Overview
Update March 2025: Some aspects of this architecture will change with the Oracle Fusion Identity Upgrade—details available here. We will update this document accordingly once the upgrade begins.
Oracle Fusion Bill Management is a popular part of the Oracle Fusion Cloud Applications Suite that allows reviewing of outstanding transactions, credit memos, monitoring disputes, and making online payments. This part of Fusion is often made available to users external to the company and hence benefits from increased security. This article describes a deployment model that separates all external users and internal users into separate IAM Domains for increased control and security. In order to simplify access for external users, this solution uses the default Service Provider initiated SSO for external Users to avoid external users to accidentally connecting to the internal IAM Domain and failing to authenticate. Internal users are using a specific link to access Oracle Fusion Cloud via the internal IAM Domain (IdP initiated SSO) – the differences between SP Initiated and IdP Initiated SSO are discussed here. Increased restrictions are placed on the internal IAM Domain to avoid anyone outside the company from logging into the environment beyond Bill Management. In preparation for this article Bill Management should be setup with at least a few accounts for testing the different access paths – the setup is described here.
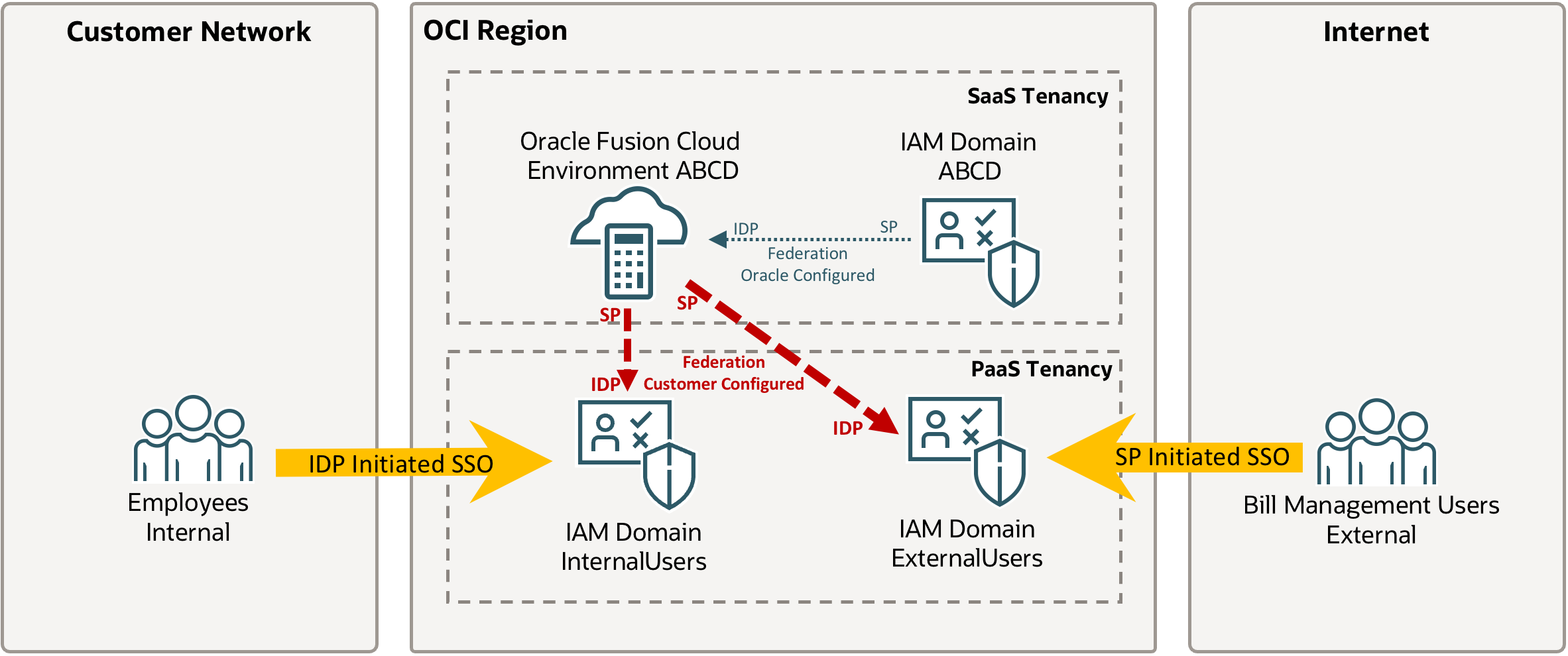
OCI IAM Domain Creation
Login to the OCI Console for your OCI tenancy with an administrator account – most likely this is your PaaS tenancy unless you have a combined SaaS/PaaS tenancy.
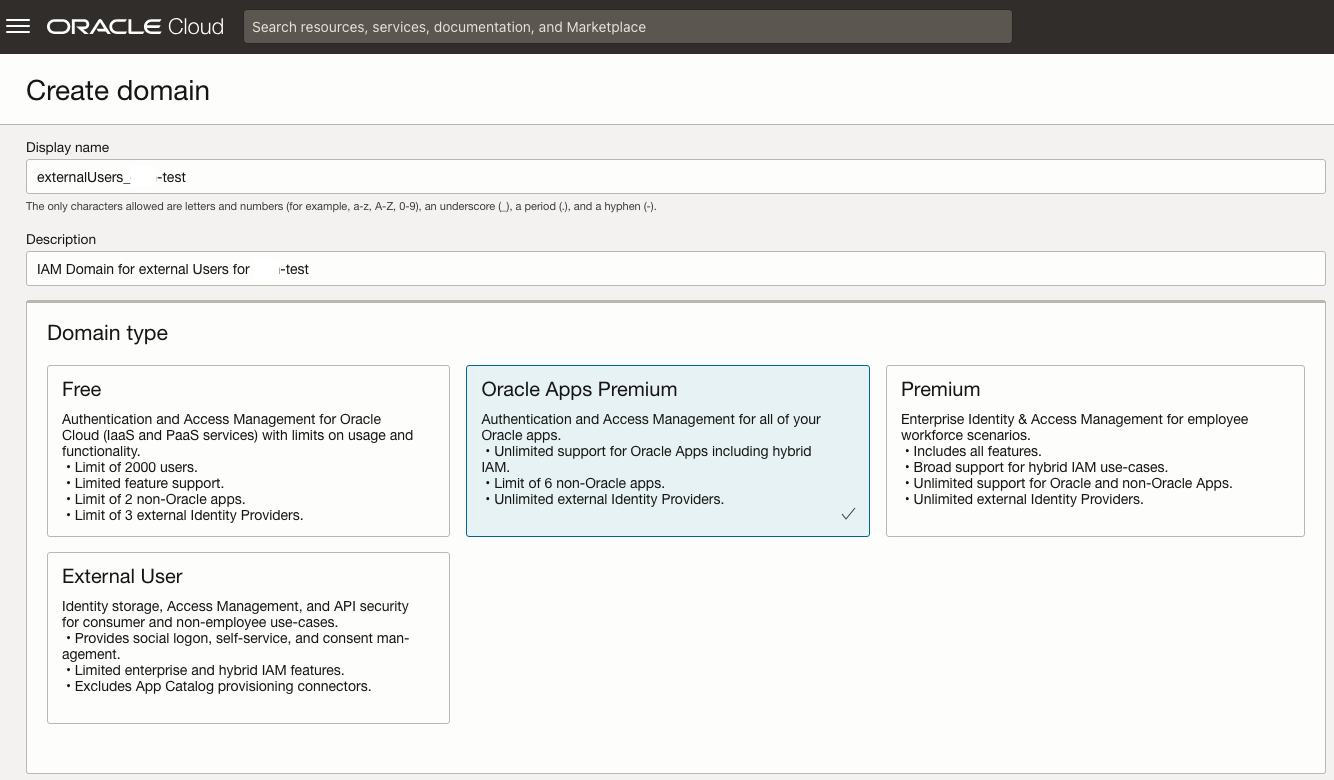
Navigate to the Domain Screen and create two new domains. First create the IAM Domain for external Users, i.e. Users that are not employees and have access to the Bill Management only. Choose a meaningful name, e.g. externalUsers_ABCD-test where ABCD-test stands for your test environment.
Select the Domain Type Oracle Apps Premium for this domain.
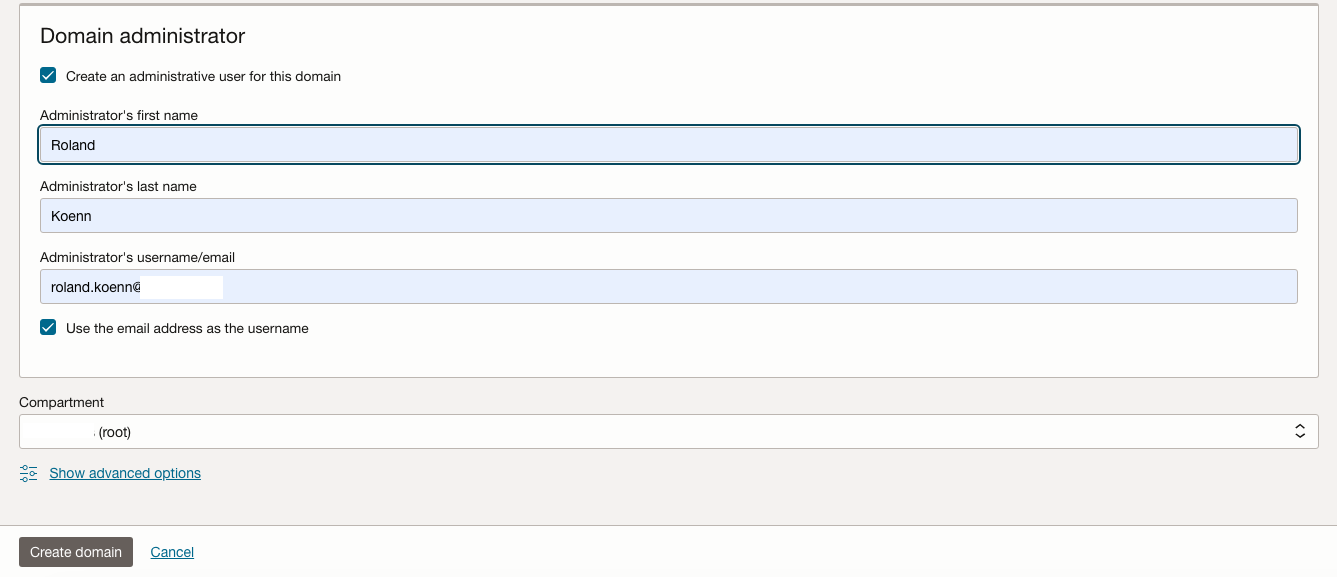
Create a Domain administrator with separate credentials to your tenancy account administrator. Be aware that the new IAM Domain will incur costs.
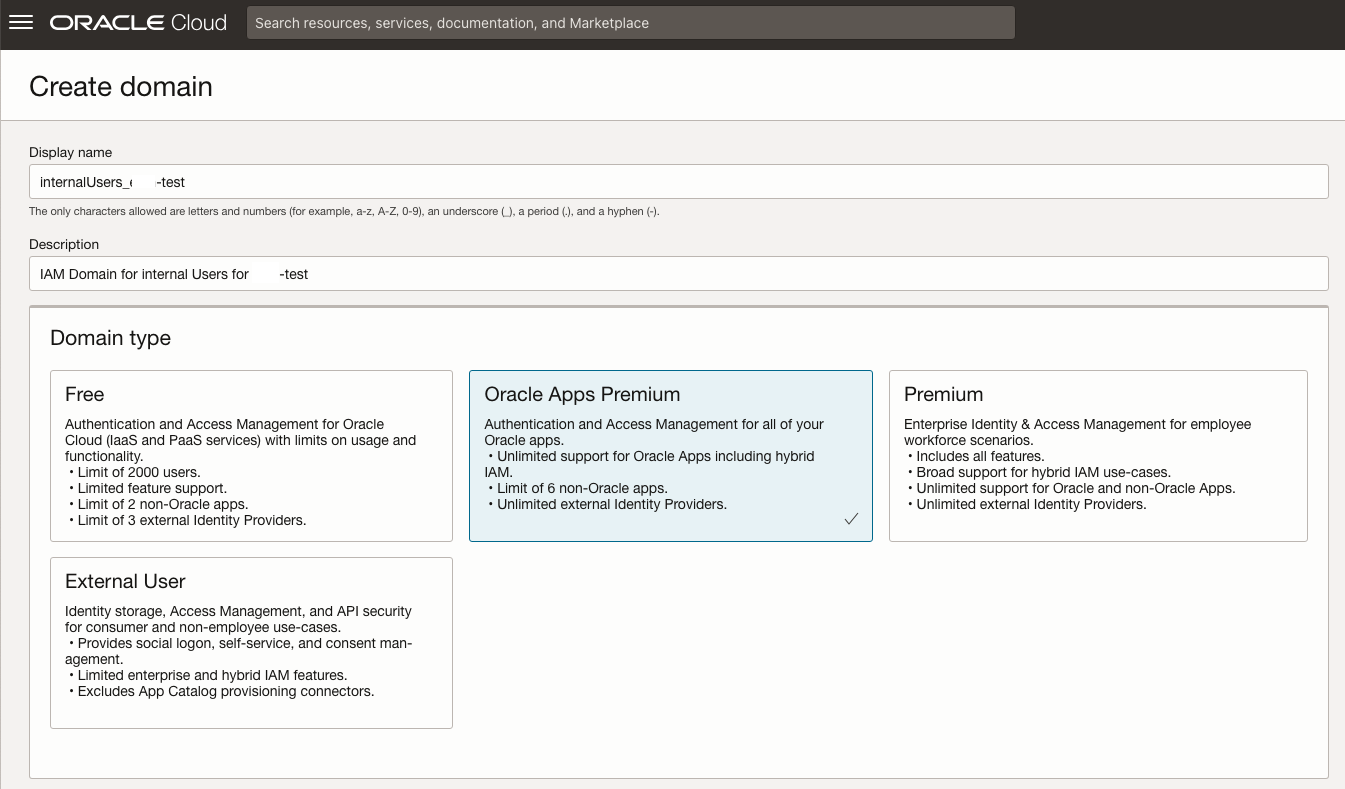
Repeat the process for the IAM Domain for the internal users. Choosing Oracle Apps Premium here. Please select the appropriate IAM Domain Type for your scenario – the types are discussed in detail here. Choose a meaningful name, e.g. internalUsers_ABCD-test where ABCD-test stands for your test environment.
Activate both IAM Domains via the link that is emailed to the Domain Administrator Account.
IAM Domain – Fusion Cloud Federation Setup
Login to Fusion Applications with an account that has the IT Security Manager Role.
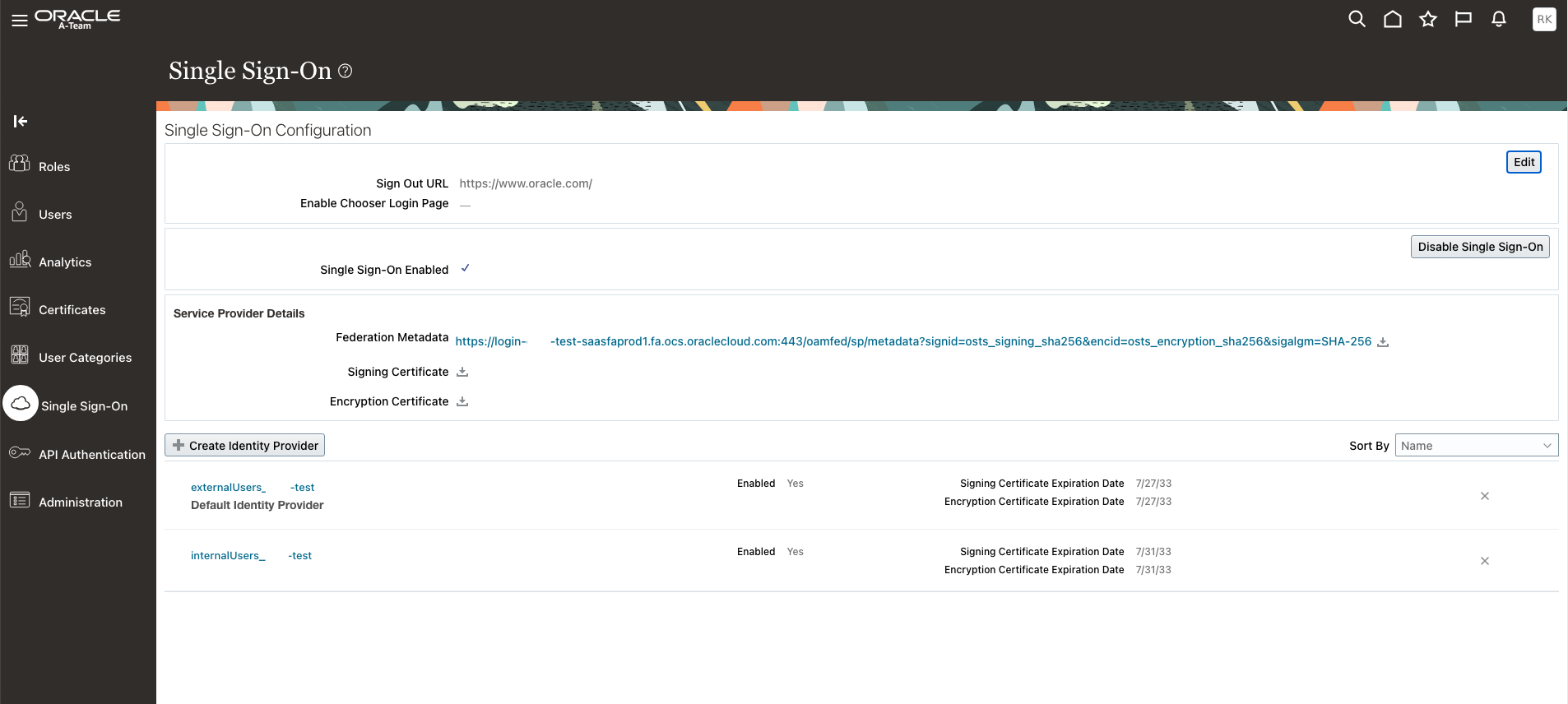
Navigate to the Security Console – click Single Sign-On and Download Federation Metadata as well as the Signing Certificate.
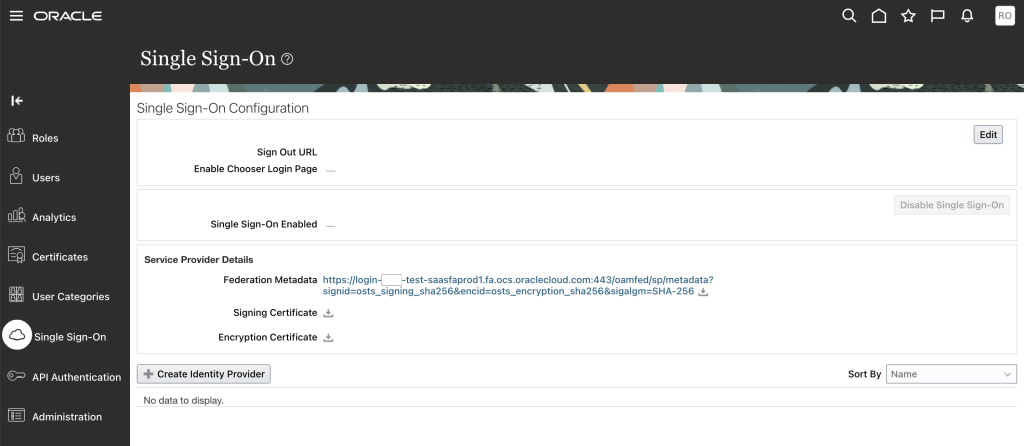
Open the Federation Metadata XML and look for the entityID attribute, e.g. https://login-ABCD-test-saasfaprod1.fa.ocs.oraclecloud.com:443/oam/fed
![]()
Open Metadata and search for the AssertionConsumerService entry. Take Note of the Location attribute, e.g. https://login-ABCD-test-saasfaprod1.fa.ocs.oraclecloud.com/oam/server/fed/sp/sso
![]()
Search for SingleLogoutService entry and note down the Location attribute, e.g. https://login-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/oamfed/idp/samlv20
![]()
Refer to Support Note Doc ID 2746354.1 for details.
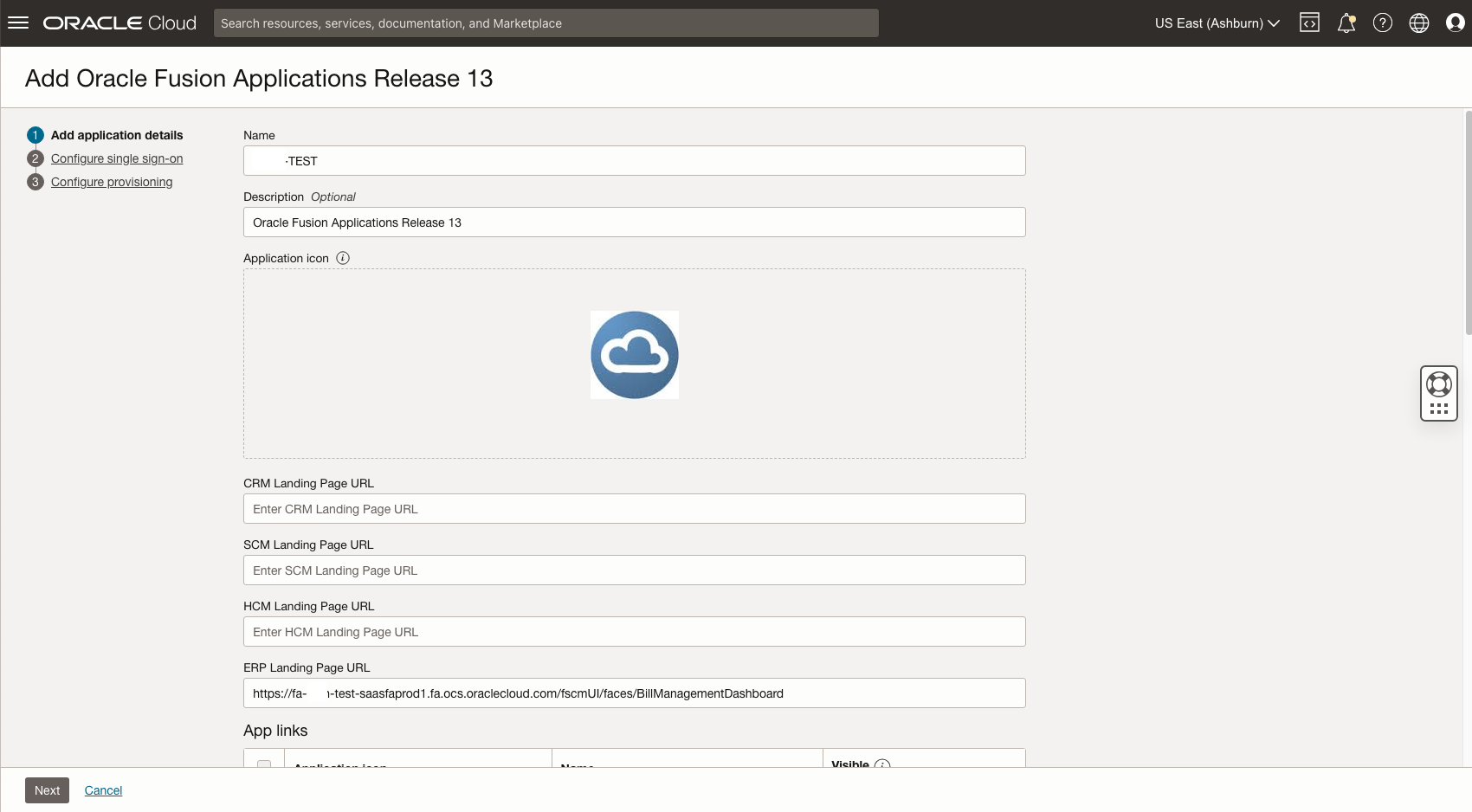
Now log back into the external domain as the domain administrator and create an Oracle Fusion Applications Release 13 application from the Application Catalog.
For now, we only want to use this IAM domain to allow external users to access Bill Management – for this we add the Bill Management Dashboard URL in the ERP Landing Page URL as shown below – this should look similar to https://fa-ABCD-test-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/faces/BillManagementDashboard
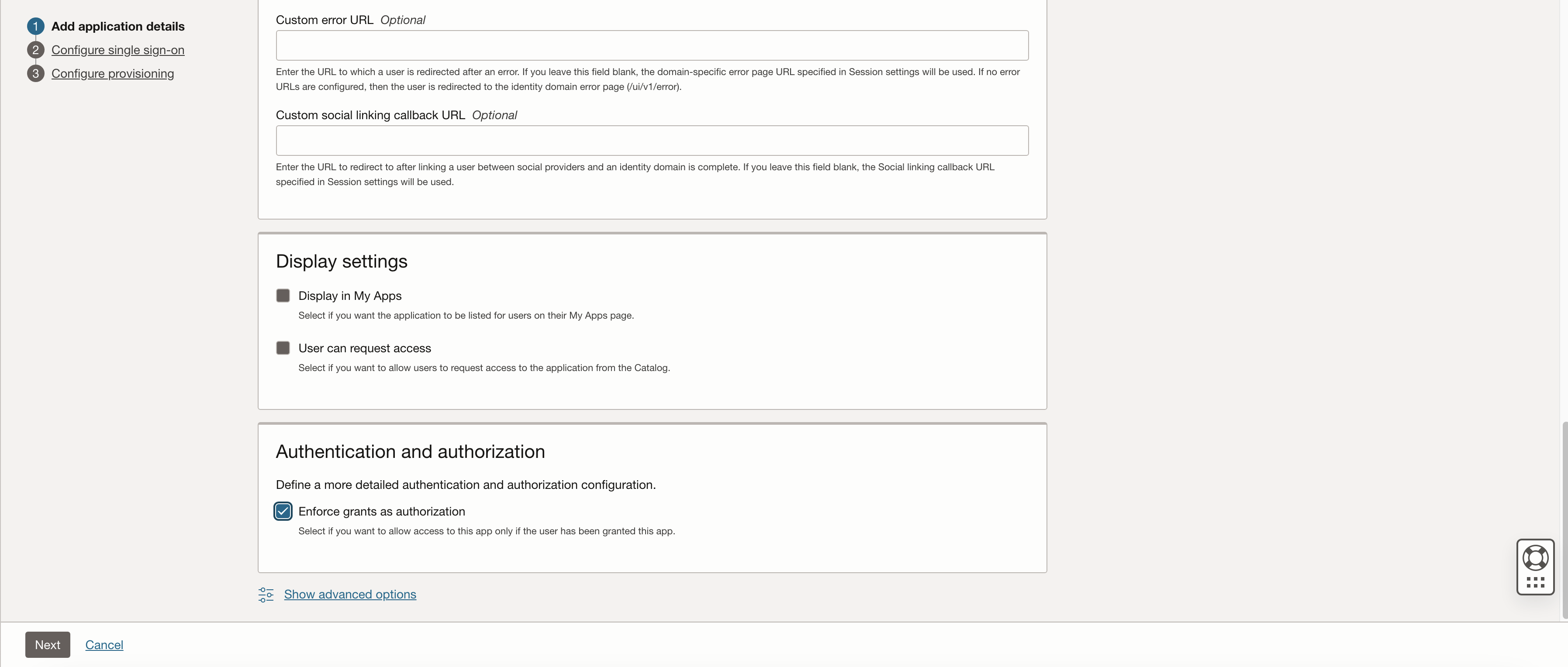
Near the bottom of the page in the Authentication and Authorization section, select the Enforce Grants as Authorization check box – this will enforce that Users can access the application only if access has been assigned or granted. All other settings on this page are optional for this use case.
On the next page make sure to download the signing certificate and identity provider metadata. For Entity ID and assertion consumer URL refer to the details retrieved above. Upload the signing certificate retrieve from your Oracle Fusion Cloud environment earlier (.cer file).
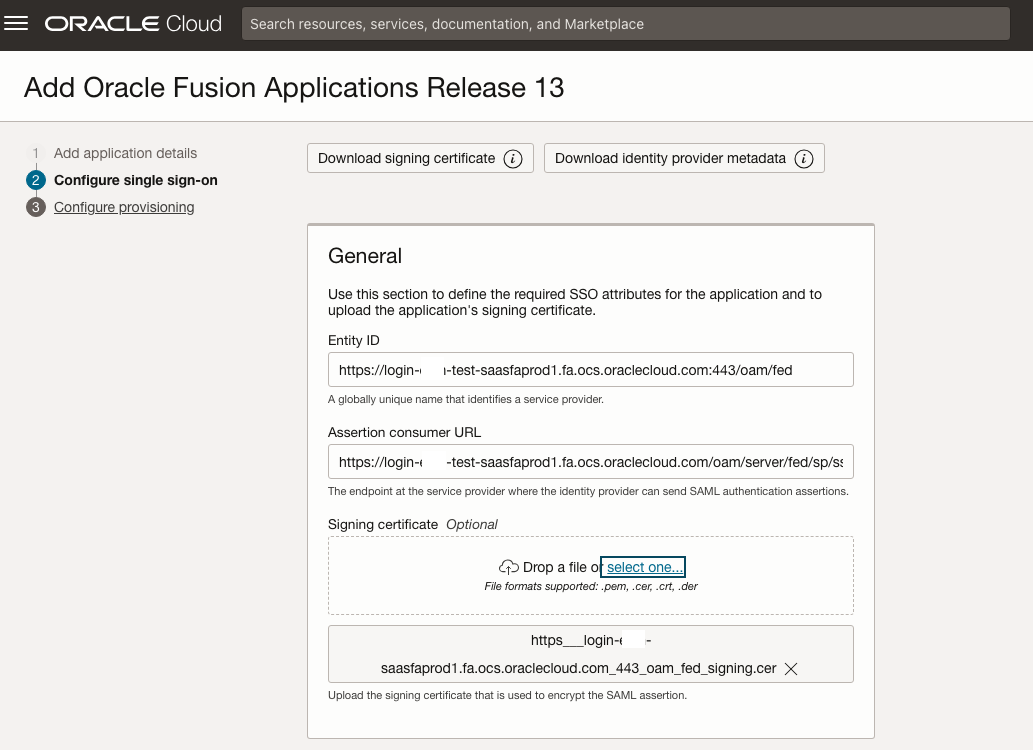
The single logout URL and logout response URL are also retrieved above.
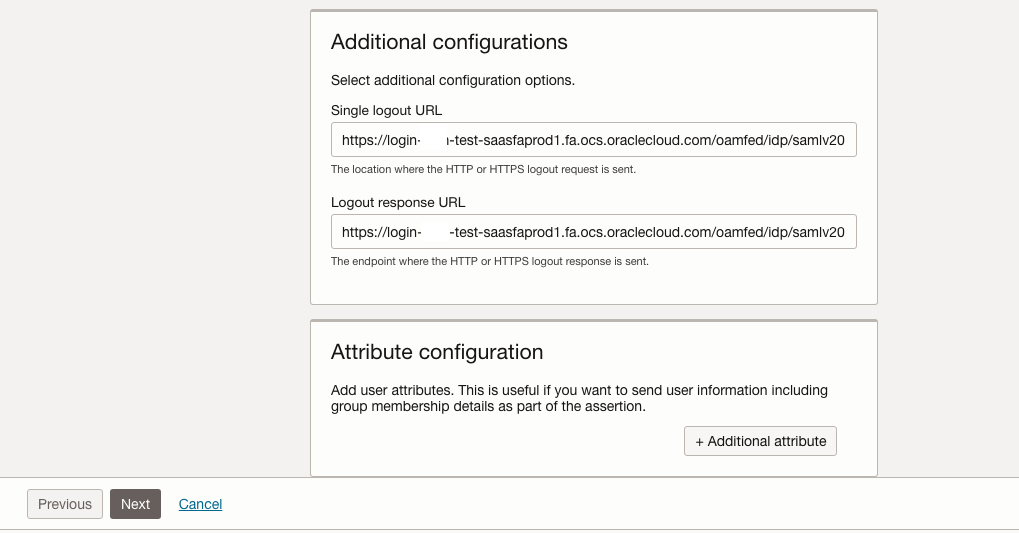
In this external IAM domain we do not want to sync all users – we only want to sync users that have access to the Bill Management part of Fusion – this requires them to have the role ORA_ARB_CUSTOMER_ACCOUNT_BILLING_INQUIRY_DISCRETIONARY (Customer Account Billing Inquiry) see Doc ID 2680489.1. Disable the Override Custom Sync checkbox and add ORA_ARB_CUSTOMER_ACCOUNT_BILLING_INQUIRY_DISCRETIONARY to the Fusion Admin Roles textbox. Further details about the configuration are here and here. Make sure to test the connectivity and then scroll further down. The user running the sync needs to have the role ASE_REST_SERVICE_ACCESS_IDENTITY_INTEGRATION_PRIV – reference here.
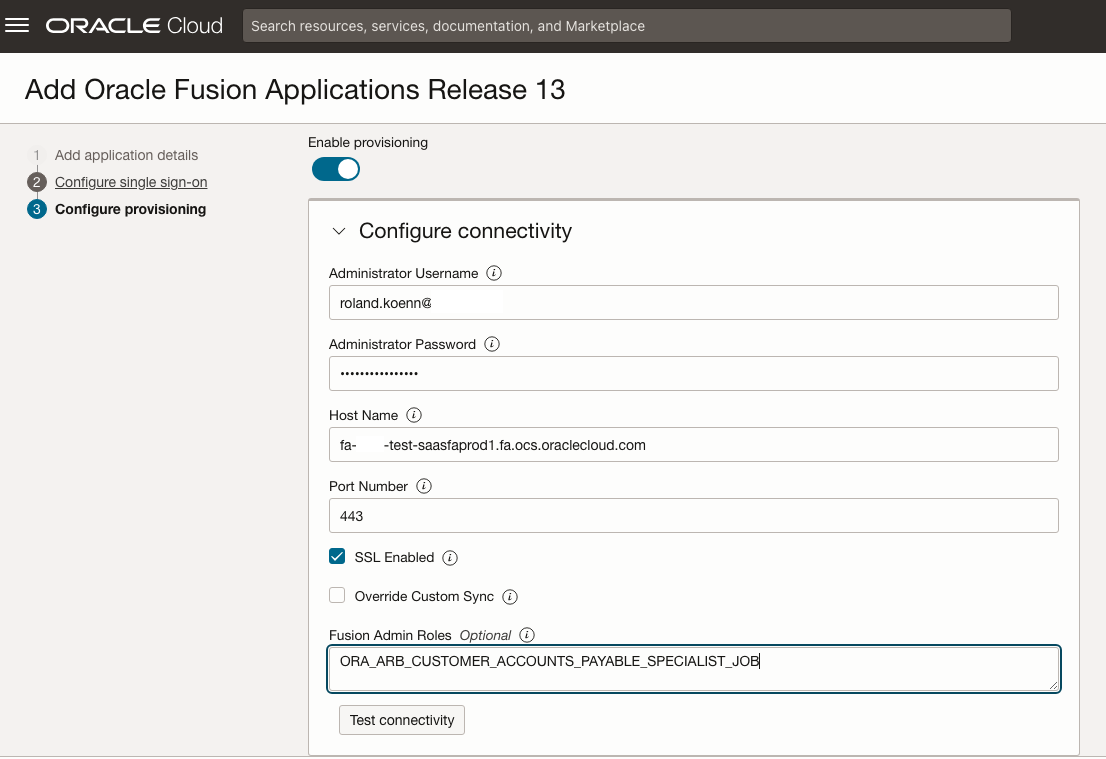
Choose to enable the Authoritative sync.
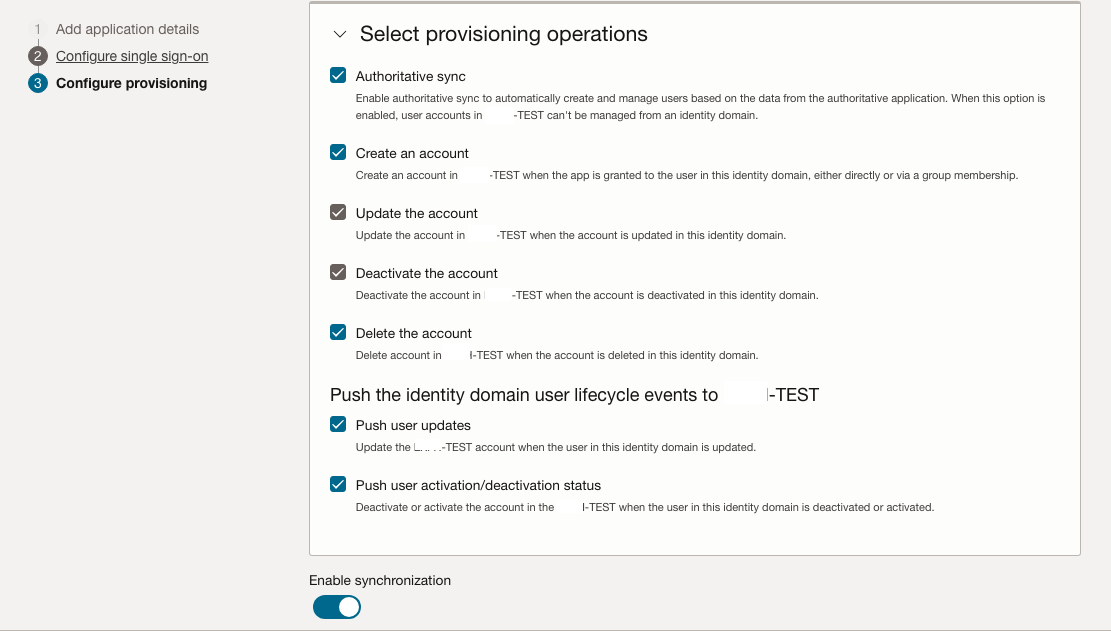
Enable the synchronization and set a schedule that matches your requirements. Hourly is a good starting point.
Activate the Application and head to the Import section to verify that the configuration is working. All users that have the role Customer Accounts Payable Specialist (ORA_ARB_CUSTOMER_ACCOUNTS_PAYABLE_SPECIALIST_JOB) should be synced to the external IAM Domain.
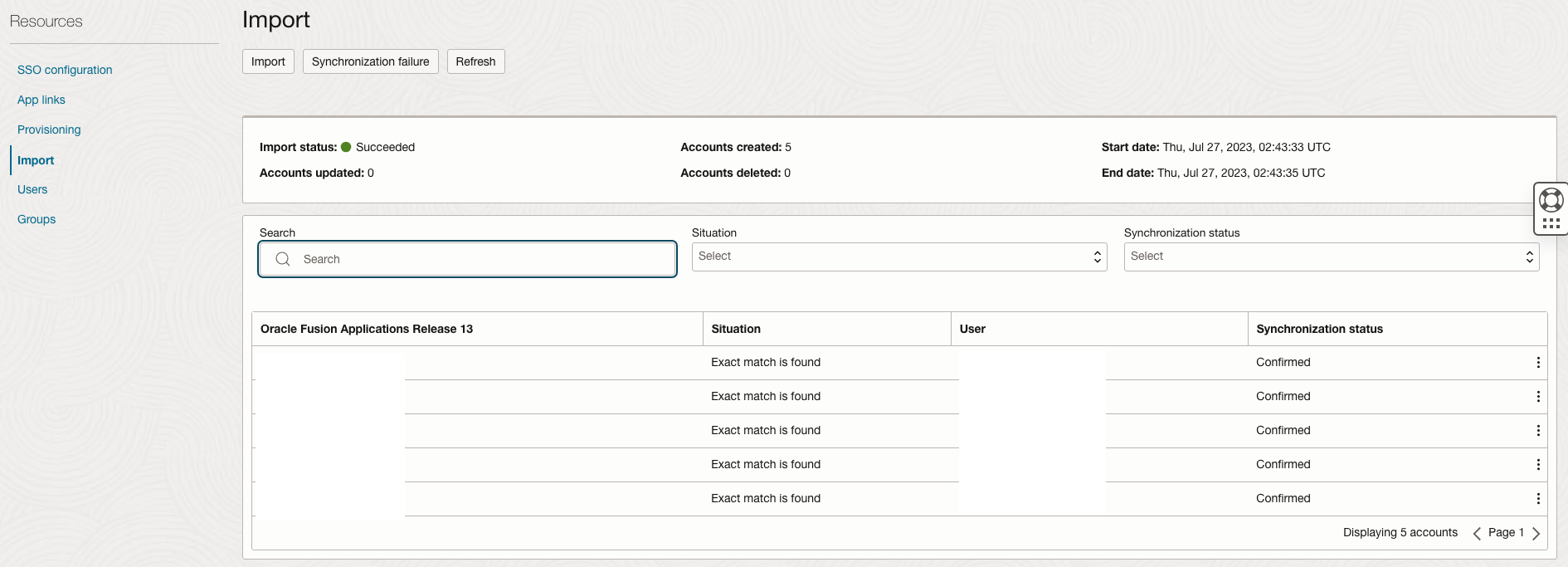
Repeat the steps above for the internal IAM domain – the internal IAM domain will have different Landing Page URLs compared to the external one. Adjust as required for your environment.
CRM Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/crmUI/faces/FuseWelcome
SCM Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/faces/FuseWelcome
HCM Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/hcmUI/faces/FuseWelcome
ERP Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/faces/FuseWelcome
In this example we want to have all employees synced to the internal IAM Domain – employees generally have the ORA_PER_EMPLOYEE_ABSTRACT role so we are using this as the synchronisation criteria.
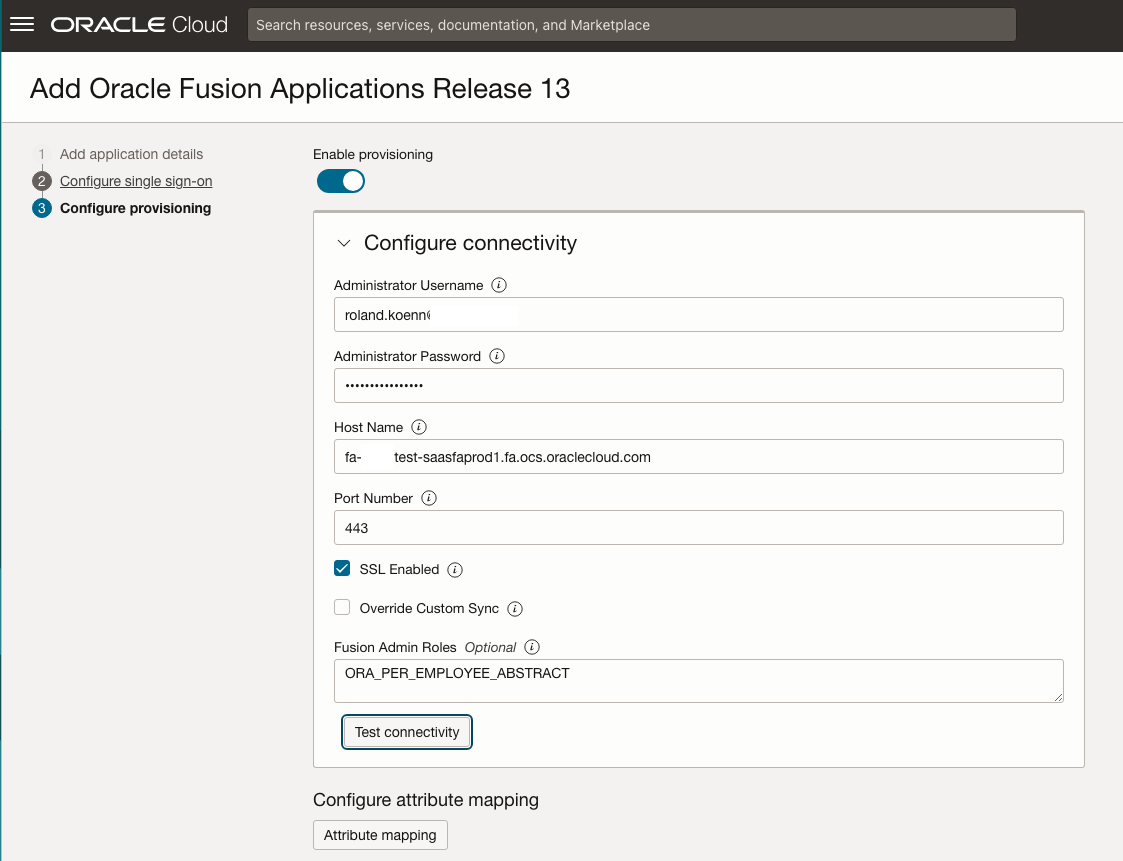
Ensure that the configuration is working as expected by running an import.
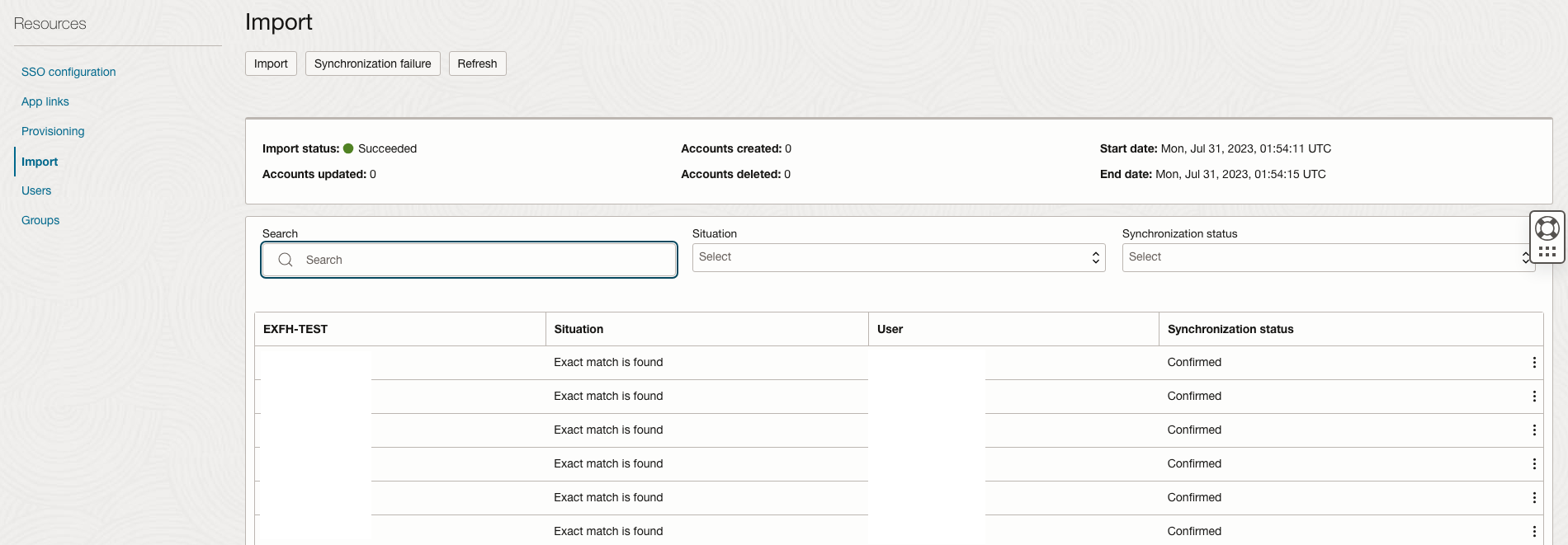
Head to the SSO Configuration Page for each Application and download the signing certificate and identity provider metadata files and name them carefully to make sure you can identify them properly. Keep these files for the next step.
Identity Provider (IDP) Configuration
Login to Fusion Applications and navigate to the Single Sign-On section of the Security Console. Add a new Identity Provider for the external IAM Domain first. Upload the downloaded IDCSMetadata.xml file and move to the next page to test.
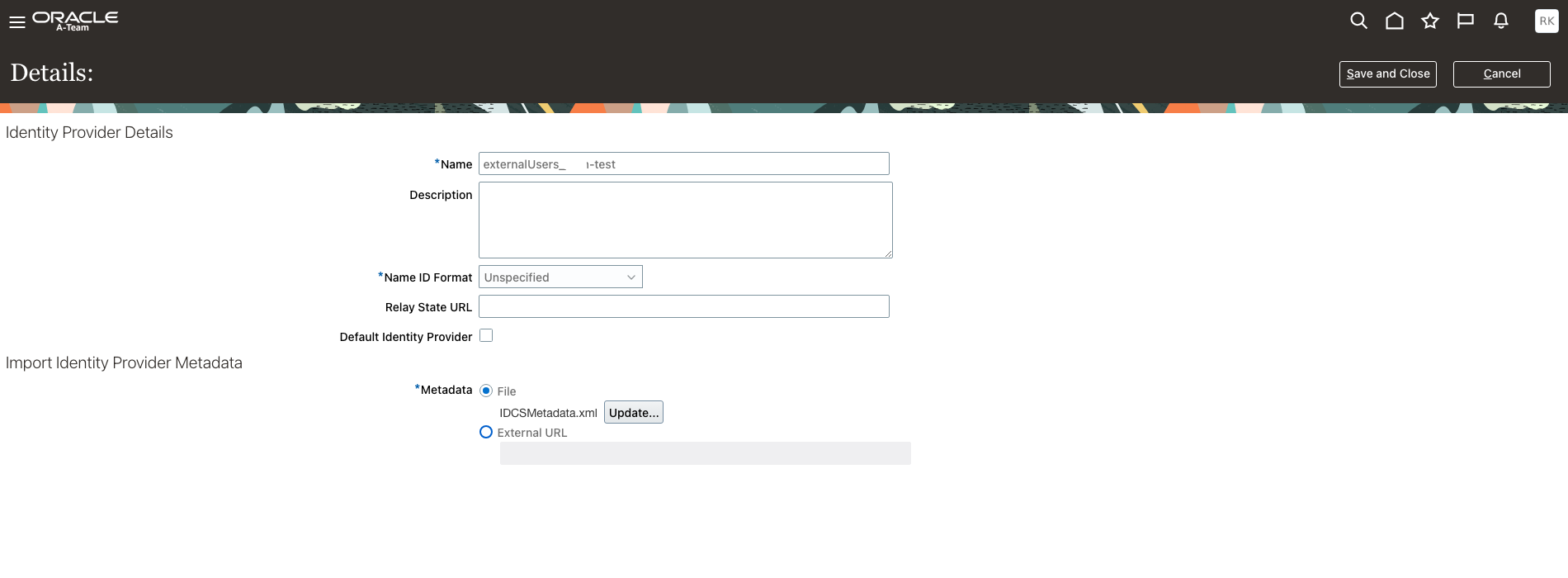
Select the external IAM domain as Partner and authenticate when challenged.
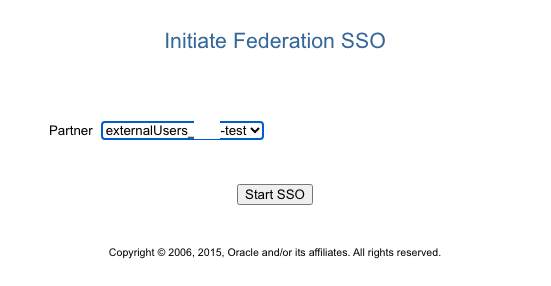
The expected outcome should look like this – do not proceed if any errors are present. If in doubt create a Service Request to get assistance.
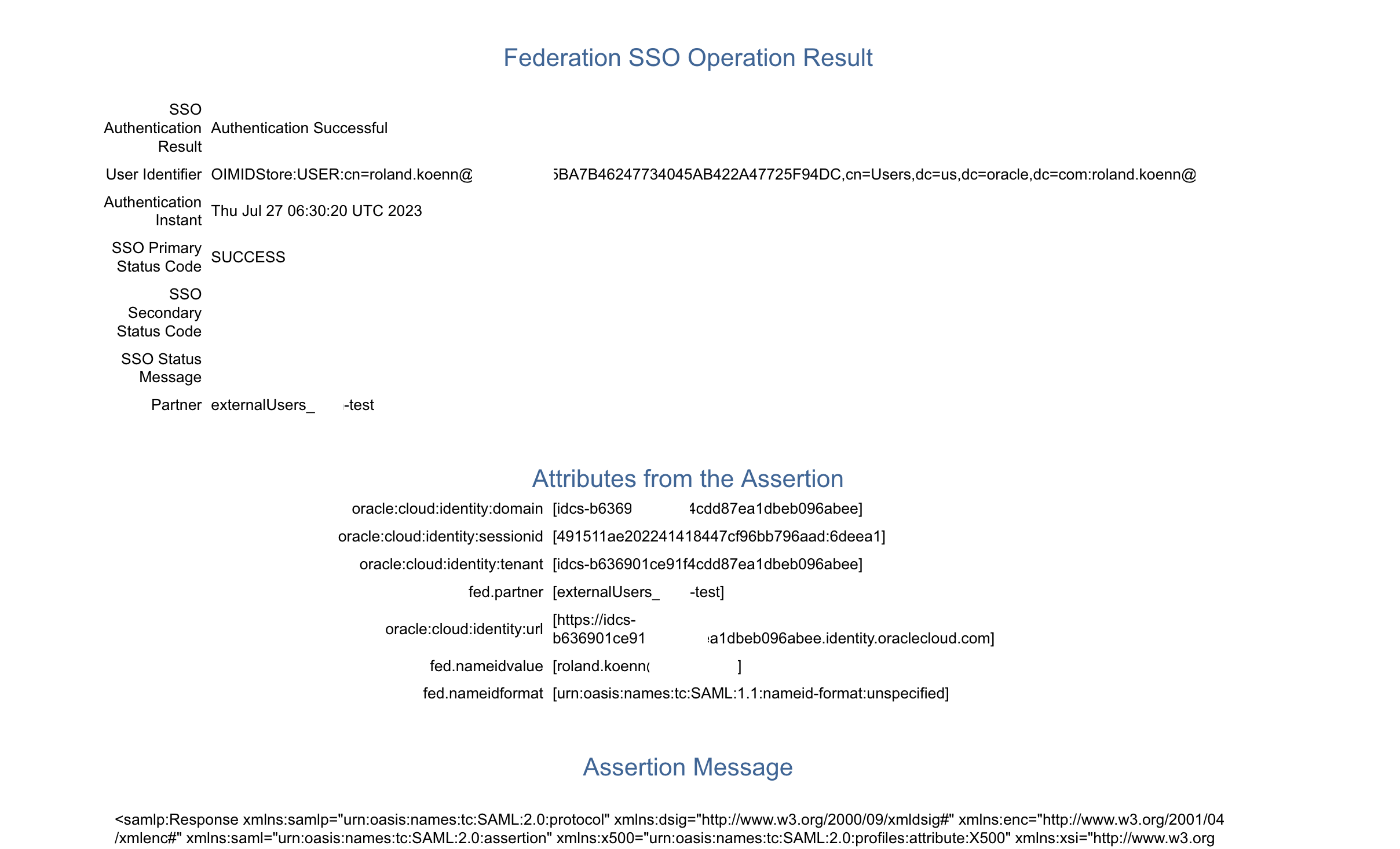
Repeat for the internal IAM domain and make sure both show up as enabled. For the troubleshooting we recommend enabling the Chooser Login Page – it should be disabled once the configuration is working as expected to avoid confusion and expose additional options for external users.
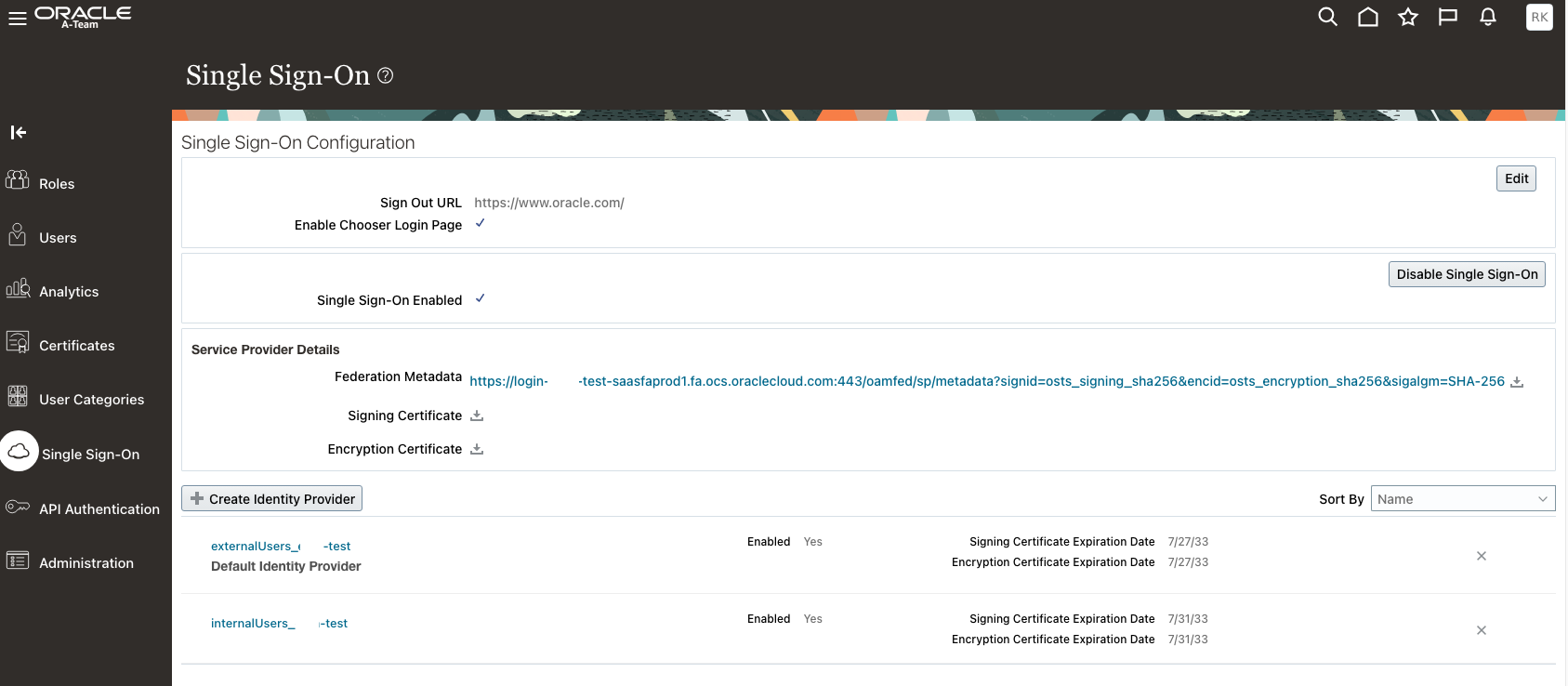
IdP Initiated SSO
The easiest way to retrieve the URLs for the IdP Initiated SSO is via the IAM Domain Console. Go to the Domain Homepage of the internal IAM Domain and copy the Domain URL.
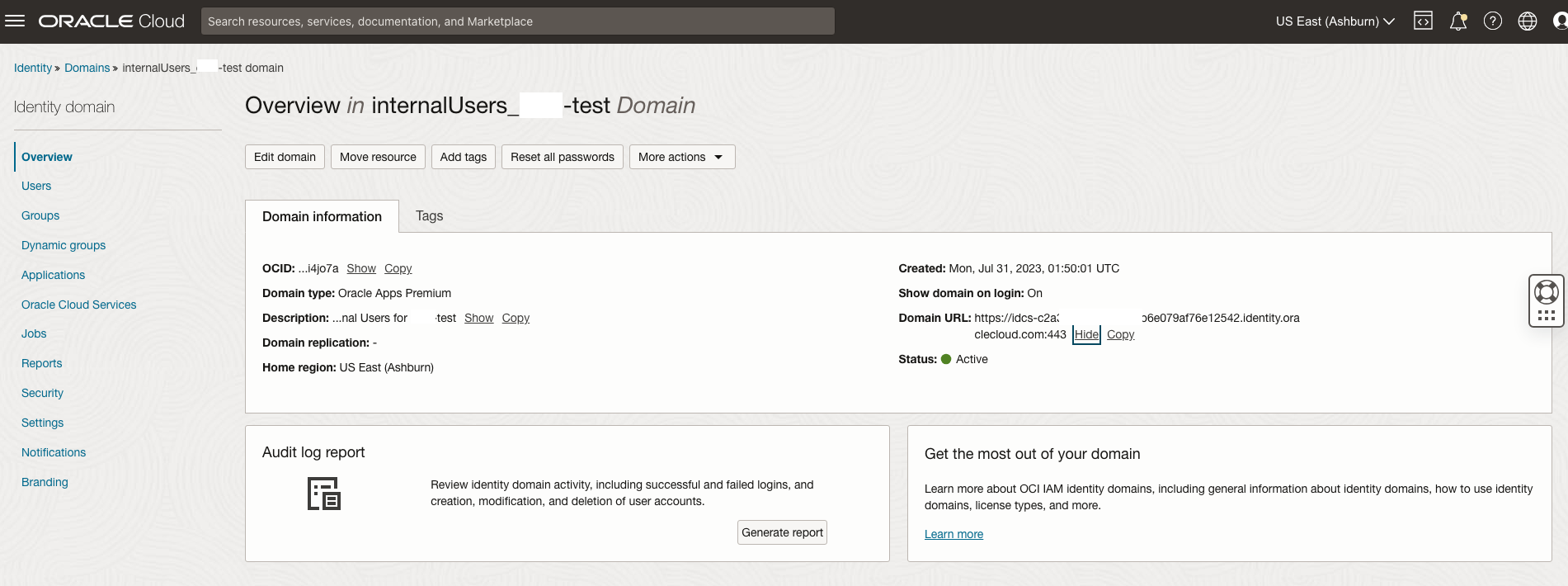
Simply add /ui/v1/myconsole to the end of the URL copied above similar to: https://idcs-XXXXXXXXXXXX.identity.oraclecloud.com/ui/v1/myconsole
Login with the user that is available in the domain to get to the following window – this console shows all apps available for the uses – copy the linked to the app you want internal users to use, e.g. for internal ERP users copy ABCD-TEST ERP App. This is the URL for the IdP initiated Login via the Internal IAM Domain created above and will look similar to:
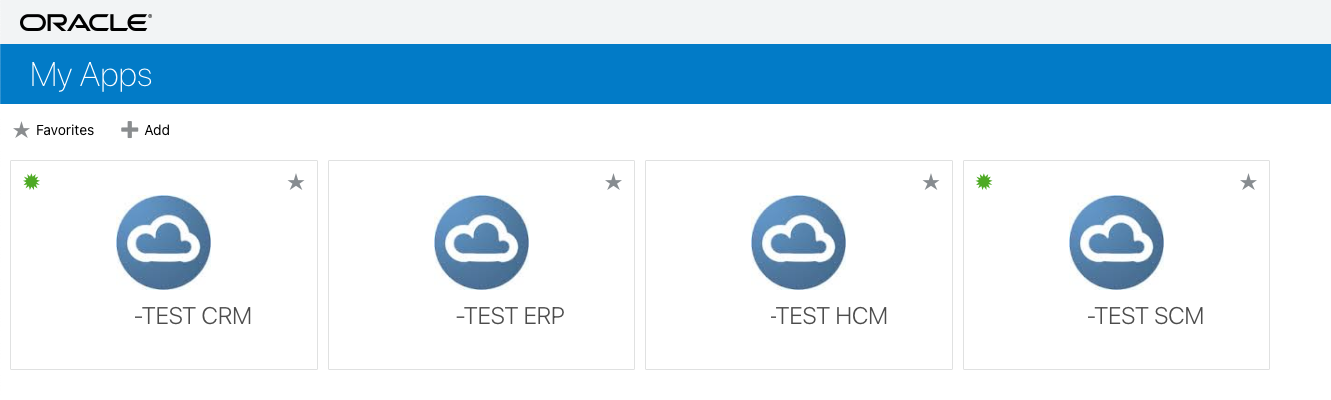
Using this URL will take the users directly to the Login of the internal domain and after successful authentication redirect the user to the configured landing page. Distribute this URL to the internal users. This is also available for external users – however these will in this configuration be redirected to the external IAM Domain automatically, even if they are entering the URL for Fusion, e.g. https://fa-ABCD-test-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/faces/BillManagementDashboard
Once everything is working as expected. Login back to the Security Console and disable the chooser page to disable the Login directly into Fusion and force users to use the IAM Domains created.
Securing IAM Domains
The next step is to setup additional security measures as required on top of the IAM Domains to increase the security overall – this could include for example:
1. Consider using MFA for all internal and external Users.
2. Implement Network Perimeters on the internal IAM Domain to restrict logins to known internal IPs only. This works great in conjunction with LBAC.
3. Review Auditing and Reporting setting the IAM Domains to match your requirements.
4. Review additional IAM Security options, e.g. here.
Conclusion
Introducing IAM Domains into your Oracle Fusion Cloud Applications landscape is strong improvement of the overall security footprint. Especially in external facing environments IAM Domains allow a finer adjustment and more control in regards to most customer security requirements. IAM Domains in conjunction with OCI Streaming can be a great solution to feed into SIEM solutions, like Splunk or QRadar.
Further Reading
IAM with Identity Domains – https://docs.oracle.com/en-us/iaas/Content/Identity/home.htm
Setup Bill Management – https://docs.oracle.com/en/cloud/saas/financials/23c/fairp/set-up-bill-management.html
