A frequent set of queries that I come across from customers of Oracle Applications is about extracting log files from applications such as HCM, ERP or CX. Typically, at the root of these questions are requirements to monitor the activities in the application – for example, they might be about who are logging in and from where, who has been granted access to what type of data or, who are creating or updating sensitive information such as PII. More often than not, this kind of monitoring is performed by a Security Information and Event Management (SIEM) application, such as the ones offered by Splunk, Datadog or Elastic.
Another common reason behind these questions is use of a central log analytics solution for the enterprise, where logs are collected, stored, and analyzed for various current and historic purposes.
In this blog, I’ll address the question of collecting audits from applications, while also presenting some alternatives in meeting the requirements behind it. Along the way, I’ll delegate some intricate details to other suitable blogs and documentation from Oracle.
Oracle applications cloud provides APIs and tools to extracts audits, instead of exposing log files to customers directly. There are certain exceptions such as logs from execution of ESS jobs, which can be downloaded from applications, but they might not be relevant for SIEM applications. The questions around extracting multiple types of audits from the applications are addressed by the support note 2723316.1. However, let’s take a birds-eye look at the security monitoring landscape, including some alternatives from Oracle OCI, and then look at the types of audits available for extraction.
Here are common alternatives to address the application event monitoring requirements.
- Use OCI services and tools to extract audits and feed 3rd party SIEM
- Extract audits to use with 3rd party SIEM applications
OCI Architecture for SIEM
OCI tools and services can also be used to extract application audits, to transform into formats suitable for a SIEM application and use a scalable architecture to feed the audits to SIEM. Below is a sample architecture, which is also explained in detail in this solution. Oracle applications can be part of this solution as well, using sources of audits provided in the next section.
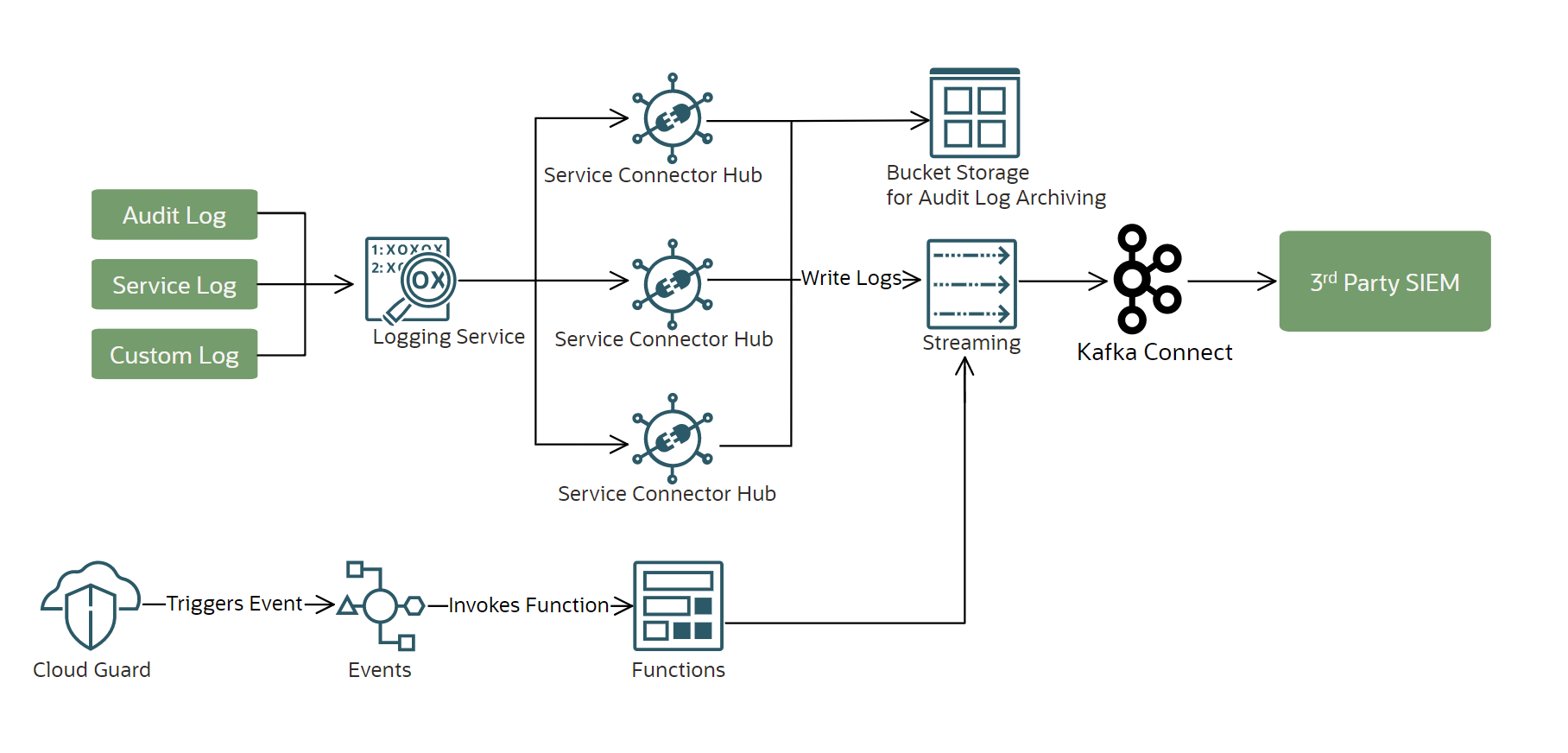
An architecture for SIEM Integration on OCI.
Extraction of application audits
As discussed previously, audits can also be extracted, formatted, and imported into a SIEM application using 3rd party tools. I’ll touch upon the types of audits while leaving the details to support note 2723316.1. There are generally two types of audits available.
- Audits of all supported business objects can be retrieved over REST API, after configuring the audits. The audits provide information on who created, updated, or deleted business objects configured for audits. The configuration is applied through audit policies. Audit data are kept until customers choose to purge them.
- Audits of user logins, logouts, password changes and security configuration changes across all application pillars. Most of this information is accessible over REST API and some can be obtained through ESS jobs.
Once these audits are extracted, they can be formatted and ingested, either using the scalable architecture mentioned in the previous section or using an architecture and tools of choice by a customer. Please refer to the documentation links below for the blogs and product documentation that might be helpful in building a SIEM solution with Oracle applications.
References
-
Audit Frequently Asked Questions (FAQ) (Doc ID 2723316.1)
