- The CIS compliance checking script is not impacted. Users should continue using it to determine tenancy compliance with the CIS OCI Foundations Benchmark.
- Users looking for a deployment experience similar to CIS Landing Zone should now use OCI Core Landing Zone, where the same features are available. OCI Core Landing Zone evolves CIS Landing Zone and complies with CIS OCI Foundations Benchmark.
- Users looking for a deployment experience based on fully declarable and customizable templates should use the Operating Entities Landing Zone or the OCI Landing Zones Modules in the OCI Landing Zones GitHub organization.
CIS OCI Landing Zone quick start template provides OCI customers a quick, easy and secure way of designing their tenancy that complies with CIS OCI Foundations Benchmark v1.1 and follows OCI best practices for architecting a tenancy. The quick start template is provided in the form of sample Terraform and Python code. Depending on what best fits your use cases and development practices, it could be used as provided, extended and built upon or could also be used as a guide to build something similar. If you are new to OCI Landing Zone, this blog post by Andre and this reference architecture are great resources to get started.
We continue to add new features to OCI Landing Zone. In this blog post, I would like to describe a recently added feature that allows for consolidating OCI security related logs – OCI Audit Logs as well as VCN Flow Logs using Service Connector Hub.
Monitoring security related logs is an important part of maintaining a strong security posture in the cloud. Customers typically export these logs to their SIEM and SOAR systems where their security teams process, monitor, analyze them and take appropriate actions to rectify various concerns.
OCI Landing Zone now comes equipped with the capability to consolidate audit logs for its compartments as well as VCN flow logs for the subnets created by OCI Landing Zone in three different targets – OCI Object Store, OCI Streaming or Oracle Functions – for independent aggregation. While configuring OCI Landing Zone, you can select one of three targets for audit logs as well as VCN flow logs. Picking up data from these locations and transmitting them to your SIEM and SOAR systems or triggering Oracle Functions to implement various business logic is out of scope for this new feature and this blog post.
Let’s briefly touch upon the OCI services and components that are used in this feature. I am not going to talk about these features in detail but want to provide pointers so that you can find more information. OCI Audit logs are described here. More information about VCN Flow logs can be found here. Service Connector Hub is used to move data from one or more sources to a destination. More information about Service Connector Hub is here.
You can set up OCI Landing Zone by using either Terraform or OCI Resource Manager. I am going to use Resource Manager for this blog post but the concepts and configuration remain the same for both approaches. Both ways require you to set some variable values to control various aspects of this feature which is documented here.
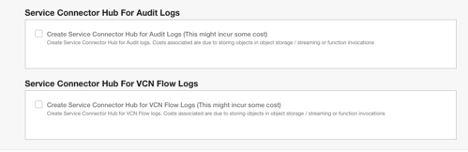
There might be some charges associated with aggregating log data in OCI Object Store, in OCI Streaming or invoking Functions and hence by default log aggregation is disabled as shown in the screen capture below:
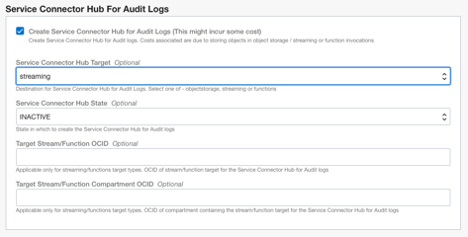
The variables for both sets are very similar and hence it is sufficient to describe only one set. Let’s take the configuration for Audit logs as an example. Enabling the feature presents the following configuration:
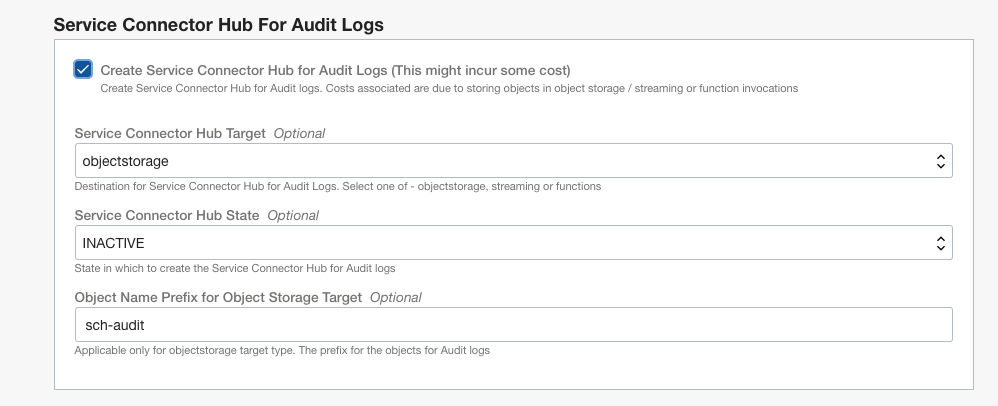
By default the Service Connector Hub is created in inactive state. That means the Service Connector Hub will be created but the data flow will not be enabled. You can set it to “ACTIVE”, if desired.
You can set the target for Service Connector Hub to one of OCI Object Store, OCI Streaming or Oracle Functions. The default target is set to OCI Object Store as shown in the screen capture above.
The remaining variables depend on the target chosen. Let’s take a look at them one by one.
In case the selected target is OCI Object Store, you can choose to specify a different prefix than the provided default value for naming the objects that will be written to OCI Object Store.
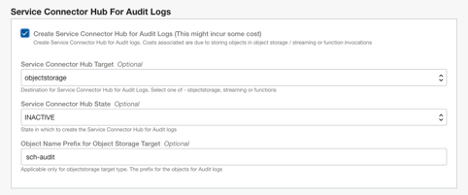
In addition, there are two more advanced options that may be specified in the “locals.tf” file in config folder:
- sch_audit_target_rollover_MBs = 100
- sch_audit_target_rollover_MSs = 420000
As their names indicate, they are used to control the batch size that is written in an object. There are similar variables for VCN flow logs as well.
In case the target is either a Stream/Function, two following values need to be provided:
- OCID of the target Stream/Function
- OCID of the Compartment that contains the above Stream/Function
As I mentioned above, the configuration for VCN flow logs section is very similar to that of audit logs.
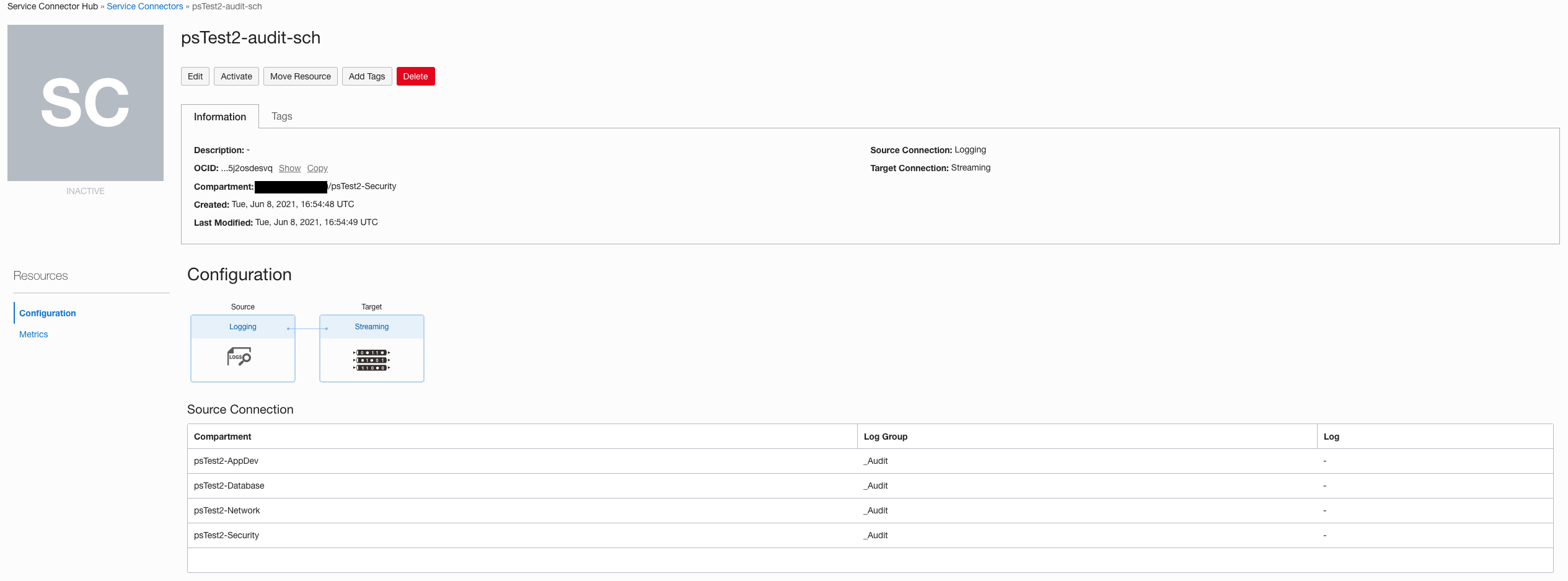
And that’s it. Once you apply the Terraform configuration you can see the two service connectors created. The following screen capture shows the created Service Connector Hub for aggregating Audit logs in a Stream:
When the service connectors are in active state, they will start flowing and aggregating the data which can be further processed depending on your use-cases.
The policies required for the Service Connector Hub as described here are also created so there is no need to create those policies.