In modern identity architectures, static or perpetual entitlements are no longer defensible. The principle of least privilege, granting users only the access they need and only for the time they need it, must be implemented as an operational control, not a manual guideline.
Oracle Access Governance (AG) brings temporal governance into the access lifecycle by enabling time-bound entitlements that are provisioned, extended, reviewed, and revoked automatically. This capability enforces access expiration by design and aligns governance controls with Zero Trust and compliance principles.
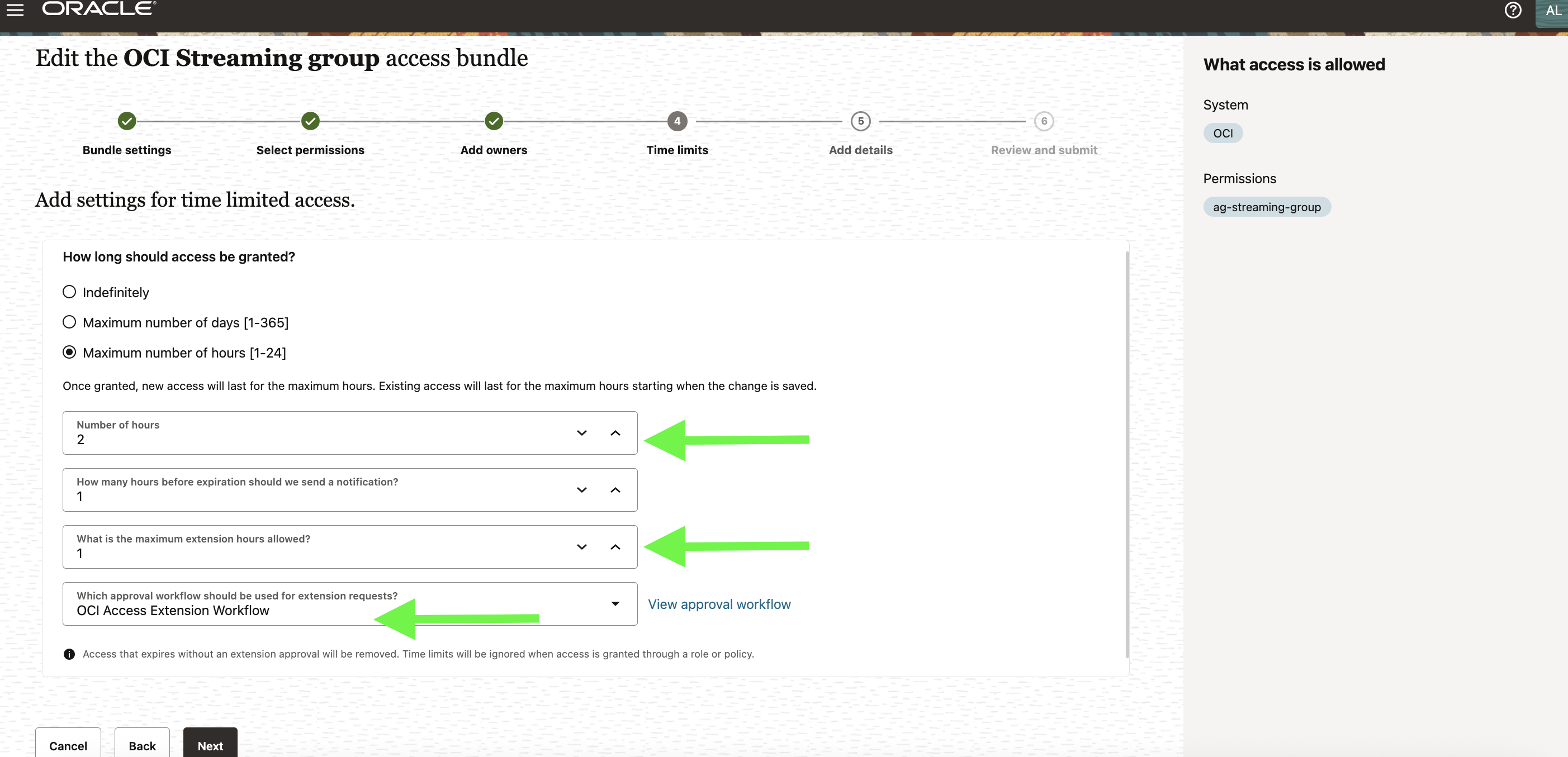
Defining the Time-Bound Access Bundle
The lifecycle begins with the Access Bundle, which acts as a governance contract. Administrators design bundles to encapsulate what access is being granted, such as OCI groups, application roles, or enterprise entitlements, and how long that access should remain valid.
Key configuration elements include:
- Access type: Indefinite or time-bound
- Maximum duration: Defined in days or hours
- Extension policy: Maximum extension allowed, and when to send pre-expiry notifications
- Approval workflows: Separate flows for initial grants and extensions
These parameters enforce temporal boundaries that apply systemically. No user or approver can exceed them, ensuring architectural consistency across all governed systems.
Request Initiation
The next stage involves access requests, typically initiated by end users or managers through the AG self-service interface.
When a request is raised:
- The system validates that the requested duration is within the bundle’s limits.
- The requester specifies a business justification and intended usage window.
- The request is logged and routed through the configured approval workflow.
The key design principle here is constraint enforcement at the UI layer. Users cannot request access longer than what administrators have defined, effectively embedding policy into the request model.

Approval with Temporal Boundaries
Approvers, often line managers, application owners, or delegated authorities, make risk-based decisions on incoming requests.
Within the workflow, the approver can:
- Approve or reject the request.
- Modify the requested duration (shorten or extend) within the bundle’s policy limits.
Once approved, AG orchestrates provisioning to the connected system (for example, OCI IAM, a SaaS application, or an on-prem directory) and records:
- Grant timestamp
- Expiry (Granted until)
This duration metadata becomes part of the entitlement record, providing downstream systems and auditors with clear temporal boundaries for each access instance.
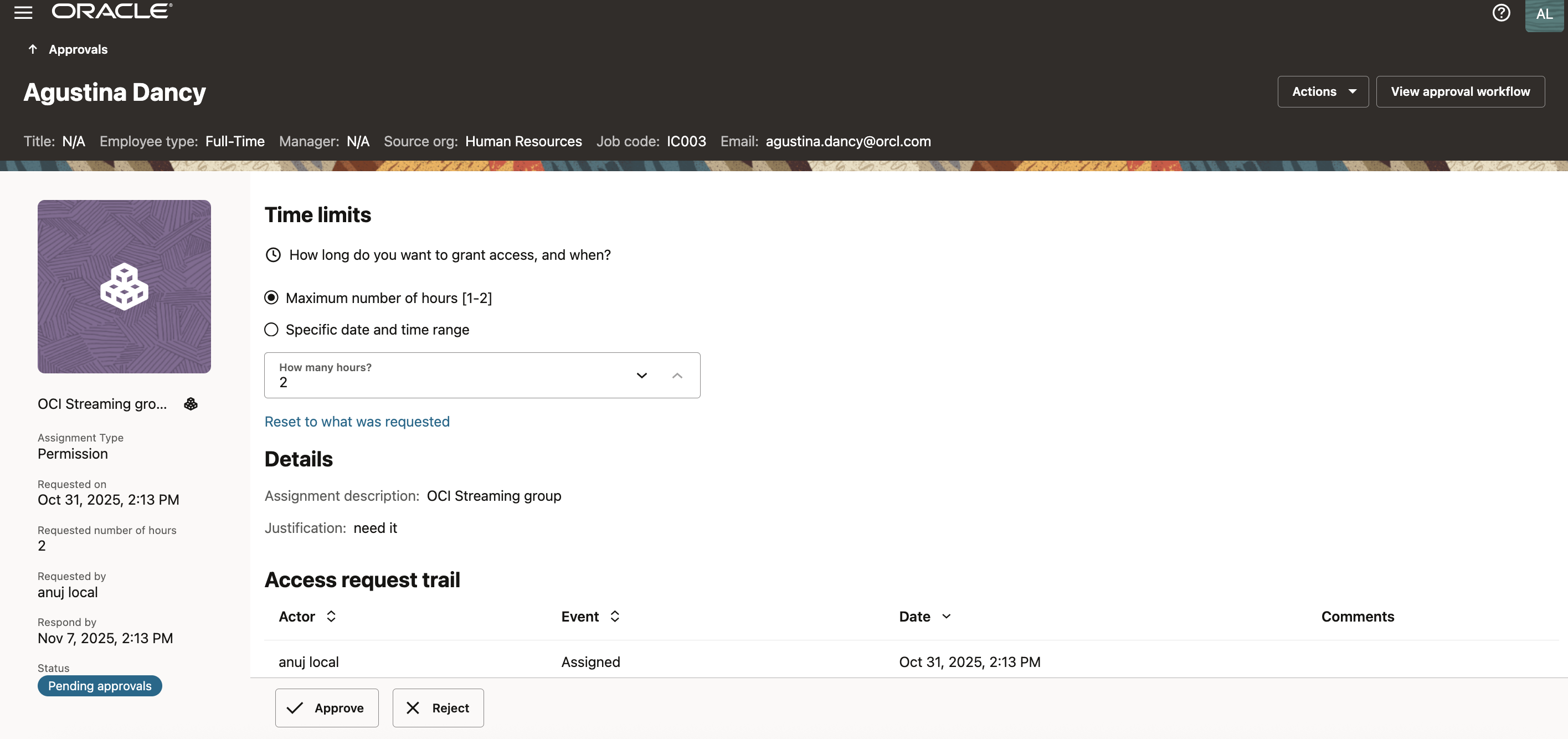
Extension Request Near Expiry
As the access nears expiry, notification events are triggered based on the bundle’s configuration.
Users or admins with ‘AG_ServiceDesk_Admin‘ app-role in AG can initiate extension requests, which are handled as separate transactions under their own workflow.
Architecturally, this separation is deliberate. Extensions follow a distinct approval path, allowing organizations to impose tighter scrutiny or higher approval levels for continued access.
For example, a three-day initial access may allow a single one-day extension with a different approver group, ensuring that extended access remains intentional.
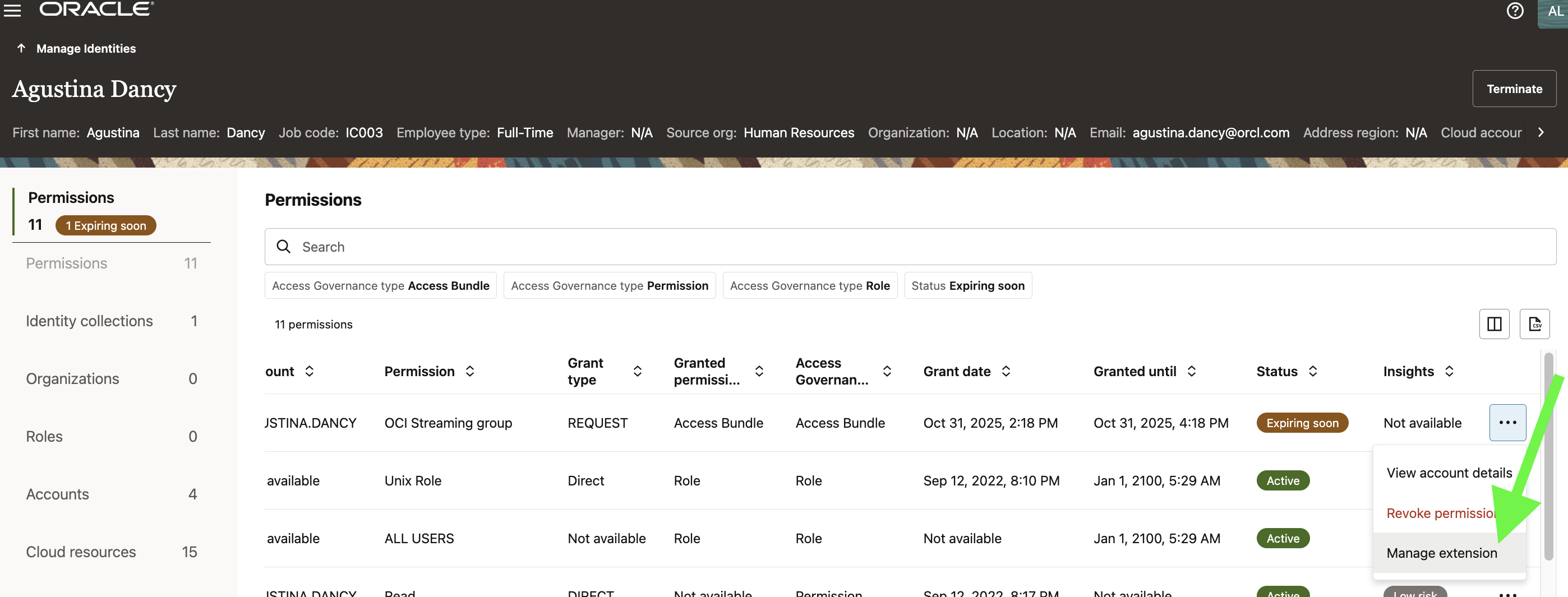

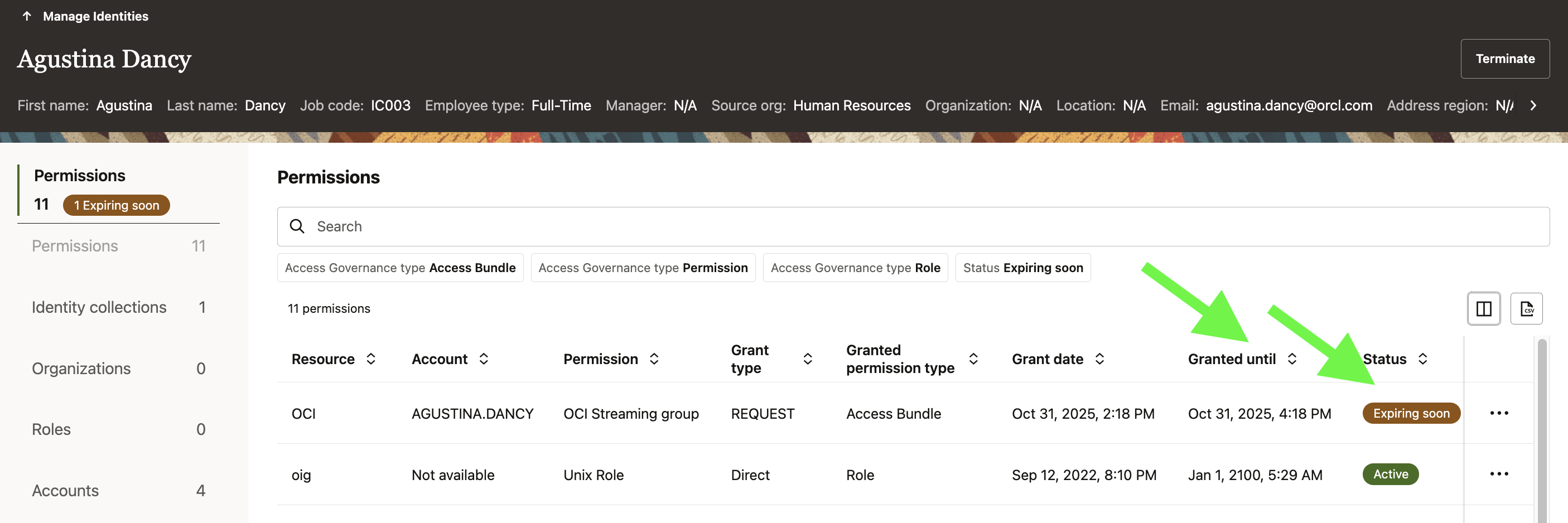
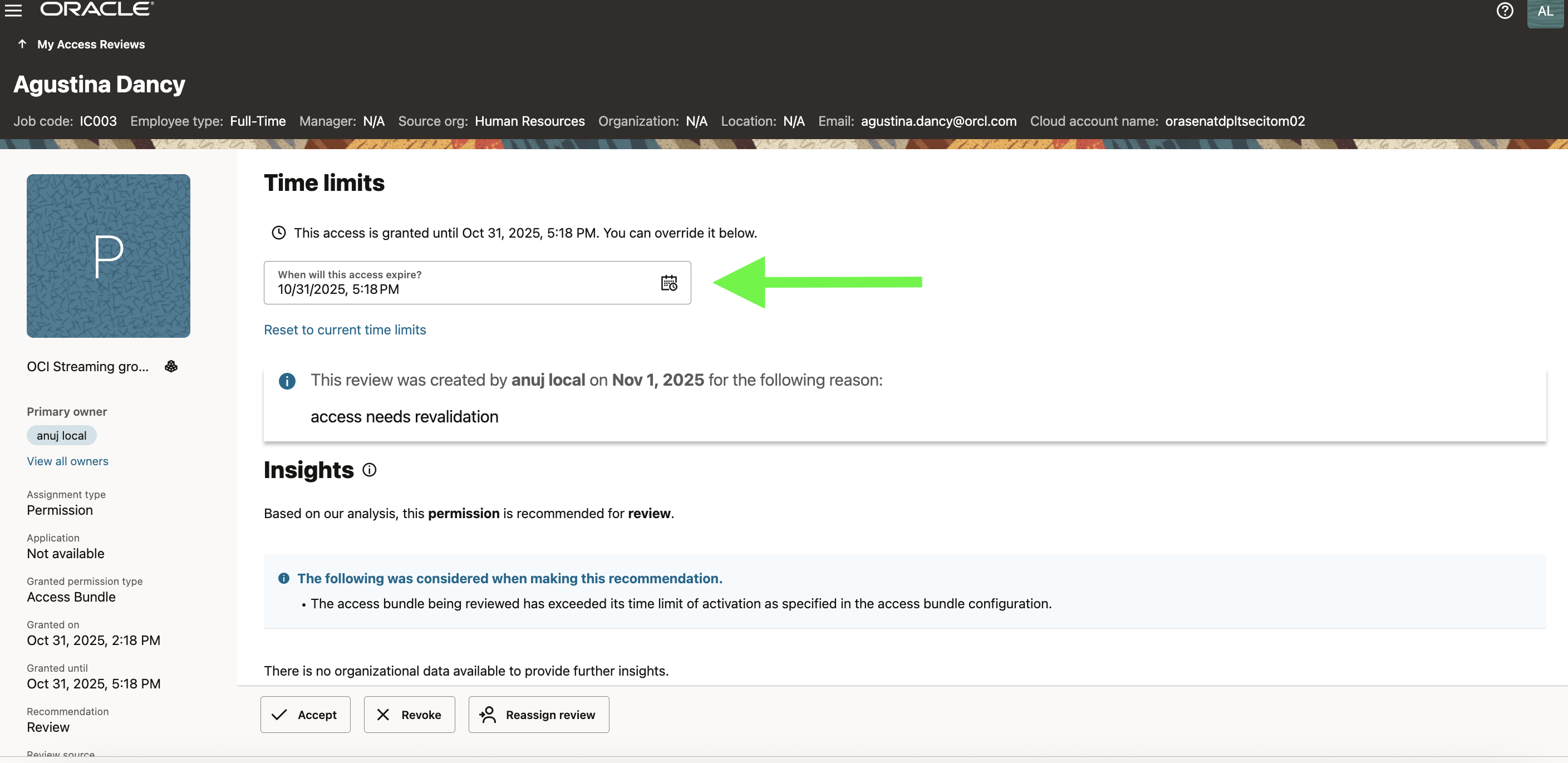
Access Visibility in the User Profile
Once provisioned, AG reflects the entitlement in the user’s Access Profile, showing both grant and expiry details.
This visibility serves multiple governance purposes:
- Users can self-audit their own temporary accesses.
- Administrators and auditors can verify active access windows without querying target systems.
- Access expiration data feeds into campaign readiness for certification cycles.
Access Review and Certification Cycle
When an Access Review campaign is initiated, reviewers operate on the existing time-bound grants. Their actions include:
- Attesting to continued need.
- Revoking access that is no longer justified.
- Adjusting grant duration, either extending or shortening, within configured policy limits.
This design enables reviewers to act as temporal governors within certification workflows.
By integrating duration control into the review interface, AG transforms access reviews from a static validation into an active correction mechanism that keeps privileges aligned with operational necessity.
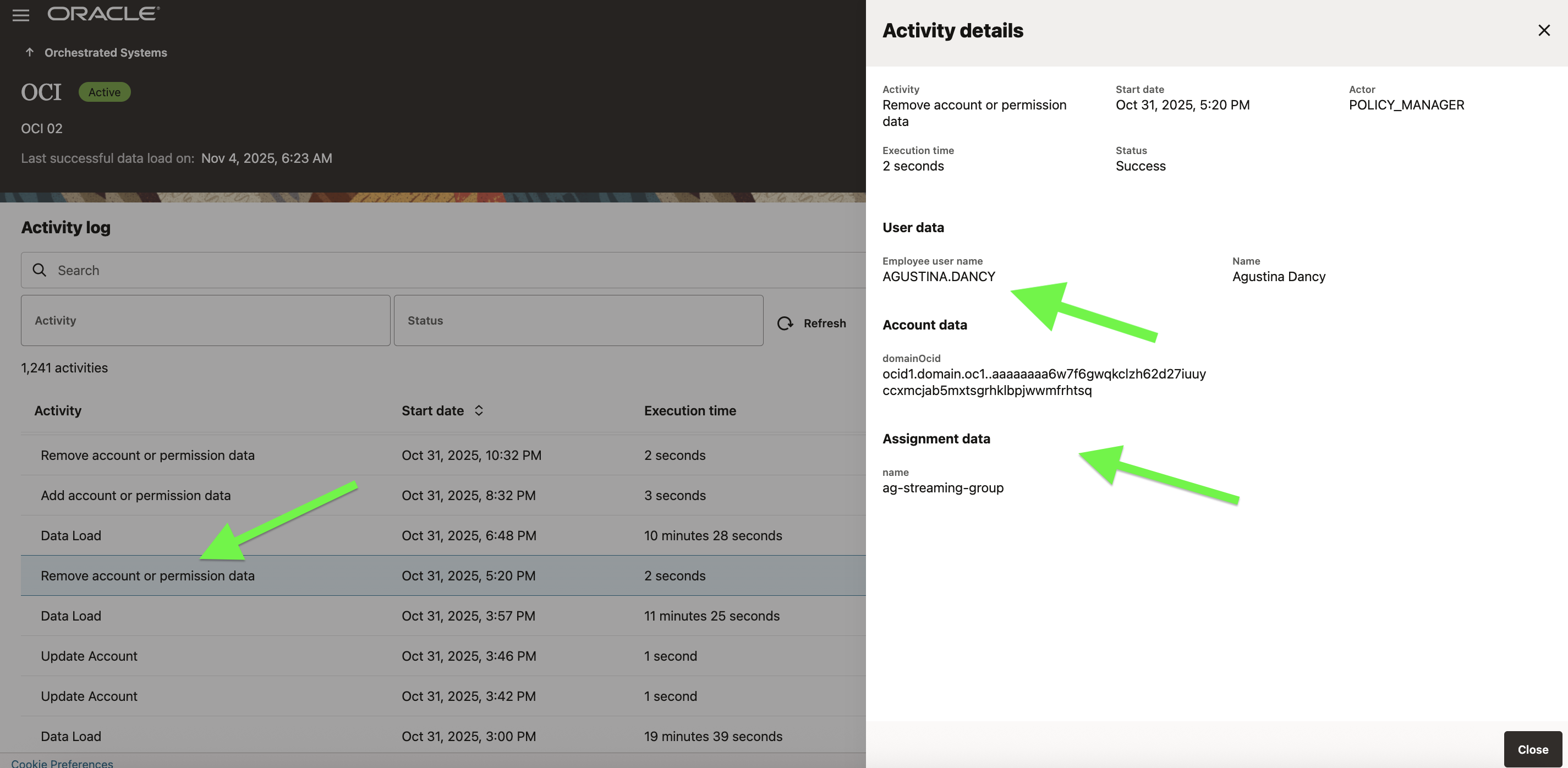
Automated Revocation on Expiry
When the configured or approved duration expires, AG triggers automated revocation across all integrated systems.
This process involves:
- De-provisioning the entitlement from the target system.
- Logging a revocation event in the audit trail.
- Updating the user’s Access Profile to reflect removal.
All actions are captured for traceability and compliance, enabling straightforward reporting of who had what access, for how long, and under which approval path.
This automation removes the administrative overhead of manual cleanup and eliminates “access drift,” one of the most common sources of privilege escalation and audit findings.
Architectural Advantages and Design Impact
| Dimension |
Architectural Value |
| Security |
Enforces least privilege and just-in-time (JIT) access; eliminates standing entitlements. |
| Governance |
Embeds policy enforcement directly into bundle definitions and approval workflows. |
| Compliance |
Every entitlement has verifiable start and end timestamps for audit assurance. |
| Scalability |
A consistent pattern applicable across OCI, SaaS, and on-prem targets without per-system customization. |
| Operational Efficiency |
Reduces manual intervention through automated expiry and lifecycle orchestration. |
Conclusion
From definition to revocation, Oracle Access Governance treats time as a first-class governance dimension.
By combining bundle-based configuration, workflow-driven approvals, temporal constraints, and event-driven revocation, AG operationalizes least privilege in a measurable and auditable way.
For IAM architects, this model represents a policy-encoded lifecycle where access is no longer open-ended but self-expiring, reviewable, and fully governed across the enterprise identity fabric.
