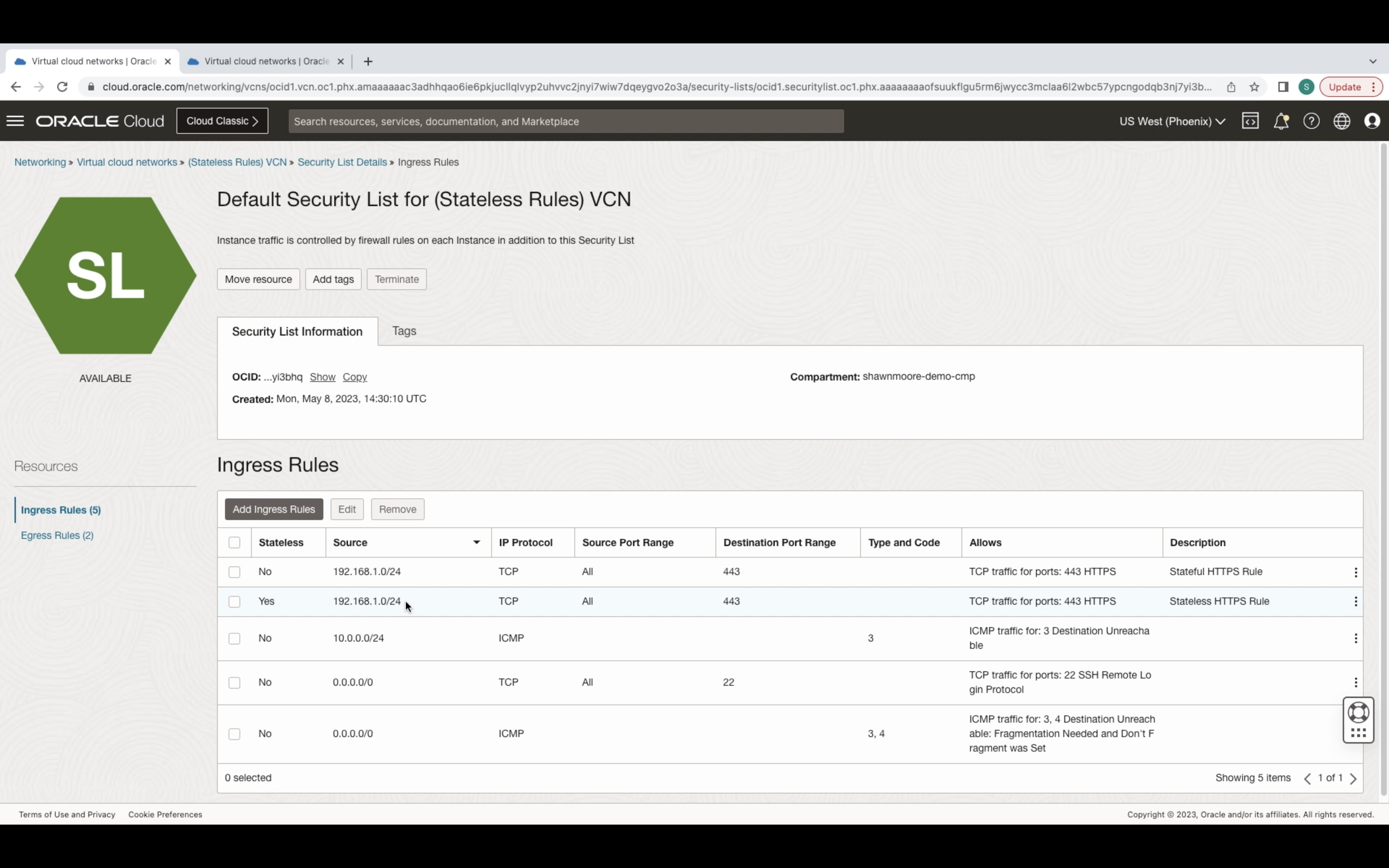
OCI Security Lists and Network Security Group use security rules available in two flavors: Stateful or Stateless. Stateful rules are the default, it provides a connection-tracked session between the source and destination IP address. This allows for ease of management and greater visibility of data flows between source and destination.
Stateless rules do not keep track of the TCP session state between the source and destination. This allows for greater performance and scalability. Removing the need to use a Connection Tracking Table for managing ingress/egress packet flows. The Connection Tracking Table is located on the Operation System within each OCI instance and is associated with its VNIC.
Be sure to view the companion video for this blog:
Stateless rules are recommended for use cases such as the following:
- An Internet-facing website that experiences high volumes of traffic (millions of concurrent connections).
- OCI Network Firewall that’s able to perform a deeper stateful packet inspection. As mentioned here, there’s a performance impact enforcing stateful packet inspection with a security list or NSG and then making another stateful inspection with the network firewall. Even worse if performed a third time with a Security List or NSG when the packet egresses the Network Firewall.
- Public Load Balancer that needs to handle millions of concurrent sessions. OCI Load Balancer health checks shows false positives if backend VNIC Connection Tracking Tables are full. Once a Connection Tracking Table is full any additional TCP sessions are dropped, such as periodic TCP health checks from a load balancer to a backend instance.
(Note: For the Network Load Balanacer, the rules assigned to a backend will always be stateful even though you configure them as stateless in the Console)
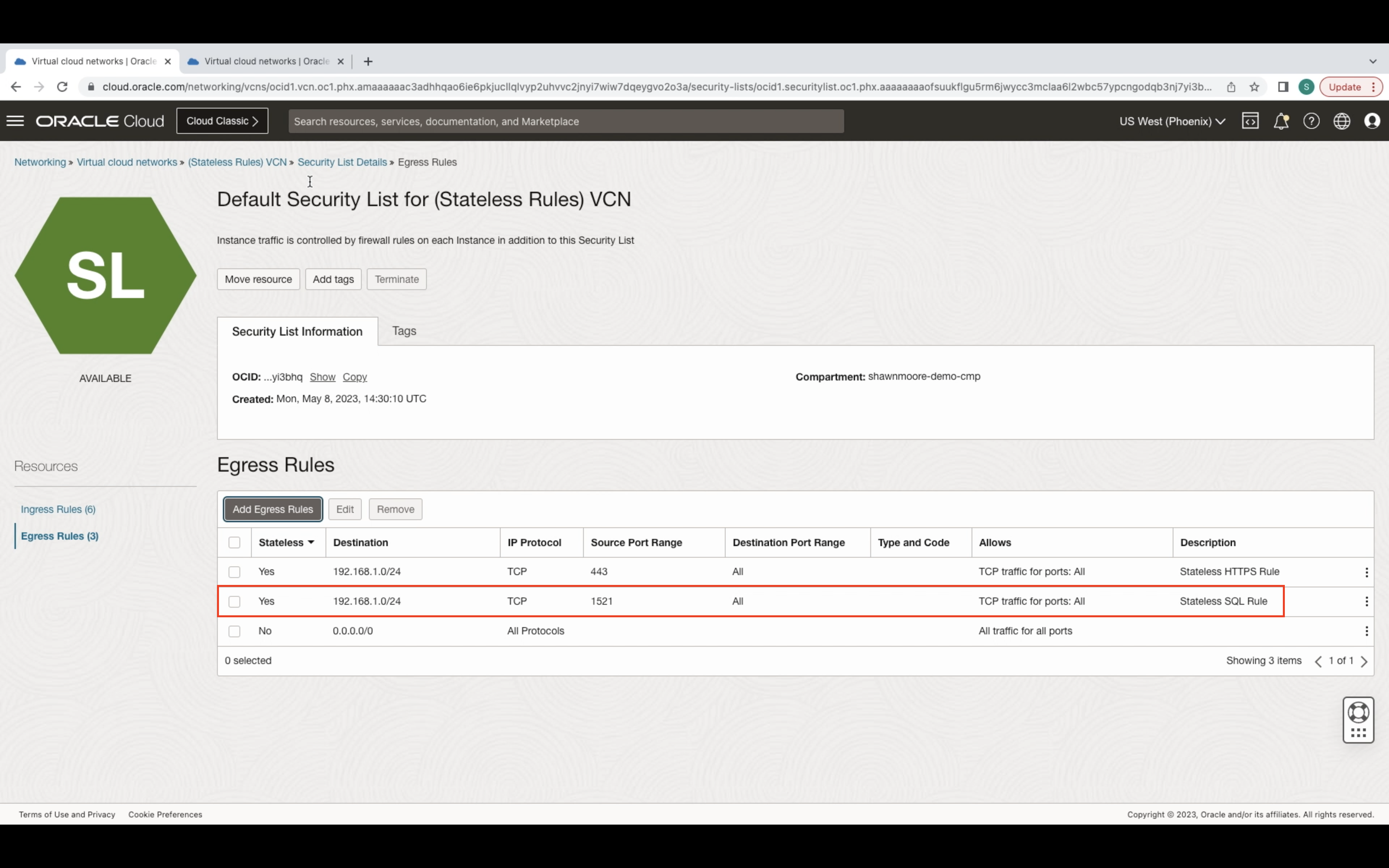
When creating stateless rules, you’ll need to create an ingress rule and a corresponding egress rule that allows the destination host to respond to the source address using the same TCP port it received the packet on.
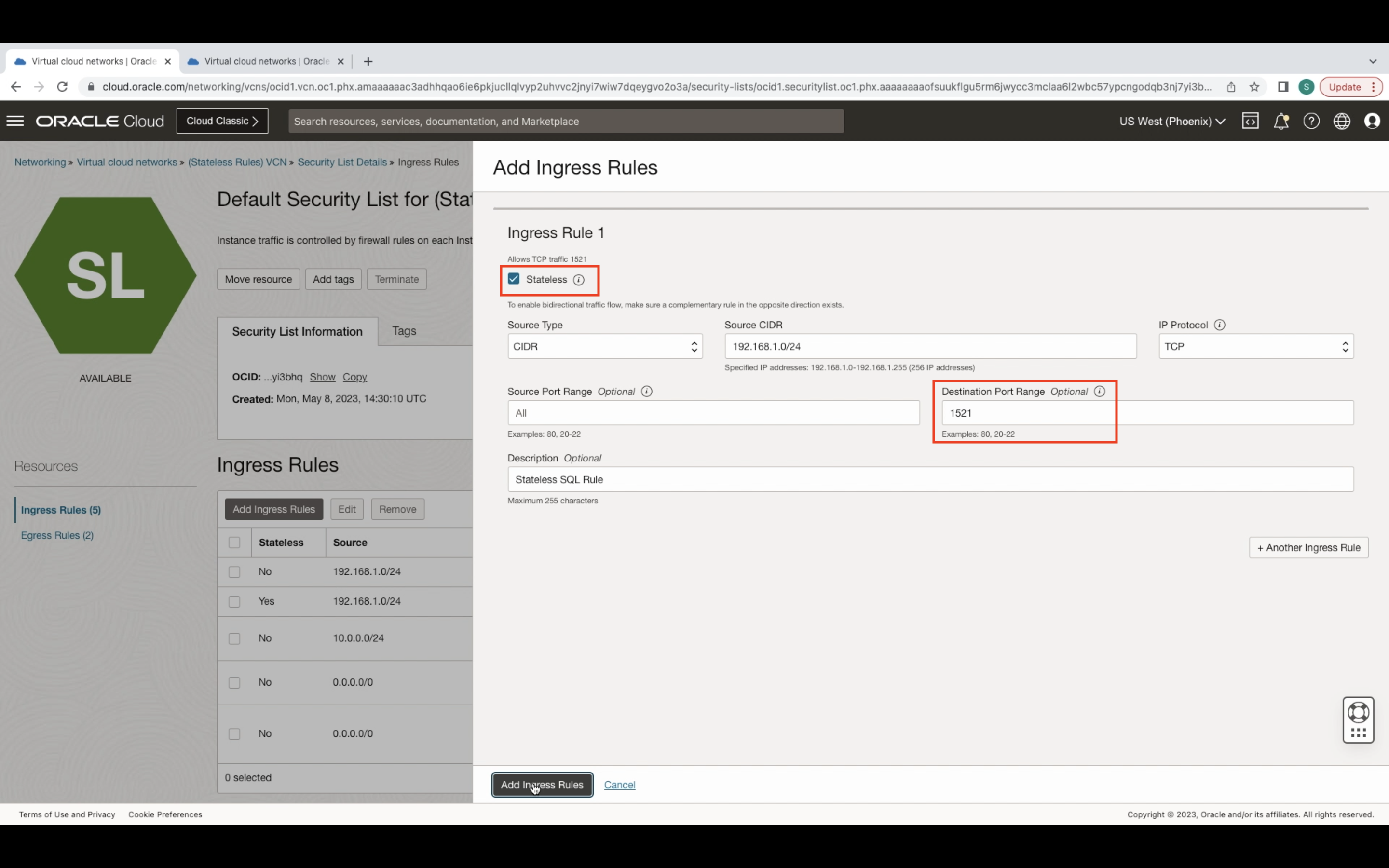
For the ingress rule, select the Stateless rule button. Then specify the incoming source address, IP Protocol, and destination port. In my example, I’ll use SQL port 1521.
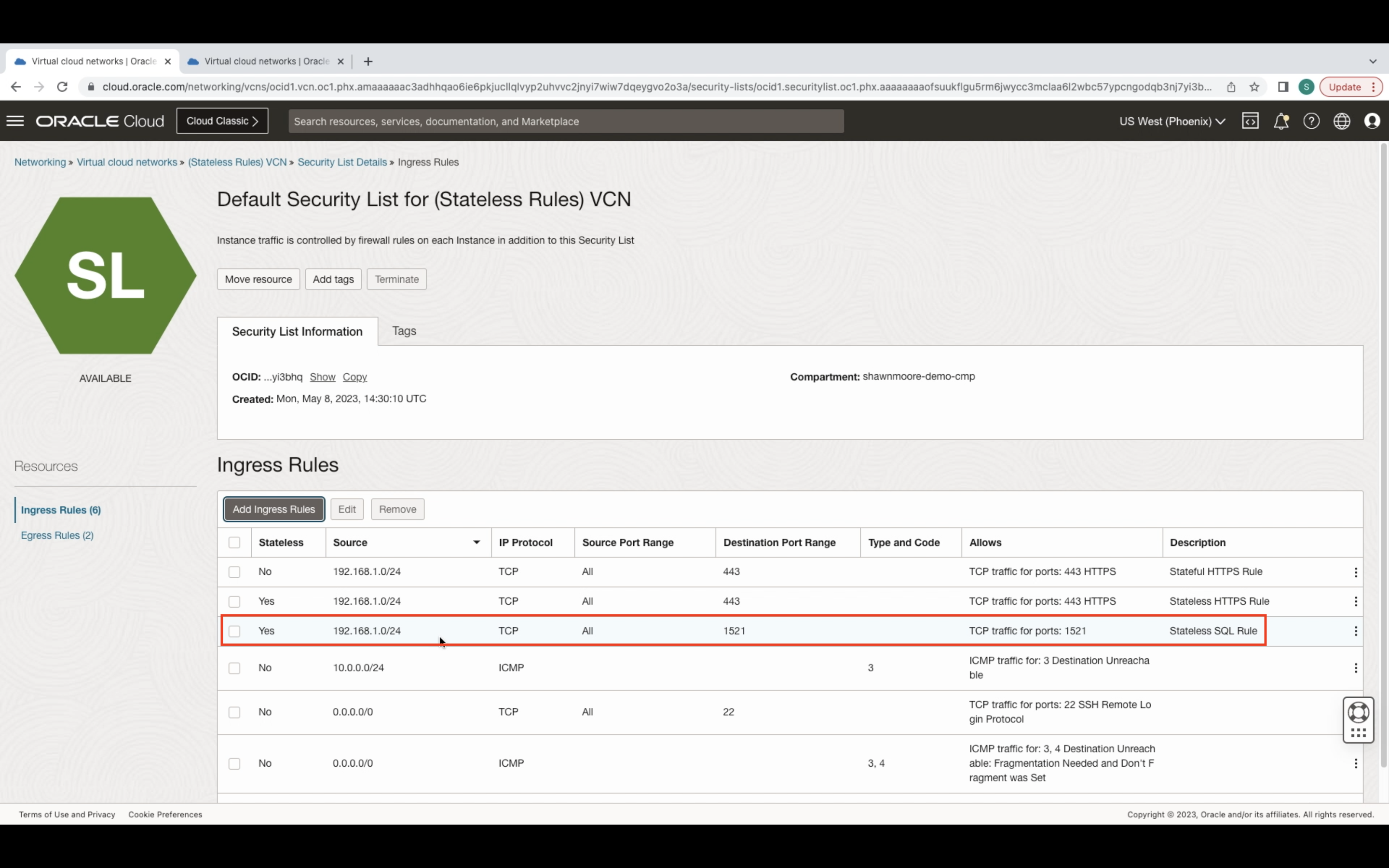
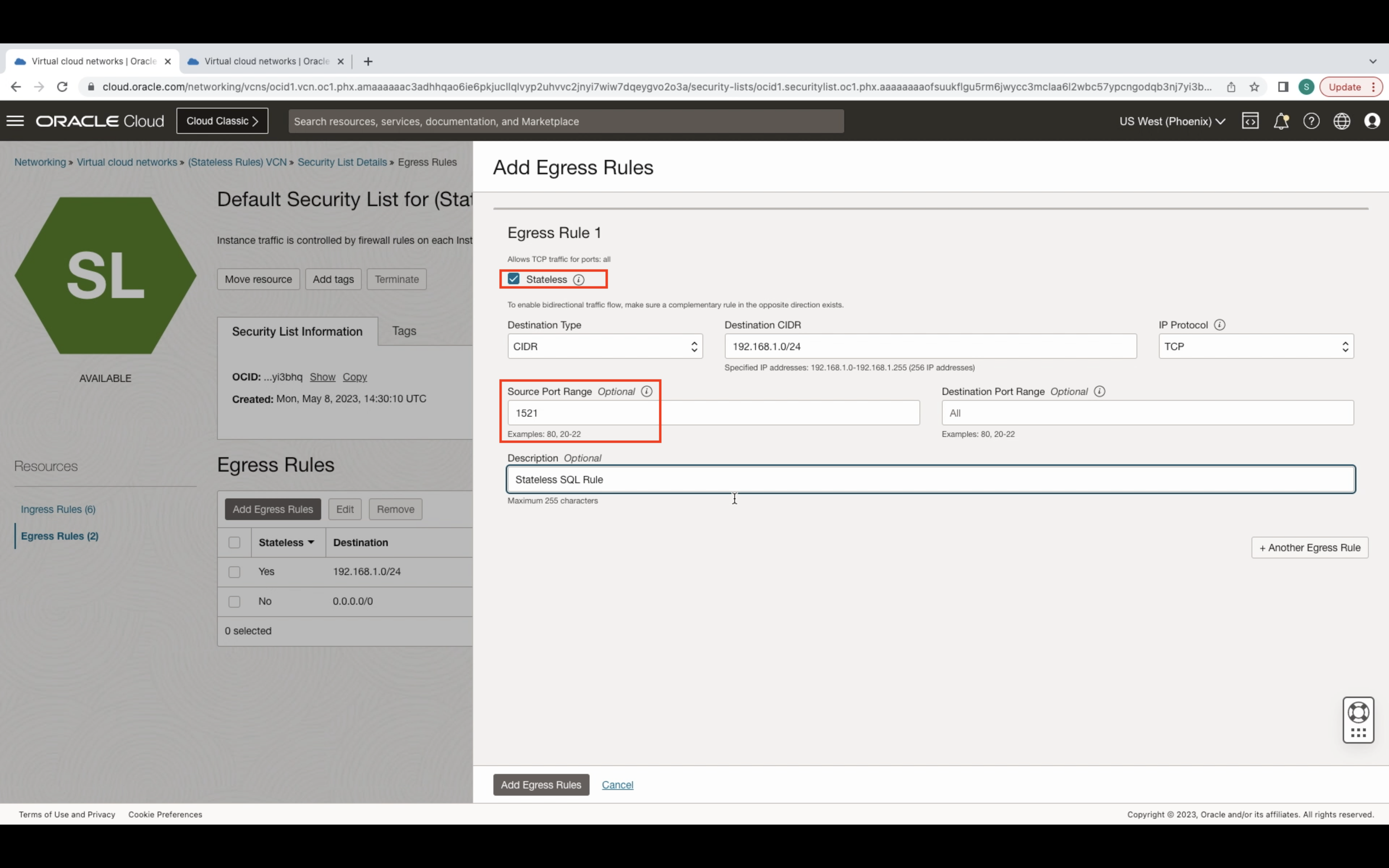
For the egress rule, once again select the Stateless rule button. Specify the destination address (same as the ingress source address) and the same IP Protocol. This time specify the same port (1521) used in the Ingress rule destination port section. The source port is what the OCI resource will respond from. This is needed because there’s no way to associate an egressing TCP packet with a previously received ingress packet and vice versa. Due to lacking connection tracking for the specific TCP port (1521).
As mentioned, stateful sessions are performance limited by each VNICs connection tracking table. VNICs attached to OCI Instances provide many metrics related to networking such as connection tracking metrics. The Connection Tracking Utilization metric shows how many concurrent TCP port sessions are open on the VNIC. Here we can see that 80% utilization was reached at different intervals throughout the day.
![]()
The Connection Tracking Table Full metric shows rather or not the VNICs connection tracking table is full. If this boolean metric changes from 0 to 1, it’s indicating a full table, any further sessions are dropped.
![]()
Two additional metrics shows if ingress or egress packets have been dropped due to a full Connection Tracking Table. The size of a VNICs connection tracking table is varied by Instance size.
![]()
![]()
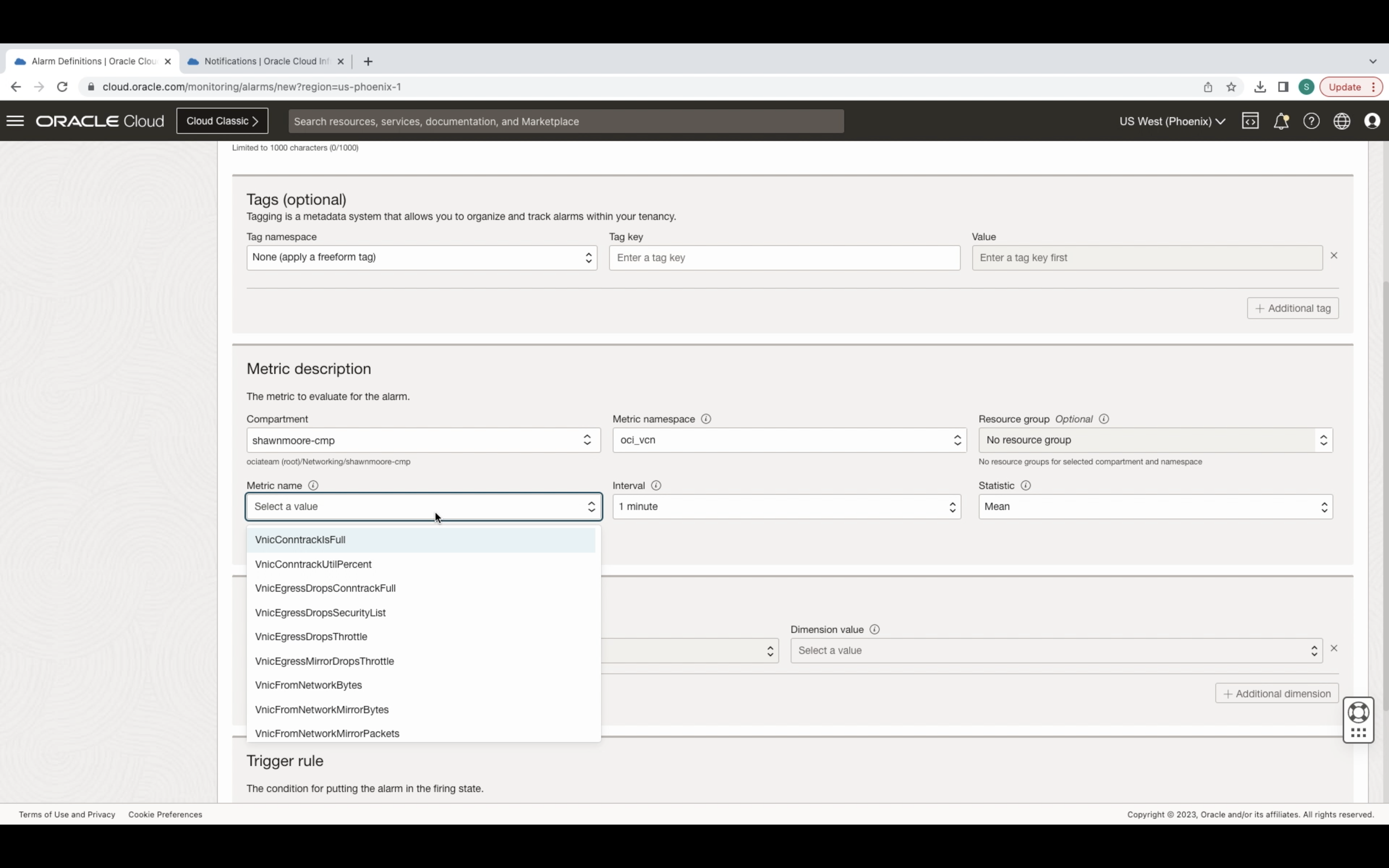
You can Monitor VNIC connection tracking metrics by creating alarms based on threshold requirements. When creating an alarm, provide a descriptive name, and provide a Metric Description. Connection tracking metrics are located under the oci_vcn metric namespace.
In the metric name drop down you’ll find the VNIC connection tracking metrics. From here, complete the rest of your threshold and notification requirements.
Keep in mind stateful rules are fine in most use cases. However, when every microsecond matters or large concurrent TCP connections are needed, deploying stateless rules to prevent many of the network performance and connectivity issues outlined above.
References
Below are helpful guides to learn more about OCI security rules and best practices.
