Architecture Overview:
We have seen in the blog how to setup inspection of North-South traffic (inbound and outbound) traffic using FortiGate firewall.
In this blog we would be using the same architecture for East-West Traffic Inspection using FortiGate in Hub-and-Spoke Architecture covering two use cases. You can refer to the blog to set up the architecture first, and then return here to configure east-west traffic inspection.
Setting up FortiGate:
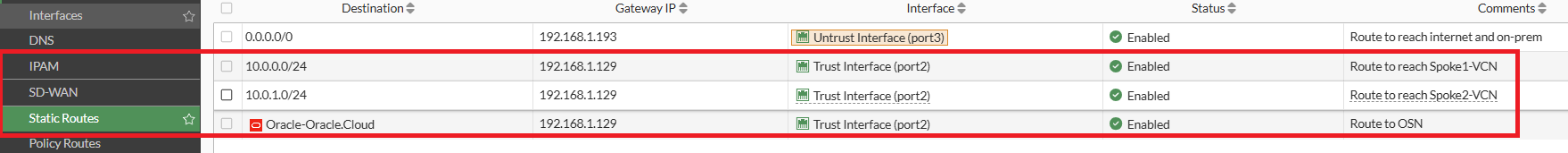
Step 1: Configure Static routing as shown in screenshot below. The purpose of each route is explained in the comments section. For the use cases discussed in this article, the static route highlighted in the red box will be utilized.
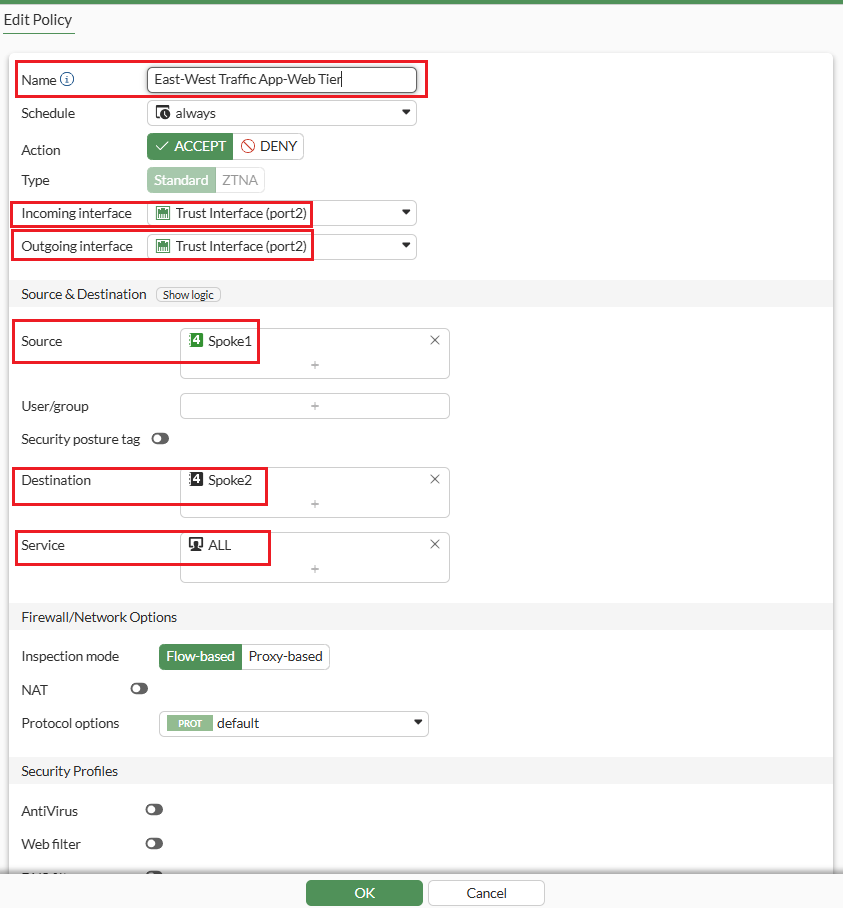
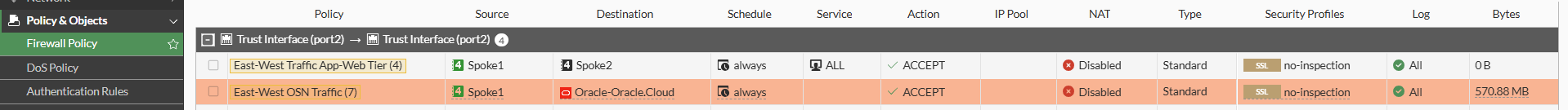
STEP 2: This Fortinet policy below allows internal (East-West) traffic between two trusted zones, Web (Spoke1) and database (Spoke2), over all services. Both incoming and outgoing interfaces use Trust Interface (port2), with no NAT or security profiles enabled. It uses flow-based inspection to efficiently manage traffic between application tiers. The policy ensures secure, unrestricted communication within the internal network.
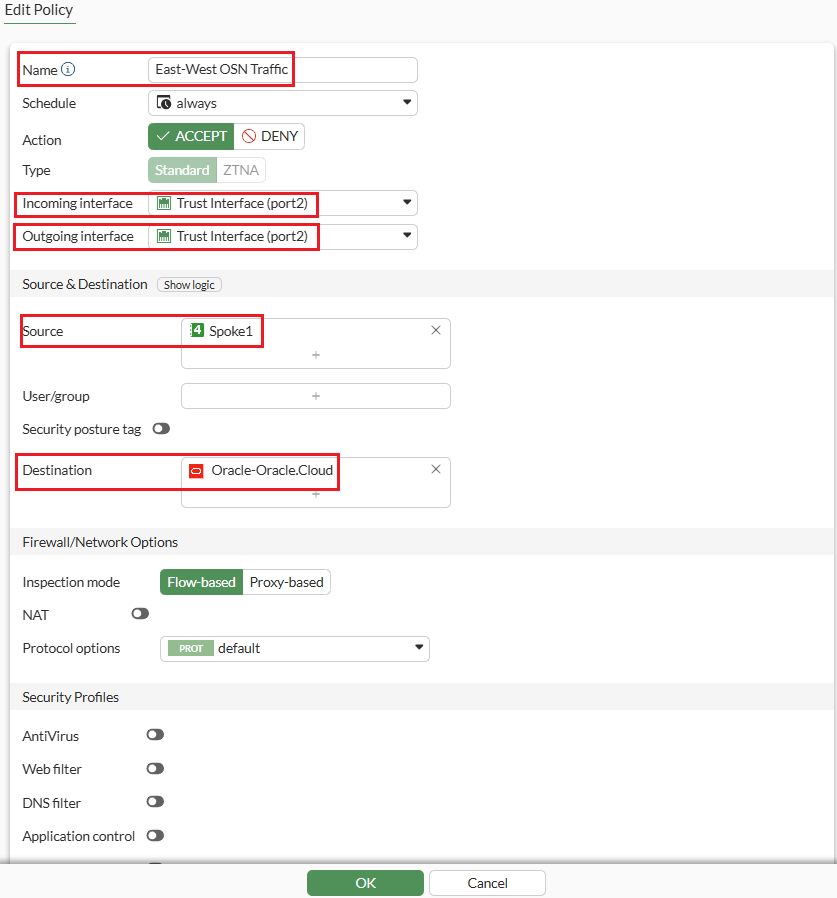
STEP 3: Below Fortinet policy enables East-West traffic from Spoke1 to Oracle services Network(OSN) , using the Trust Interface (port2) for both directions.
The focus is specifically on East-West policies, so we have configured firewall policies for East-West traffic between internal VCN’s , which looks like below.
Demonstrating use cases:
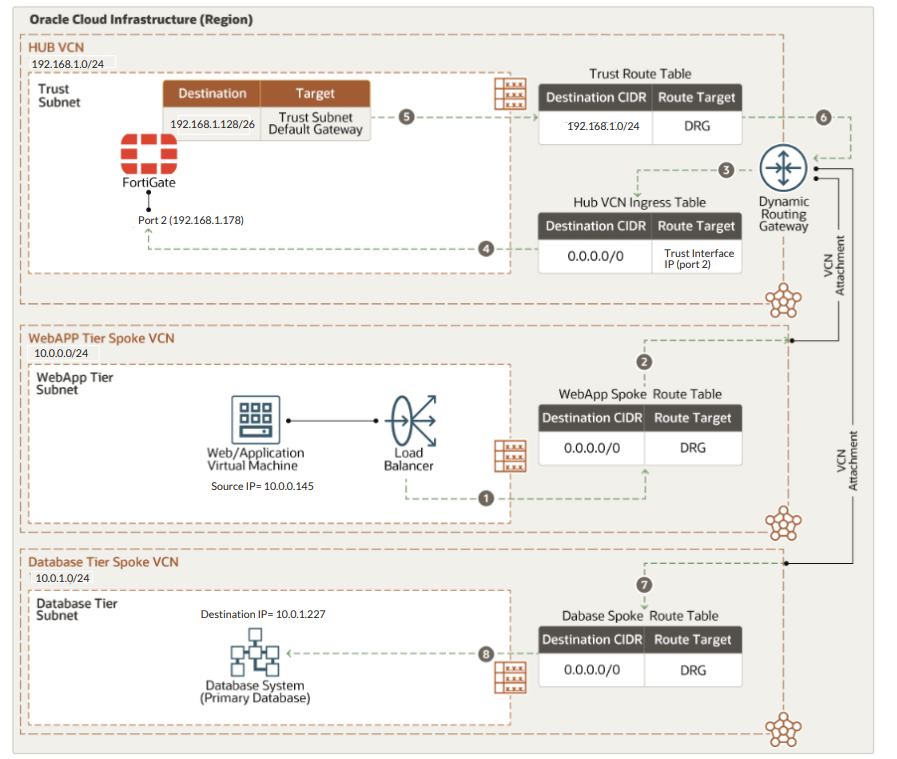
Use Case 1: East-west traffic Inspection (web to database)
The image shows step by step east-west traffic flow from the web/application tier to the database tier in a hub-and-spoke topology. Traffic flows from the web VCN to the database VCN via the hub VCN, passing through the FortiGate firewall (port 2) in the trust subnet over dynamic routing gateway.
Verification:
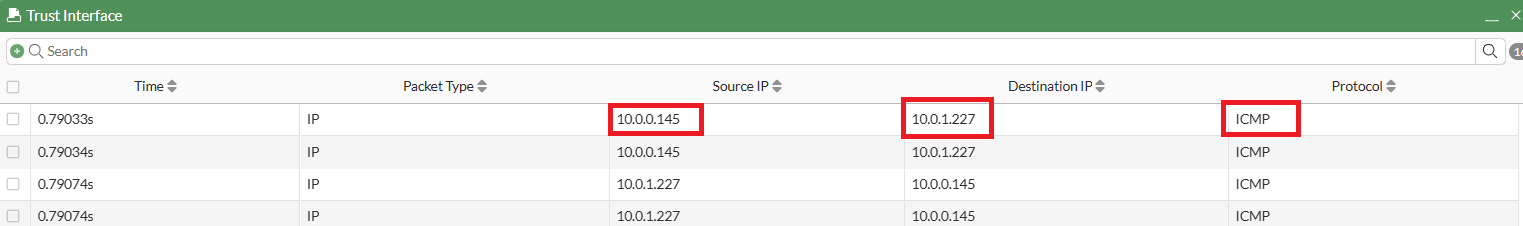
Below image shows ICMP traffic captured on trust interface, flowing between the web tier (source IP: 10.0.0.145) and the database tier (destination IP: 10.0.1.227). The bidirectional traffic indicates successful east-west connectivity along with the inspection of this traffic performed by the Fortinet firewall.
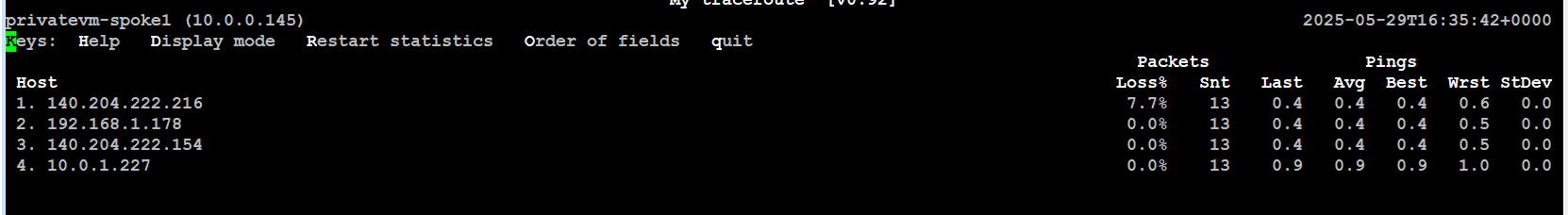
Below image shows MTR output from the web tier in Spoke1 VCN , VM (10.0.0.145) to database tier (10.0.1.227).
Use Case 2: East-west traffic Inspection (Web Application to Oracle Services Network)
The below image showsstep by step east-west traffic flow from the web/application tier to OCI Object Storage and other Oracle services in a hub-and-spoke topology using a Fortinet firewall. Traffic flows from the web tier VCN (10.0.0.0/24) to the hub VCN (192.168.1.0/24) via a DRG, passes through the FortiGate firewall (port 2) for inspection, and is routed to Oracle services through a service gateway.
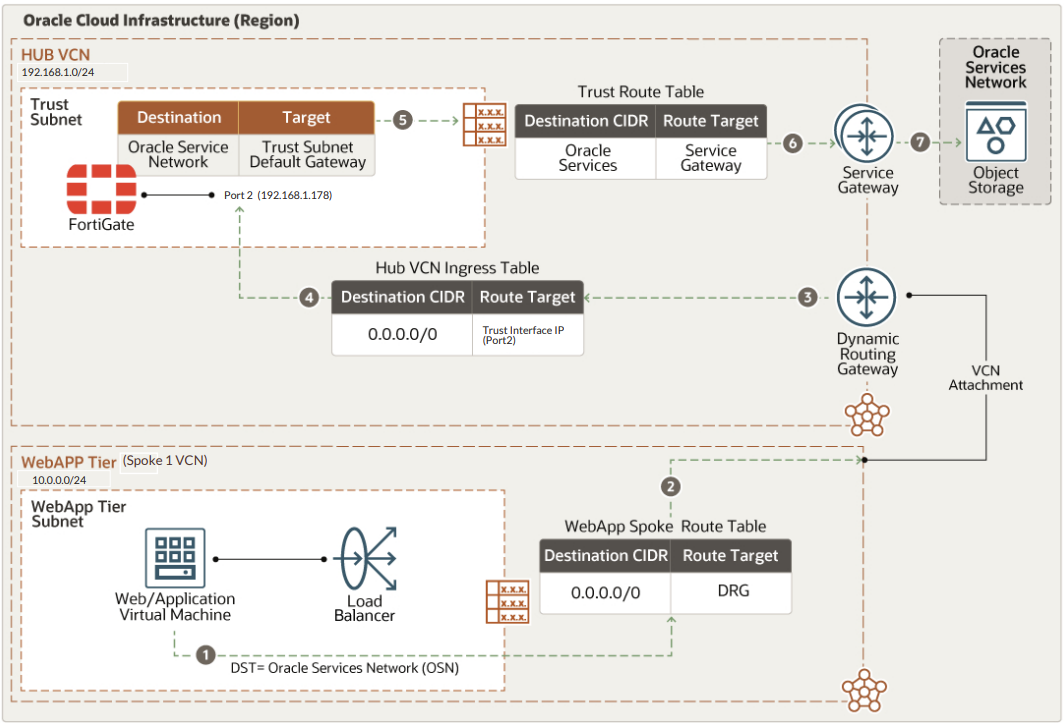
Verification:
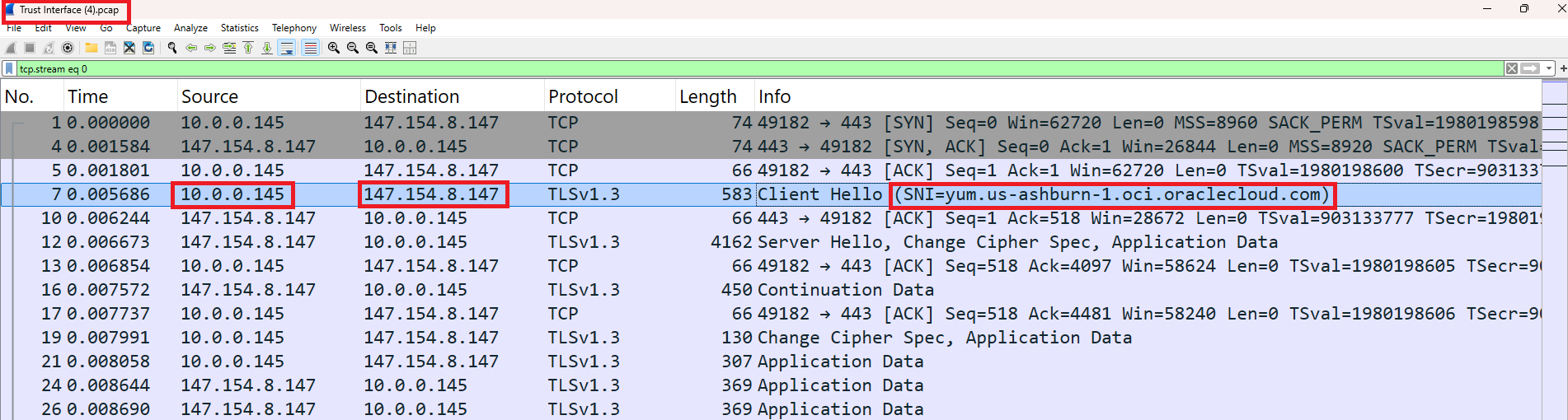
To demonstrate traffic inspection between the Web Tier (source IP: 10.0.0.145) and Oracle Services Network (OSN), we initiate the download of the (nmap-2:7.92-1.el8.x86_64) package from the (ol8_appstream) repository hosted in OSN. This action is performed on a Linux machine within the Web VCN to generate observable traffic for analysis.
While the package is being downloaded, we have collected packet capture on Trust Interface in Wireshark. It highlights a packet initiated by the source IP 10.0.0.145 (web/application tier in spoke VCN) to the destination IP 147.154.8.147 (OSN). The SNI (Server Name Indication) field shows that the traffic is intended for yum.us-ashburn-1.oci.oraclecloud.com, confirming that the web tier is making a secure outbound connection to OCI Object Storage or a related Oracle service via HTTPS and traffic is being inspected by FortiGate firewall.