Overview
Security – Like Layers of an Onion
Building layers of security is not a modern concept. In the days, kingdoms built layers of security to protect their castles. Medieval castles were physical security layers with moats, gates, walls, and anchor towers providing different layers of protection against invaders and attackers. Modern-day security relies on building layers of defense, known as layered security or defense-in-depth.
Those layers are like layers of an onion. An onion is not an exotic vegetable or does not look anything special from the outside. Similarly, security is not flashy or always visible from the outside. However, as you bite into it an onion, you sink your teeth into layer after layer of juicy flavor with tears in your eyes.
In security, we build a security onion – a shield of defensive layers that support each other, as shown in the diagram below. If one layer fails, the next one protects the data. The more layers there are, the safer the system (usually).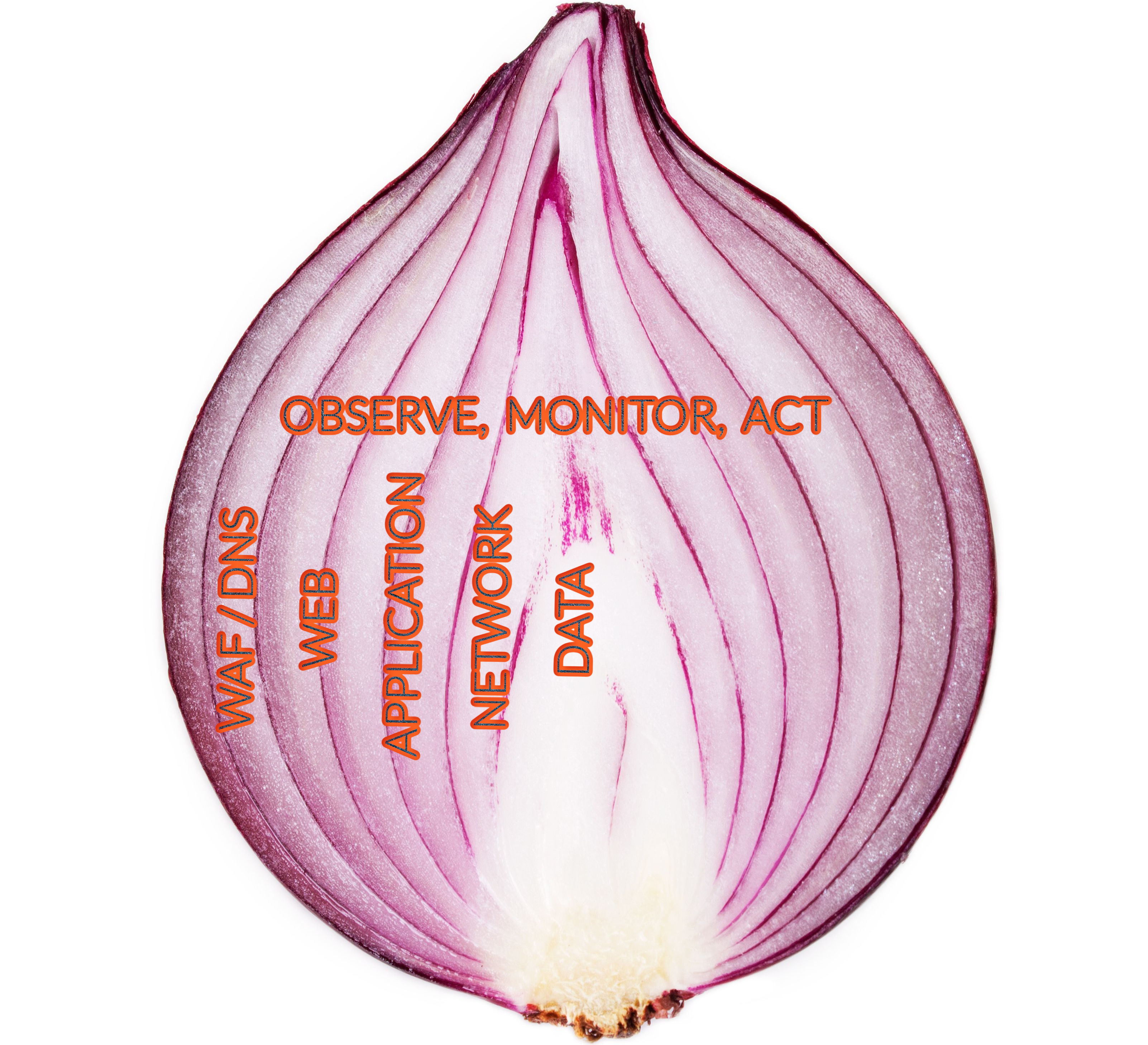
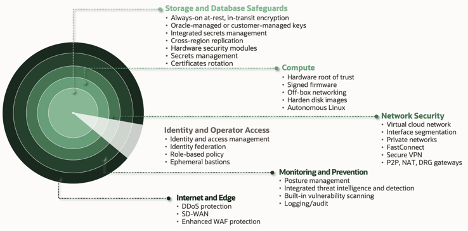
Oracle has implemented multiple layers of security (like layers on the onion) on OCI, starting from data security to Internet and Edge security, as you can see in the below diagram. I will discuss those layers one after the other. In this part-I blog, I will cover data security and application security. Part-II will cover the remaining layers of security.
Data Security
Data is the most fundamental entity/object that needs security in the infrastructure, sometimes referred to as the crown jewel. Refer to my last blog. You must protect data from unauthorized access, modification, and deletion. You also want to ensure uninterrupted and seamless access to the data by designing the maximum available architecture and building tools to access data from different devices (Computer, Phone, Tablet, Watch, API, CLI, etc.).
There are five facets of data security, and I will discuss them one after the other.
1. Securing data from malicious attacks
Protecting data from ill-intentioned individuals (External legit users or Internal users) is often the priority from a security perspective. Several security controls are deployed to prevent malicious attacks; however, last-mile delivery is the key. I have listed them below for reference.
- Deployment of perimeter security to prevent access to an unauthorized application or unauthorized network source
- Conduct regular access governance exercises to revoke stale access to data
- Implement end-to-end Identity life cycle management to de-provision accounts
- Deploy monitoring and reporting tools to monitor and detect malicious access to data
2. Securing data from unauthorized access
Data is the crown jewel of any infrastructure. Unauthorized access is broader and more challenging to detect than malicious access. It could appear like any other legitimate access from a monitoring perspective. For example, a user can access PII data while analyzing marketing campaign results. There are IAM principles or frameworks to prevent unauthorized access to data.
- Least privilege
- Segregation of duties while granting access to data
- Zero trust (Just because an application or user is trying to access data from a known location or device, that does not grant access to data)
3. Securing data from data exfiltration
Users may have access to specific data sets in the ordinary course of their business, but when they attempt to extract a vast number of records, is it because they need to process a historical report — or because they plan to quit tomorrow and leave with the client database? Or maybe they have been victims of some social engineering attack or compromised their credentials? Identifying the boundaries of normal/expected behavior and limiting what a user is permitted to do with data they use daily is an important measure to prevent this situation. Data monitoring with behavior analysis can avoid or block data exfiltration attempts.
4. Securing availability of data
Data is accessed through one of the many available tools and using various devices. It could be a cli or web-based application, or API client. One of the essential design principles to ensure availability with security is to use a single shared interface (API layer) to access data. Every tool would use the interface. We can then implement scaling to ensure availability and authentication with monitoring to ensure security.
5. Ensure secure transfer of data
It is relatively easy to enforce using TLS. However, with multiple tools, it is essential to ensure every device implements a secure version of TLS, a.k.a. TLS 1.3. Any blind spot can lead to a data leak or data compromise.
Data Security in OCI
- Any data stored in OCI (irrespective of storage service or device) is always encrypted.
- Customers can use customer-managed keys to encrypt data. They can also integrate their preferred HSM solution with OCI vault service.
- Administrators must explicitly create IAM policies to allow access to the data. By default, even an authenticated user does not get access to any data.
- Take a secure backup of data in Archival storage.
- Data can only be accessed over TLS-enabled interfaces.
- DLP helps you classify data from object storage and protect it from secure data exfiltration attempts.
Application Security
Application is the first and direct interface for end users to access data. They connect to the interface from both secure and insecure networks. That exposes applications to a range of vulnerabilities and threats. That is why an application is where most prevention controls and processes are deployed, starting from Identity and Access Management, Web Application firewall, API security, and Cybersecurity testing.
API Security
APIs are the basis of next-generation microservices applications. An entire API economy has emerged, enabling organizations to share data across tools and organizations securely. Although APIs are powerful and allow many integrations, they can expose sensitive data and cause significant data breaches. Common security issues of APIs are weak authentication, risks of DDoS attacks, and unwanted data exposure. API Gateway service can help you centralize management and implement policy-based security controls, including audit and monitoring, on all the APIs.
Web Application Firewall (WAF)
A WAF tool monitors and secures traffic between an application and the internet (end-users). It serves as layer seven defense to protect against cross-site scripting, SQL injection, OWASP threats, cross-site forgery, etc. It can also safeguard applications from sophisticated bot attacks. It can enforce access control based on network source and request signature. It can analyze user and application traffic to identify anomalies and protect applications from known and unknown vulnerabilities.
Identity and Access Management (IAM)
Since web applications are the direct interface to access data, IAM helps enforce authentication and authorization to prevent unauthorized access to data. Modern and context-based authentication and authorization can detect anomalies in the user access pattern to block unauthorized access.
Oracle Cloud Infrastructure supports all three application security services (WAF, API Gateway, and IAM) to help customers protect applications and, in turn, data accessed by those applications.
Network Security and Observability
Contrary to the marketing pitch from Identity services, the network remains a vital security perimeter or one of the foundation defense layers of cloud security. It helps protect data, applications, and IT resources deployed within cloud environments and the traffic flowing between cloud and on-premises environments. No amount of security can assure or guarantee hundered percept security. At Oracle, we assume a compromise would take place and have built tools to detect and respond to those compromises as part of Observability and Monitoring platform. I will cover both Network Security and Observability in the next one (Part-II of the blog).
