Overview
Update March 2025: Some aspects of this architecture will change with the Oracle Fusion Identity Upgrade—details available here. We will update this document accordingly once the upgrade begins.
A key focus at the top of the agenda for all of our customers is Security – one increasingly popular option to step up the overall security of their Oracle Fusion Cloud environments is Multi-Factor Authentication (MFA). We generally recommend enforcing MFA at a minimum for all Power and Admin Users and where possible even all users for the Fusion Cloud as well as the OCI Console. At this stage end users are very comfortable with the use of MFA, as it is established for use with banking and many other personal applications.
MFA requires users to provide more than one factor to identify themselves. This way MFA reduces for example the risk of compromised passwords. Hackers would not be able to log on to the system with only the compromised username and password, but additionally they would have to have access to the mobile app like Oracle Mobile Authenticator to generate a time-base one-time password (TOTP) to successfully login. The app however is secured and only installed on the rightful user’s mobile phone rendering a compromised password alone as unusable.
There are multiple ways and options how to implement MFA, e.g. through Okta or Azure AD. For this example MFA will be implemented via IAM. The configuration has become even easier with the introduction of IAM with Identity Domains. For this example, a new IAM domain is created and federated with Fusion Applications as shown in the picture below.
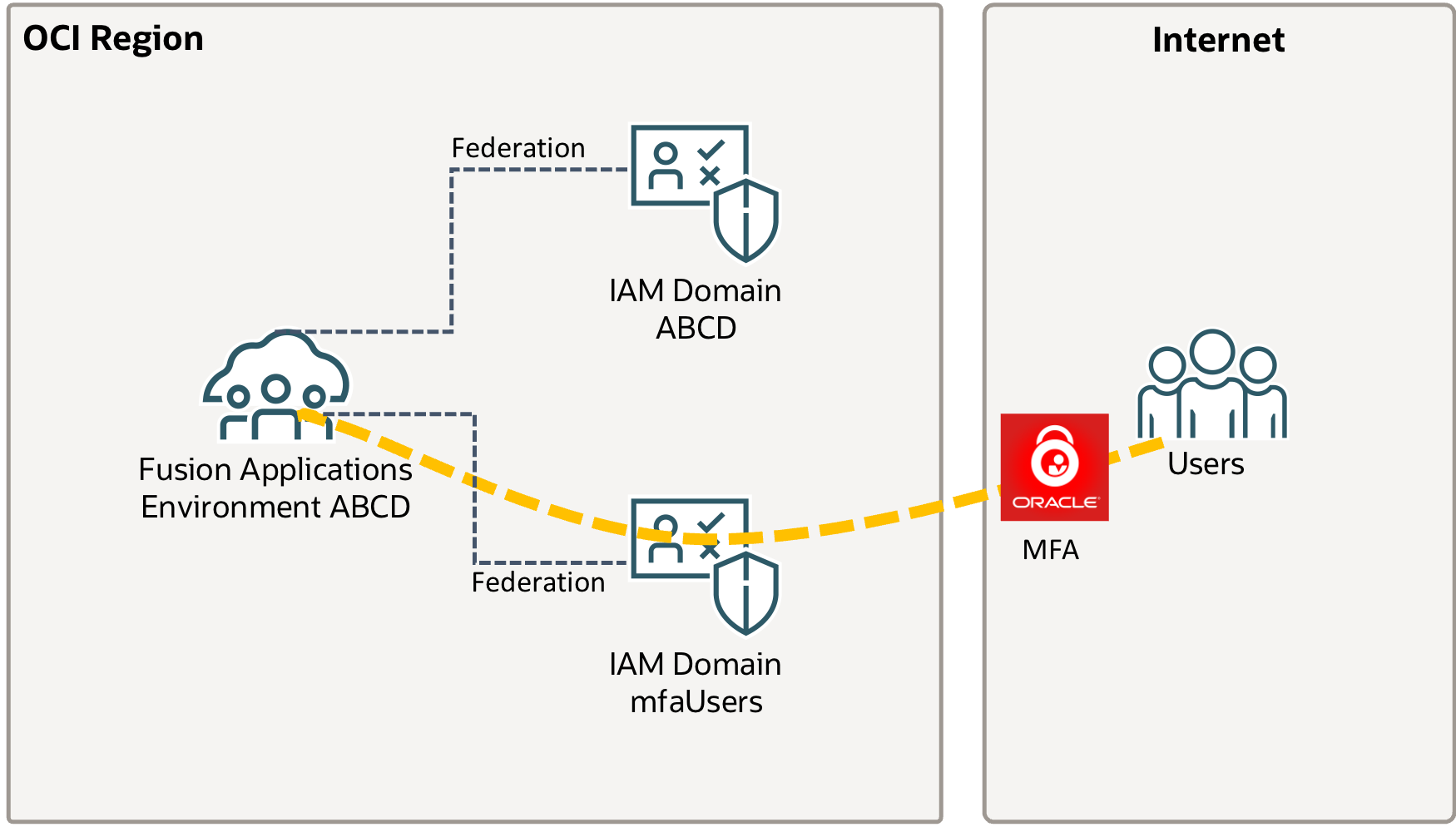
Please note the pre-existing IAM Domain / IDCS Stripe created with the Fusion Applications environment is not part of this solution. Users authenticate with Fusion Applications using the new IAM Domain, which will enforce the use of MFA.
IAM Domain – Fusion Cloud Federation Setup
In preparation for this setup login to Fusion Applications with an account that has the IT Security Manager Role. Navigate to the Security Console – click Single Sign-On and Download Federation Metadata as well as the Signing Certificate.
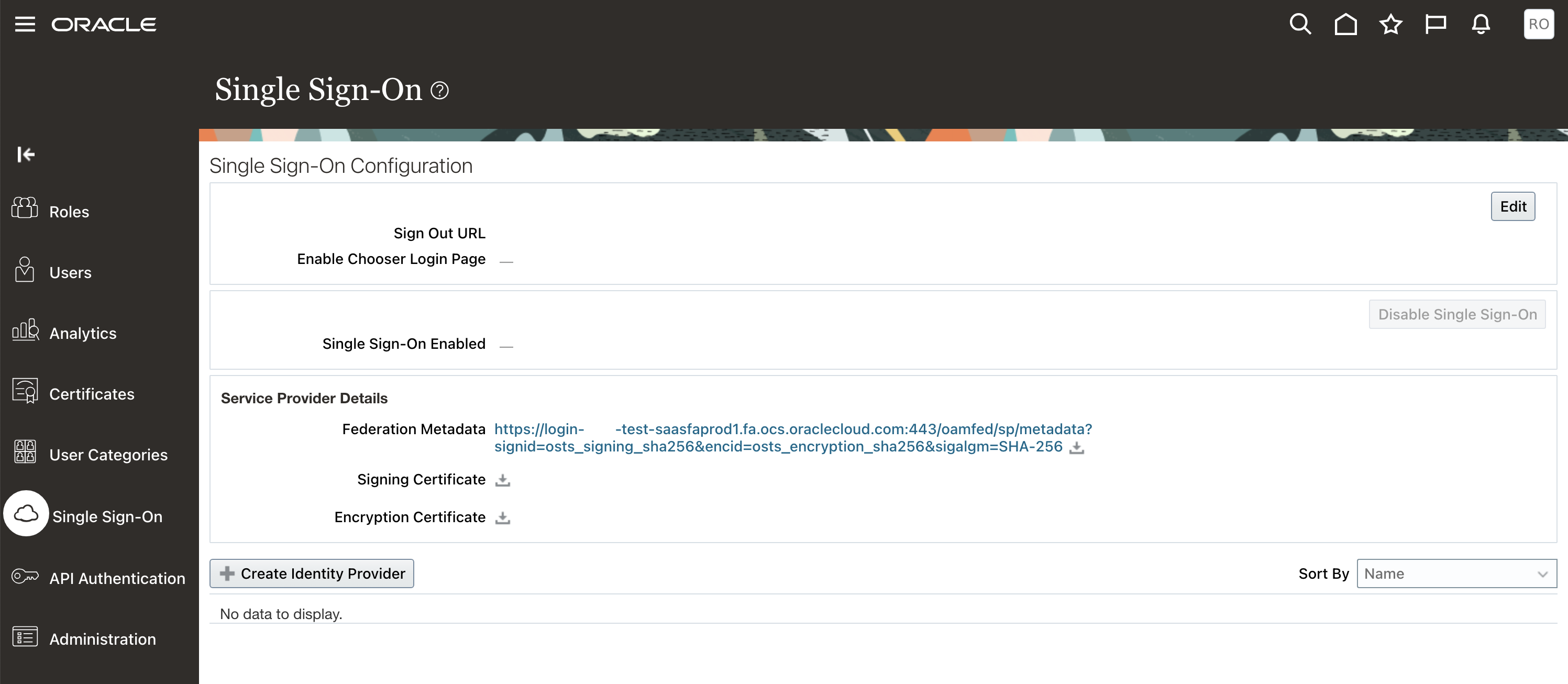
Open the Federation Metadata XML and look for the entityID attribute, e.g. https://login-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com:443/oam/fed
![]()
Open Metadata and search for the AssertionConsumerService entry. Take Note of the Location attribute, e.g. https://login-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/oam/server/fed/sp/sso
![]()
Search for SingleLogoutService entry and note down the Location attribute, e.g. https://login-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/oamfed/idp/samlv20
![]()
Login to the OCI Console with an Administrator user for your tenancy and navigate to the Domains page in Identity & Security. Create a new domain – please select carefully which type of domain suits your specific use case – all the details and differences can be found here. For this example, the Oracle Apps Premium is the best choice.
Once created you will receive an email to activate your user and set a password. Afterwards navigate to the Applications Section in the newly created domain and hit Add Application. Make sure to select Application Catalog and continue by clicking “Launch app catalog”. Search for “Oracle Fusion Applications Release 13” and click on the highlighted result.
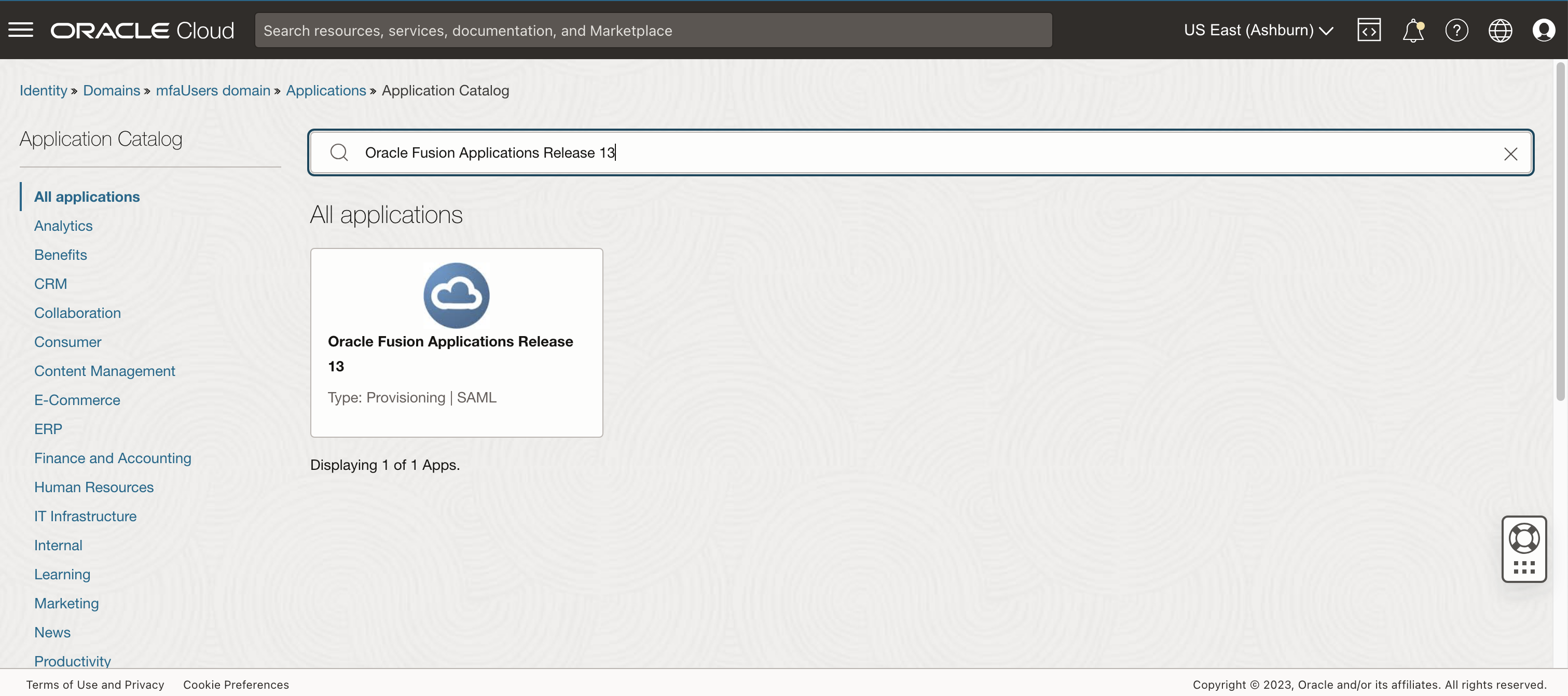
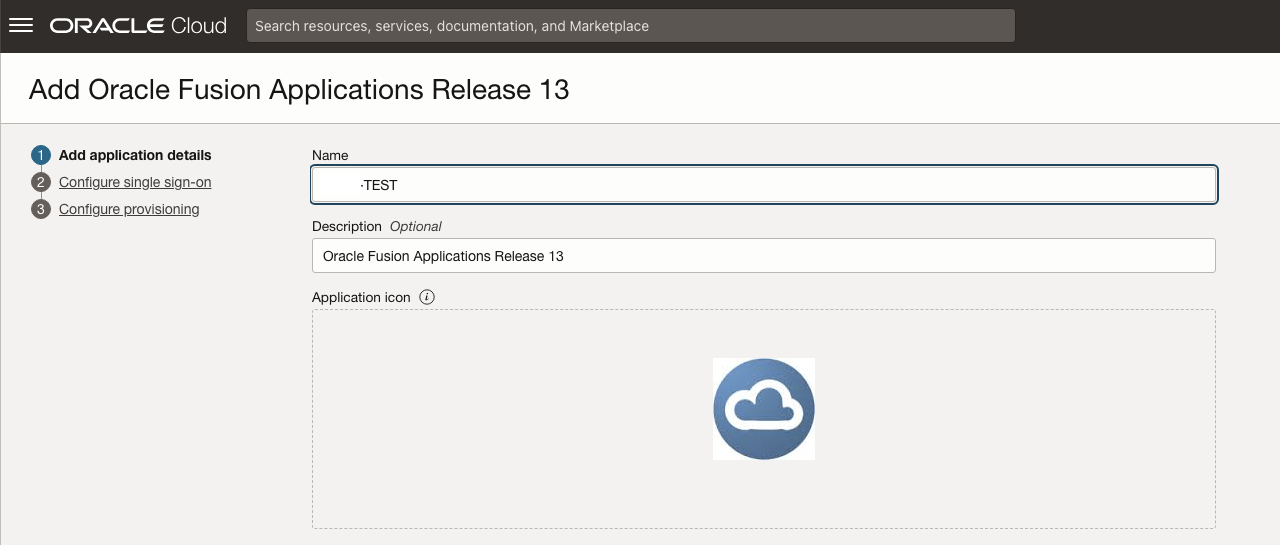
Give the Application a meaningful name – for example the environment name – and select your preferred landing pages these could for example be where XXXX is you environment name:
CRM Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/crmUI/faces/FuseWelcome
SCM Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/faces/FuseWelcome
HCM Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/hcmUI/faces/FuseWelcome
ERP Landing Page URL: https://fa-XXXX-test-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/faces/FuseWelcome
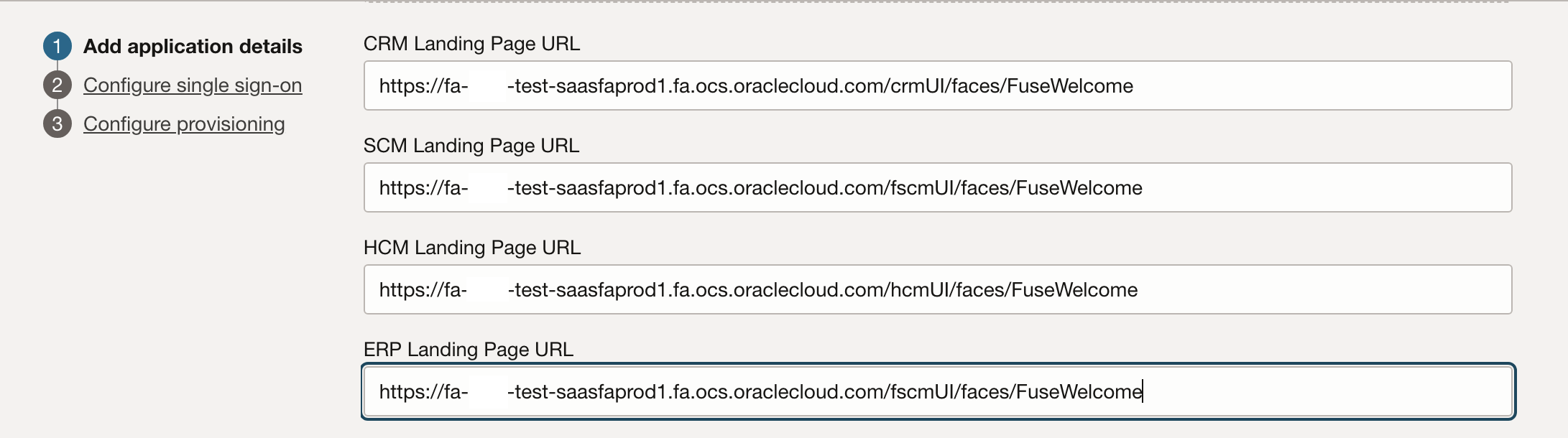
Near the bottom of the page in the Authentication and Authorization section, select the Enforce Grants as Authorization check box if you only want users that are assigned to the application to access Fusion. All settings on this page are discussed here.
On the next page make sure to download the signing certificate and identity provider metadata. For Entity ID and assertion consumer URL refer to the details retrieved above. Upload the signing certificate retrieve from your Oracle Fusion Cloud environment earlier (.cer file).
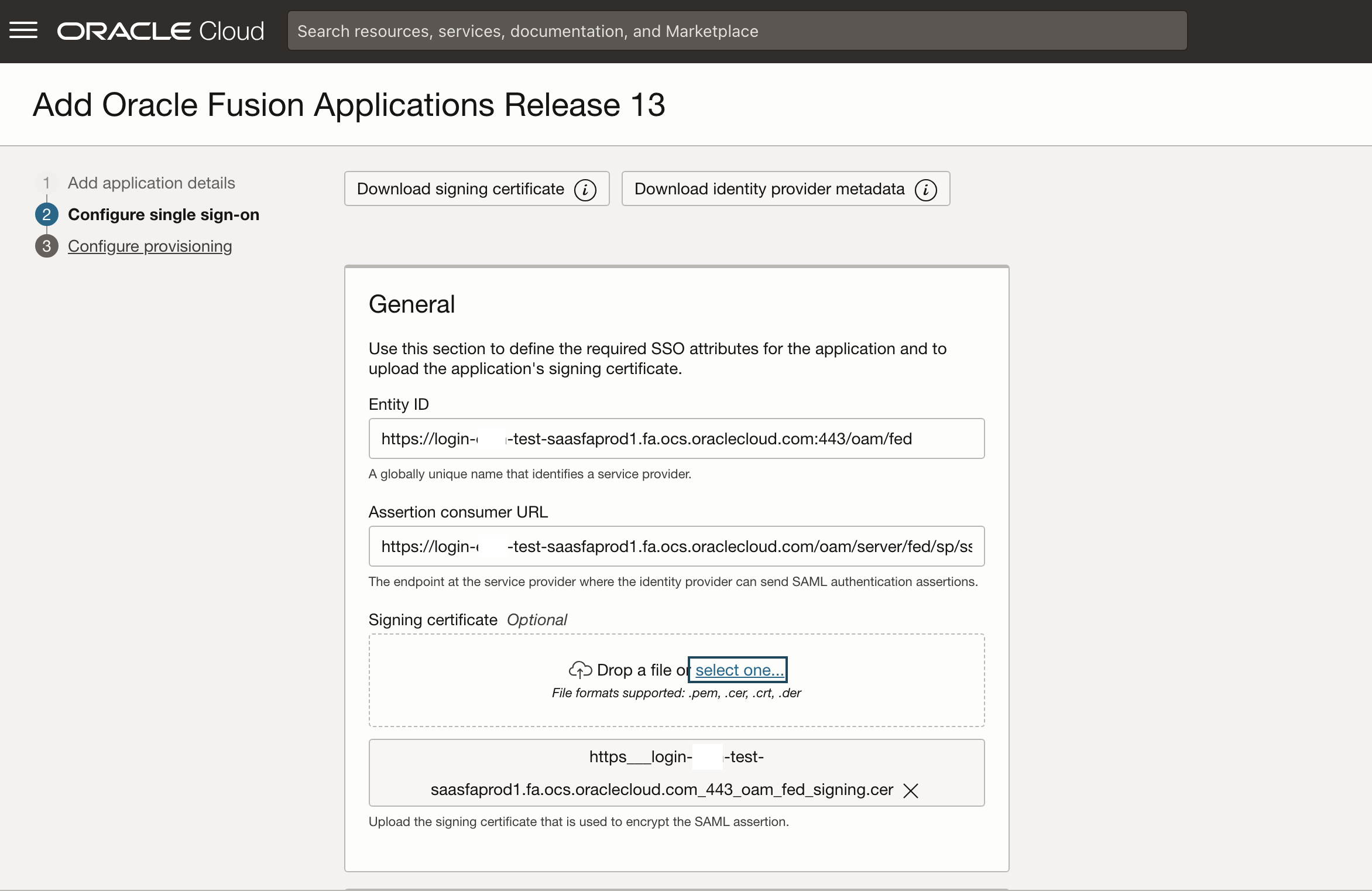
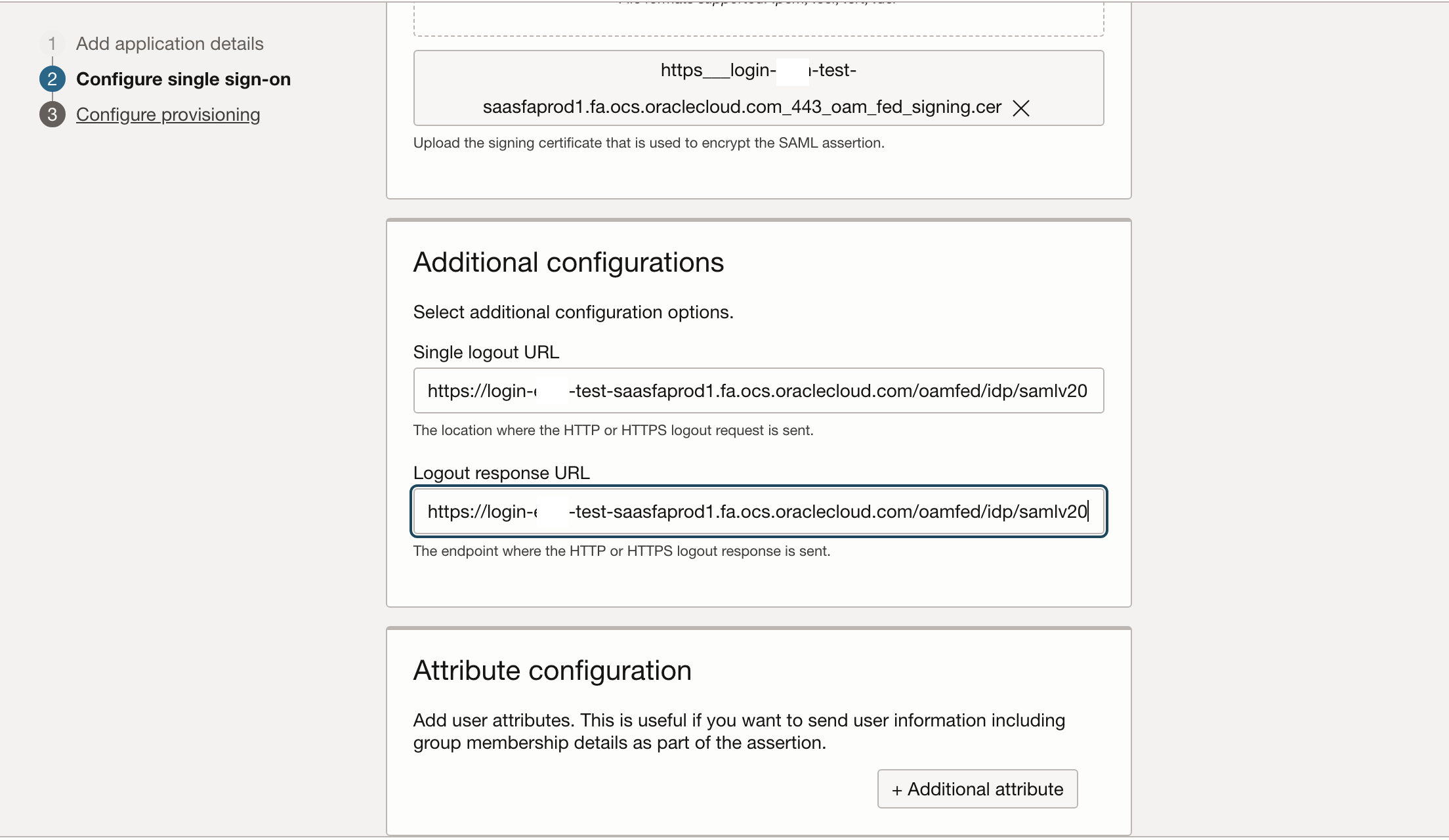
The single logout URL and logout response URL are also retrieved above as SingleLogoutService.
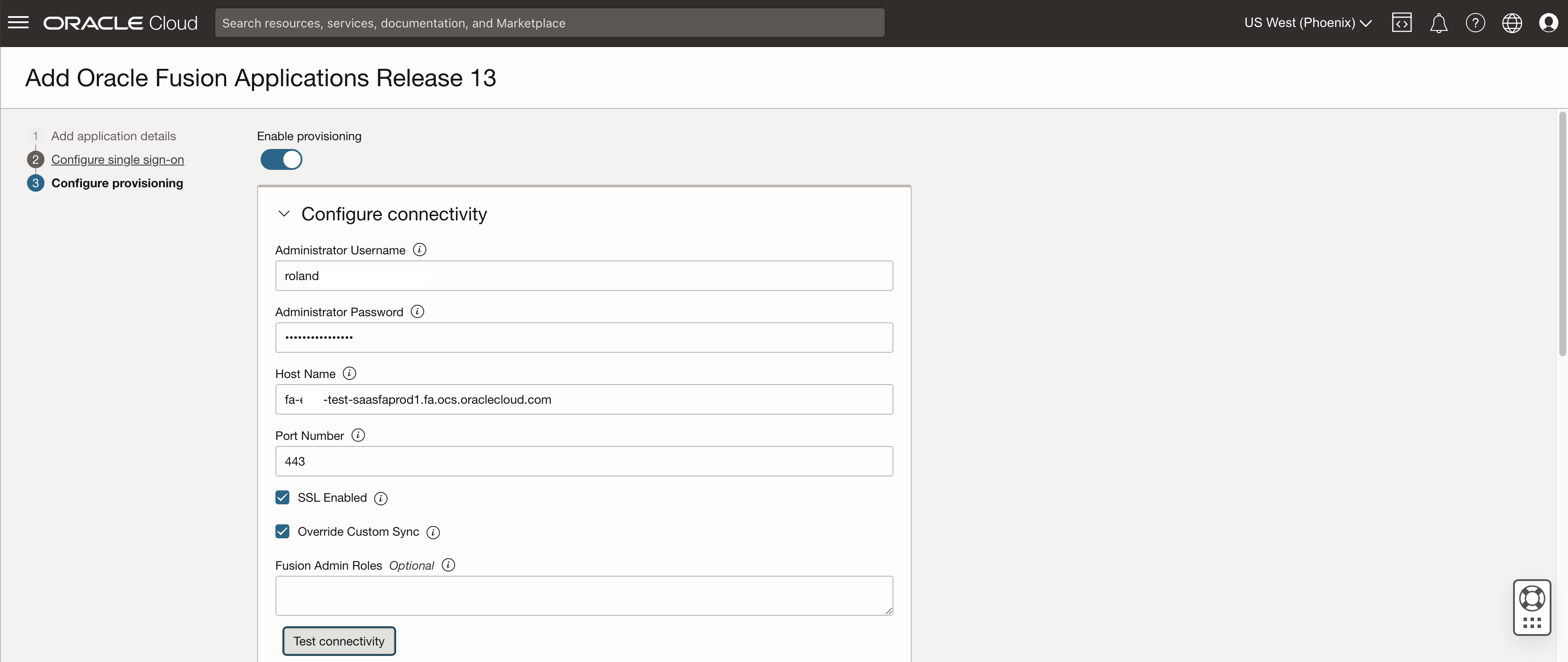
For this example we are simply going to sync all users between the IAM domain and Fusion Applications – configuration details are here. Make sure to test the connectivity and then scroll further down. The user running the sync needs to have the role ASE_REST_SERVICE_ACCESS_IDENTITY_INTEGRATION_PRIV – reference here.
Choose to enable the Authoritative sync – all details can be found here.
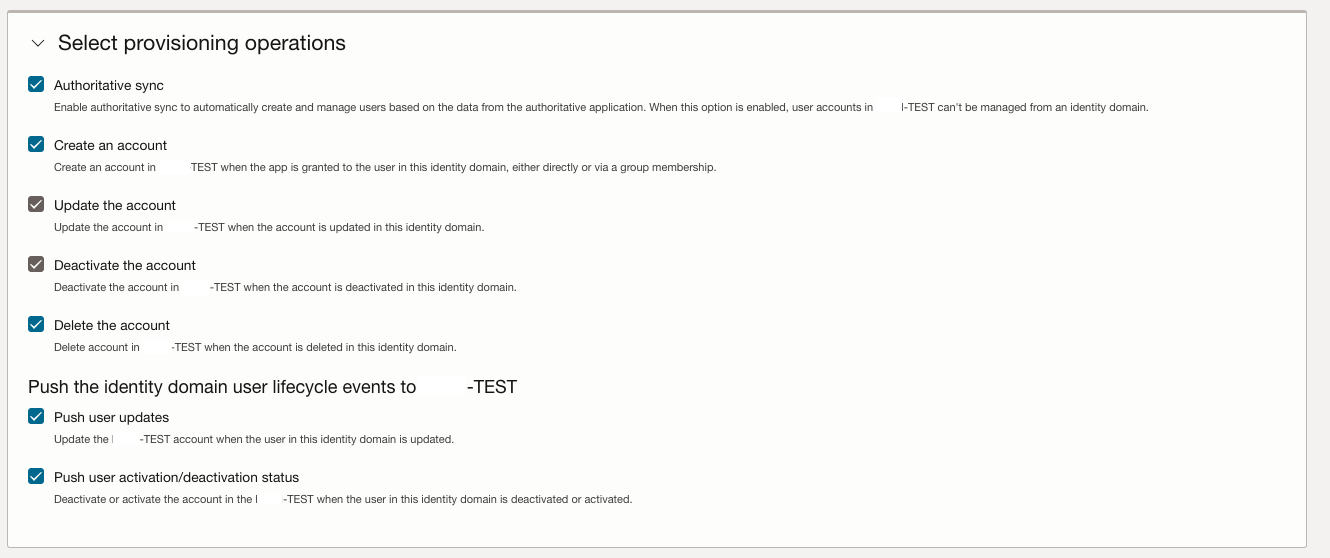
Enable the synchronization and set a schedule that matches your requirements – daily is good starting point, but increased should be considered where frequent change in users is required.
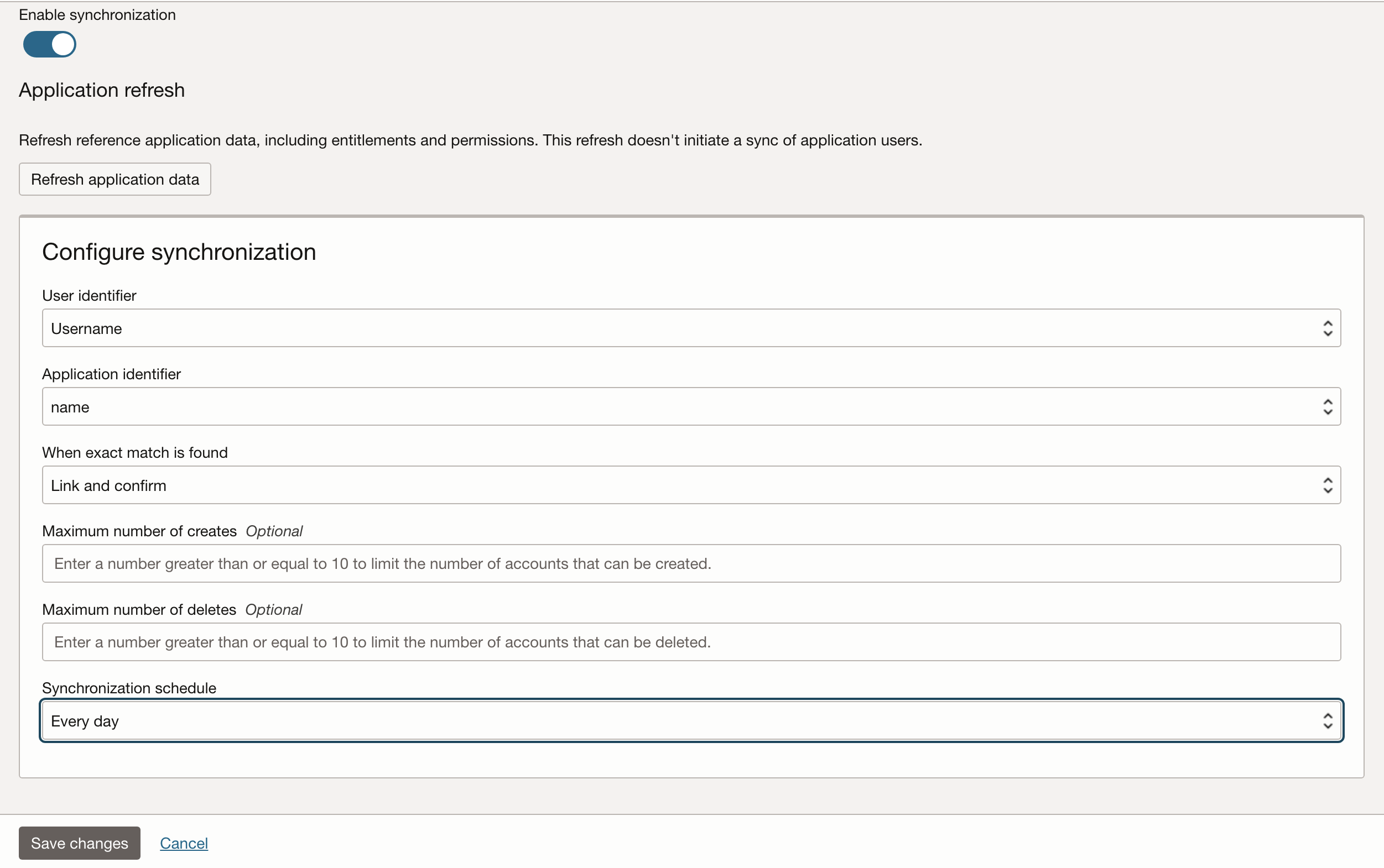
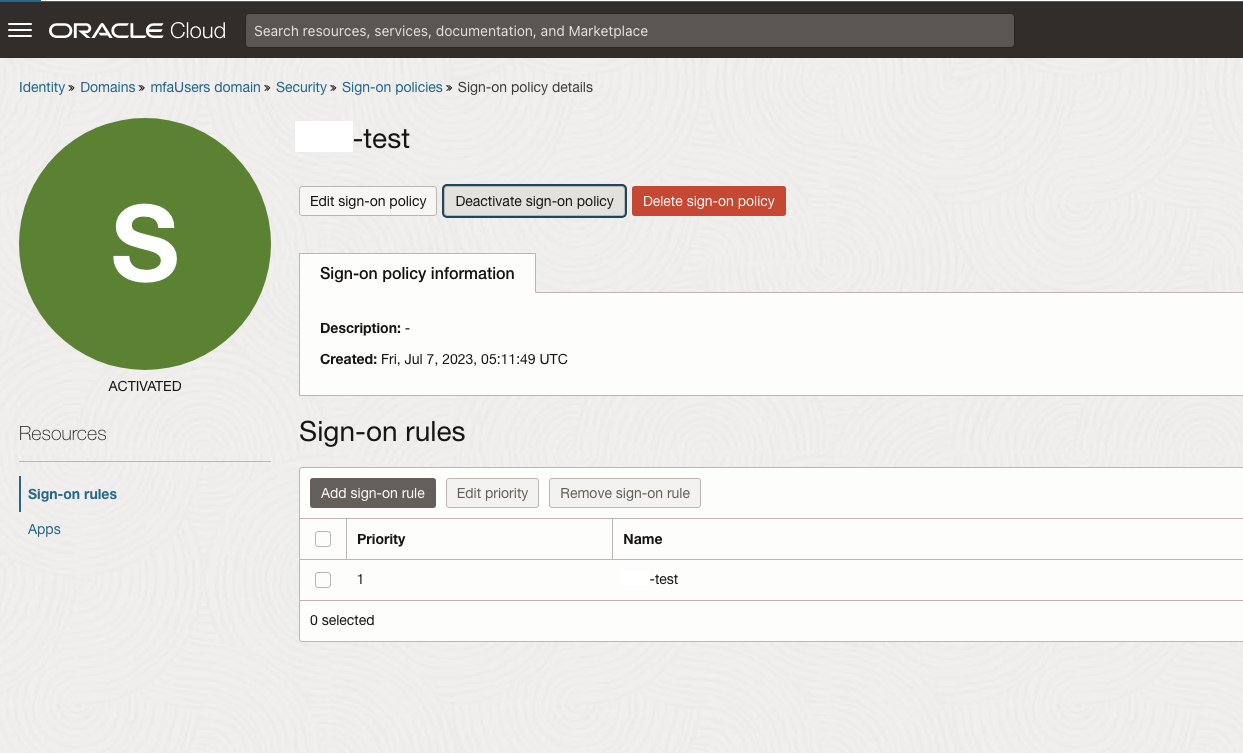
Once the application is created in the Domain – hit the activate button and wait for the circle to turn green.
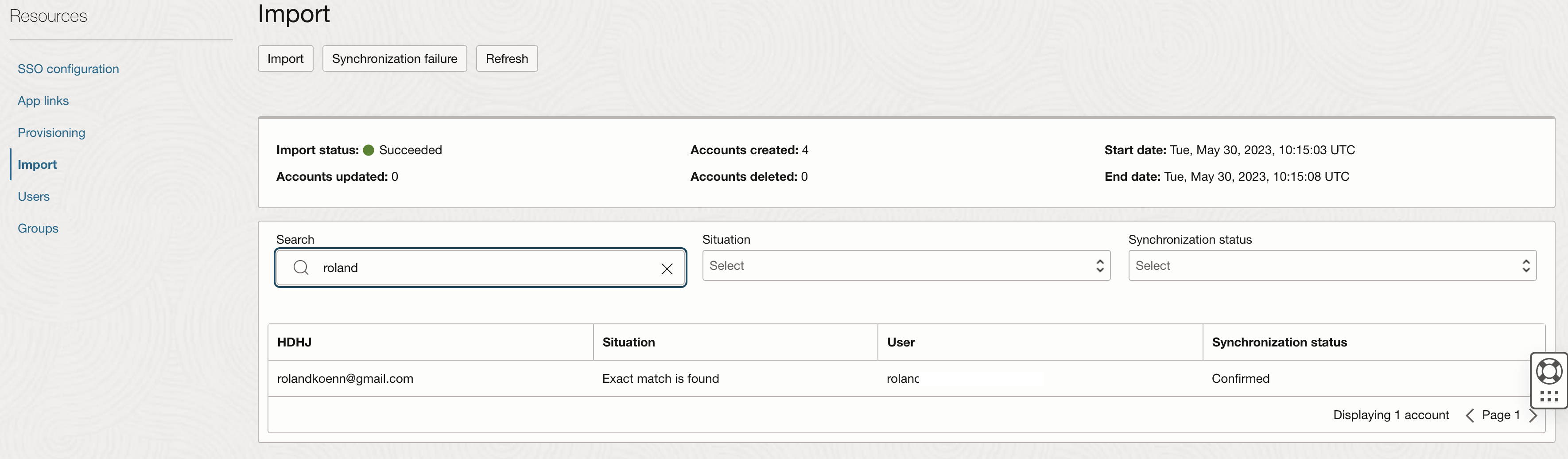
Once enabled make sure to run the import procedure to validate the configuration and create the users for immediate testing. Make sure to create and delete additional users to ensure that the configuration works as expected.
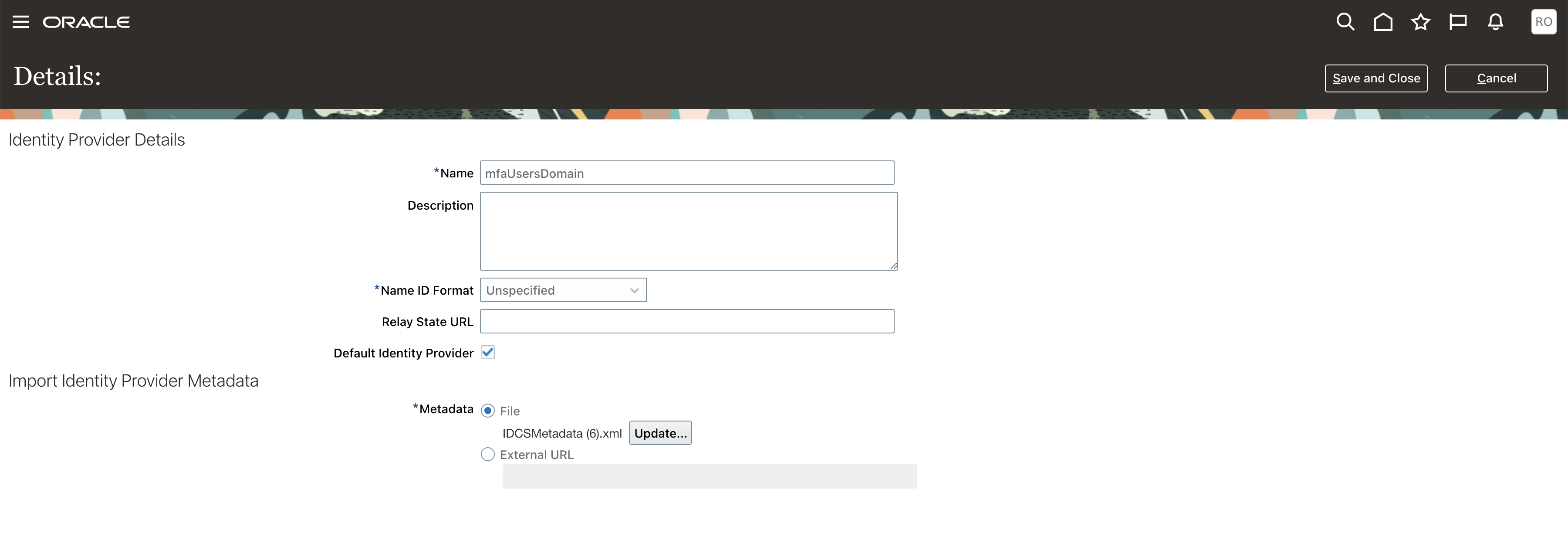
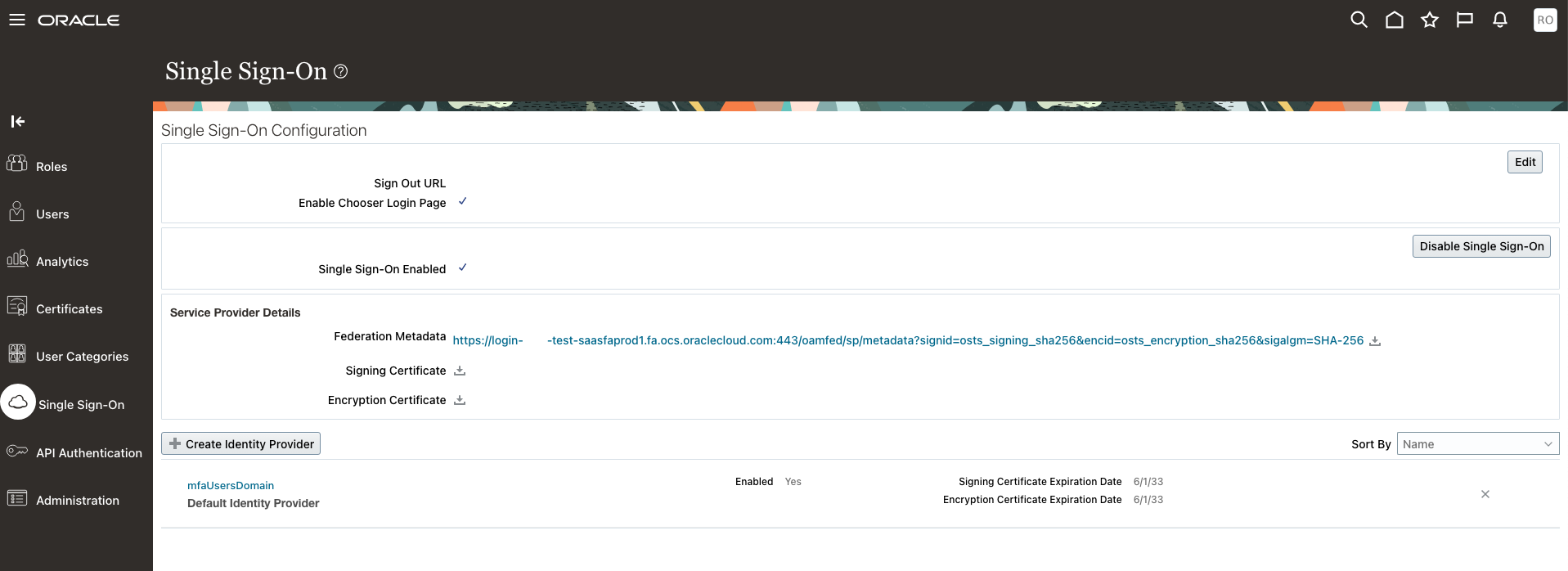
Return to Fusion Application and open the Security Console. Navigate to the Single Sign-On section and create a new Identity Provider (IDP). Once the page loads hit the edit button at the top. Assign a name and select the IDCSMetadata.xml file that was downloaded from the newly created IAM Domain and hit Save and Close at the top.
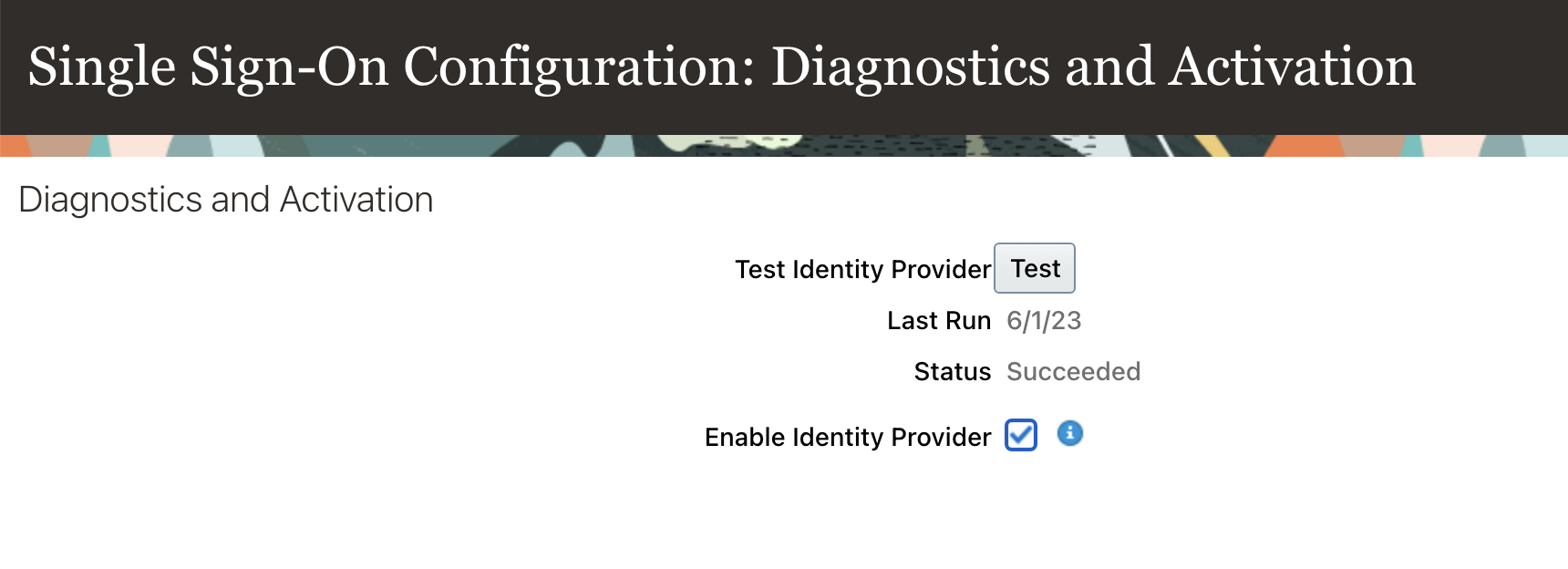
Hitting the “>” at the top brings up the Diagnostics and Activation Section. Running the Test Identity Provider will take a few moments – please note the IDP can only be activated after the test ran successfully.

The test msut succeed as shown here in order to proceed. Revisit all settings if there are errors and if in question raise a Service Request with Oracle Support.
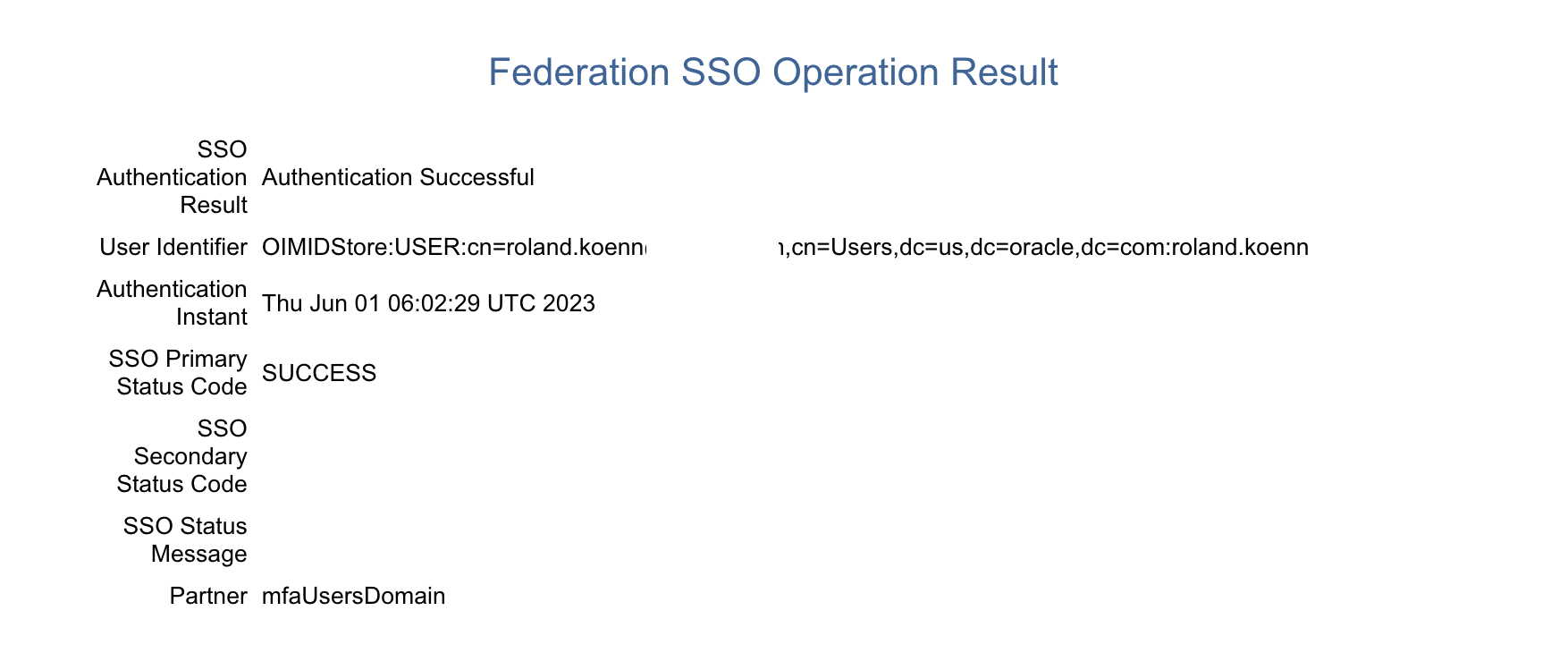
At this stage it is strongly recommended to try the login to the OCI Console for the IAM Domain from another browser or workstation to avoid any lockout issues.
Once the test is successful, hit edit at the top and select the “Enable Identity Provider” checkbox followed by clicking the “Save and Close Button”.
From this point forward users will be redirected to the Domain login page to authenticate.
For easier troubleshooting it’s recommended to enable the Chooser Login Page in the Security Console.
MFA Configuration
Oracle recommends configuring Mobile app passcode, Mobile app notification and Fast ID Online (FIDO) as we consider these phishing-resistant – all options are discussed here.
Login to the OCI Console with the new domain and navigate to the MFA page of the Security page in the newly created IAM Domain. We are selecting Mobile app passcode, Mobile app notification and Fast ID Online (FIDO) as factors for this example. Also select Bypass code to allow generating codes in case for example a user loses their access to the mobile app.
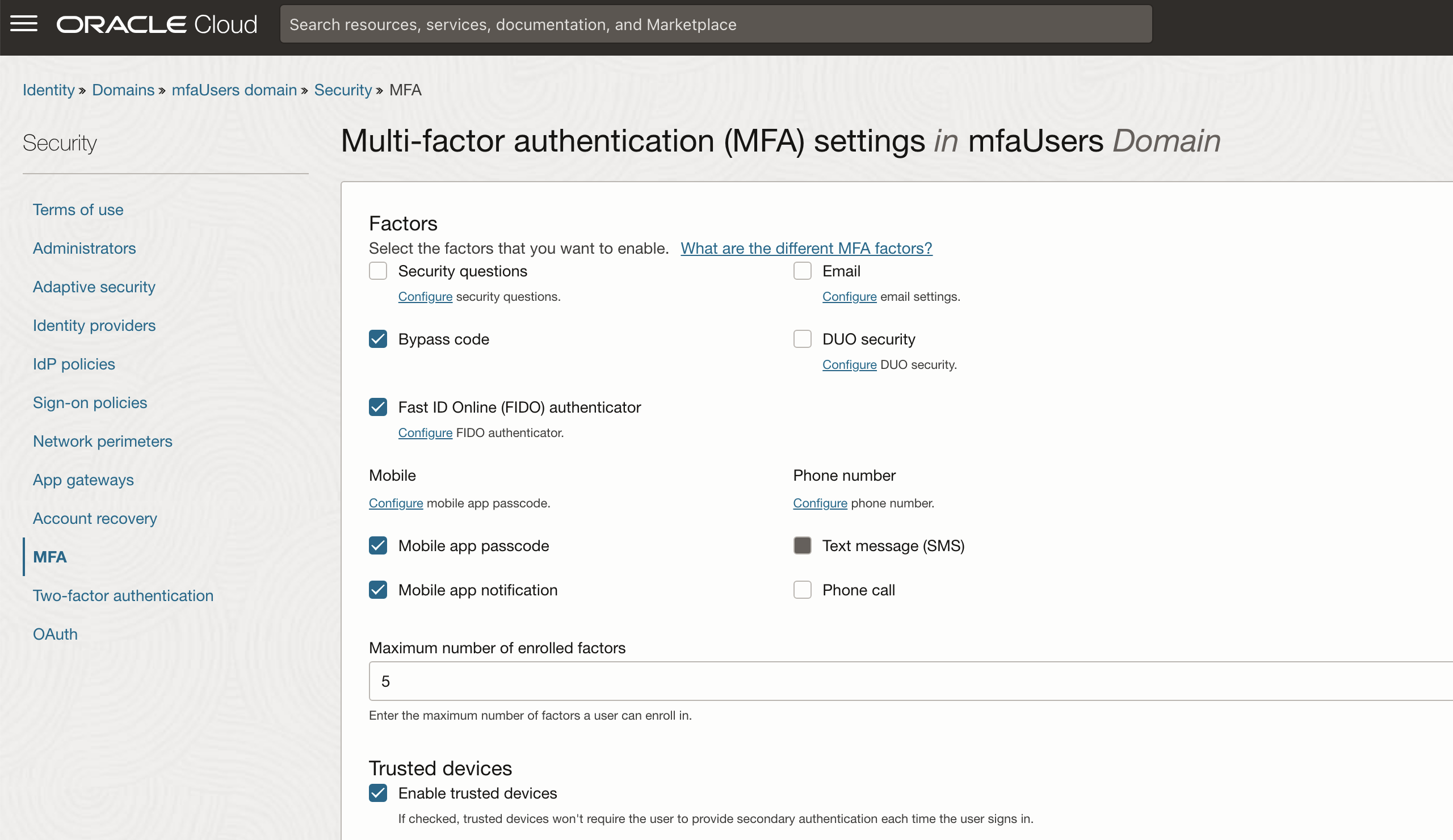
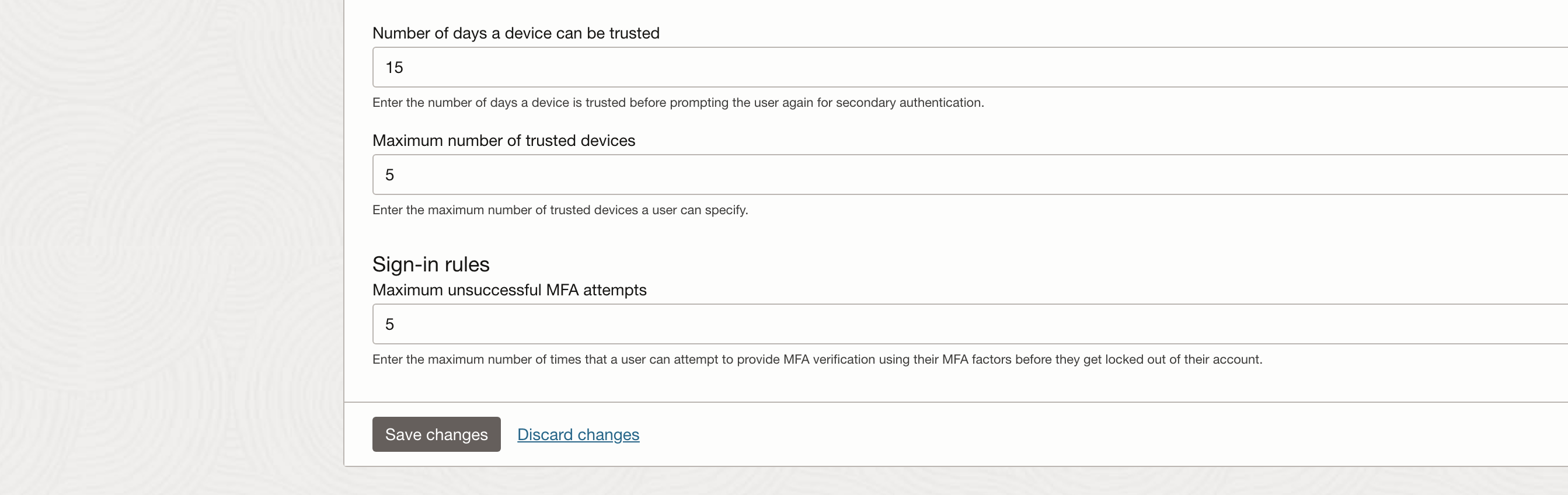
Adjust trusted devices settings to your requirement we recommend lowering the Maximum unsuccessful MFA attempts to no more than 5. These settings need to be hardened to your specific requirements.
The next step is to create a Sign-on Policy – make sure to stay in the newly created domain navigate to the security section and select the Sign-on policy. Create a new Sign-on policy with the name of your application / environment name.
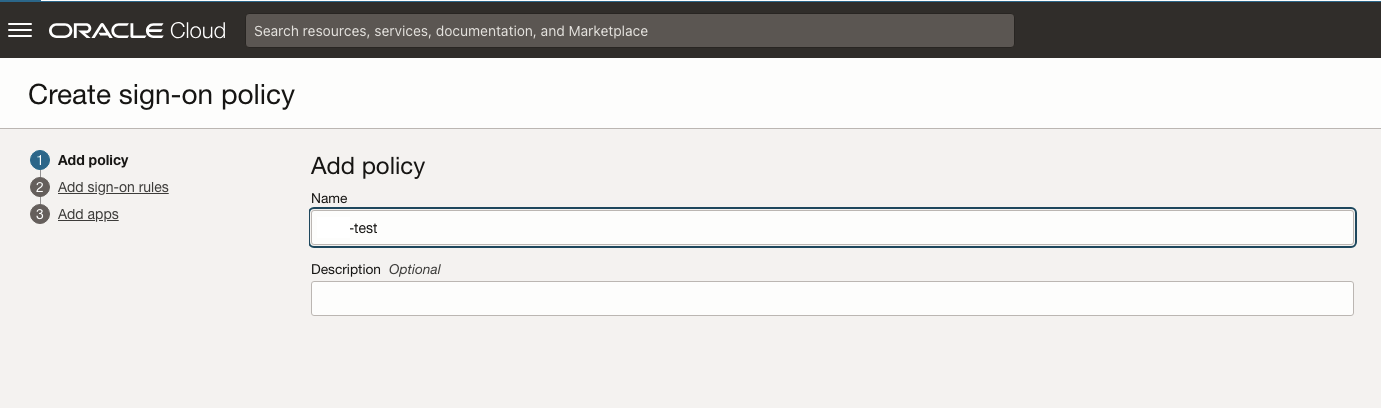
Details about Sign-On Policies and Rules are document in much detail here.
The next screen is key for a secure configuration so select the options carefully – make sure to only select the authenticating identity provider you want to allow to be used with the Fusion Cloud.
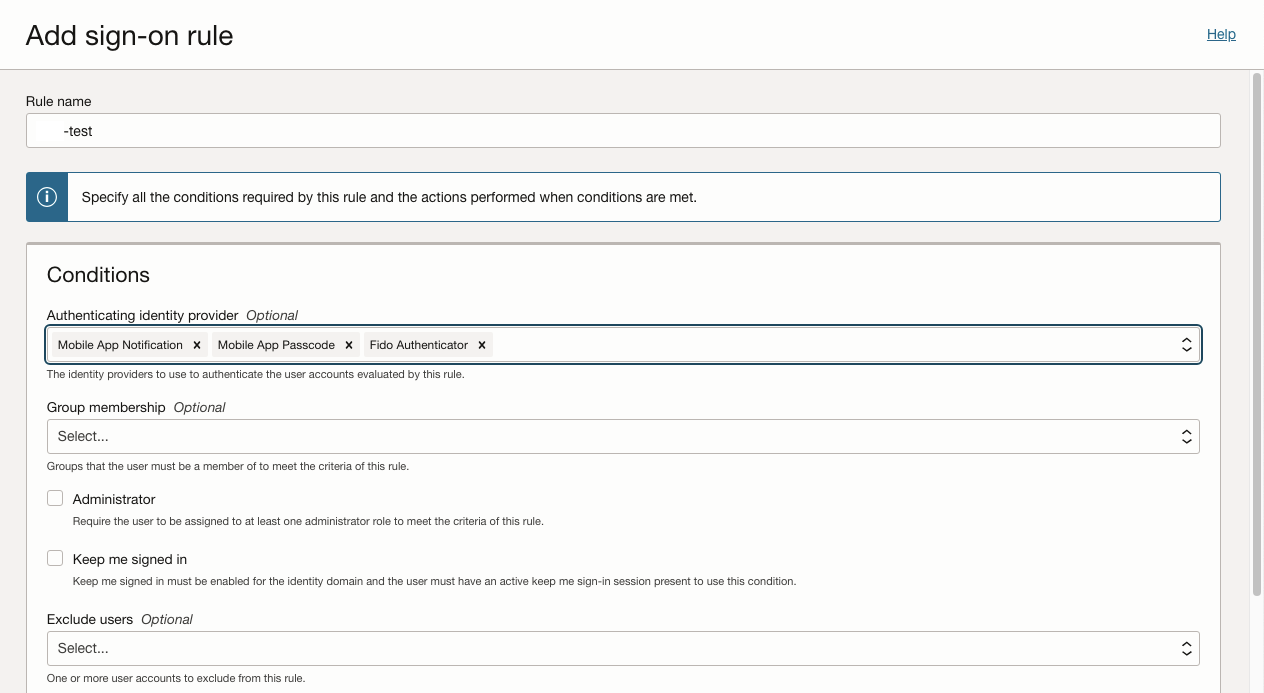
Further down in the screen, it’s important that you check the Prompt for an additional factor checkbox for MFA to work properly. Adjust all settings to your specific requirements. This example is generic and only illustrates a simple way to configure this. Review your choices and hit “Add sign-on rule” to continue.
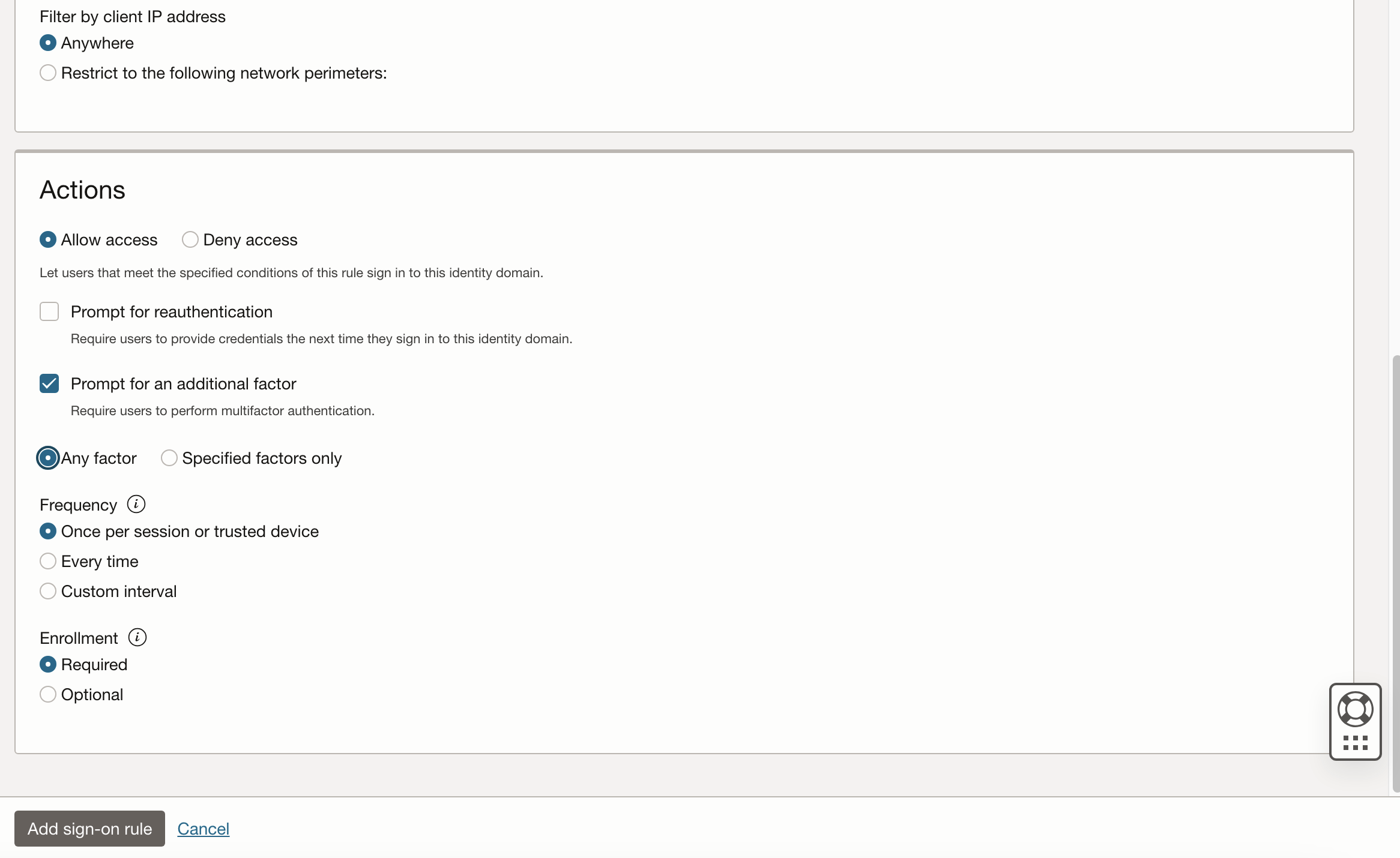
Link the previously created app with the sign-on policy to enable MFA for Fusion.
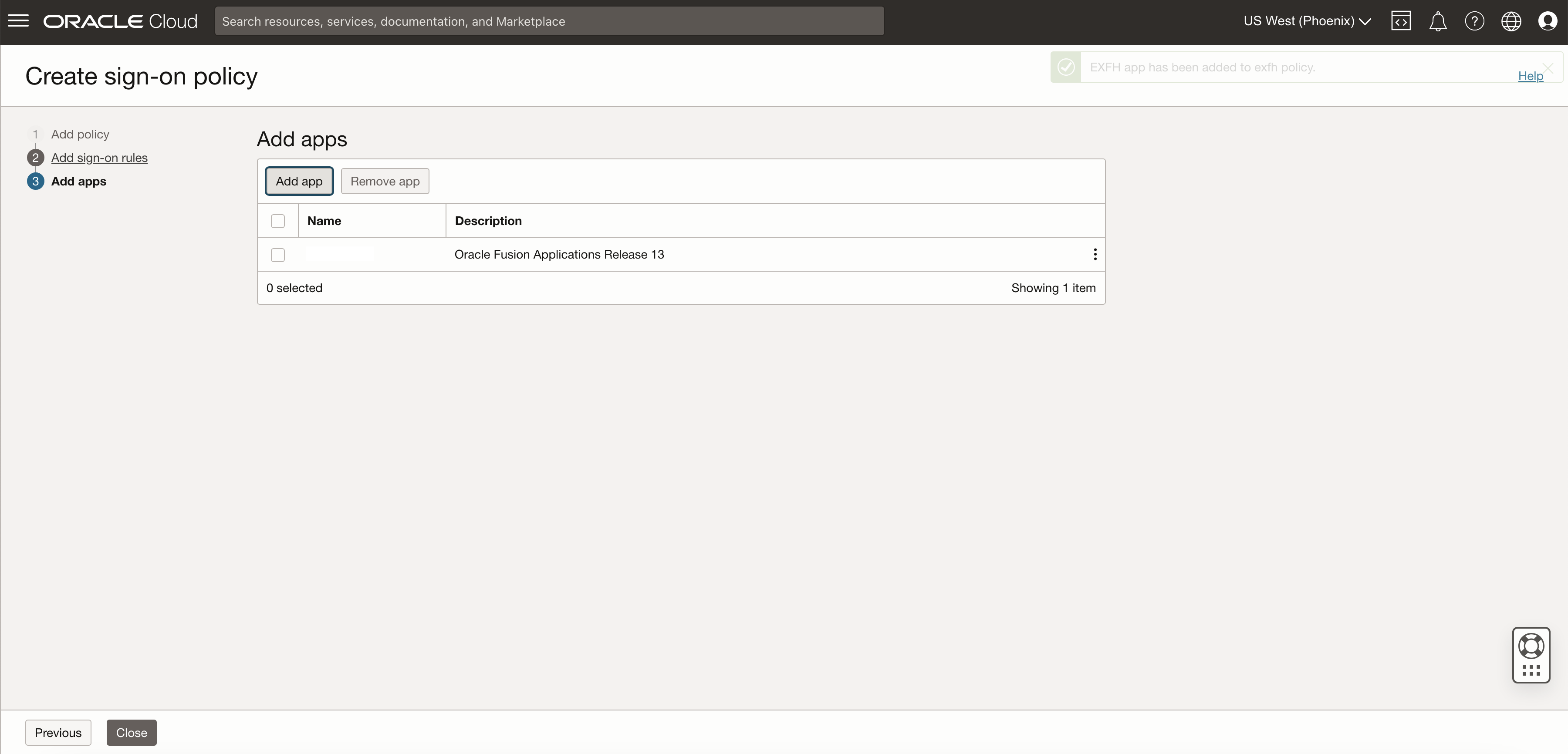
Finish the configuration off my ensuring the Sign-on policy is enabled and shows green as activated.
Testing MFA
Navigate to the homepage of the Fusion Applications environment – this will redirect you to the new IAM Domain to login. Login with your Fusion Credentials as usual.
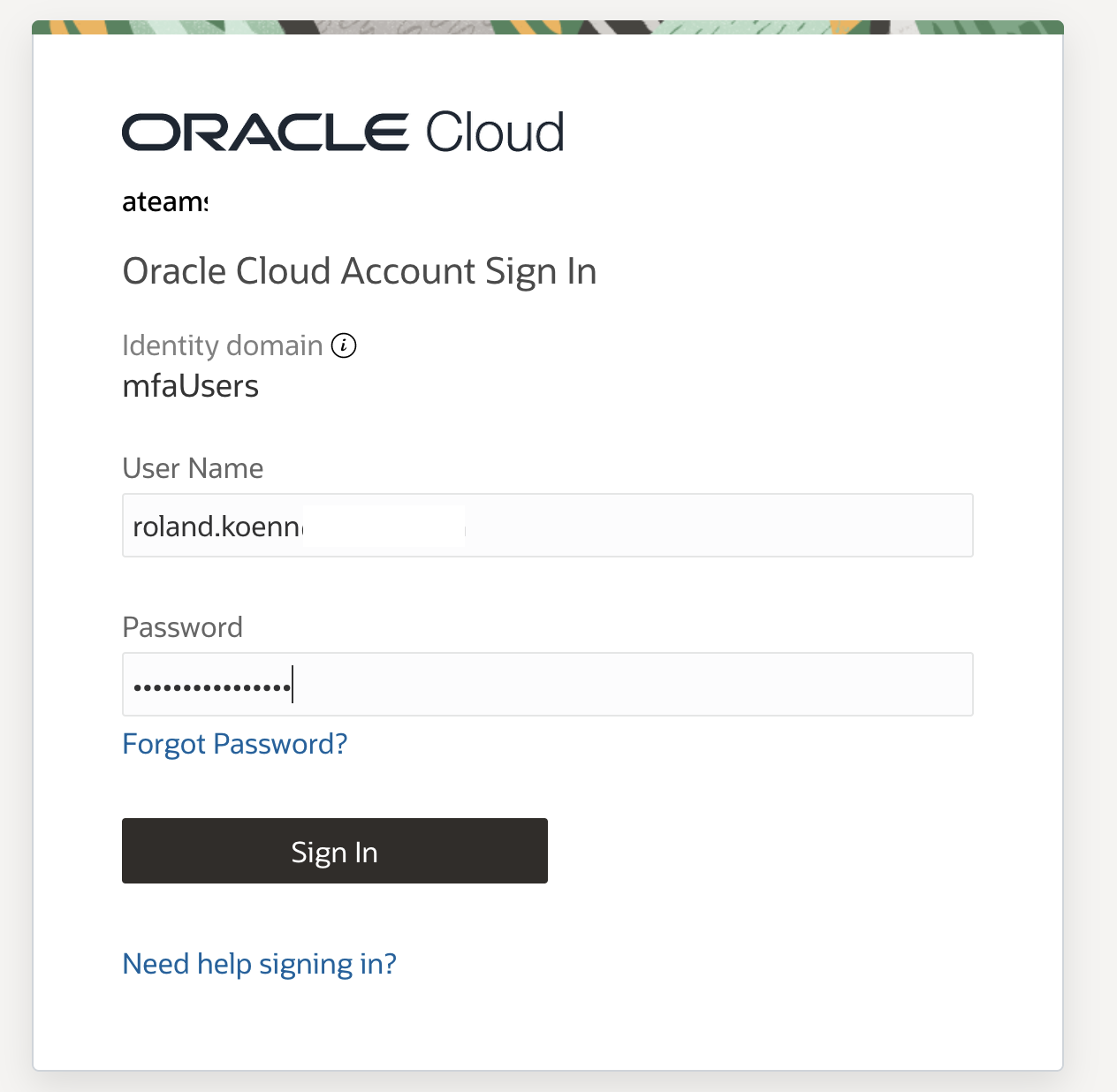
The setup now triggers the MFA enrolment screen for the user. The example shows the process using an iPhone with the Oracle Mobile Authenticator App. The installation of the app is part of the dialog and very straight forward. You will not be able to proceed without enabling the MFA configuration.
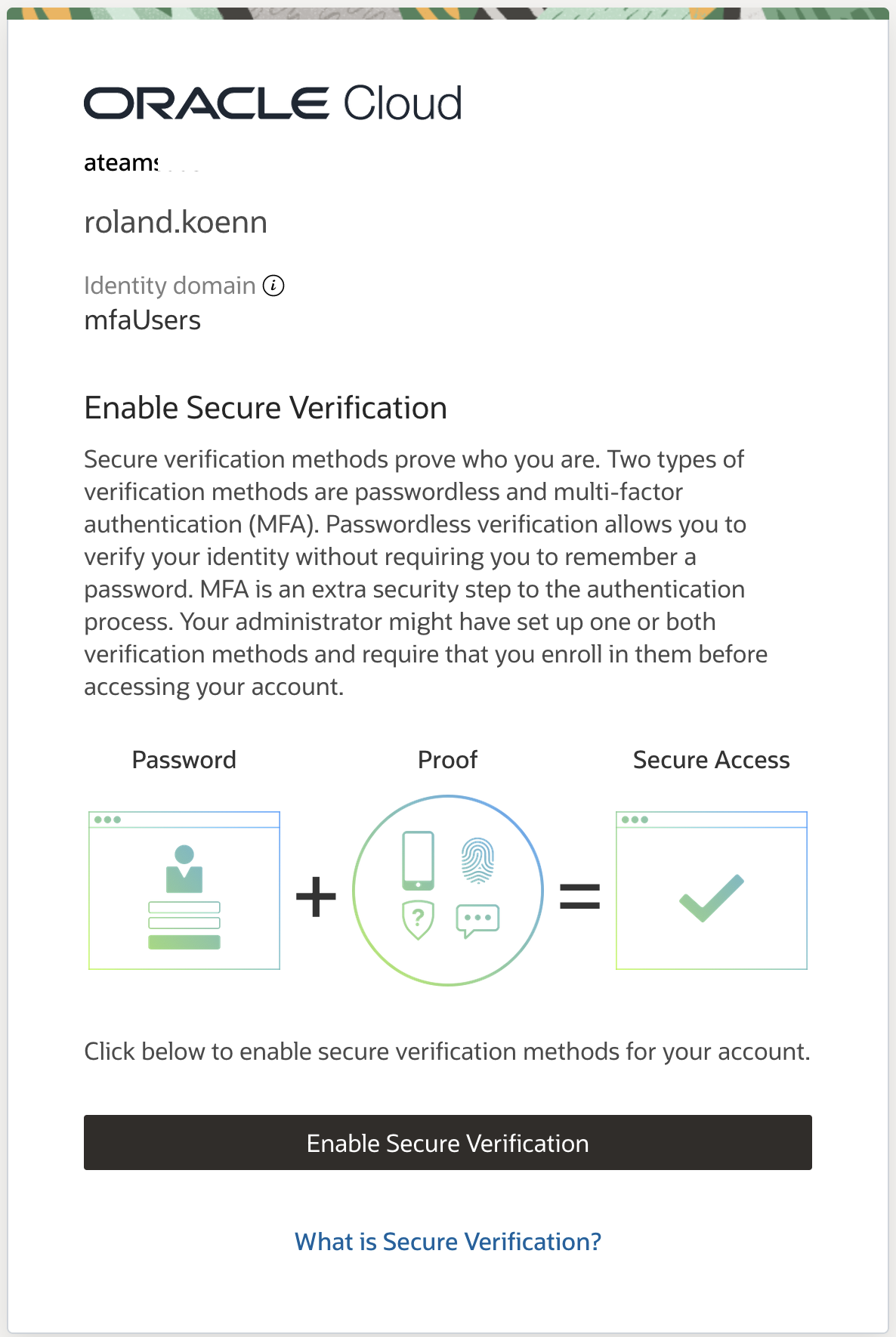
Once the app is installed on the phone simply scan the displayed QR code and the Oracle Mobile Authenticator App will register.
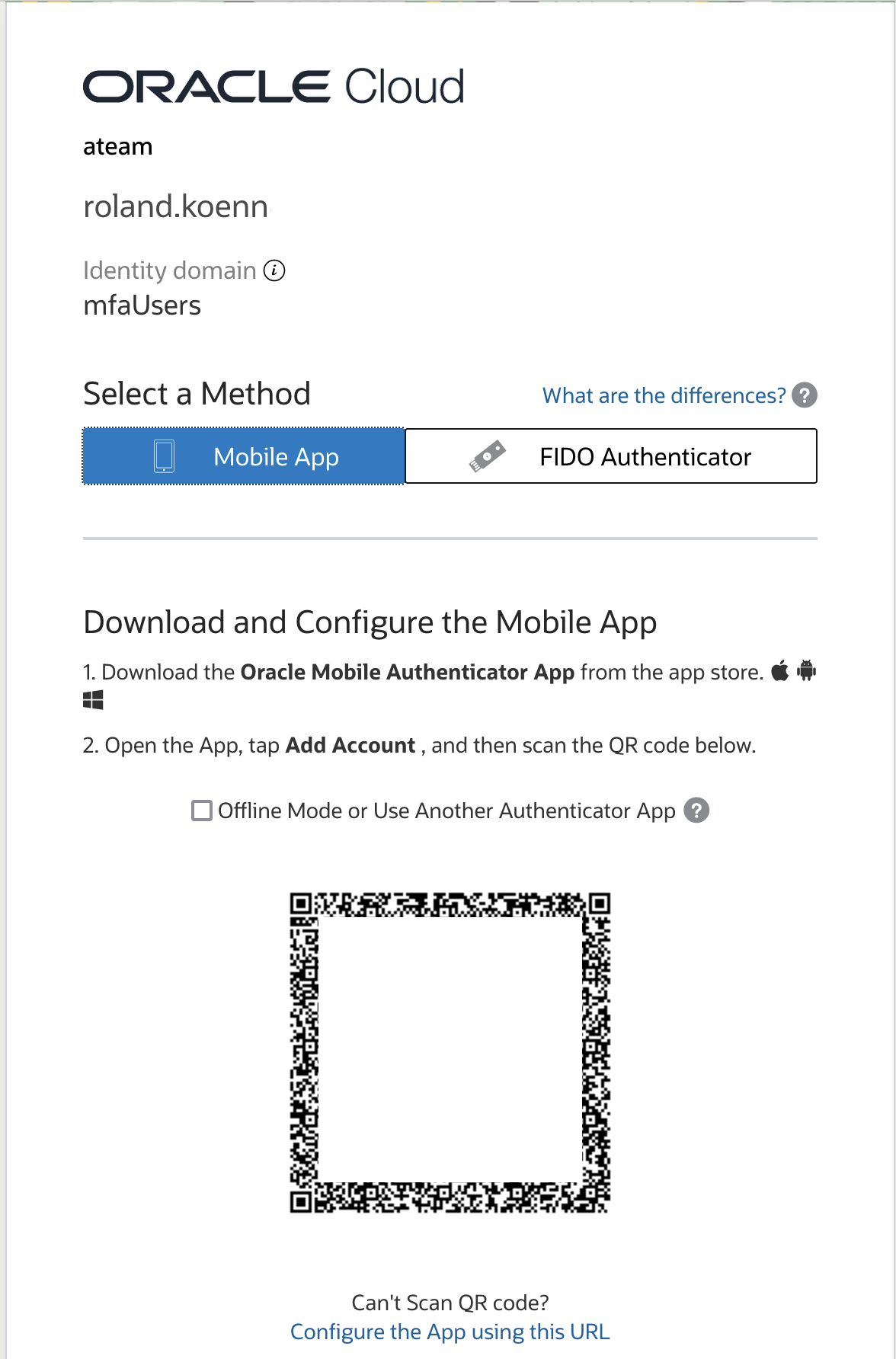
The system dsiplays the success page if the phone is succesfully enrolled.
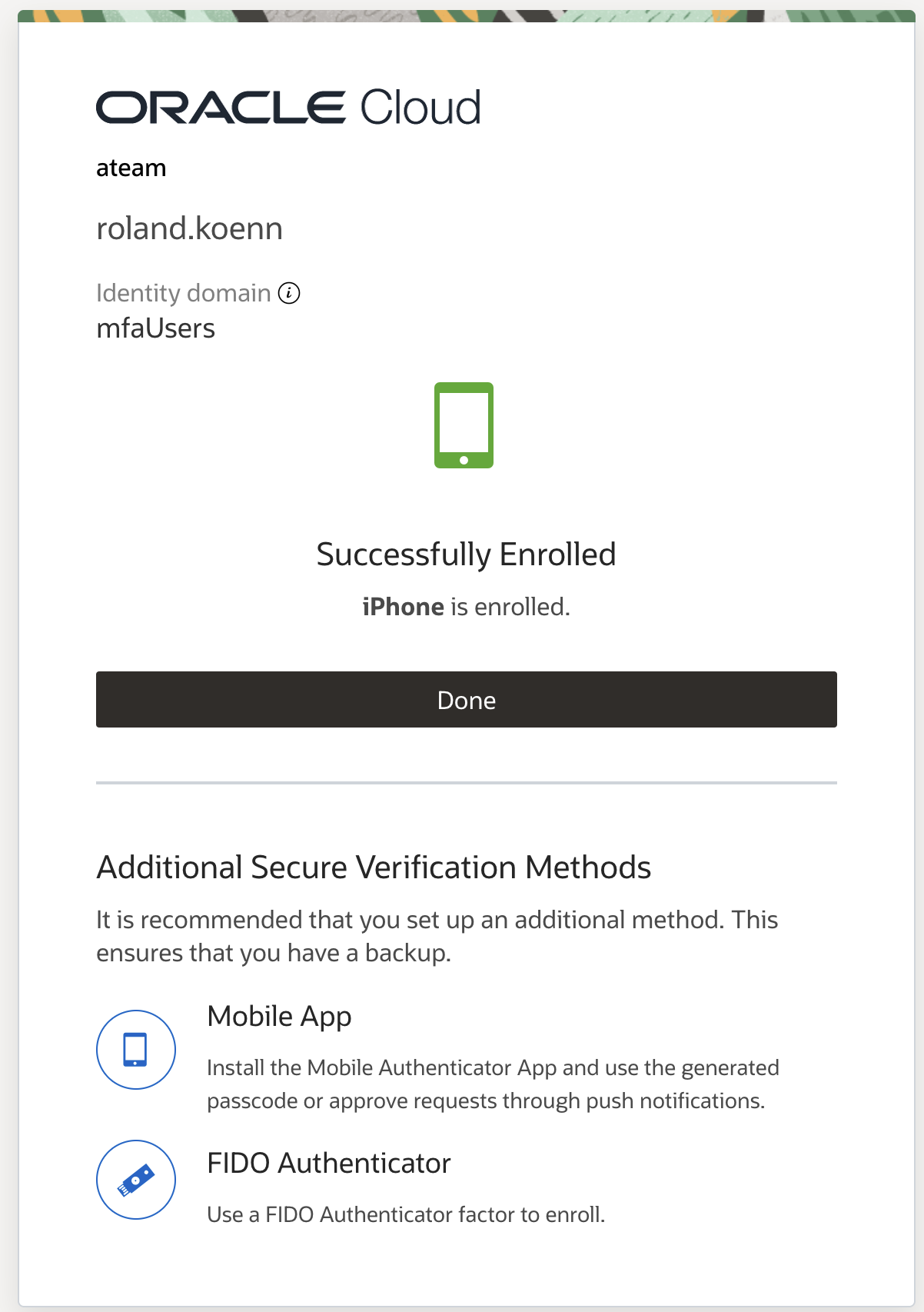
The next step will trigger a normal MFA flow that would occur during a regular login attempt into Fusion – the Oracle Mobile Authenticator App will trigger a notification on the registered mobile after providing the credential – username and password and ask for the login attempt to be approved as shown in the screenshot.
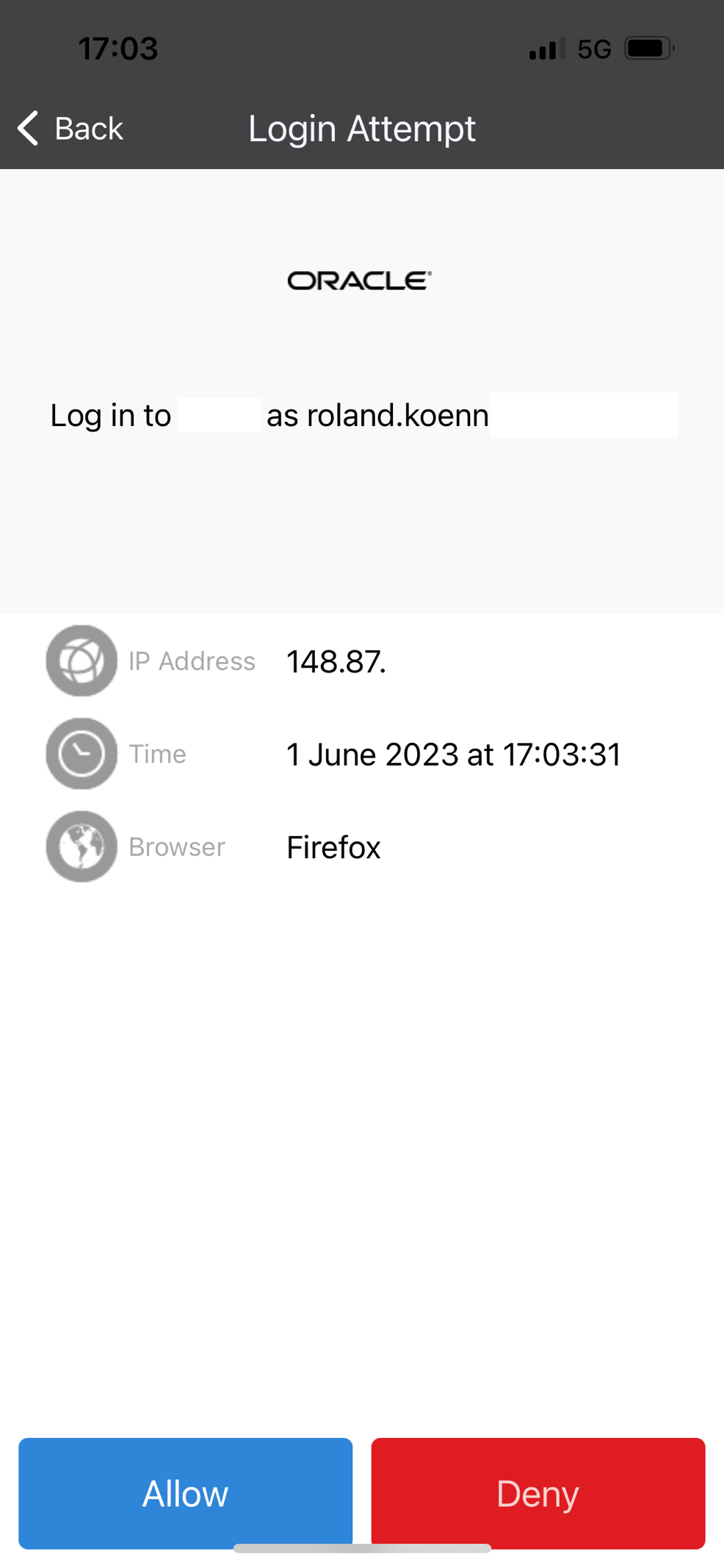
The phone shows the successful login.
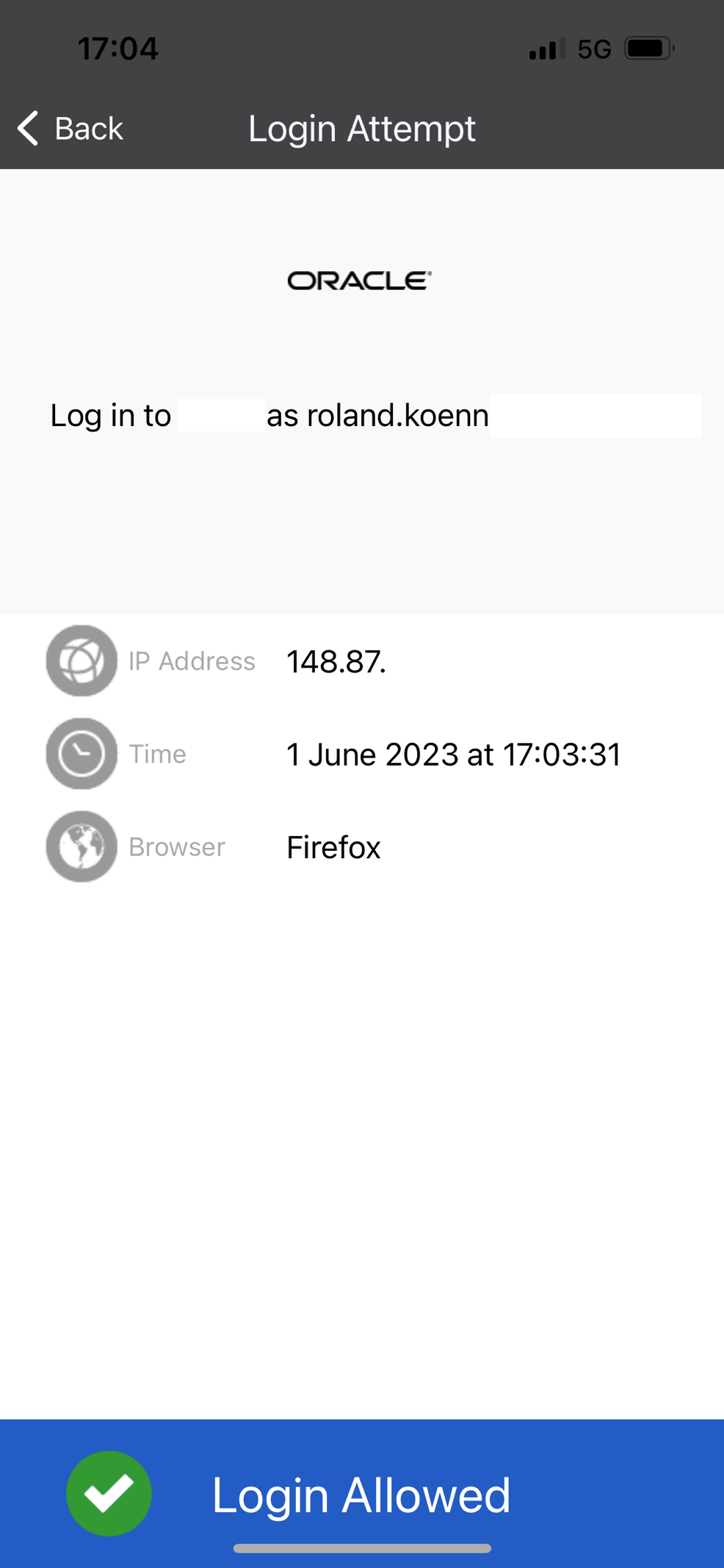
Back on the devices that triggered the login the user has the option to trust the devices – meaning no MFA is required for the configured time – in this example we configured 15 days above.
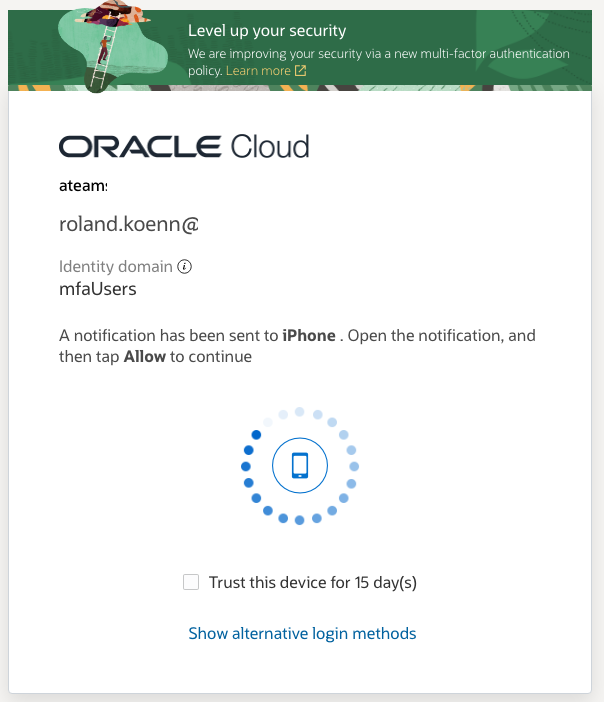
This concludes the MFA testing with the user successfully logging into Oracle Fusion Cloud providing two factors to prove their identity.
Conclusion
Multi-Factor Authentication is a great way to increase the security of your Fusion Cloud environments. It should be considered as one layer in securing every environment. The configuration appears a little complex, but is actually straight forward and allows easy troubleshooting. Most people are already very familar with MFA so the rollout has minmal impact to your users.
Further Reading
IAM Multi-Factor Autentication
Important: Please review the Support article Doc ID 2889855.1, before making any changes to existing IAM Domains / IDCS Stripes.
Shoutout to Angelo Santagata and Maximilian Froeschl for their contributions.
