Overview
CA/B forum released new standards for subscriber key protection requirements. As part of the new requirements, a code signing certificate private key must be stored in FIPS compliant HSM device.
Oracle cloud offers fully managed Key Management service that stores and manages keys in FIPS compliant HSM device. Customers can use the service to create PKI and use that for code signing. The standard process for code signing certificate with OCI vault would look like below.
- Create Public-Private key pair in OCI vault.
- Generate CSR (Certificate Signing Request) using the keys.
- Get CSR signed from trusted well-known CA and get code signing certificate.
- Use Private key from OCI vault and code signing certificate to sign the code (jar file).
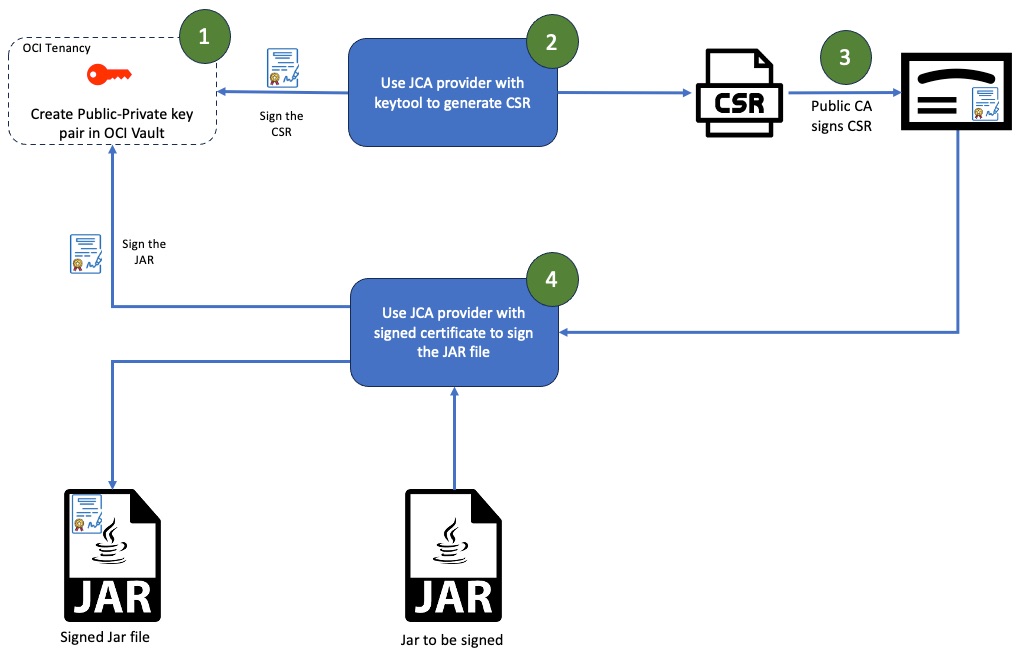
I published a blog earlier this week that talked about using JCA provider to generate CSR. In this blog, I will focus on the second half that is signing the jar file using signed certificate and JCA provider. Once the CSR is generated, you can get the CSR signed from public CA like DigiCert and get code signing certificate. That process is out-of-scope for this blog post.
Setup
From a setup perspective, I assume you have followed the steps (OCI Setup and JCA setup) from the previous blog.
Once the CSR is signed and you receive the signer certificate, we use the signed certificate along with the JCA provider to sign the jar file. Like the keytool command, the jarsigner command also requires some command line parameters related to OCI. Those parameters are below.
Alias: This is name of the certificate file. If the signed certificate filename is certfile.crt, then the alias would be certfile. Alias is the last parameter of jarsigner command without any command line argument.
certAuthorityId: OCID of the certificate authority created in step 1.3.
cryptoEndpoint: Crypto endpoint for the OCI key created in step 1.2.
certFile: Location of the signed certificate file on the file system.
keyId: OCID of the key that was used during creation of the CSR. This is the OCID of the key created in step 1.2 from the previous blog.
jarsigner -keystore NONE -storetype OCIKeyVault -signedJar signedhello.jar hello.jar -verbose -storepass “” \
-providerClass com.oci.security.keyvault.jca.OCIJcaProvider \
-J-Doci.certAuthorityId=${certAuthorityId} \
-J-Doci.cryptoEndpoint=${cryptoEndpoint} \
-J-Doci.certFile=${certFile} \
-J-Doci.keyId=${keyId} \
-J-Djava.util.logging.config.file=”logging.properties” ${Alias}
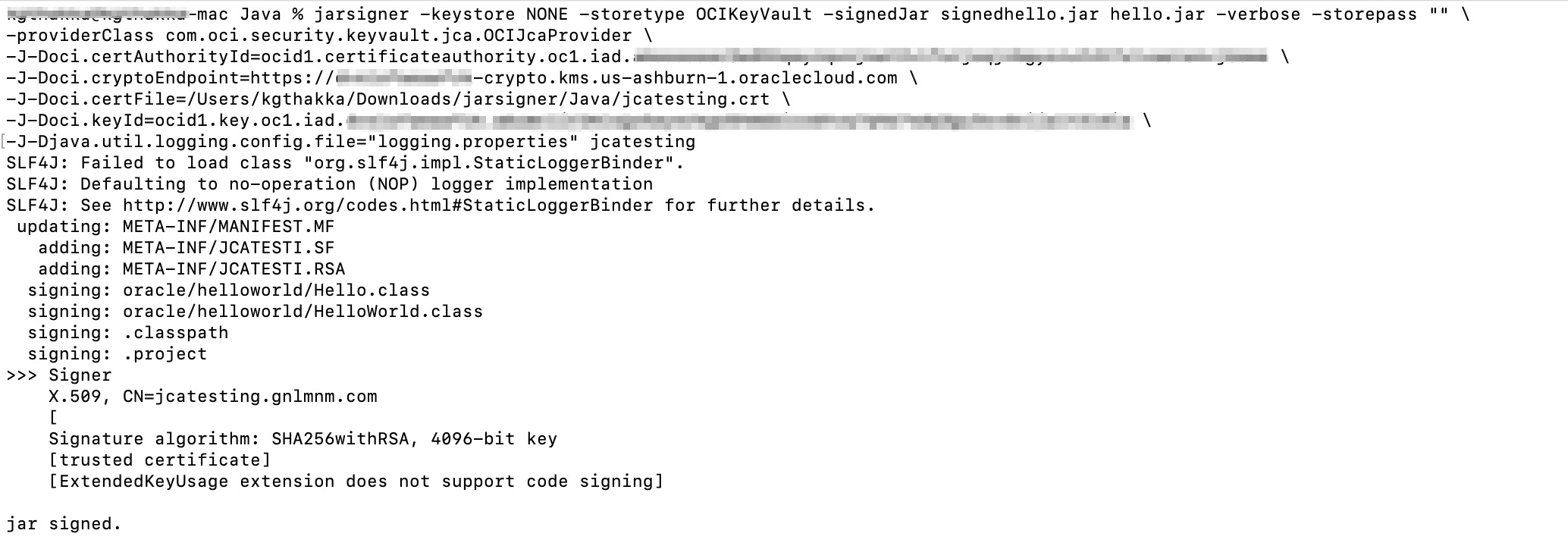
Once the jar file is signed, you can also verify the signature using jarsigner -verify command.

Conclusion
Jarsigner is just one of the use cases. However, you can use it for encryption-decryption, signing-verification, and many other cryptographic use cases in your Java application.
