- The CIS compliance checking script is not impacted. Users should continue using it to determine tenancy compliance with the CIS OCI Foundations Benchmark.
- Users looking for a deployment experience similar to CIS Landing Zone should now use OCI Core Landing Zone, where the same features are available. OCI Core Landing Zone evolves CIS Landing Zone and complies with CIS OCI Foundations Benchmark.
- Users looking for a deployment experience based on fully declarable and customizable templates should use the Operating Entities Landing Zone or the OCI Landing Zones Modules in the OCI Landing Zones GitHub organization.
Introduction
Scanning for vulnerabilities is a must for any security-conscious organization. Security practitioners know that when a public IP address is made available in the network, its ports will get probed for an attack 30 seconds later. Operating systems not patched regularly with security updates are a honey pot for hackers. And in the cloud’s intrinsic hyper-scale model, easy automation and reporting are equally important. Oracle Cloud Infrastructure provides the Vulnerability Scanning Service (VSS), which is free and allows for quick host/port scanning automation, helping OCI customers to quickly identify and remediate security vulnerabilities.
At a high level, VSS works by defining recipes and targets. A recipe sets the scanning parameters for a resource, including what to scan and how often. A target represents the resource to scan with a recipe, such as compute instances. A nice shortcut is defining a compartment as a target. In which case, all compute instances further deployed in that compartment are automatically made scanning targets.
VSS scans for open ports in public IP addresses and inspects hosts’ operating systems for installed packages, comparing them to several open source vulnerability databases. In addition to that, VSS checks the hosts’ packages configuration against published CIS (Center for Internet Security) Benchmarks. The findings are expressed in vulnerabilities reports, stored in the compartments where targets are defined.
VSS integrates with Cloud Guard service, enabling Cloud Guard to detect and respond to vulnerabilities identified by VSS. The default Cloud Guard configuration detector recipe checks for vulnerabilities and open ports found in a VSS report. The Cloud Guard recipe can be customized for changing port numbers that VSS reports or ignores and changing the vulnerability risk levels that Cloud Guard reports as problems. Using this integration is interesting if you want to aggregate the detection and remediation of tenancy security issues in Cloud Guard.
Please refer to https://docs.oracle.com/en-us/iaas/scanning/using/overview.htm for details on the Vulnerability Scanning Service.
Scanning in Landing Zone
As VSS is a free service, Landing Zone enables it by default, creating a default recipe and four scanning targets, one for each Landing Zone compartment. The default recipe is set to execute weekly on Sundays, which can be easily changed when provisioning the Landing Zone.
With such target settings, any hosts deployed in the Landing Zone compartments are guaranteed to be scanned. All targets are created in the Security compartment, which means the vulnerabilities reports are also created in the Security compartment. The Landing Zone grants Security admins the right to manage these reports while allowing other admins the ability to read them.
The input variables for VSS in Landing Zone are:
- vss_create: whether Vulnerability Scanning Service recipes and targets are to be created in the Landing Zone. Default is true.
- vss_scan_schedule: the scan schedule for the Vulnerability Scanning Service recipe, if enabled. Valid values are WEEKLY or DAILY. Default is WEEKLY.
- vss_scan_day: the weekday for the Vulnerability Scanning Service recipe, if enabled. It only applies if vss_scan_schedule is WEEKLY. Default is SUNDAY.
These settings are displayed in the OCI Resource Manager stack as shown below:
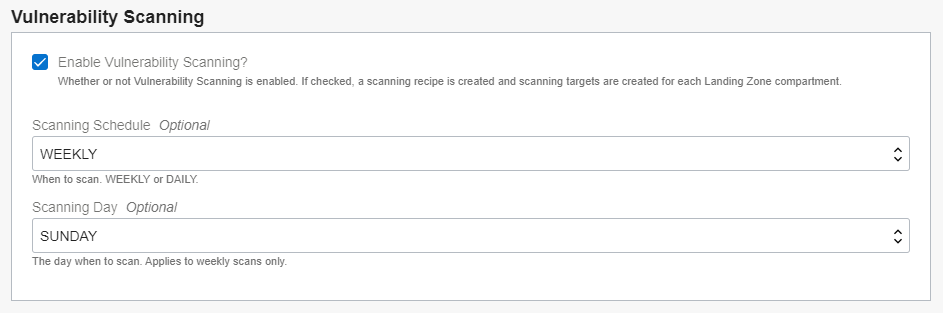
Ports and hosts vulnerability scan levels are set to STANDARD (the highest at the time of this writing), while CIS benchmark scan level is set to MEDIUM (scale is STRICT > MEDIUM > LIGHTWEIGHT > NONE).
Note: These are not exposed as input variables by Landing Zone Terraform, but can be easily customized directly in vss.tf file.
These are the variables to customize in vss.tf:
- port_scan_level: STANDARD, LIGHT or NONE.
- STANDARD checks for the 1000 most common port numbers.
- LIGHT for the 100 most common port numbers.
- NONE disables it.
- agent_scan_level: STANDARD or NONE. This setting effectively enables host scanning via the Oracle Cloud Agent, a lightweight process that manages plugins running in Compute instances. VSS implements one of these plugins.
- STANDARD enables agent-based scanning.
- NONE disables it.
- agent_cis_benchmark_settings_scan_level: STRICT, MEDIUM, LIGHTWEIGT or NONE.
- STRICT: if more than 20% of CIS benchmark items fail, the target is assigned a risk level of Critical.
- MEDIUM: if more than 40% of the CIS benchmark items fail, the target is assigned a risk level of High.
- LIGHTWEIGHT: if more than 80% of the CIS benchmark items fail, the target is assigned a risk level of High.
- NONE: disables it.
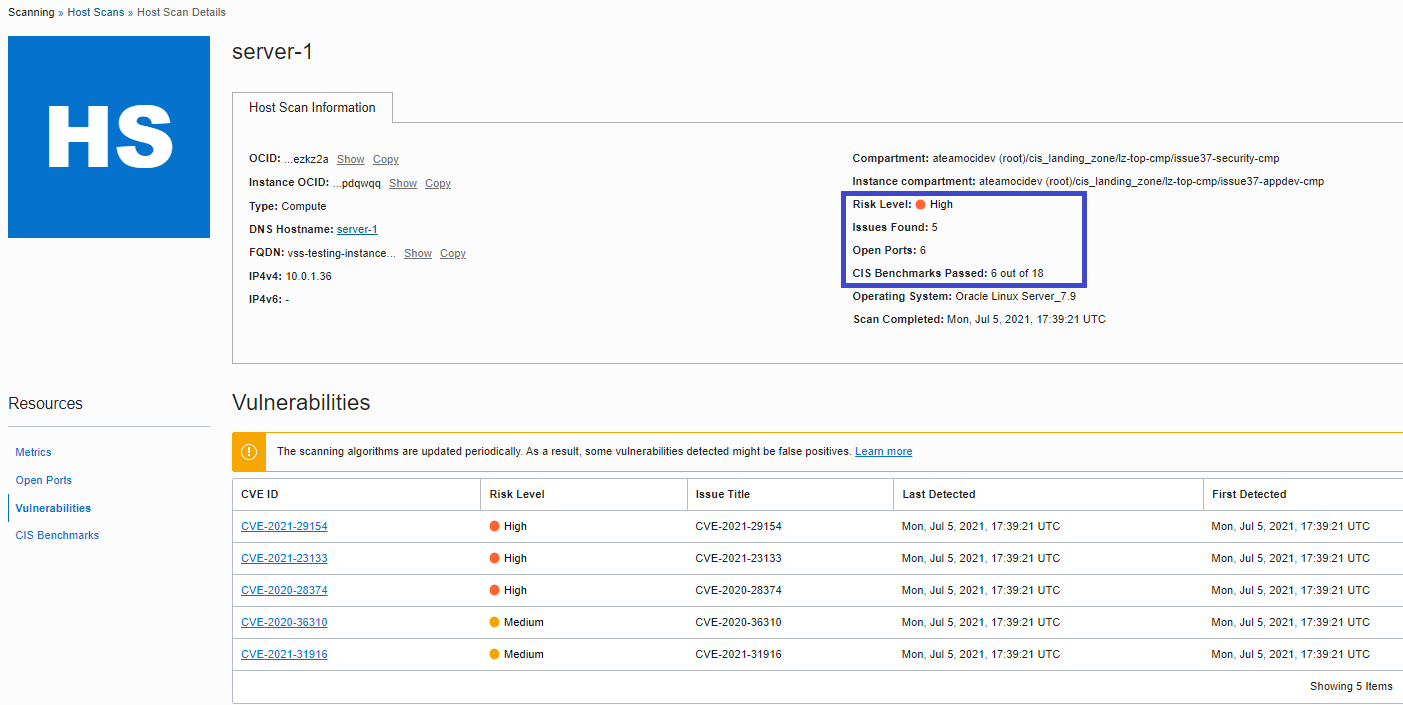
See below OCI Console with the vulnerabilities findings for a server deployed in Landing Zone’s AppDev compartment. Note the information within the blue rectangle for Risk Level, Issues, Open Ports and CIS Benchmarks Passed. The Vulnerabilities table drills down to found Issues (the CVE ID) and their respective Risk Level.
On the left hand-side you can navigate for drilling down to Open Ports and CIS Benchmarks.
Next Steps
Check how the Landing Zone uses other key OCI security services for improving your cloud security posture:
