Managing access to critical systems is a key aspect of enterprise security and compliance. Oracle Access Governance offers Access Guardrails, an access control feature that ensures only authorized and compliant identities can gain access to specific permissions. By implementing Access Guardrails, organizations can enforce security and compliance policies, maintain Segregation of Duties (SoD), prevent conflicts of interest, and minimize security risks.
This article explores how Access Guardrails work, how they can be leveraged to enforce Segregation of Duties (SoD) policies, enhancing overall security and compliance.
Access Bundles in the Context of OCI
An Access Bundle is a set of permissions that users can request collectively as a single unit. These bundles simplify access management by grouping permissions that are frequently requested together.
In the context of Access Governance for managing users and their access to Oracle Cloud Infrastructure (OCI), Access Bundles can include one or more OCI groups and application roles, which can be assigned to users through manual access requests or automated policies.
For example, consider a scenario with three different OCI groups:
Security Admins : Grants administrative access to manage security policies.
Network Admins : Grants administrative control over network resources.
Application Admins : Grants administrative access to applications and related resources.
To streamline user access management for these OCI groups, Access Bundles can be defined, each representing one of the above OCI groups. These bundles can then be associated with Access Guardrails, as discussed next.
What Are Access Guardrails?
Access Guardrails are assigned to Access Bundles to define eligibility criteria for granting access. These criteria help ensure that users meet specific requirements before being granted permissions.
Common examples of Access Guardrails include:
- Mandatory training completion
- Preventing toxic combinations of permissions (Segregation of Duties)
- Identity attributes such as organization, location, or department
By enforcing these guardrails, organizations can control access at a granular level, reducing security risks and improving compliance.
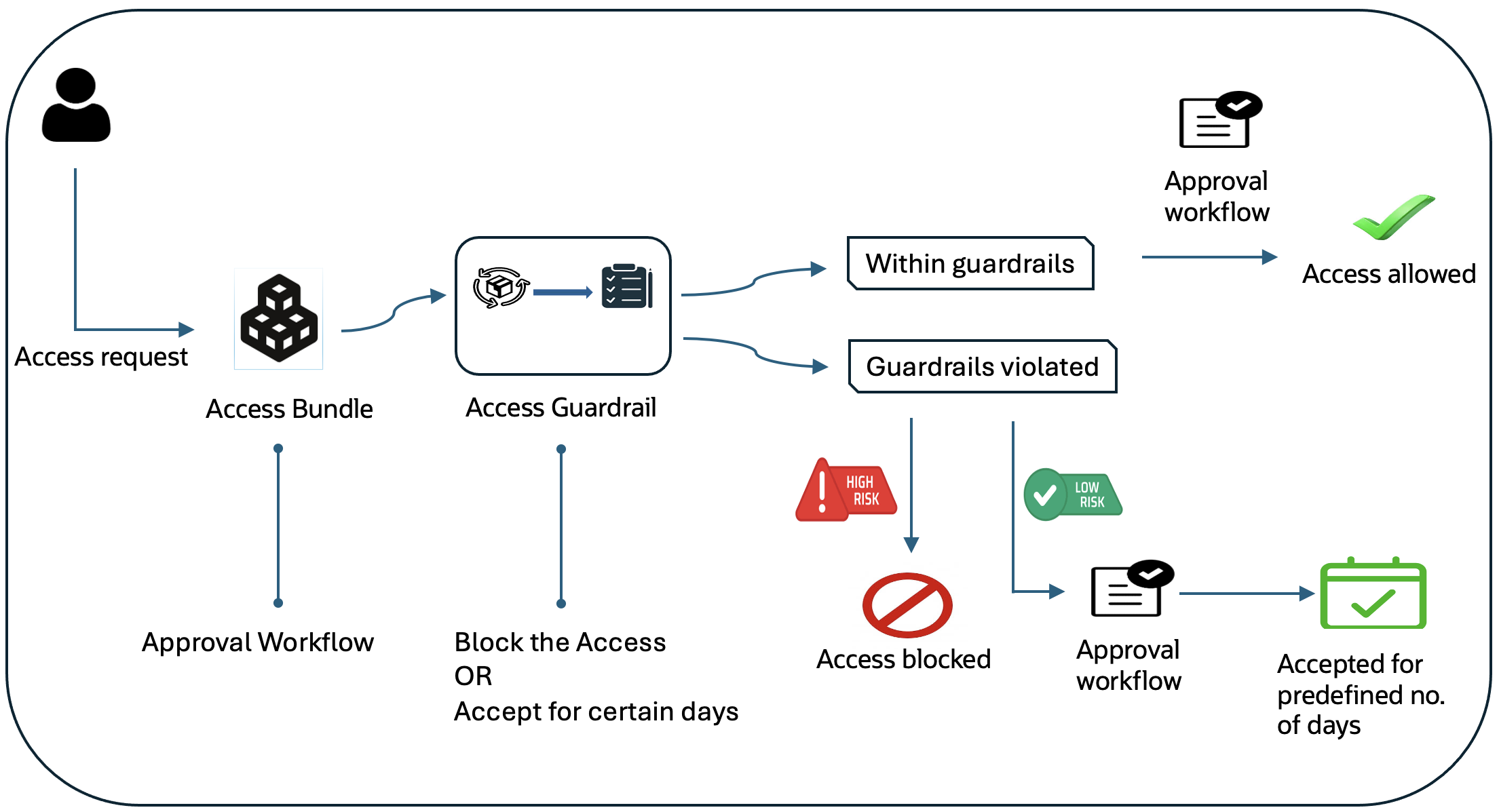
How Access Guardrails Work
Once a guardrail is defined with eligibility criteria, it can be mapped to an Access Bundle. This ensures that whenever a request is made for the Access Bundle, the corresponding guardrail is evaluated for violations.
Workflow of Access Guardrails Enforcement:
- A user submits an access request for an Access Bundle.
- The request is evaluated against Access Guardrails.
- If the request meets the guardrail criteria, access is granted via an approval workflow if configured.
- If the request violates guardrails, the predefined configuration determines whether it is:
- Immediately blocked
- Accepted for a predefined period with conditional approval.
This enforcement mechanism helps prevent unauthorized access while allowing flexibility in managing exceptions.
Enforcing Segregation of Duties with Access Guardrails
Segregation of Duties (SoD) is a key principle in access control. It ensures that no single user has excessive privileges that could lead to conflicts of interest or security risks.
Referring back to our previous example, a user should not be both a Security Admin and an Application or Network Admin simultaneously, as this could result in excessive control over security policies, network resources, or applications in OCI.
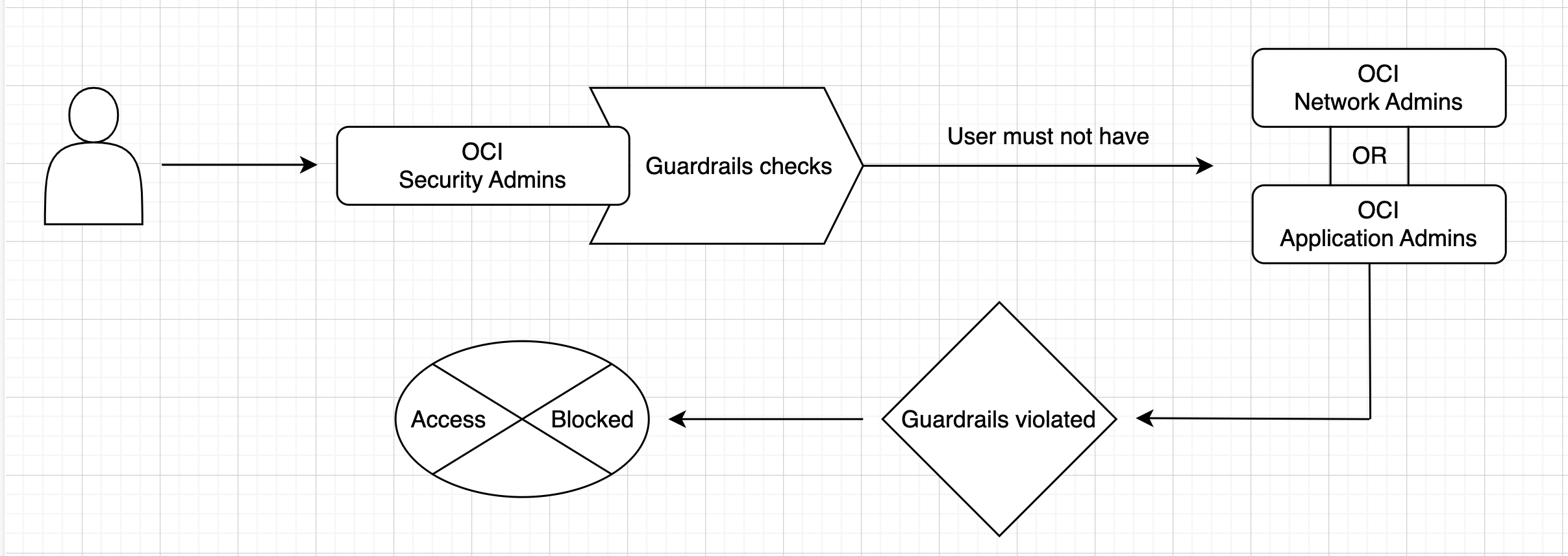
Example: SoD Policy for OCI Administrators
The following diagram illustrates how Access Guardrails prevent users from holding conflicting OCI admin roles:
- A request for OCI Security Admins access bundle is evaluated.
- The guardrails ensure that the user must not have OCI Network Admin or OCI Application Admin privileges.
- If the user holds any of those roles, the request violates the guardrails, and access is blocked.
Cross-System Policy Enforcement with Access Guardrails
While this article focuses on OCI groups, Access Guardrails can also be extended to various applications and services, such as Oracle Fusion, PaaS solutions, as well as on-premises and third-party systems.
For example, Access Guardrails can be configured to enforce dependencies between external systems like Active Directory (AD) and Oracle Fusion roles. For instance, an organization may require that a user can only be granted the Fusion Procurement Manager role if they belong to a specific Active Directory group that signifies procurement approval authority. If the user does not meet this requirement, the access request can be denied or flagged for further review.
Similarly, in Oracle Fusion Cloud ERP, financial roles such as Payables Manager and Receivables Manager should not be assigned to the same user to prevent conflicts of interest and ensure compliance with financial controls. By implementing Access Guardrails, organizations can enforce Segregation of Duties (SoD) policies, ensuring that a user requesting access to the Receivables Manager role does not already have the Payables Manager role.
This extension of gardrails to different services along with cross-system enforcement ensures that access policies remain consistent across cloud and on-premises environments, reducing security risks and maintaining regulatory compliance.
Final Thoughts
As enterprises increasingly adopt Oracle Cloud Infrastructure (OCI), Fusion Applications, and third-party services, the complexity of access management continues to grow, especially in multi-cloud and hybrid environments. To effectively manage user access in this evolving landscape, organizations need a proactive approach. By implementing Access Guardrails, they can:
✅ Enforce Segregation of Duties (SoD) policies to avoid conflicts of interest.
✅ Enforce a least-privilege access model.
✅ Enhance security and compliance across cloud and on-premises environments.
Additional Resources
To learn more about Oracle Access Governance, please refer to the following resources:

