In today’s topic, I will be describing how we can access the WebLogic Admin Console when the WebLogic server is deployed in a ‘private’ subnet. I will also show how you can configure the popular ‘putty’ application to gain access to the WebLogic console.
In security terms we usually recommend to use private endpoints/subnets whenever possible. Especially in the cloud, no one likes to send requests over the internet unless absolutely necessary. The same goes for accessing the WebLogic Admin Console. What if we deployed the WebLogic container in a private subnet? How would we access console via the internet?
The answer is Oracle Cloud Infrastructure (OCI) Bastion Service. Similarly when accessing the command line on a private compute node , we create a Managed SSH Session (default port 22) to gain access. In our use case, I would like to access the WebLogic Admin Console via a browser that is located on my laptop. In this case, you will setup a SSH Port Forwarding Session. For more details on the types of sessions within OCI Bastion service check out my earlier post here.
The Setup
I have deployed WebLogic in a private subnet using the OCI Marketplace. I then created a Bastion service to access that private subnet. Using my windows box (which happens to be deployed in OCI) I will use ‘putty’ to create a port forwarding session to the private subnet where I can access the WebLogic Admin Console via a browser at ‘https://localhost:7001/console’.
I will not be describing the setup/configuration for the WebLogic container using the marketplace. If you don’t know what the Marketplace is then check out this link. Just note that I have configured a WebLogic container where the Admin Console is listening on port 7001 and the server is running on a ‘private’ subnet. The configuration below describes how you can connect to 7001 port via a browser to manage the WebLogic Container.
Configuration
First we need to create and configure a Bastion Service within OCI. There are some existing post and documentation on how to do this if you are not familiar. After creating the service you will then create a SSH Port Forwarding Session for port 7001, as shown below:
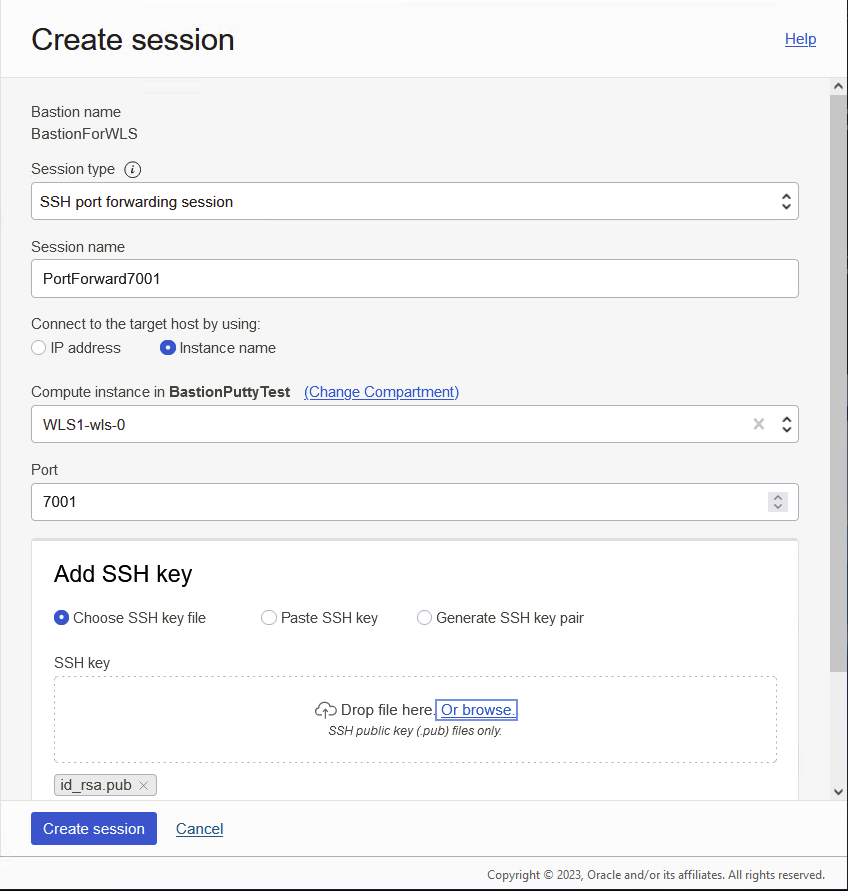
Configuring in this way, you have essentially created a tunnel on port 22 that forwards all traffic from localhost to the admin port 7001 of WebLogic server host. This will allow you to access the console from a browser on your local machine.
Before using Putty, let make sure that we can run the command line provided in the OCI Control Plane as shown below. After you create the Session, click on the elipses (…) on the right then click on ‘Copy SSH command”. Paste this command to a ternainal window.
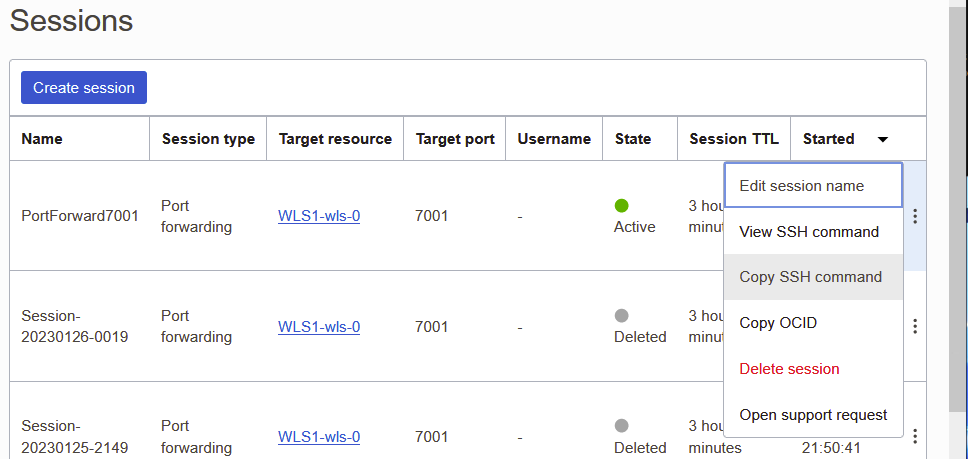
The command line format for SSH Port Forwarding is as follows:
ssh -i <privateKey> -N -L <localPort>:PrivateIP:7001 -p 22 OCID_of_session@host.bastion.us-ashburn-1.oci.oraclecloud.com
You need to provide the private key file and the local port you want to use on your laptop to access the console. Make note of the OCID_of_session and the host name of the Bastion Service combined. You will need this later when configuring ‘putty’.
After running the command, let’s try and connect to the WebLogic Admin console (https://localhost:7001/console).
Hmm, I got a connection failed messge from the browser. Can you guess why? If you guessed Security List or NSGs are blocking the port 7001, you are correct. The OCI Bastion Service, needs permission to access the port 7001. So we must allow ‘ingress’ access for port 7001 as shown here on the ‘private’ subnet security list:

Now let’s try again. It should work now:
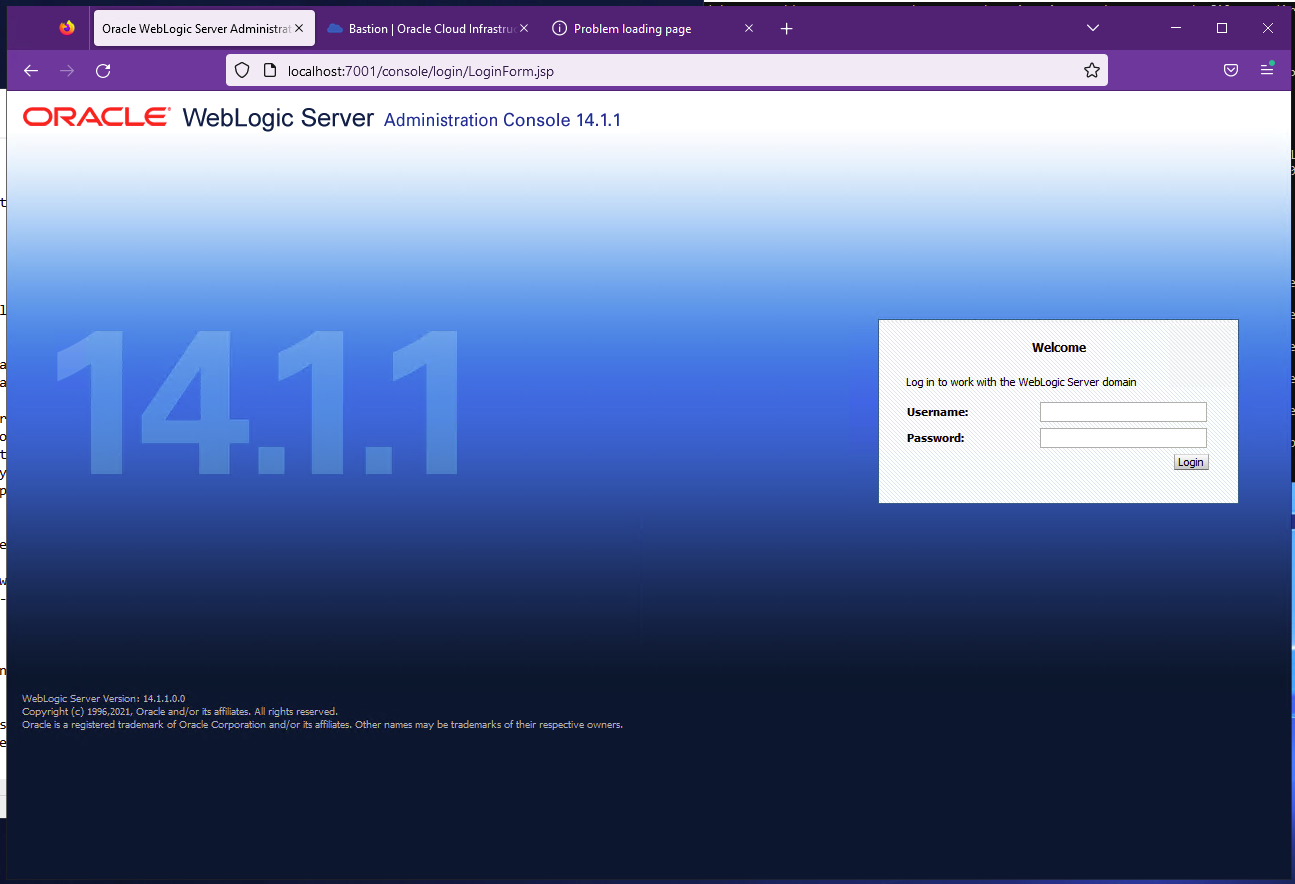
Success! Now we can see the WebLogic Login Screen.
So far so good. Now let’s configure putty to behave the same as the command line above. Follow these steps to configure:
First let’s configure the host name and port on the initial screen. The hostname needs to be the OCID_of_session@hostname that we saw above in the command line.

Next we need to check the ‘Don’t start a shell or command at all’. This is required when you port forward!

Next we need to provide the path and the private key file. When you configured the Bastion Port Forwarding Session above you should have used the corresponding public key, if not you will fail authentication.

‘Putty’ does not accept the old PEM format for private key. If you have already created the key pair using openSSH or similar in PEM format you will need to convert this to something ‘puttty’ accepts. In this case you can use the ‘puttygen’ tool to convert the private key from PEM to Putty Private Key (PPK) files. See below:

Here we import the private key with the old PEM format. Enter the passphrase if required then click on the Save Provate Key button to save in the key in .ppk format. The new file that is generated will be the one you use in putty for the private key for authentaction.
Lastly you will need to configure the tunnel ports you want to use. In our case its 7001 for WebLogic.
Tunnel Page Putty” height=”447″ src=”/wp-content/uploads/sites/134/2025/11/TunnelPagePutty.png” width=”454″>
Summary
With the popular ‘putty’ tool you can achieve the same connectivity to your private nodes via OCI Bastion service as you would using the command line. Putty also provide a key management tool calle ‘pagent’ that allows you to authenticate to different sessions without you having to select the private key manaually.
