Oracle’s PeopleSoft applications are designed to address the most complex business requirements. They provide comprehensive business and industry solutions, enabling organizations to increase productivity, accelerate business performance, and provide a lower cost of ownership.
In this new blog post we will analyze the OCI networking architecture that needs to be in place either for migrating Oracle PeopleSoft from OCI-Classic to OCI, from On-premises to OCI or just having a brand new Oracle PeopleSoft deployment.
The PeopleSoft application will be installed on IaaS VMs and will act as backend servers for public and/or private application LBaaS. Our focus will be on the networking infrastructure that needs to be in place to support the PeopleSoft deployment and accomplish the performance and security requirements.
1. Using third party firewalls for PeopleSoft networking architecture
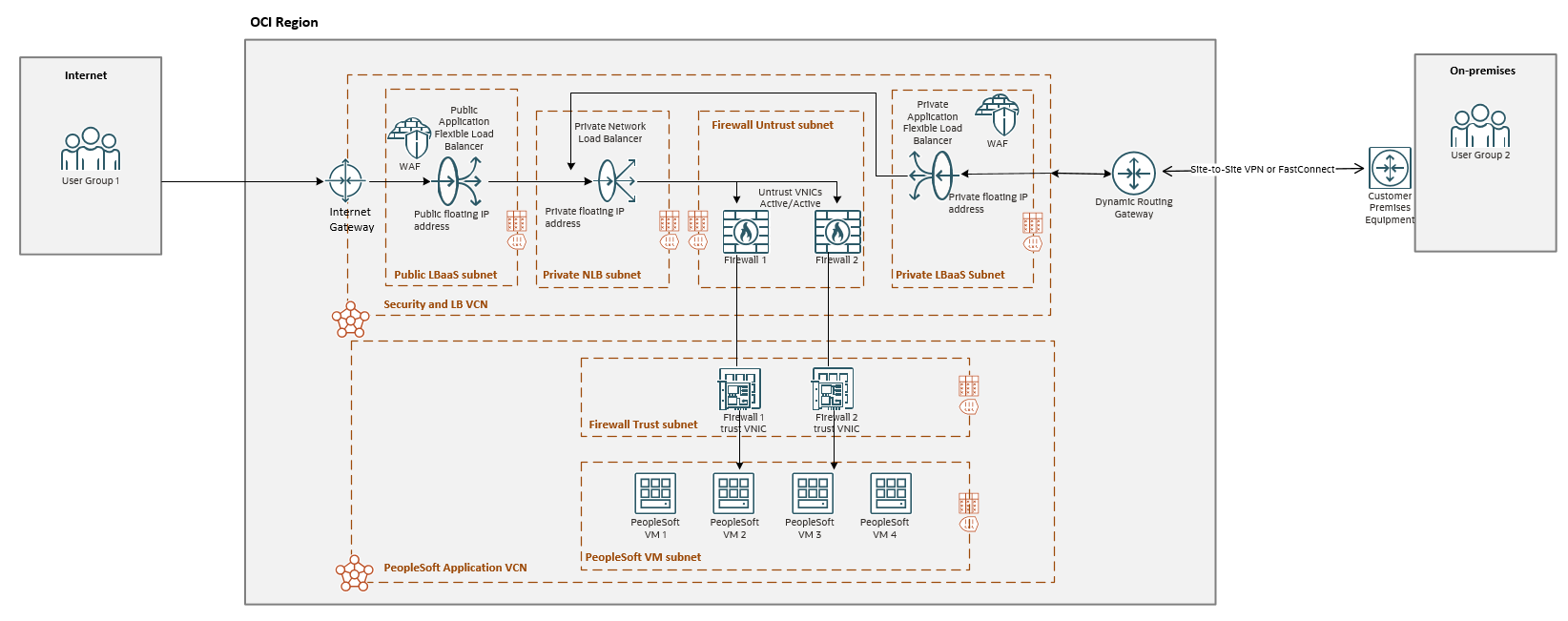
User Group 1 from the left side of the diagram will access the PSFT using the Internet while the User Group 2 from the right side will access the PSFT from On-premises using IPSec of FastConnect type of connections.
Having two types of access, the design will include two application LBaaS, one public and one private. In most of the use cases the access to PSFT application will use multiple Listeners and Backend Sets on the LBaaS using the same 443 port. In order to create multiple Listeners using the same port, the virtual hostnames will be used.
An example is below:
Listener1: abc.com:443
Listener2: xyz.com:443
Hostname for Listener1: abc.com
Hostname for Listener2: xyz.com
Backend Set for Listener1: PSFT VM1/2
Backend Set for Listener2: PSFT VM3/4
The WAF Gen2 service should be enabled on the LBaaS and configured with specific rules for PSFT. The SSL certificates needs to be in place for every Listener.
Besides OCI built-in security capabilities, a pair of third party firewalls are used in Active/Active mode with the OCI Network Load Balancer in front to distribute the traffic to both appliances. This part will be used for Internet originated connections and from On-premises via the private LBaaS.
The health check will also be sent through the firewalls. One important fact to consider is that each of the firewalls will perform SNAT using the private IP address of the trust vnic, which in our case is placed in the PSFT Application VCN. This posture will simplify the routing, providing minimal packet handling, maximize the performance and assuring symmetric traffic path.
The NLB will preserve the source/destination IP address and 5-tuple hash will be used.
Scenario 1
Let’s follow the life of a connection initiated by the User Group 1 to abc.com:
User Group 1 -> Internet -> OCI IGW -> OCI public LBaaS (match Listener1) -> OCI NLB -> Firewall1/2 and SNAT using the trust vnic -> PSFT VM1/2
The response will follow the path:
PSFT VM1/2 -> Firewall1/2 trust interface -> OCI public LBaaS -> User Group 1
Scenario 2:
The life of a connection iniated from User Group 2 using the IPSec VPN or FastConnect to xyz.com:
User Group 2 -> IPSec or FC -> OCI DRG -> OCI private LBaaS (match Listener2) -> OCI NLB -> Firewall1/2 and SNAT using the trust vnic -> PSFT VM3/4
The response path:
PSFT VM3/4 -> Firewall1/2 trust interface -> OCI private LBaaS -> OCI DRG -> User Group 2
2. Using the OCI Network Firewall for PeopleSoft networking architecture
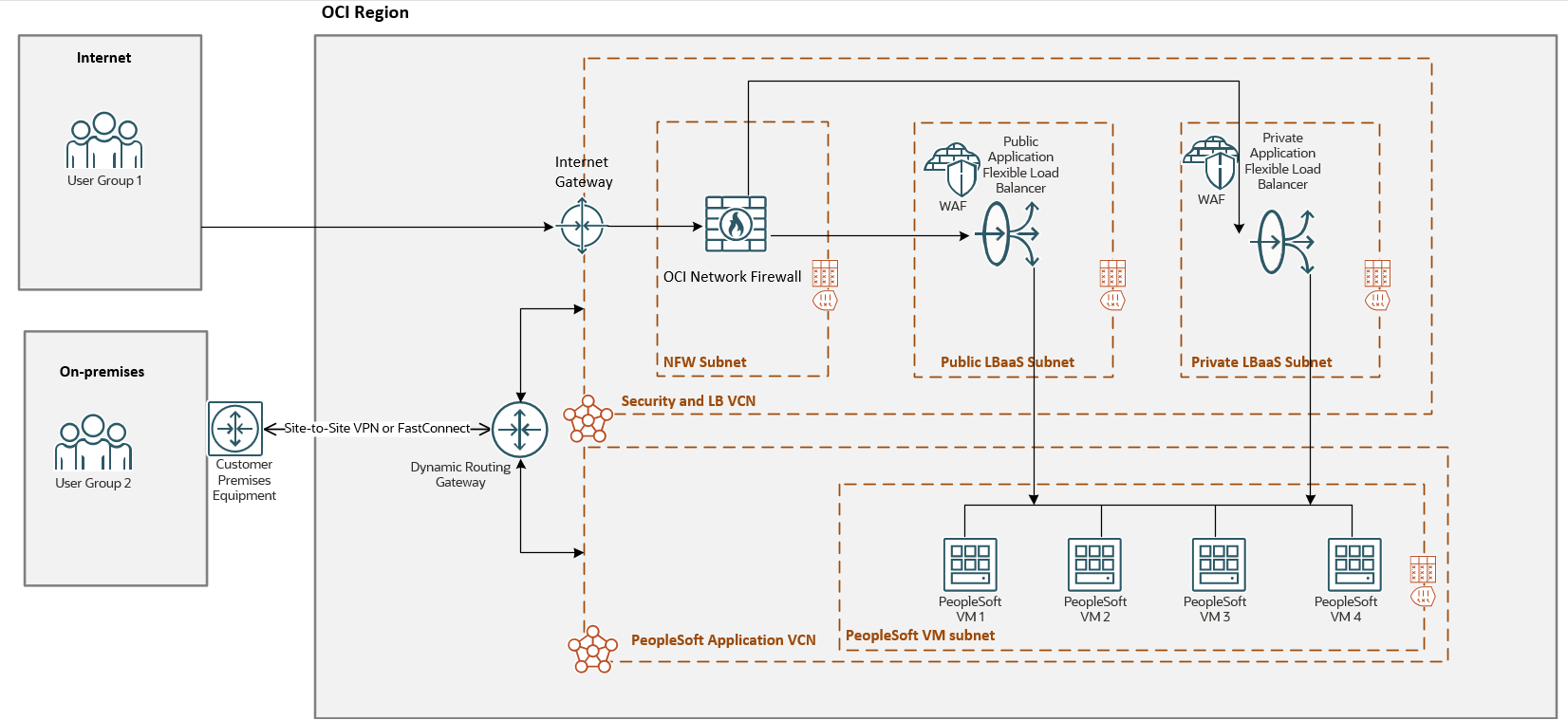
Some time ago, we have discussed about the NFW capability for securing the public and private LBaaS traffic:
OCI Network Firewall – Securing the LBaaS traffic
OCI Network Firewall – Securing the Private LBaaS traffic
We can definitively integrate the two discussions above in our current PSFT design.
As we noticed from the networking diagram, the DRG routing capabilities will be used to achieve the communication between the Security and LB VCN to the PeopleSoft Application VCN and vice-versa. The routing details are completely analyzed in the above blog posts.
Scenario 3
As the previus use case, let’s follow the life of a connection initiated by User Group 1 to abc.com:
User Group 1 -> Internet -> OCI IGW -> NFW -> OCI public LBaaS (match Listener1) -> NFW -> DRG -> PSFT VM1/2
The response will follow the path:
PSFT VM1/2 -> DRG -> NFW -> OCI public LBaaS -> NFW -> OCI IGW -> User Group 1
Scenario 4:
The life of a connection iniated from User Group 2 using the IPSec VPN or FastConnect to xyz.com:
User Group 2 -> IPSec or FC -> OCI DRG -> NFW -> OCI private LBaaS -> NFW -> DRG -> PSFT VM3/4
The response path:
PSFT VM3/4 -> DRG -> NFW -> OCI private LBaaS -> NFW -> DRG -> User Group 2
Both networking constructs can be used to secure the PSFT application in OCI, at the end, you can pick the one that is more easy to be deployed and maintained in your environment.
