Overview
Distributed Denial of Service (DDoS) attacks have existed since the internet’s early years. A simple explanation of DDoS is a room of 100 people trying to start a conversation with one person. So, what happens to that one person processing all those conversations simultaneously? They become overwhelmed!
Now take the world of Oracle Cloud, which has a suite of services and applications providing business value to an organization. If a critical service or application on Oracle Cloud Infrastructure is the target of a DDoS attack, that resource may no longer be available to legitimate requests. DDoS attacks are Denial of Service attacks where the incoming traffic is originated from multiple sources, often spanning several geolocations. Therefore, any resource accessible via a public address can be a potential target of a DDoS attack.
DDoS attacks can cause significant disruption for seconds, minutes, or even hours, preventing the delivery of services to an organization.
Understanding the DDoS Layers
Network/Transport Layer (3 and 4) Protection (TCP, UDP, ICMP)
All Oracle Cloud data centers have DDoS attack detection and mitigation for high volume, Layer 3 or 4 DDoS attacks. These DDoS protection services from Oracle Cloud help ensure the availability of Oracle network resources even under sustained Layer 3 or 4 attacks.
Application Layer (7) Protection (HTTP/HTTPS)
Layer 7 attacks (HTTP/HTTPS) target applications exploiting vulnerabilities and misconfigurations. The size and sophistication of these attacks are growing exponentially. Therefore, protecting applications from cyber threats, including malicious bots, cross-site scripting, SQL injection, and other vulnerabilities defined by the Open Web Application Security Project (OWASP), is vital.
What Should a Customer Consider When Understanding the DDoS offerings from Oracle?
When Oracle talks about DDoS Protection associated with OCI, it refers to the network-based attack (Layer 3 and 4 of the OSI Model) or what many people think of as a volume-based attack. Oracle monitors its entire address space, including Bring Your IP Address (BYOIP) for all customers. If it sees high-volume-based attacks, it has the tools and processes to mitigate and scrub the malicious traffic. Oracle is fully managing this protection for organizations. For organizations that want to have control of this protective layer for additional visibility, management, and particular-based rate limits and alerts, it’s possible to look at enabling these features in a Network Virtual Appliance (Firewall, Scanner/Scrubber) deployed in OCI.
Layer 7 application-layer-based attacks require something to protect the application itself. Within OCI, Oracle provides a Web Application Firewall (WAF) as part of its Cloud Security portfolio. WAF provides application-layer protection against botnets, application attacks, and DDoS attacks. It can protect ANY internet-facing web applications, not just those hosted on OCI. In addition, WAF has capabilities like rate limiting, as well as access control to protect web applications from DDoS attacks.
DNS-based attacks are prevalent as they exist at the transport layer as part of the UDP protocol and can be attacked from many avenues. DNS Services can be deployed in OCI as a customer-owned entity behind a Network Load Balancer, for example, to service public DNS services. From a DNS design perspective, it’s a working solution, but mitigating UDP Flood attacks at the network layer would require a user-controlled Layer 3 and 4 DDoS protection mechanism. Think about rate-limit and controls mentioned above and what Oracle covers; there might be a better approach if the expectation is that Oracle will block a UDP Flood attack. Oracle’s DNS service can be your organization’s primary or secondary DNS provider. OCI DNS is a global anycast network of multiple data centers strategically located across various continents. It leverages a mix of redundant internet transit providers for ultimate resiliency and protection against DDoS attacks. Another solution is to continue with any third-party, public DNS services that also provide DDOS capabilities.
We can summarize the attack types and mitigations in the diagram below:
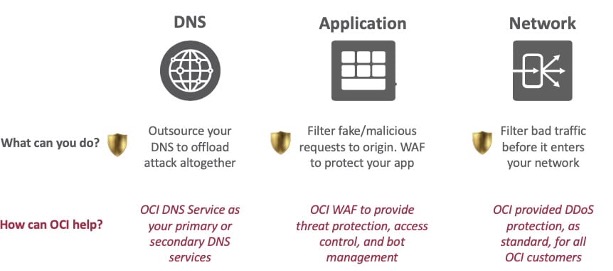
Summary
DDoS attacks are multi-faceted; therefore, defense against these attacks must be multi-faceted and follow a defense-in-depth strategy to mitigate the threats. First, it’s essential to understand what Oracle provides from a native services perspective and how design choices can impact those offerings and require third-party solutions. Hopefully, this article has helped clarify our understanding of Oracle DDoS offerings and considerations for DDoS mitigations and visibility.
The total depth of the Oracle Security offering is at the link below:
https://www.oracle.com/security/cloud-security/