Introduction
Oracle Integration (OIC) Gen3 supports OAuth 2.0-based connections to Fusion Applications which is better security posture to replace basic authentication with JWT token flows. Customers invoking Oracle SOAP services can leverage secure OAuth flows.
This blog covers two approaches (Fixed Credential Method) –
Connection security type – OAuth 2.0 in OIC Gen3 SOAP Adaptor is designed for inbound authentication (external → OIC), not for outbound calls from OIC to FA SOAP, it protects OIC APIs (SOAP) to external callers using OAuth token validation, the external client must provide an OAuth2.0 token when invoking the OIC SOAP trigger ie. OAuth2.0 is protecting OIC’s exposed trigger endpoint.
As of now Oracle Integration Cloud (OIC) Gen3 SOAP adapters do not natively support identity propagation in the same way as newer REST adapters, this is why Authorization Code is recommended flow for SOAP calls in OIC when you want long-lived / user-context aware integrations.
Refer – Identity Propagation – VBCS > IC > Fusion Apps
Connection security policy – OAuth using JWT User Assertion which provides identity propagation is not available as of now in SOAP adaptor
Refer – A Test Run of Identity Propagation with OIC REST Adapter
We’ll also compare them, share use cases, and provide a decision tree to help you choose the right method.
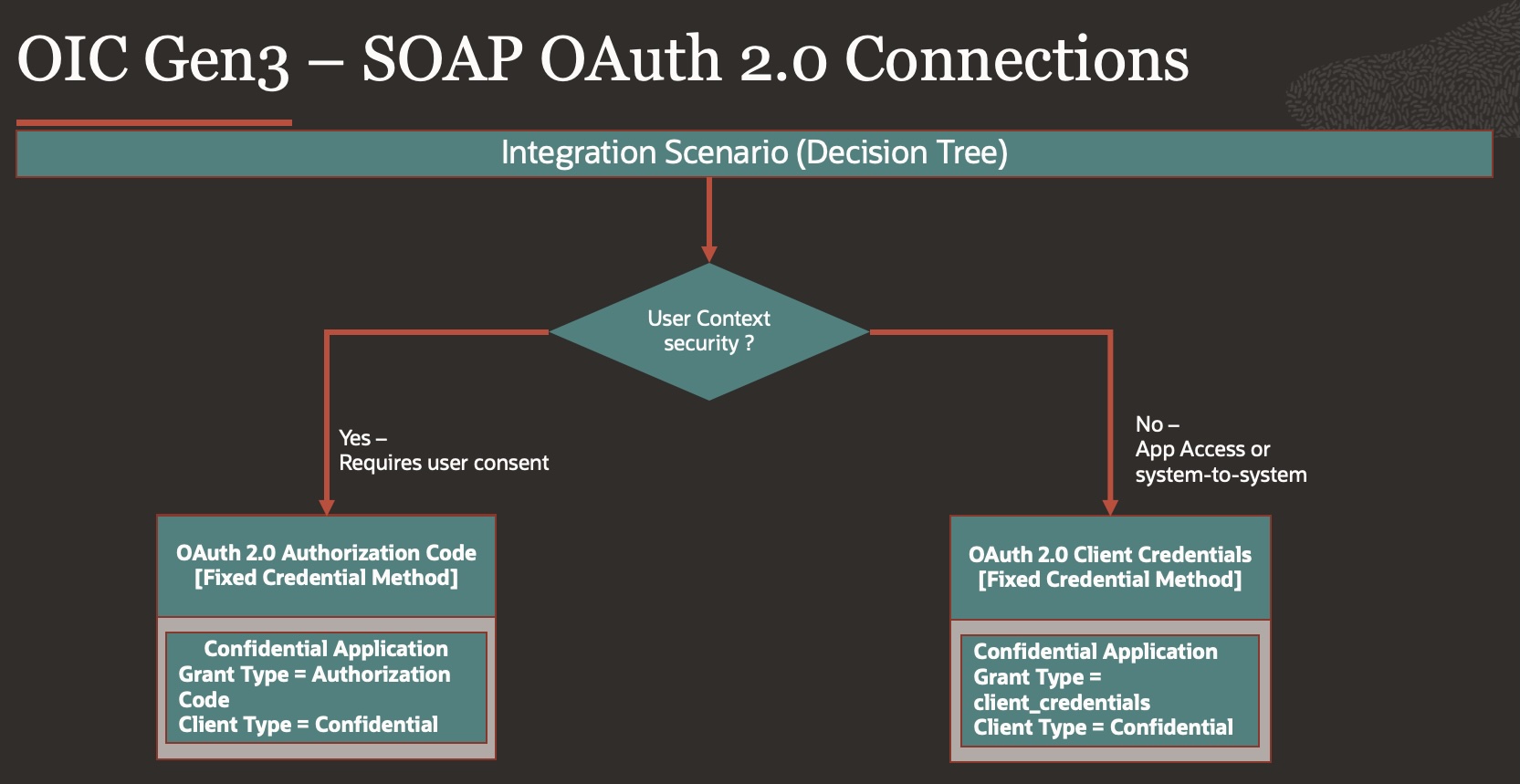
Details:
1. Using OAuth 2.0 Authorization Code Flow
When to Use
Best suited for user-context operations where actions must run on behalf of a Fusion Applications user.
Steps
- Create OAuth Confidential Client in FA IAM
- Login to IAM in same domain which is domain of FA
- Navigate to Identity > Domain> Choose FA Domain
- Go to Integrated Application, Press Button – Add Application
- Choose Confidential Application.
- Configure this application as a client now
- Select Client Configuration
- Authorization Code
- Refresh Token
- Add the Redirect URI for OIC Gen3:
- https://<oic_instance>/ic/pub/oauth2callback
- https://<oic_instance>/icsapis/agent/oauth/callback
- Add Resource >> Add Scope
- Oracle Applications Cloud (Fusion)
- Press Next for Configure Policy
- Finish
- Activate Application.
- Make note of the application’s Client ID and Client Secret & Scope.
- Configure Connection in OIC Gen3
- Create a new SOAP Connection.
- Enter WSDL URL Information ending with ?wsdl
- Choose OAuth 2.0 Authorization Code as the security policy.
- Enter:
- Client ID & Client Secret (from IAM app).
- Authorization Code URI (FA IAM /oauth2/v1/authorize).
- Access Token URI (FA IAM /oauth2/v1/token).
- Optional Security
- Scope (Defined from IAM app – Resource/Scope)
- In scope to obtain refresh token along with access_token, you need to add – offline_access, refer Scopes, eg..
- urn:opc:resource:fa:instanceid=XXXXXurn:opc:resource:consumer::all offline_access
- Client Authentication – Send client credential as basic auth header
- Test the connection – you’ll be prompted for consent.
- Enter Fusion Application Username/password.
- Post Consent, test, validate and save connection.
- Use in Integration
- Invoke SOAP adapter
- OIC automatically injects the JWT Bearer token.
- No need to manually configure headers.
2. Using OAuth 2.0 Client Credentials Flow
When to Use
Best suited for system-to-system integrations where no user interaction is required. Example: scheduled OIC integration running SOAP calls with service-account privileges.
Steps
- Create OAuth Confidential Client in FA IAM
- Login to IAM in same domain which is domain of FA
- Navigate to Identity > Domain> Choose FA Domain
- Go to Integrated Application, Press Button – Add Application
- Choose Confidential Application.
- Configure this application as a client now
- Select Client Configuration
- Client Credentials
- No redirect URI is needed.
- Add Resource >> Add Scope
- Oracle Applications Cloud (Fusion)
- Press Next for Configure Policy
- Finish
- Activate Application.
- Make note of the application’s Client ID and Client Secret & Scope.
- Create the Client ID as a user in Oracle Applications Cloud
In Client Credentials flows, any call is invoked in the context of the application itself and not in the context of a user. Therefore, you must model the application’s client ID as a user in Oracle Applications Cloud.
By creating the Client ID as a user, you are indicating that the user (application) has the necessary role and privileges and is authorized to access the resources.
Complete the following steps to create the Client ID as a user:
-
- Sign in to Oracle Application Cloud.
- On the Security Console, click Users.
- Click Add User Account.
- Under User Information in the Username field, specify the Client ID of the application that you registered with Oracle IDCS.
- Enter the other details under User Information.
- Click Add Role.
- Based on the resources that you want this application to access, add the appropriate roles.
- Configure Connection in OIC Gen3
- Create a new SOAP Connection.
- Enter WSDL URL Information ending with ?wsdl
- Choose OAuth 2.0 Client Credentials as the security policy.
- Enter:
- Client ID & Secret.
- Access Token URI – Token Endpoint.
- Test connection – OIC will request a token automatically.
- Optional Security
- Scope (Defined from IAM app – Resource/Scope)
- Client Authentication – Send client credential as basic auth header
- Test the connection
- Validate and Test – save connection.
- Use in Integration
- Same as above: use SOAP adapter.
- No need for extra headers.
- OIC handles JWT token management.
Pros, Cons & Use Case
| Approach |
Pros |
Cons |
Use Case |
| Authorization Code |
User-context security, honors user privileges, granular |
Requires interactive consent during setup, more complex |
When actions must reflect logged-in user’s access rights |
| Client Credentials |
Simple, fully automated, service account-based, good for batch jobs |
No user-level granularity, all actions run under service account |
System-to-system integrations, scheduled Jobs |
Conclusion
With these approaches, you can securely modernize SOAP calls in OIC Gen3, eliminating basic authentication and aligning with Oracle’s JWT token-based security model.
