Introduction:
Oracle recently introduced its Network Firewall service which has capabilities such as intra VCN traffic inspection, custom URL/FQDN filtering, SSL inspection, etc. This has opened doors to many scenarios which require granular access control in the architecture. In this blog, we will focus on the URL filtering feature of OCI Network Firewall and see how it can help in implementing various use cases. For general concepts and implementation, please refer to this blog.
Use case 1: Allowing only upgrades/patches through NAT Gateway
NAT gateway allows resources within private subnets to initiate connections to the internet. It is mostly used to patch/upgrade and get the latest updates from the Oracle YUM repositories. However, this requires the following:
- A route rule that sends traffic destined to the internet (0.0.0.0/0) to the NAT gateway.
- An egress security rule allows all communication to the internet (0.0.0.0/0)
As you can see, the issue with the above is these rules allow connection initiation from the subnet to everything on the internet along with the Oracle Yum repositories. Some customers have stricter security requirements and are hence hesitant to allow everything going out to the internet. Having said that, Oracle Yum repositories are hosted on multiple IP addresses, and they can change without notice. So, it is cumbersome to keep track and add those IPs manually to the security list.
Also, security lists don’t have the facility to allow/deny traffic based on the URLs/FQDNs. With OCI Network Firewall’s URL filtering capability, customers can allow traffic only to Oracle Yum repositories and deny everything else.
Configuration:
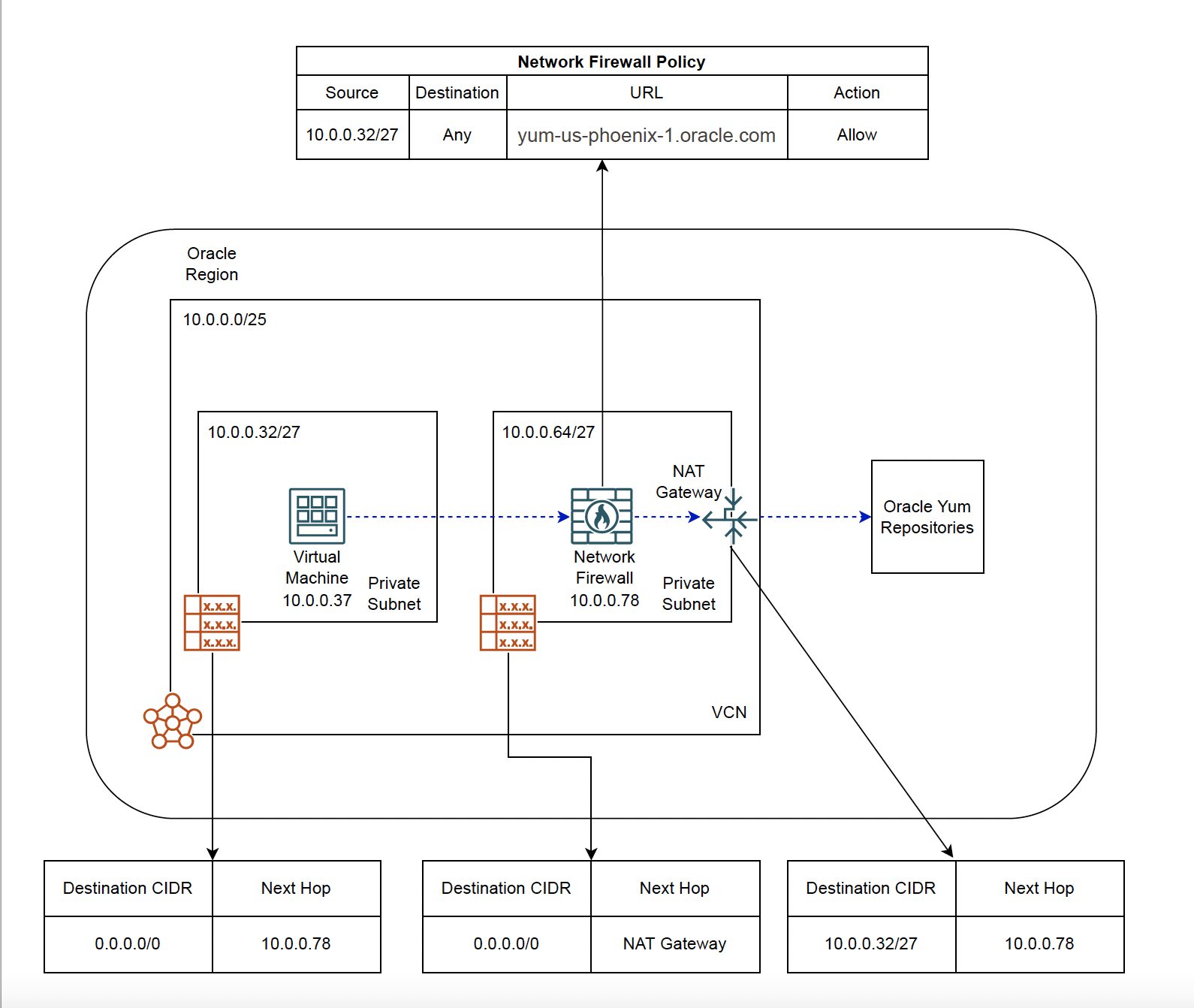
The Network Firewall is placed in a separate subnet. Route rules are configured as shown in the diagram.
To create a network firewall policy, go to Identity and Security → Firewalls → Network Firewall Policies and create a new one.
After adding basic information,
- Add URL for Oracle Yum repositories of Phoenix region. You can get URLs for all the regions here: https://docs.oracle.com/en-us/iaas/Content/General/Concepts/addressranges.htm
- Add Private Subnet’s CIDR block where your resources are in the IP Address List. If you want to be more granular, you can also add individual virtual machine IP addresses with /32 notation
- In rules, add a security rule which explicitly allows the private subnet’s CIDR block to reach out to the internet if and only if the URL matches ‘yum-us-phoenix-1.oracle.com’
Hit Create. Your policy configuration should look like this:
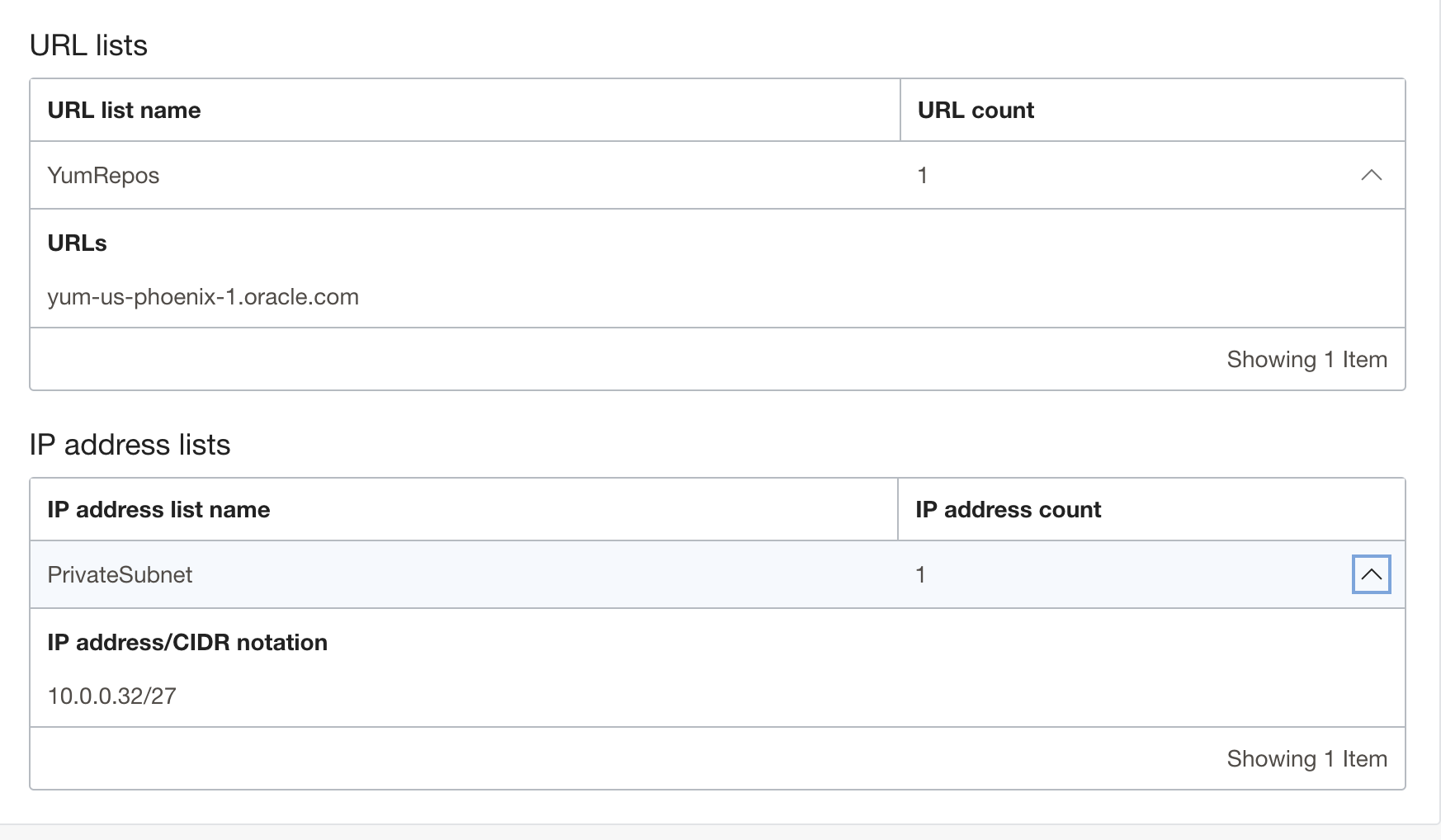
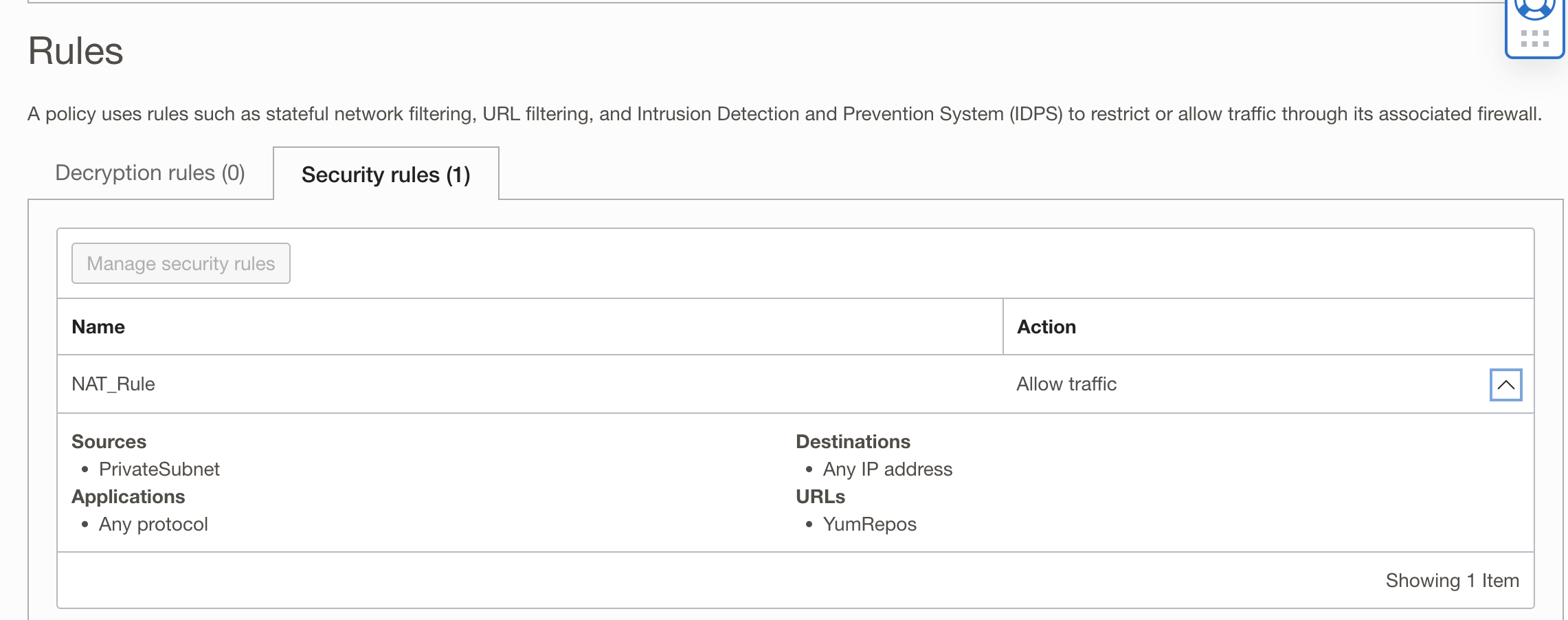
Verification:
From the Virtual Machine,
Attempt to reach out to google.com:
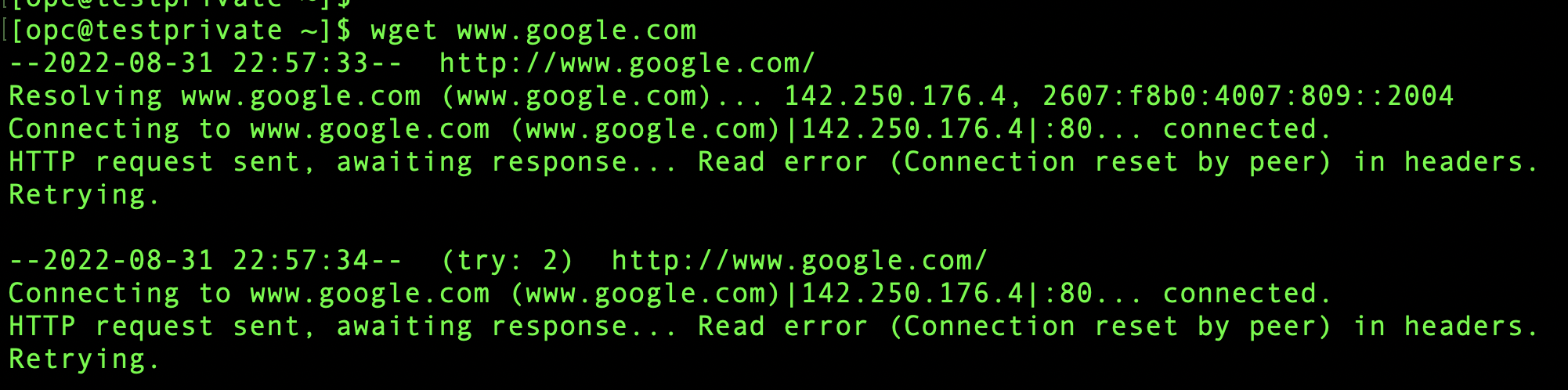
Connection fails as expected even though we have routes rules and security rules in the subnet allowing everything. That means our network firewall policy is working.
Attempt to reach out to Oracle Yum Repos:
We can successfully download a package from Oracle Yum repository!
Use case 2: Restricting access to applications using URL filtering
Customers often host public-facing applications which external users can access from the public internet. Customers can choose to restrict access based on the destination port in the security list but do not have any control over the URL in the request.
With URL filtering, you can allow the request destined to the application only if a URL match is found in the security rule. Request to any other virtual machine/IP or any other URL will be denied.
Configuration:
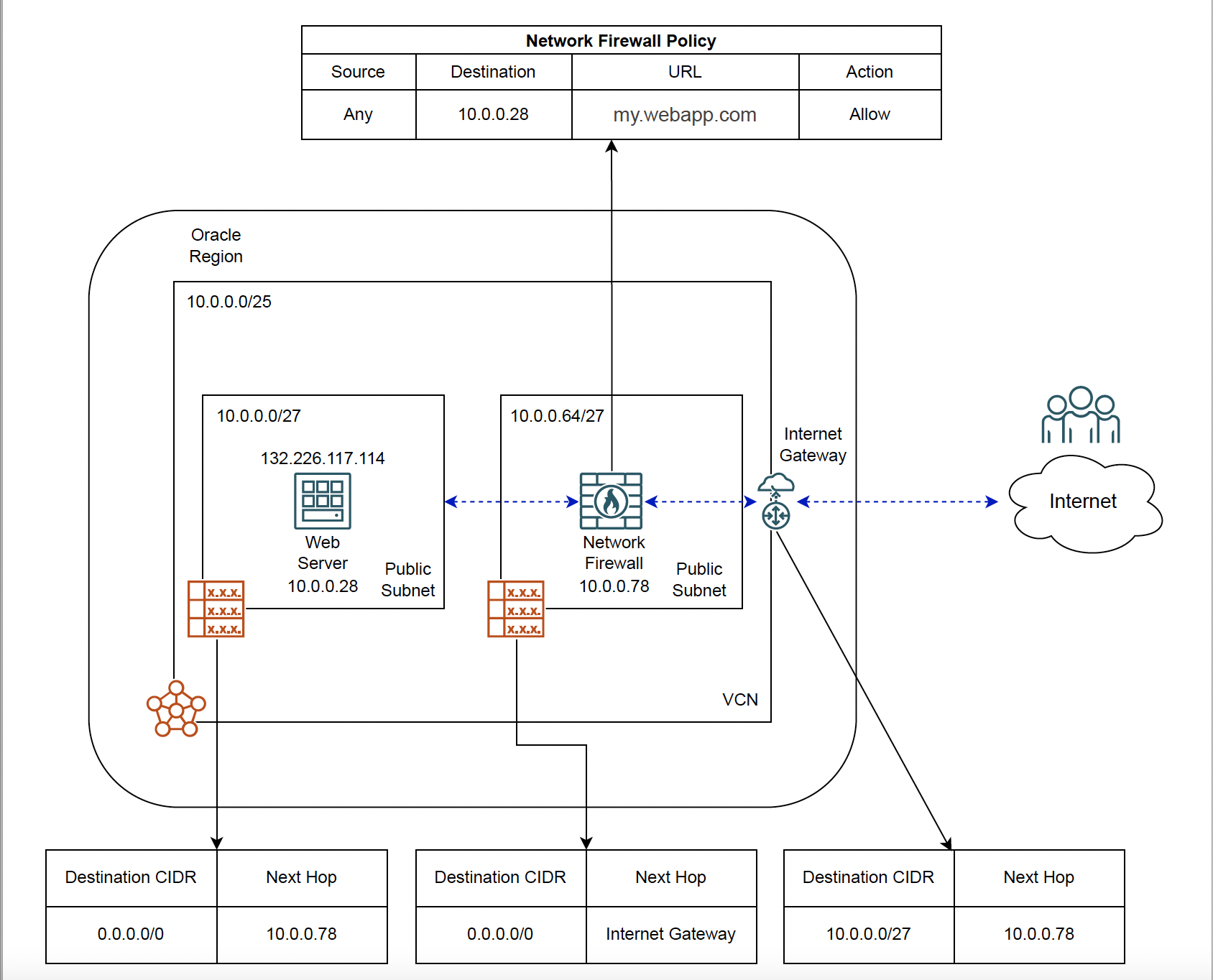
The public-facing application is hosted on 132.226.117.114 and I have a DNS entry on my machine resolving my.webapp.com. Only one security rule is needed to restrict access to the application subnet. All other traffic would be denied.
Network Policy Configuration:
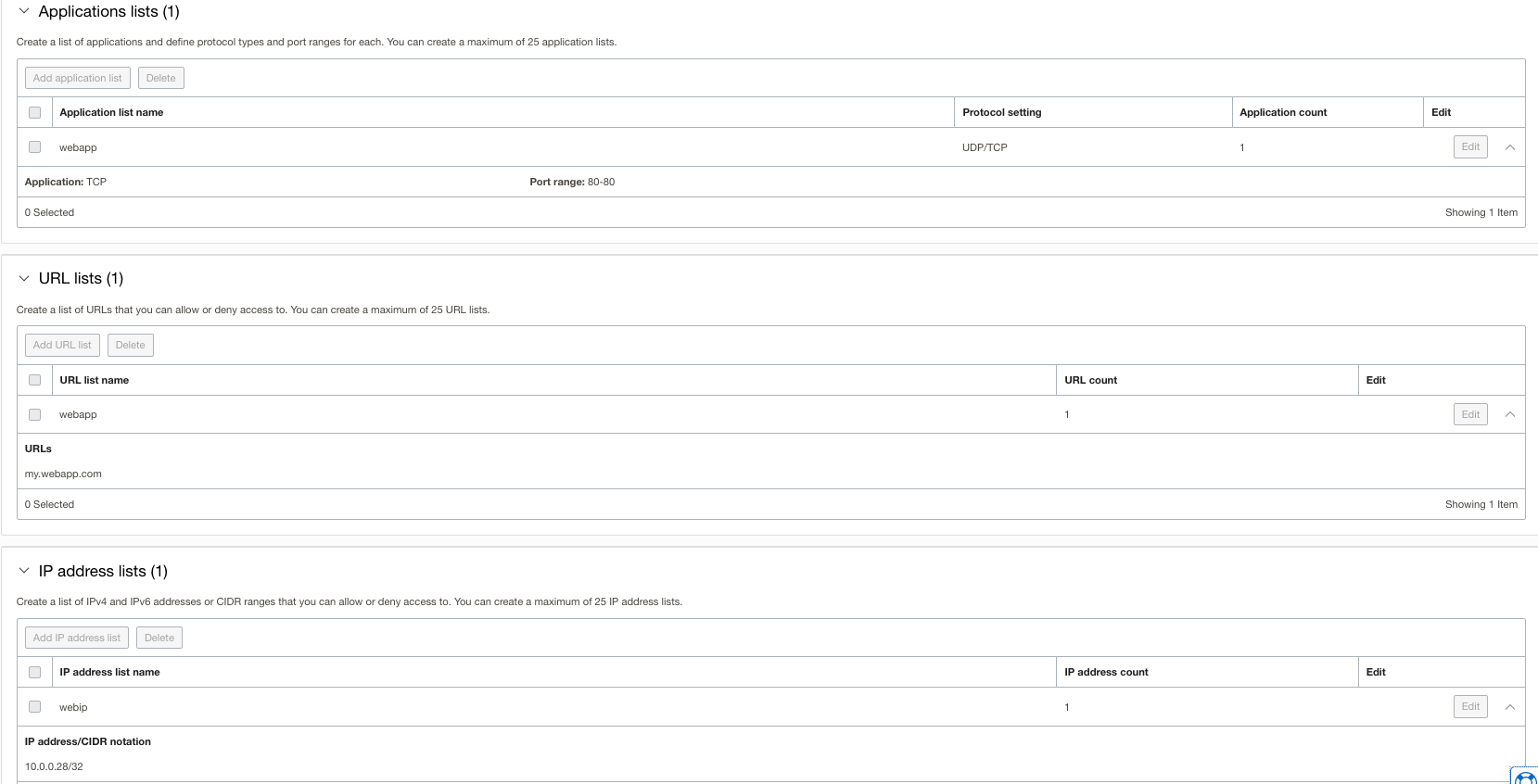
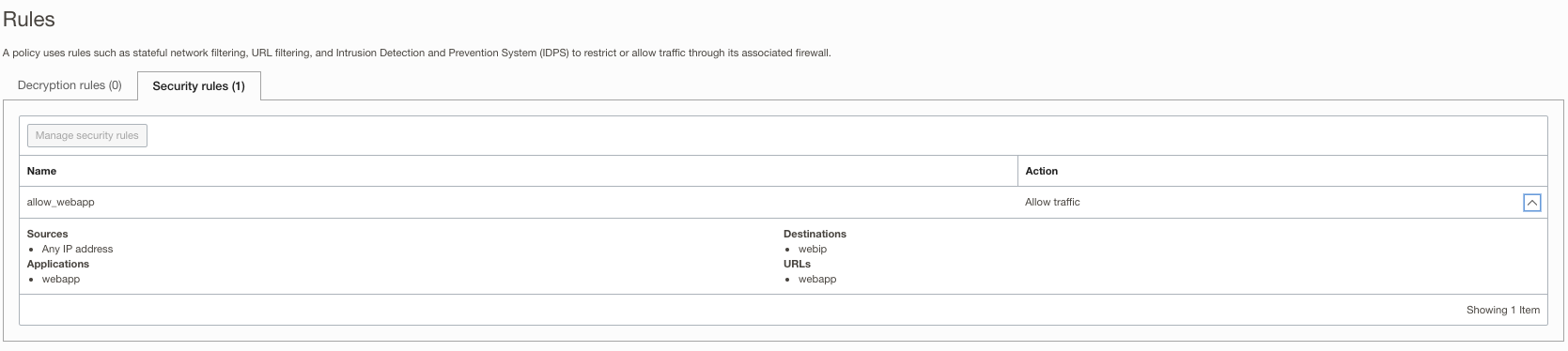
Verification:
Request with URL ‘my.webapp.com’ from local PC:
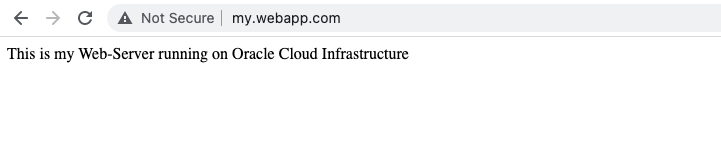
Request with public IP from local PC:
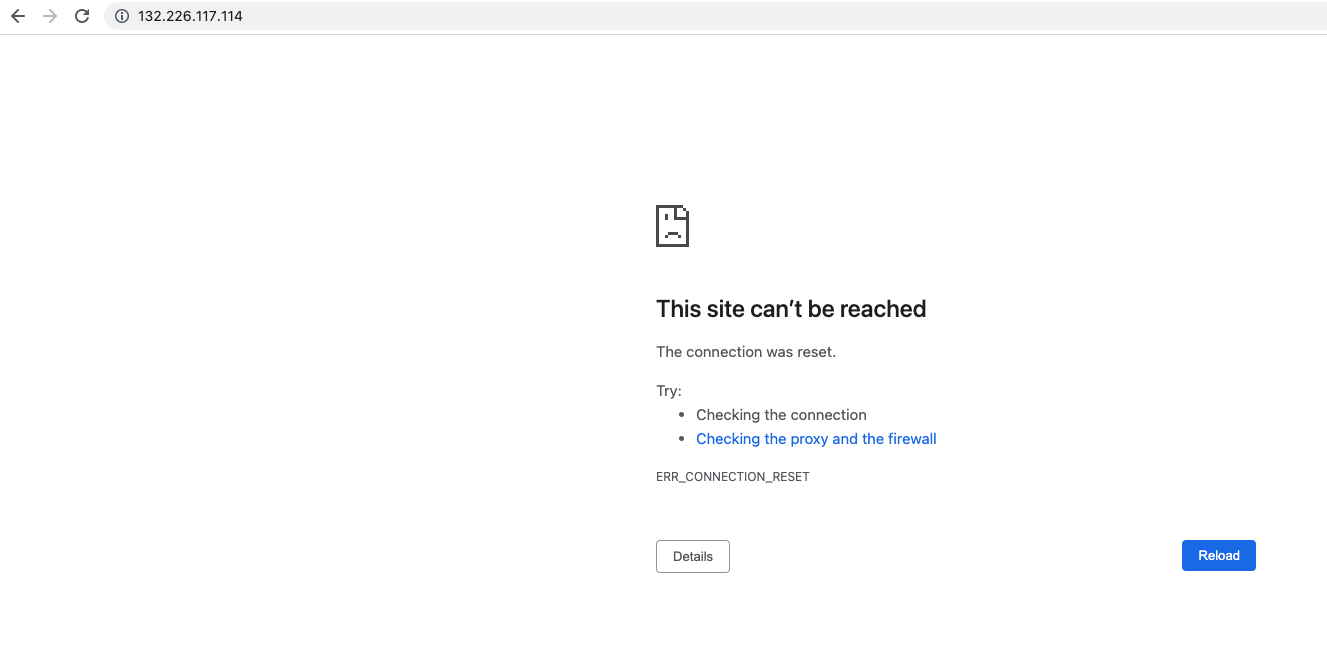
Use case 3: Selective access control to the public internet
Consider a scenario where there is more than one virtual machine within a subnet that requires access to the public internet. Customers must add a route rule for 0.0.0.0/0 and add 0.0.0.0/0 as egress in the security list as well. There can be scenarios where customers want some Virtual Machines to not have access to the specific website. Furthermore, there can be different sets of VMs which require a different level of access to the internet’s websites. For example, some machines should not access gaming websites, some should not access social media, and all should be able to access educational websites. This can be achieved with the help of URL filtering.
Configuration:
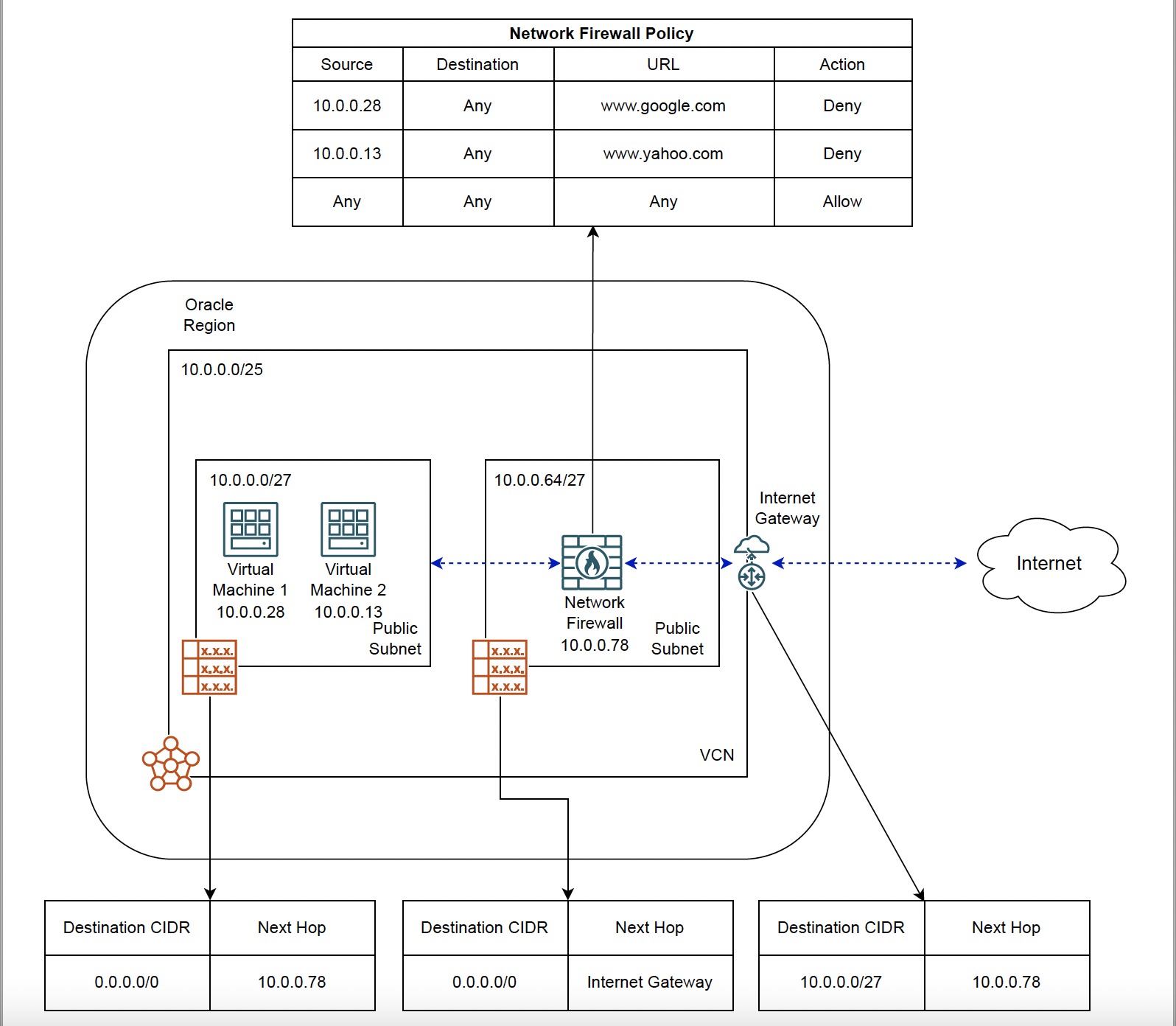
In this diagram, Virtual Machine 1 should have access to anything except www.google.com. Similarly, Virtual Machine 2 should have access to anything except for www.yahoo.com. Although VMs shown here are in the public subnet, they can be in the private subnets as well. Also, it is important to note that since we are opting to deny specific traffic, we need to explicitly allow everything at the end, and the order of rules matters. If we don’t add that rule at the end, the network policy will by default deny everything if no rules are matched.
Network Policy configuration:
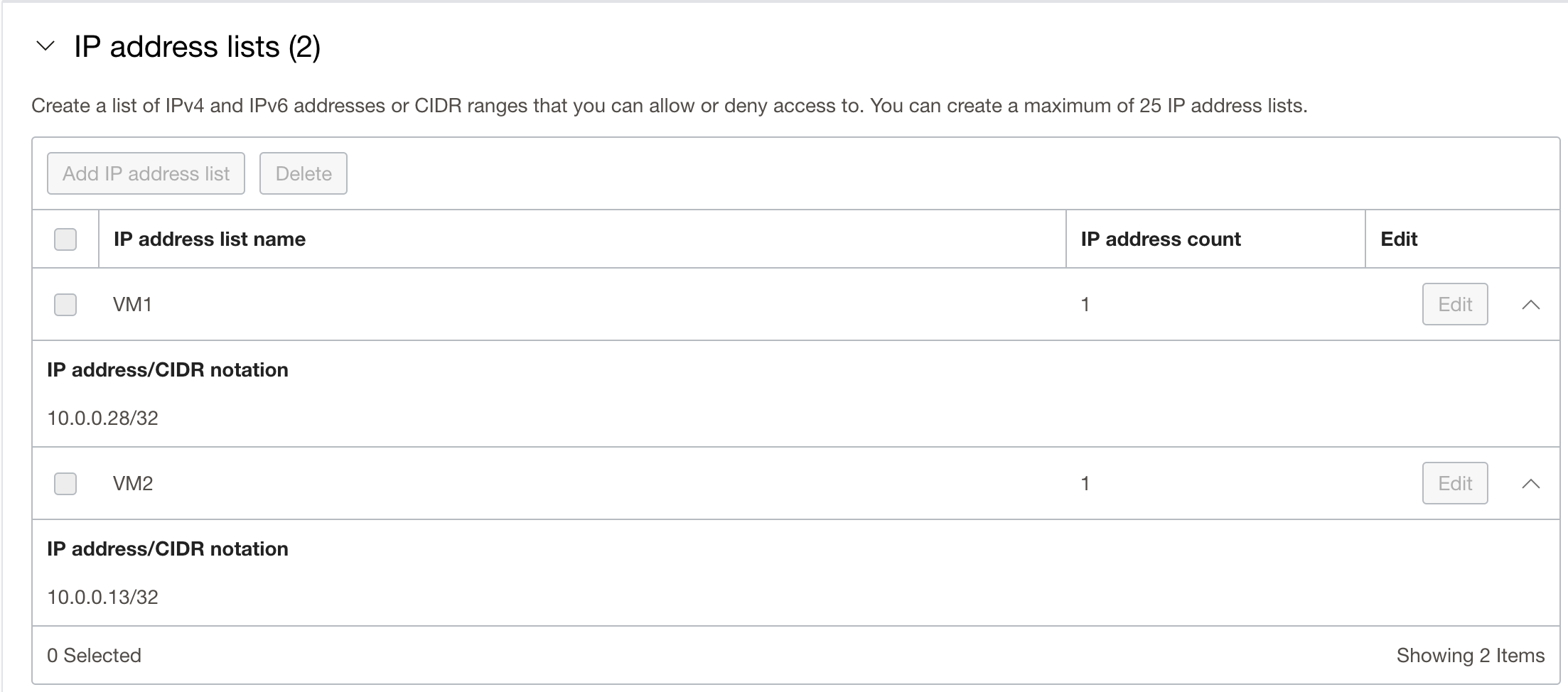
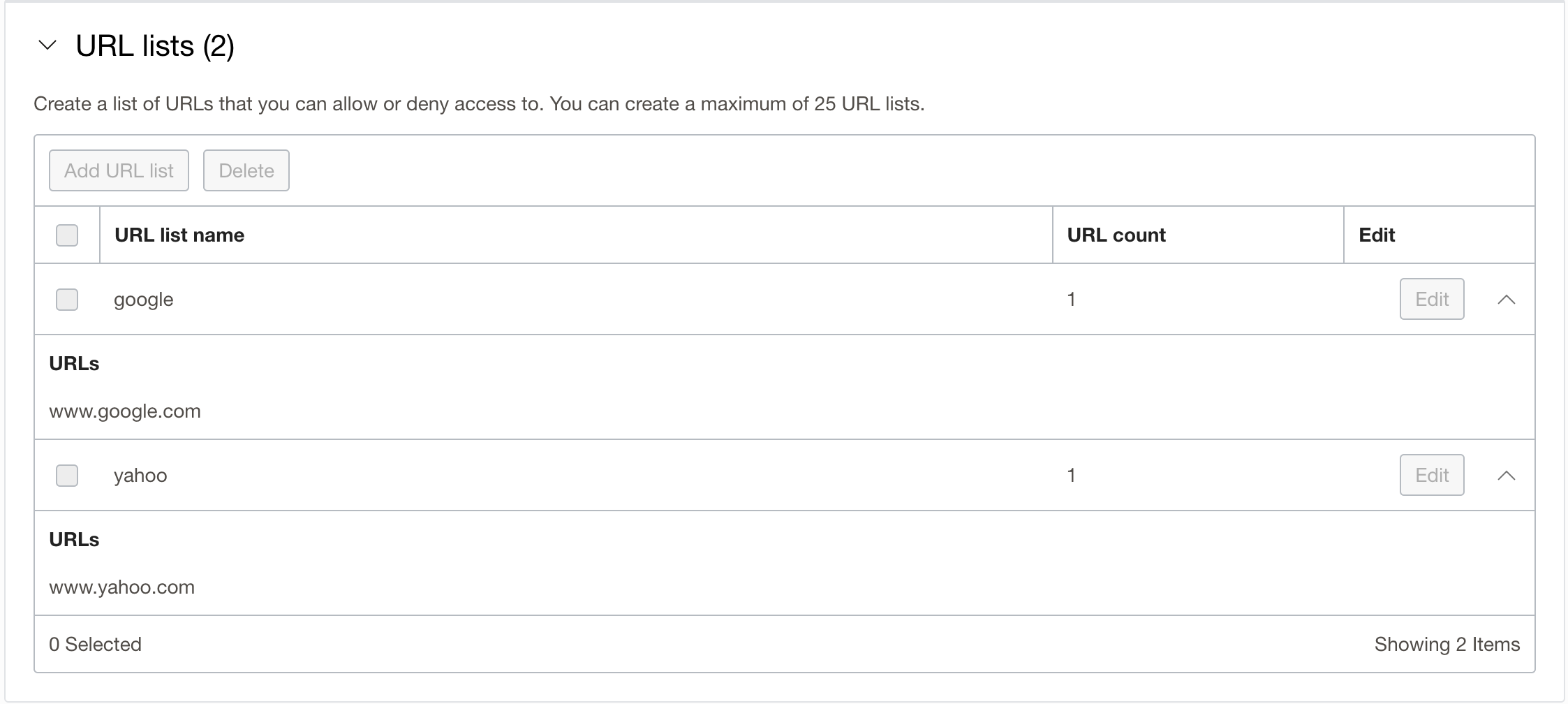
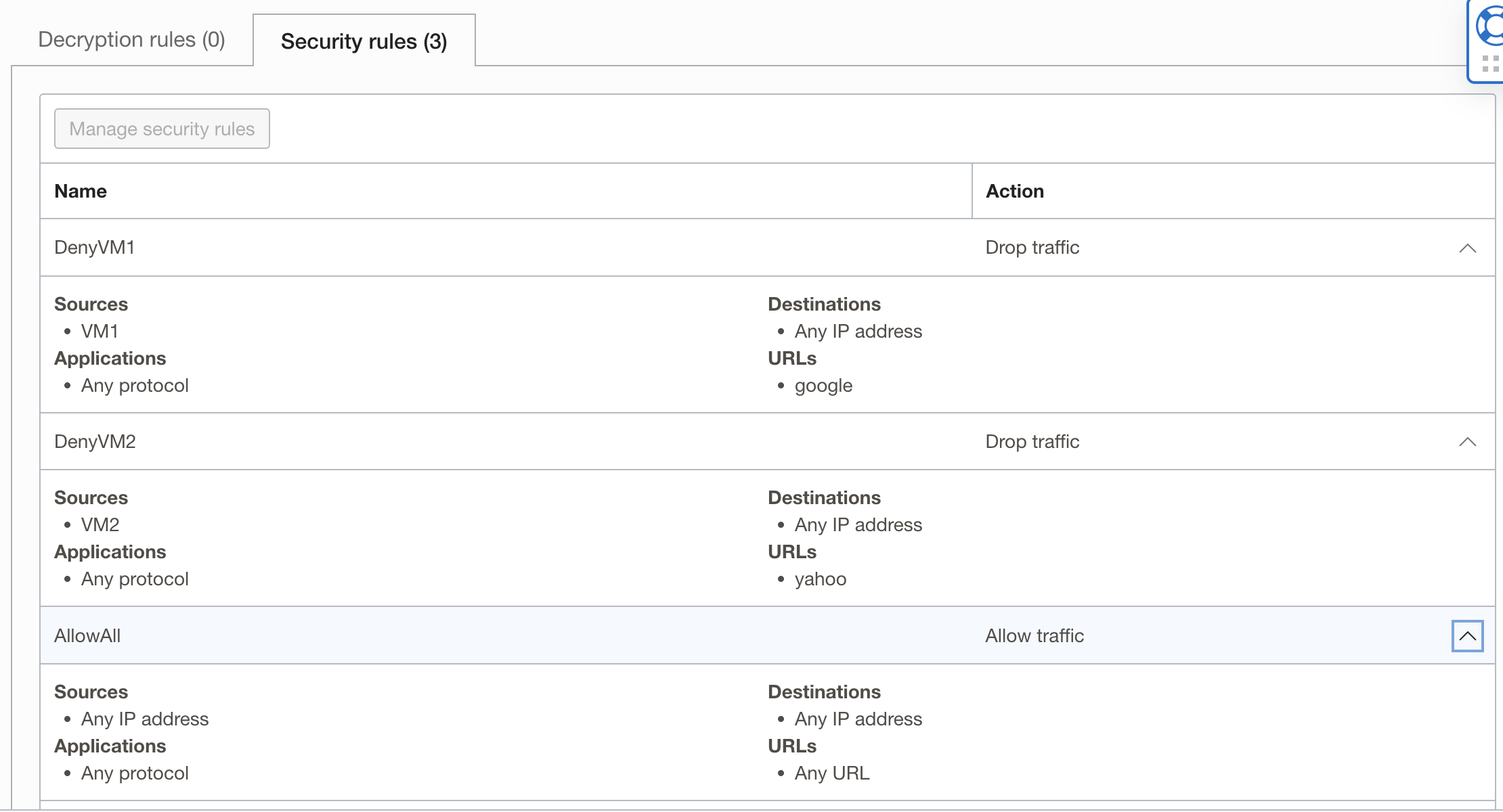
Verification:
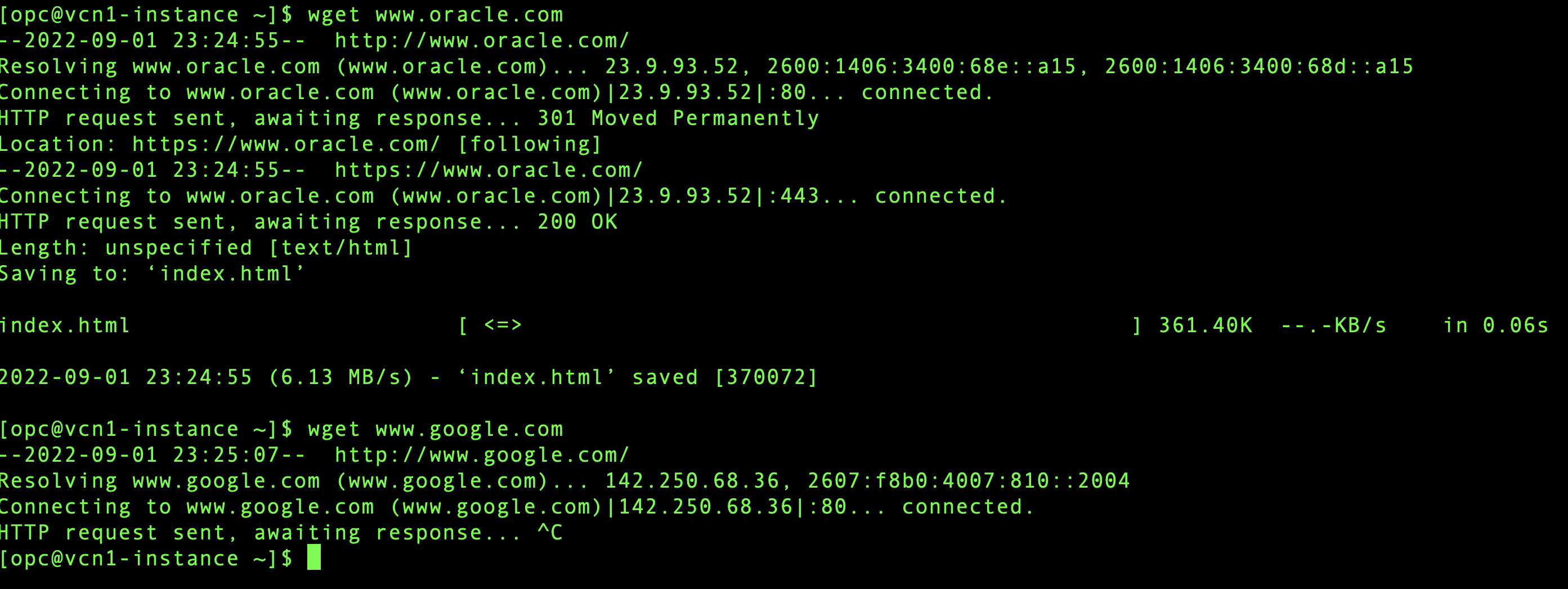
From Virtual Machine 1 (10.0.0.28):
 From Virtual Machine 2 (10.0.0.13):
From Virtual Machine 2 (10.0.0.13):
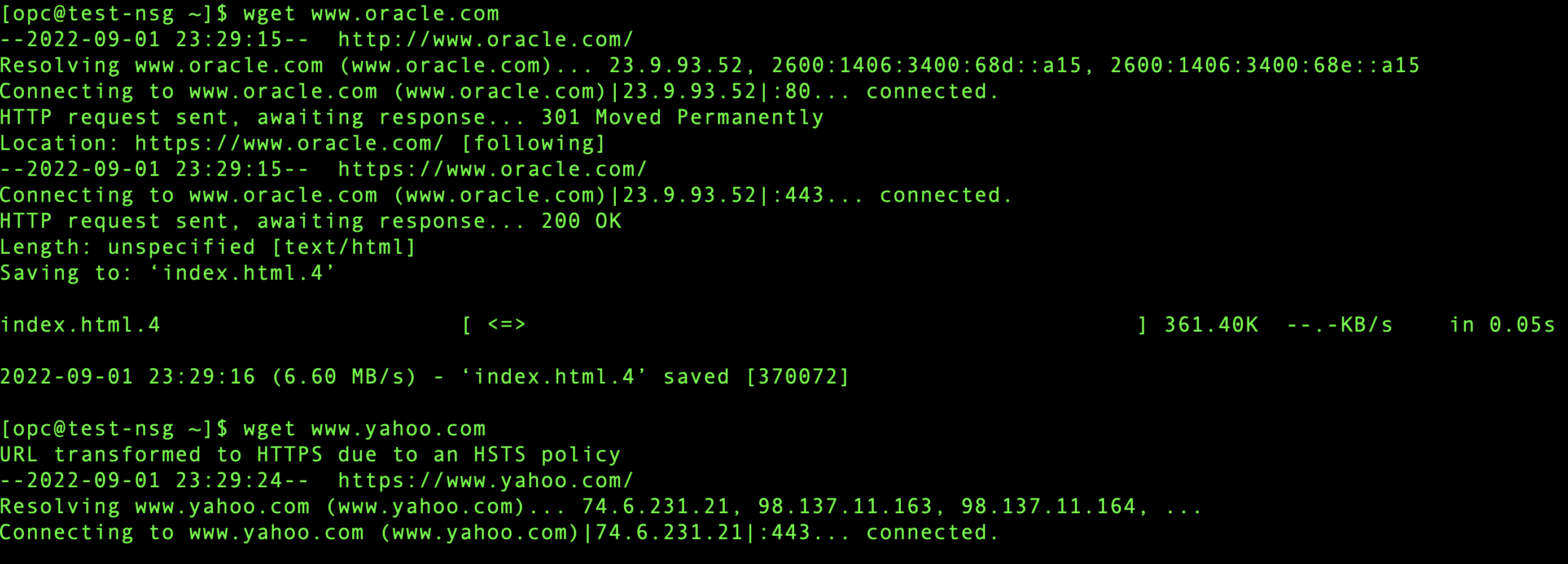
As expected, Virtual Machine 1 cannot reach www.google.com, Virtual Machine 2 cannot reach www.yahoo.com but they can reach to rest of the internet.
Conclusion:
To conclude, the URL/FQDN filtering capability of OCI native Network Firewall lets you manage access control policies at a more granular level. We explored various use cases where this feature can be beneficial. It will help customers better architect their network solutions without compromising security.
View the companion videos of all the use cases below:
Allow access to only YUM repositories using OCI Network Firewall :
Restricting access to public-facing applications using OCI Network Firewall :
Selective access to the public internet using OCI Network Firewall :
