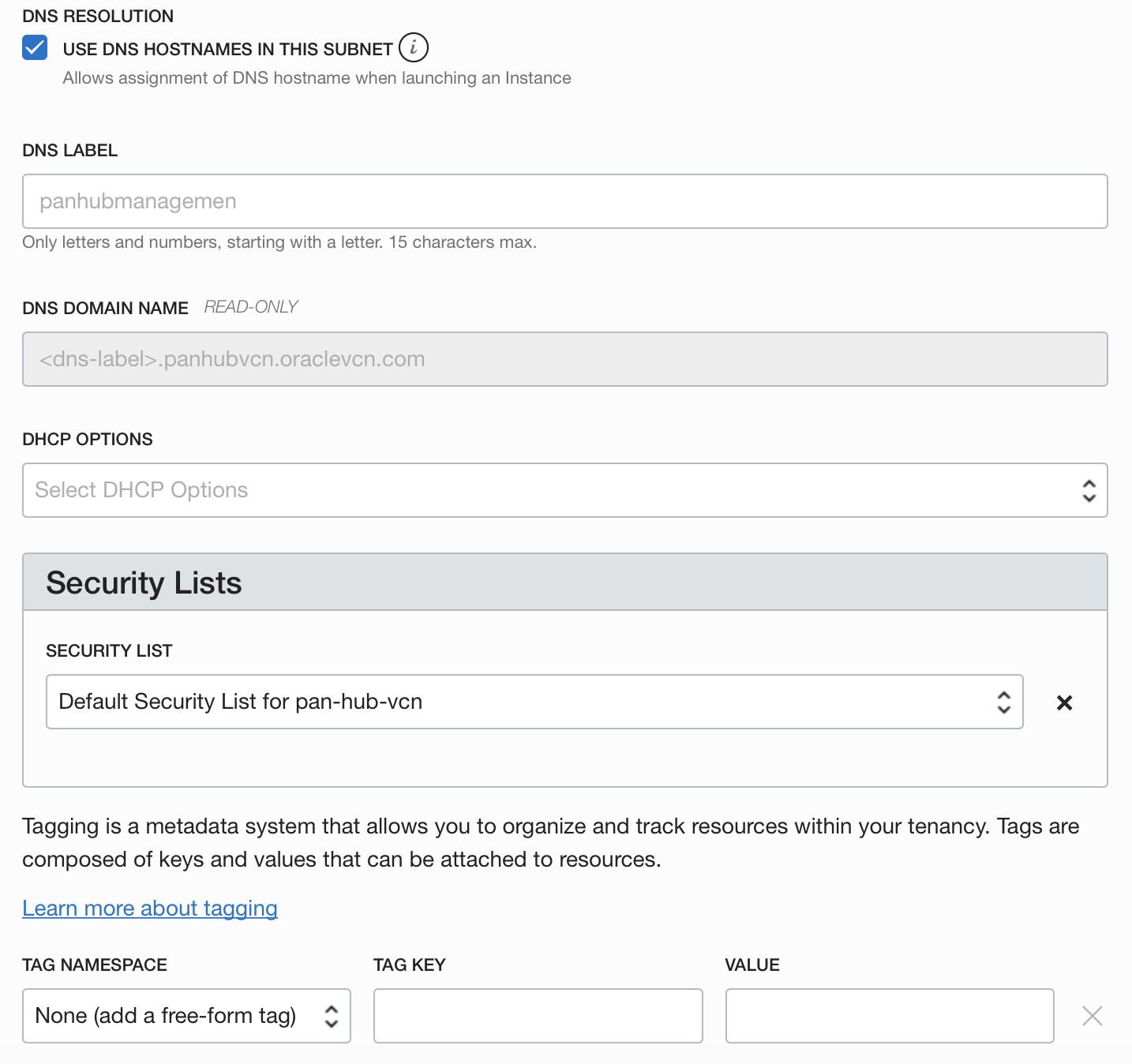

3.2.2 HUB-Internet Subnet
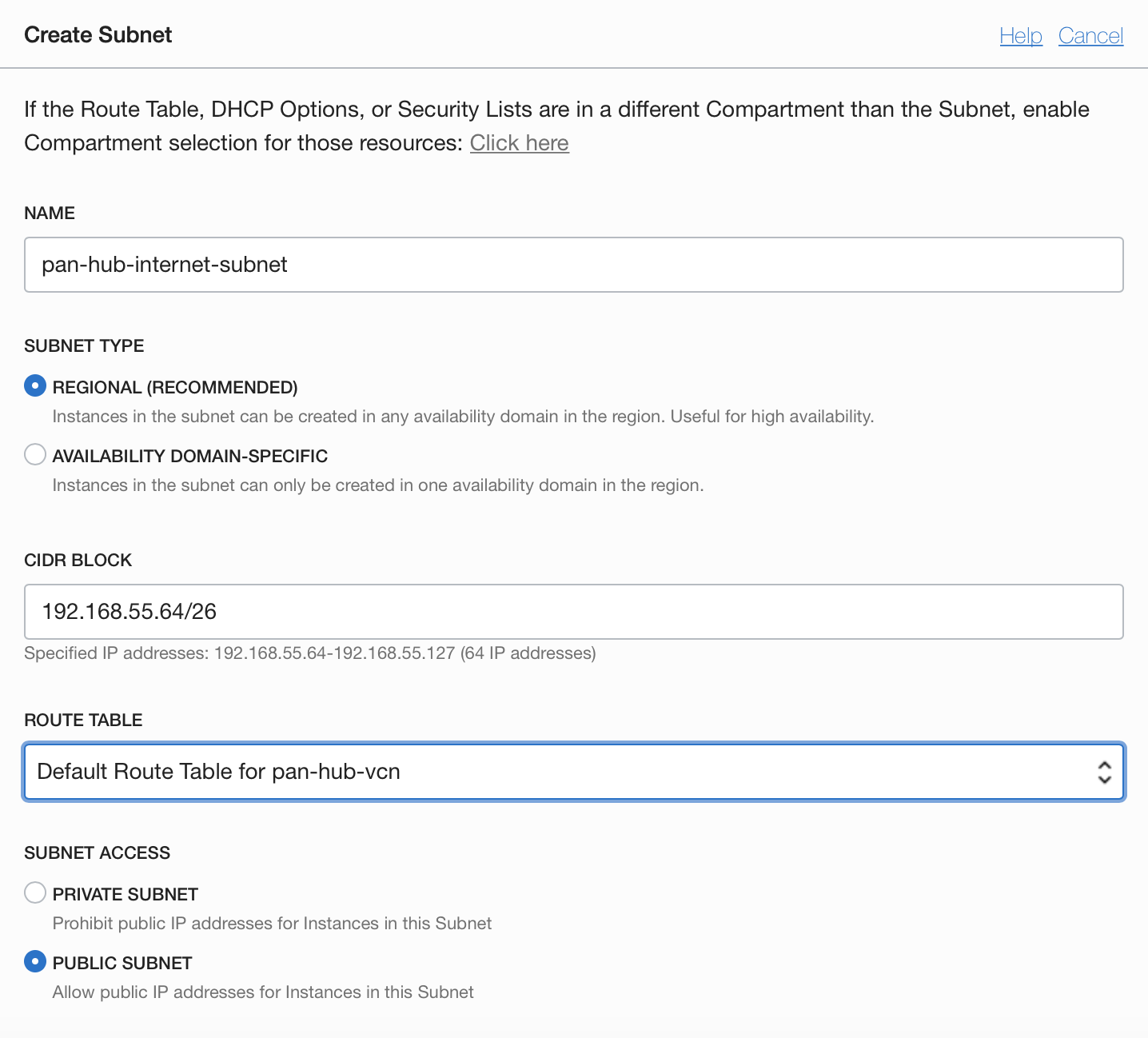
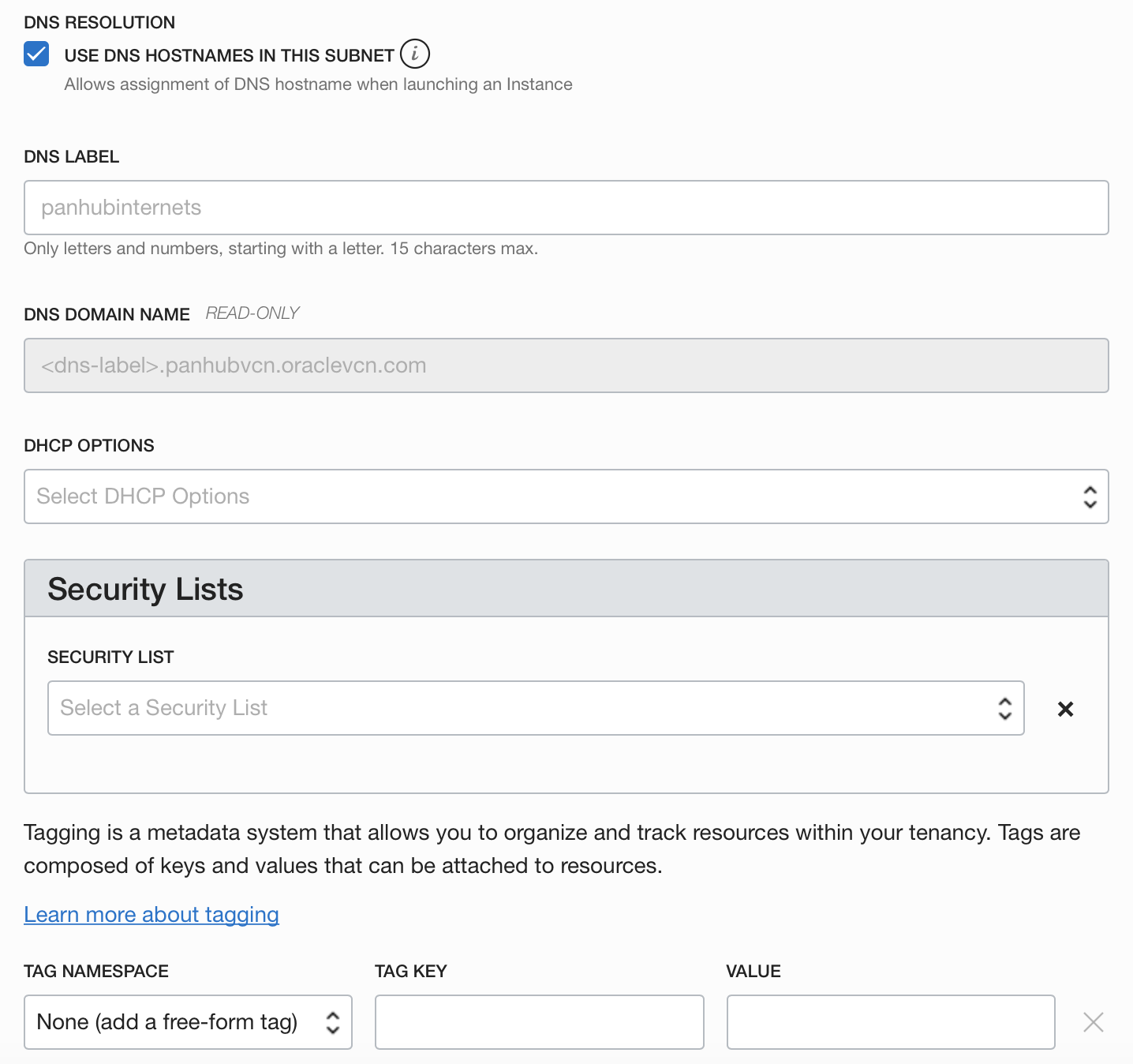

3.2.3 HUB-OSN-and-ON-PREM Subnet
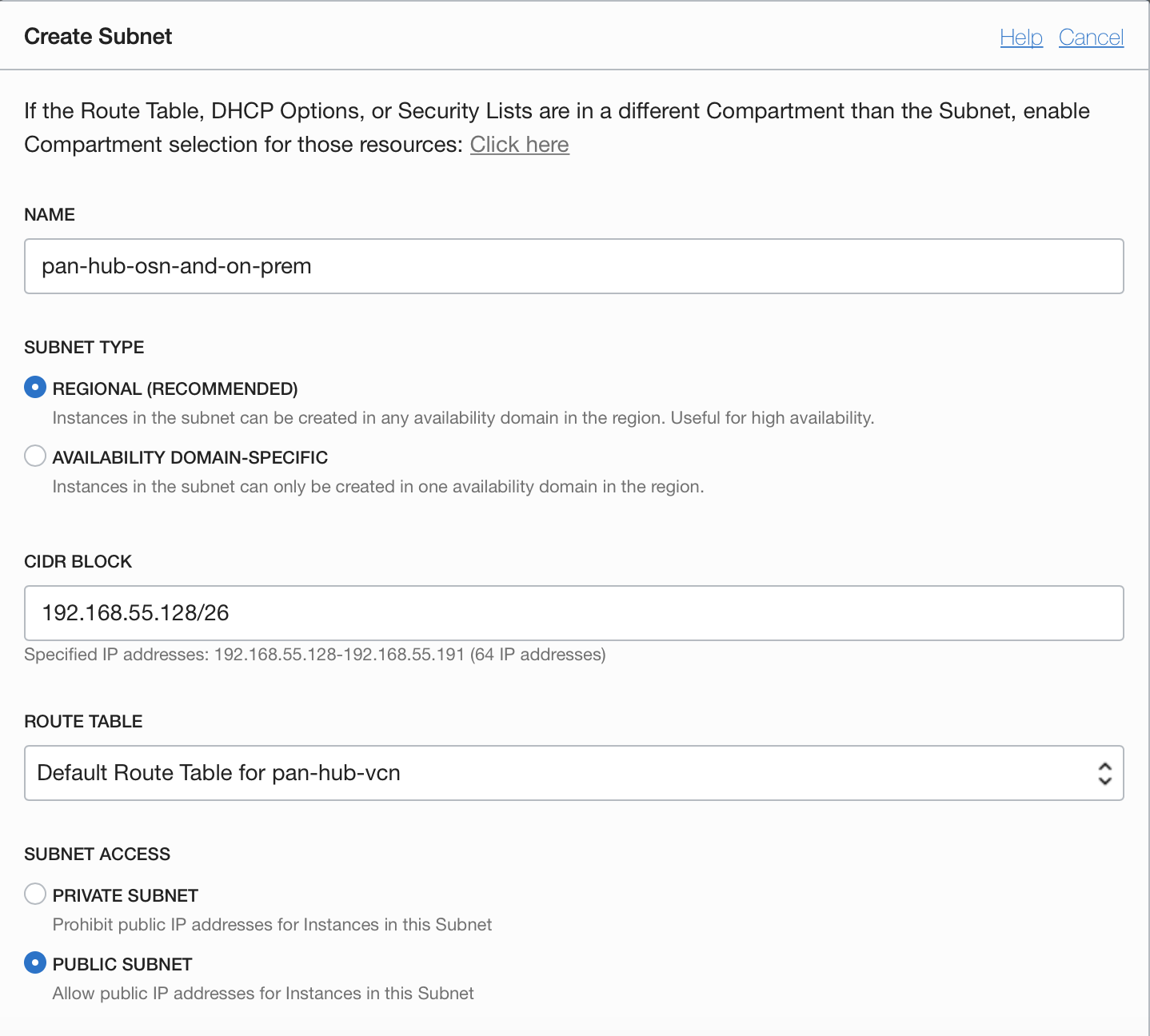

3.3 Modify the security list for HUB VCN to permit all traffic for ingress and egress.
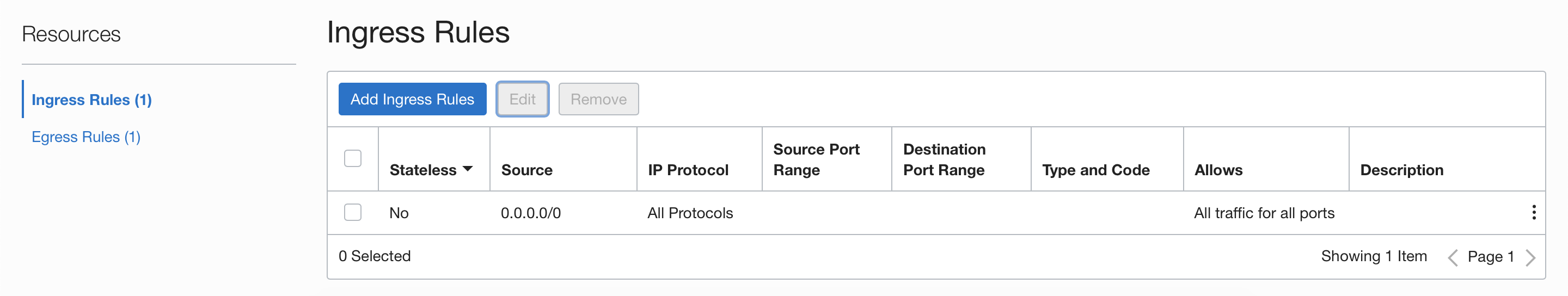
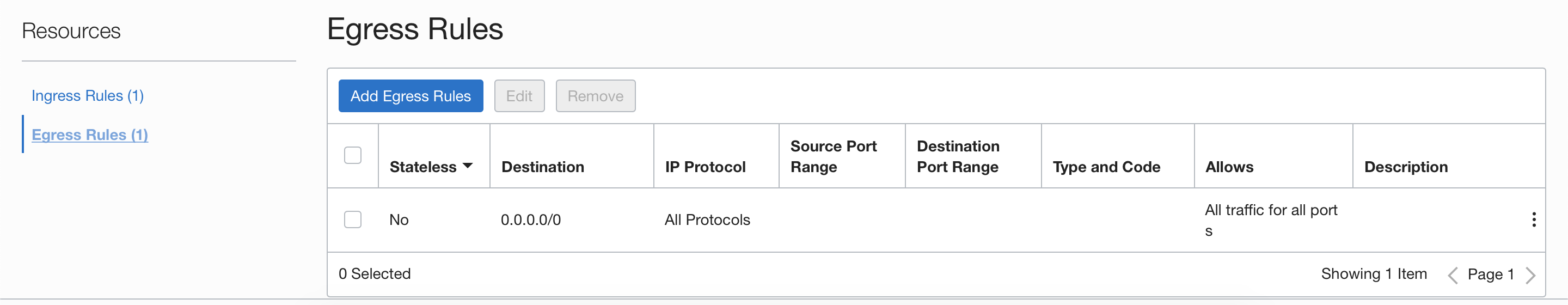
For this exercise, we will use the default security lists created with the VCNs. These will contain only one stateful rule for ingress and egress with 0.0.0.0/0 permitting All protocols. The intent is to filter everything using Palo Alto Networks VM-Series policy security rules. You also have the option to add additional security by filtering at Palo Alto Networks VM-Series instance and at the OCI level.
3.3.1 Ingress Security Rules
3.3.1 Egress Security Rules
3.4 Create Internet Gateway and Service Gateway in HUB VCN
3.4.1 Internet Gateway
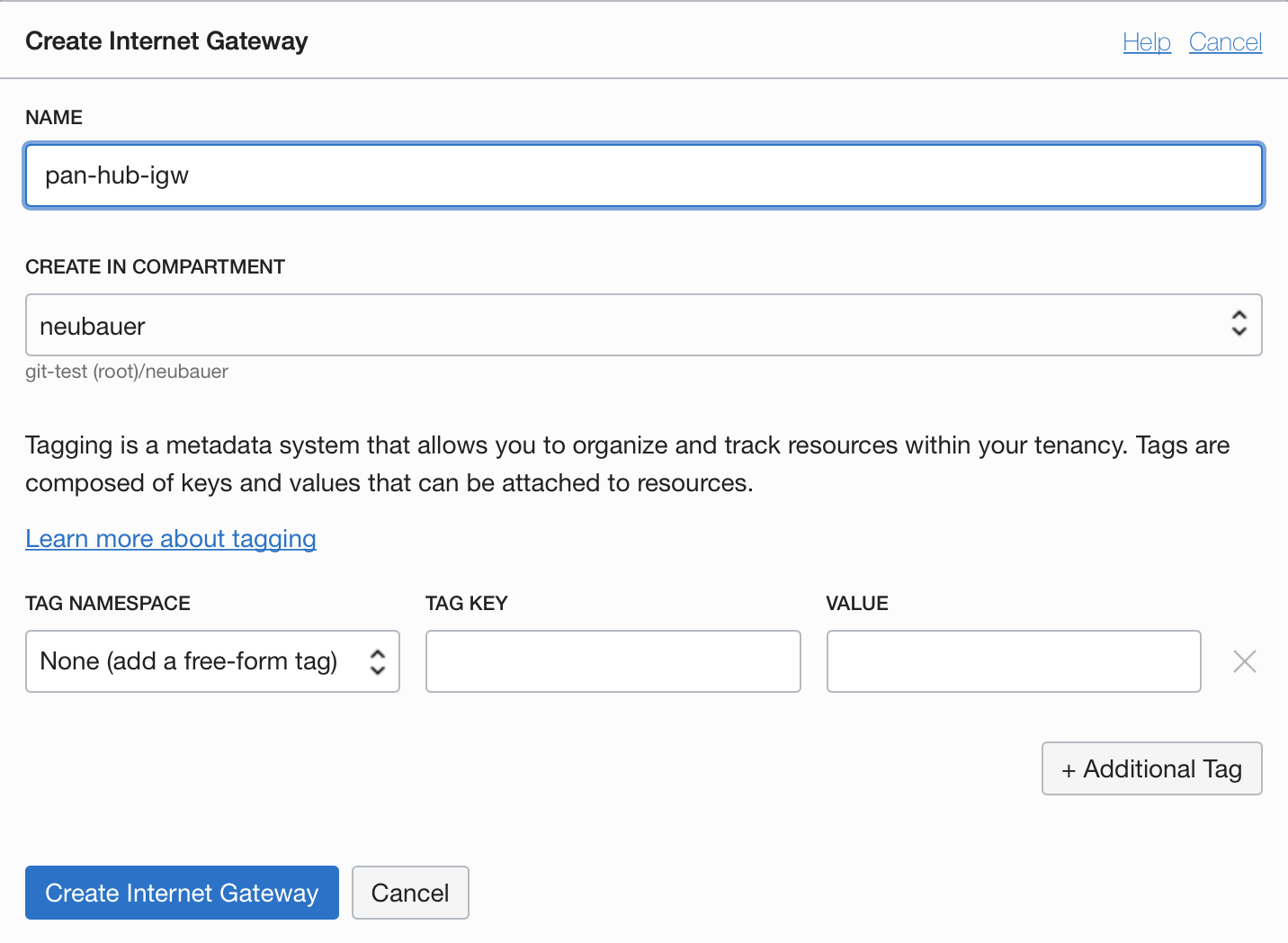
3.4.2 Service Gateway with Object Storage access

3.5 Create DRG and attach it to the HUB VCN
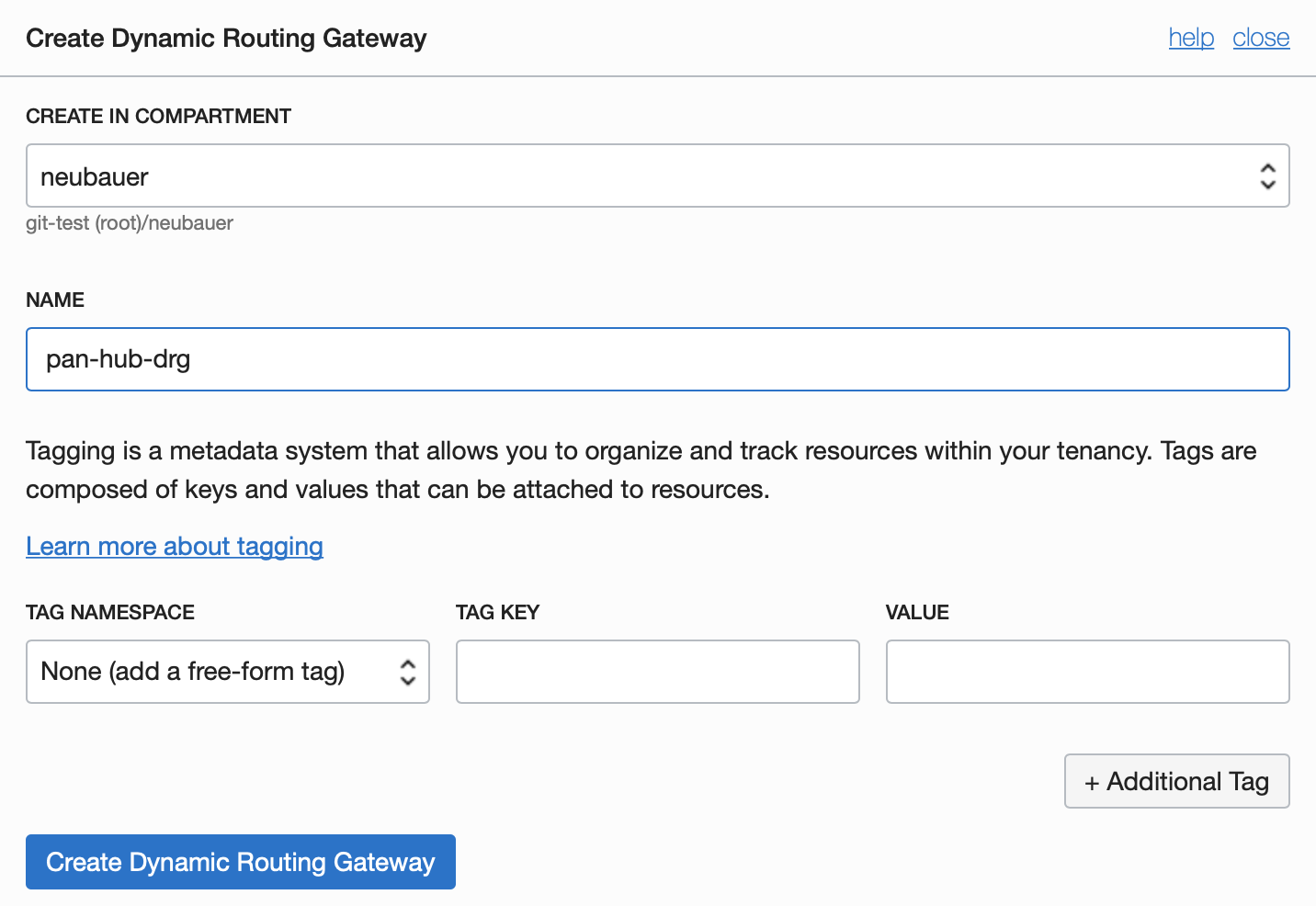
3.5.1 Create DRG
To create a DRG go to Networking and select Dynamic Routing Gateways.
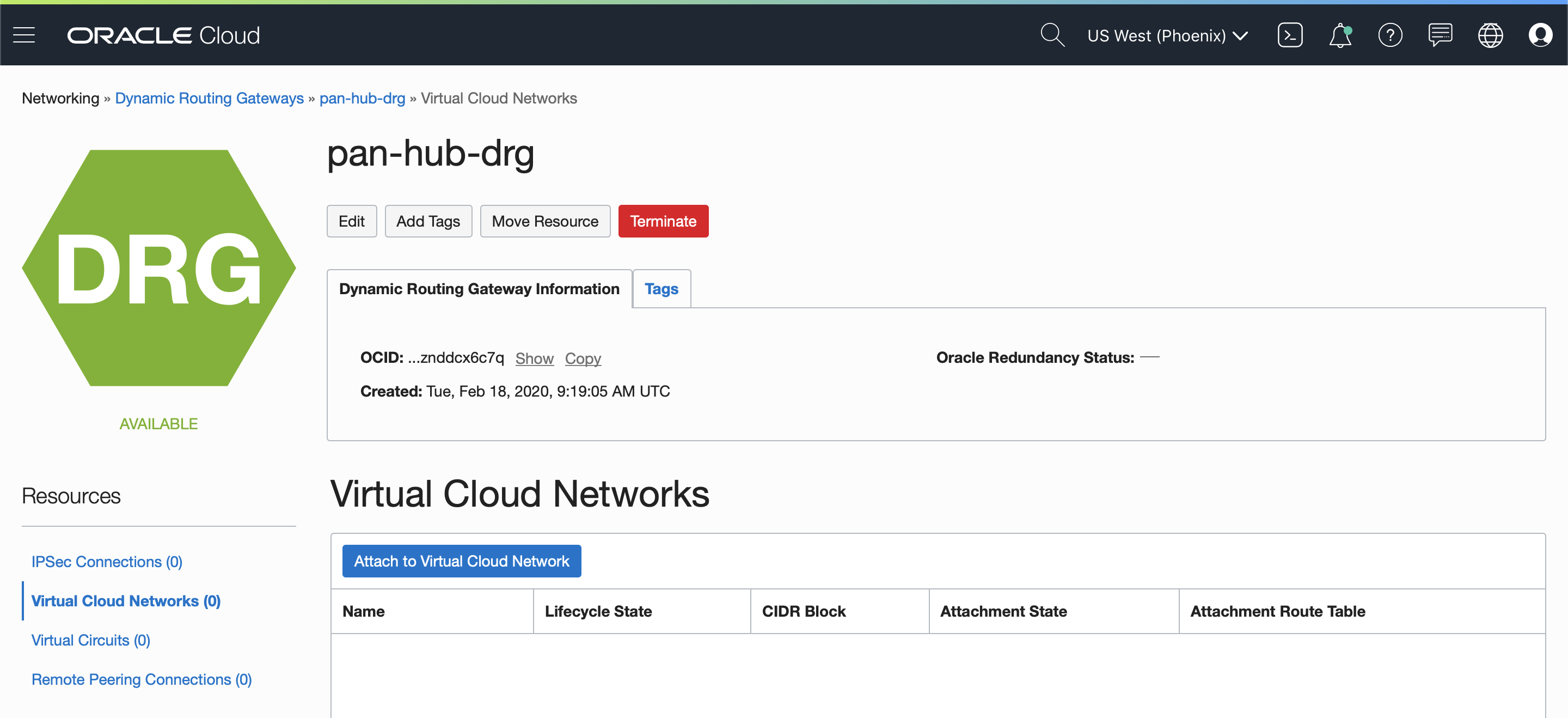
3.5.2 Attach DRG to HUB-VCN
From DRG select Virtual Cloud Networks and click on the “Attach to Virtual Cloud Network” button.
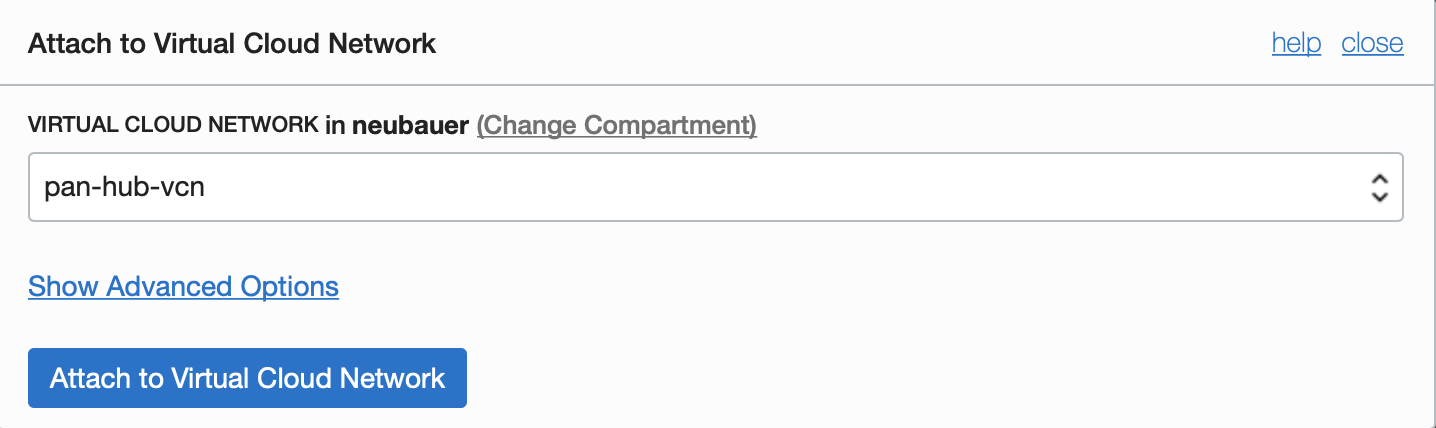
Select the HUB-VCN and click on the “Attach to Virtual Cloud Network” button.
3.6 Create Routing Tables for HUB-VCN Subnets
Go back to the HUB-VCN by selecting “Networking” and “Virtual Cloud Network”. Select the HUB-VCN and after the “Routing Tables”.
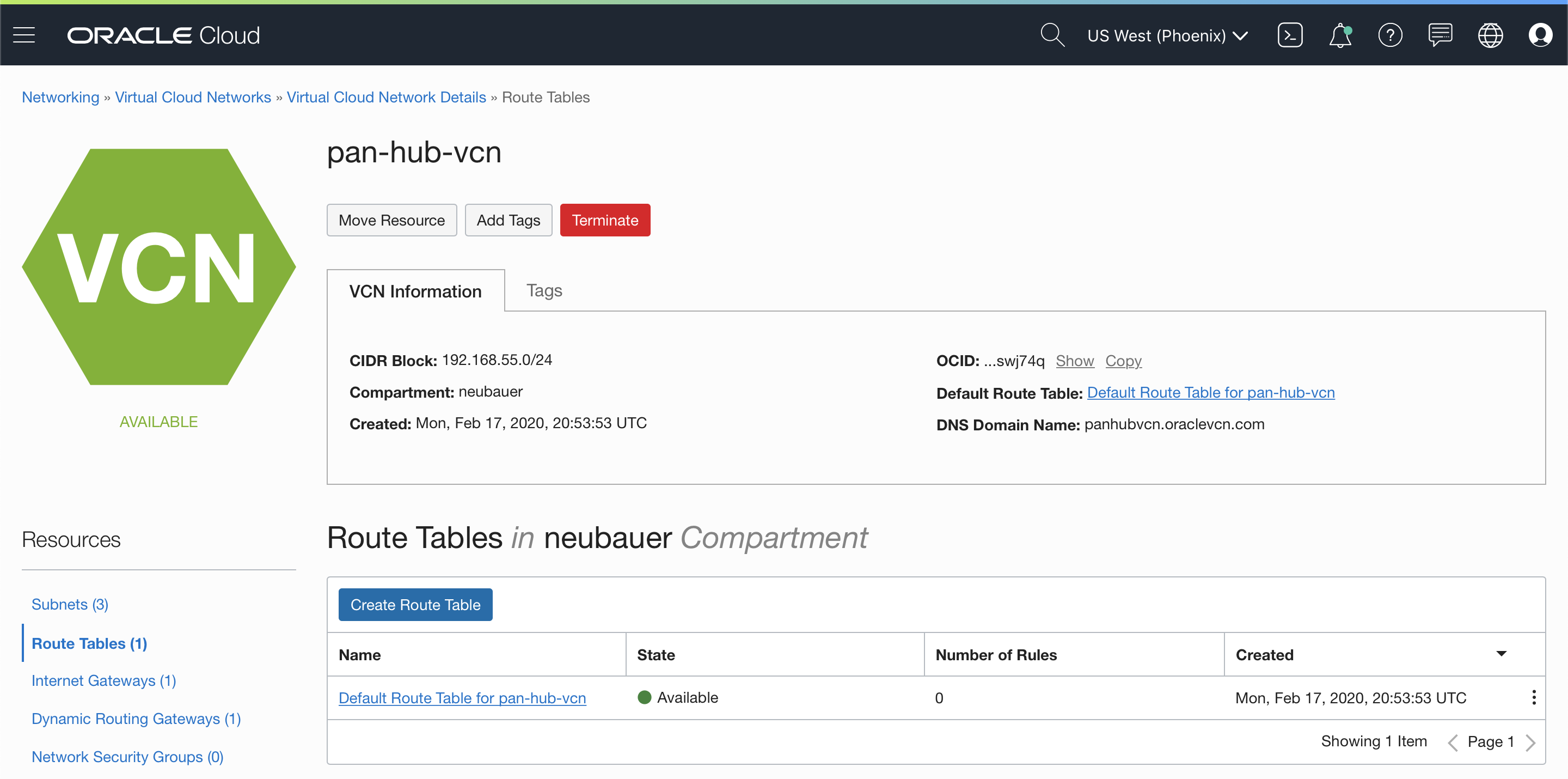
The “Default Route Table” crated by the VCN will not be used in this example. Instead, we need to create 3 routing tables for Management, Internet and OSN & On-premises access and 2 additional routing tables for DRG and Service Gateway.
3.6.1 Management Routing Table
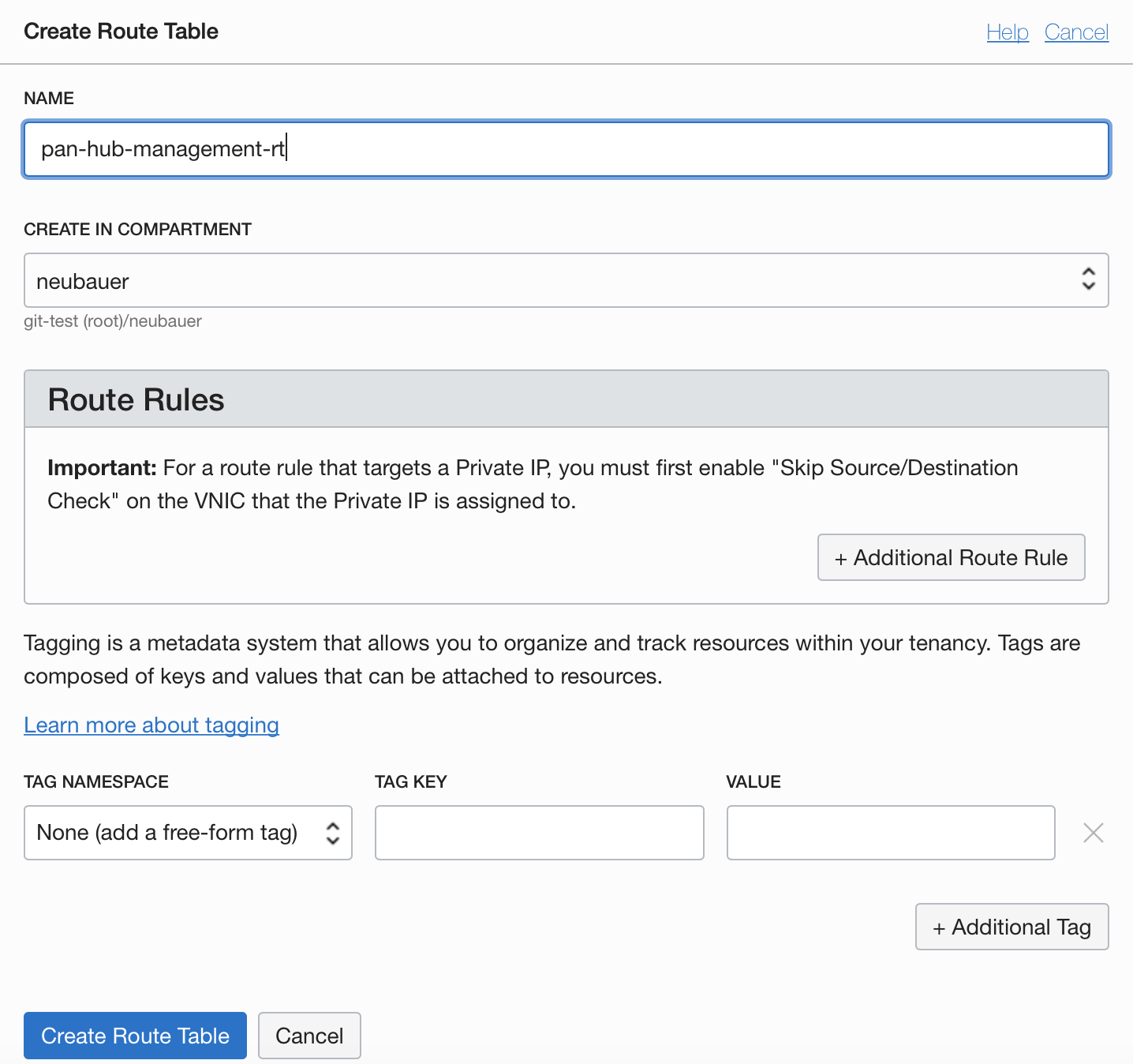
3.6.2 Internet Routing Table
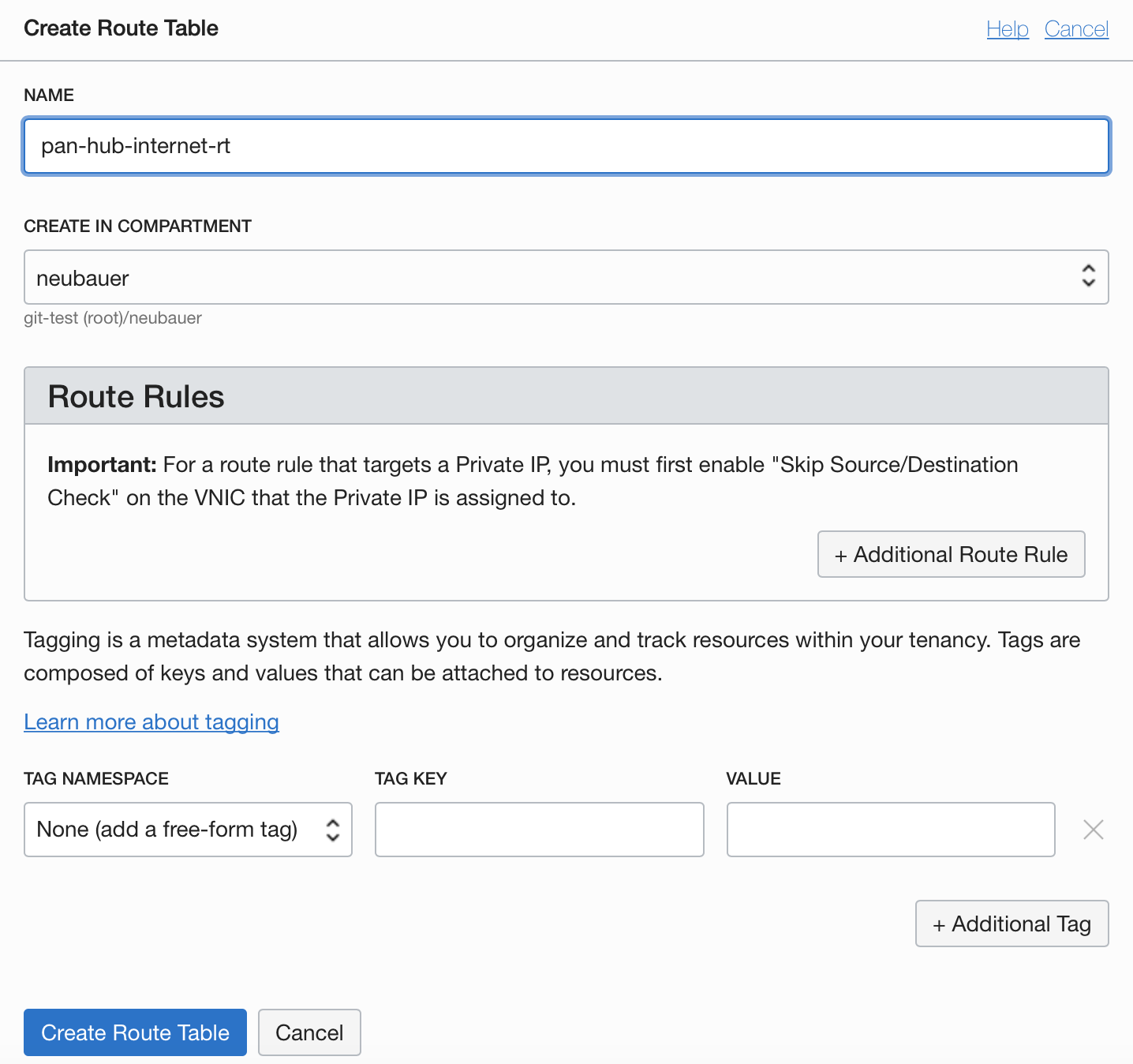
3.6.3 OSN and On-prem Routing Table
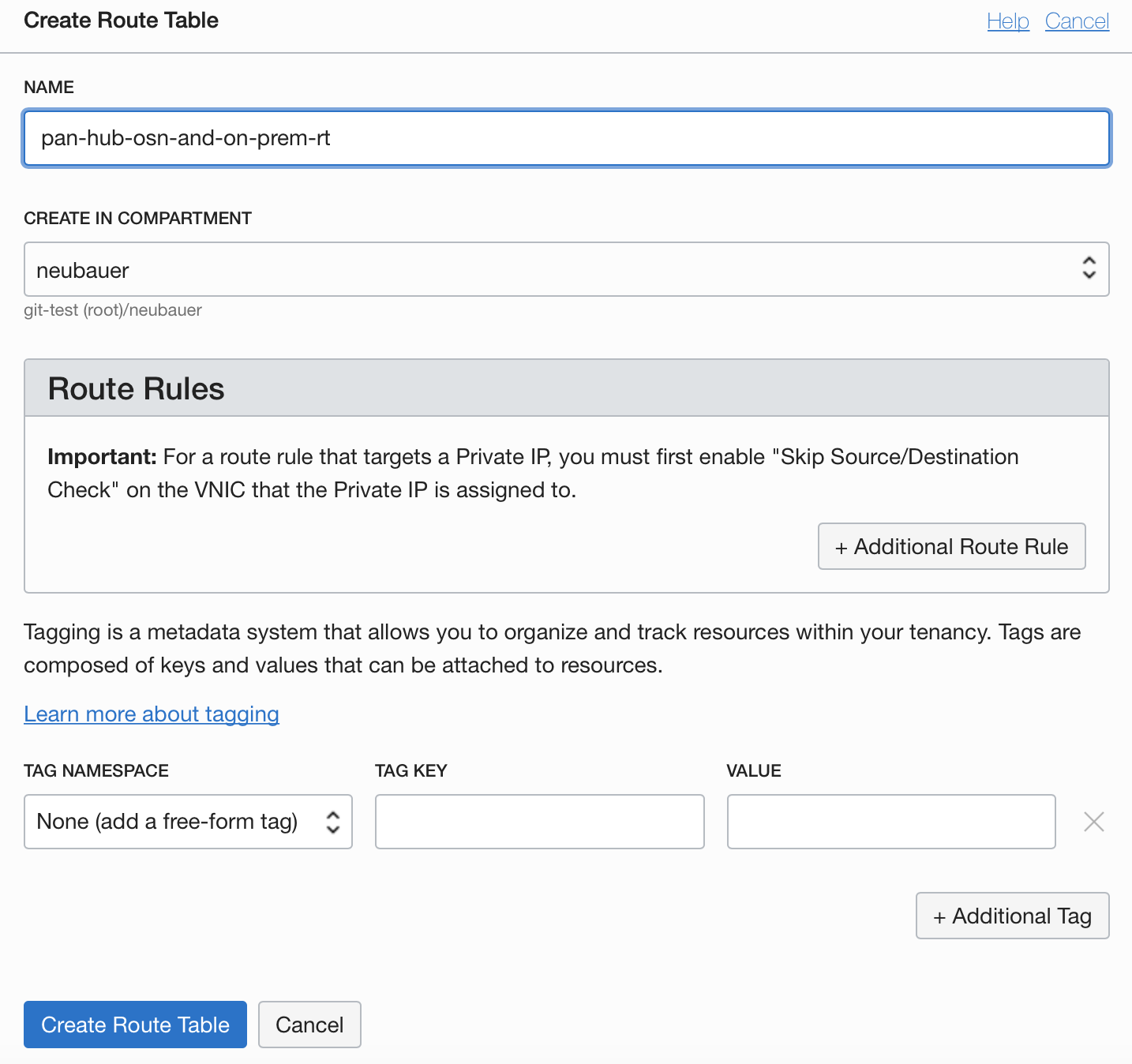
3.6.4 DRG Routing Table
3.6.5 Service Gateway Routing Table
Part 2 will contain the configuration of Palo Alto Networks VM-Series and the routing rules necessary to permit communication. The final chapter in part 2 will be testing the access from Spoke 1 to Object Storage and between Spoke 1 and Spoke 2 – https://www.ateam-oracle.com/palo-alto-hub-spoke-architecture-part-2.
