Overview
I was reading about Maximum availability architecture, and while reading it, I started thinking about Maximum security. However, Is it really a thing? There is no maximum security. You can add layers of protection along with layers of detection. However, you are just one step away from a compromise due to a human error or a security lapse. It may sound not very pleasant, but that’s the reality.
Security – Layers on Onion
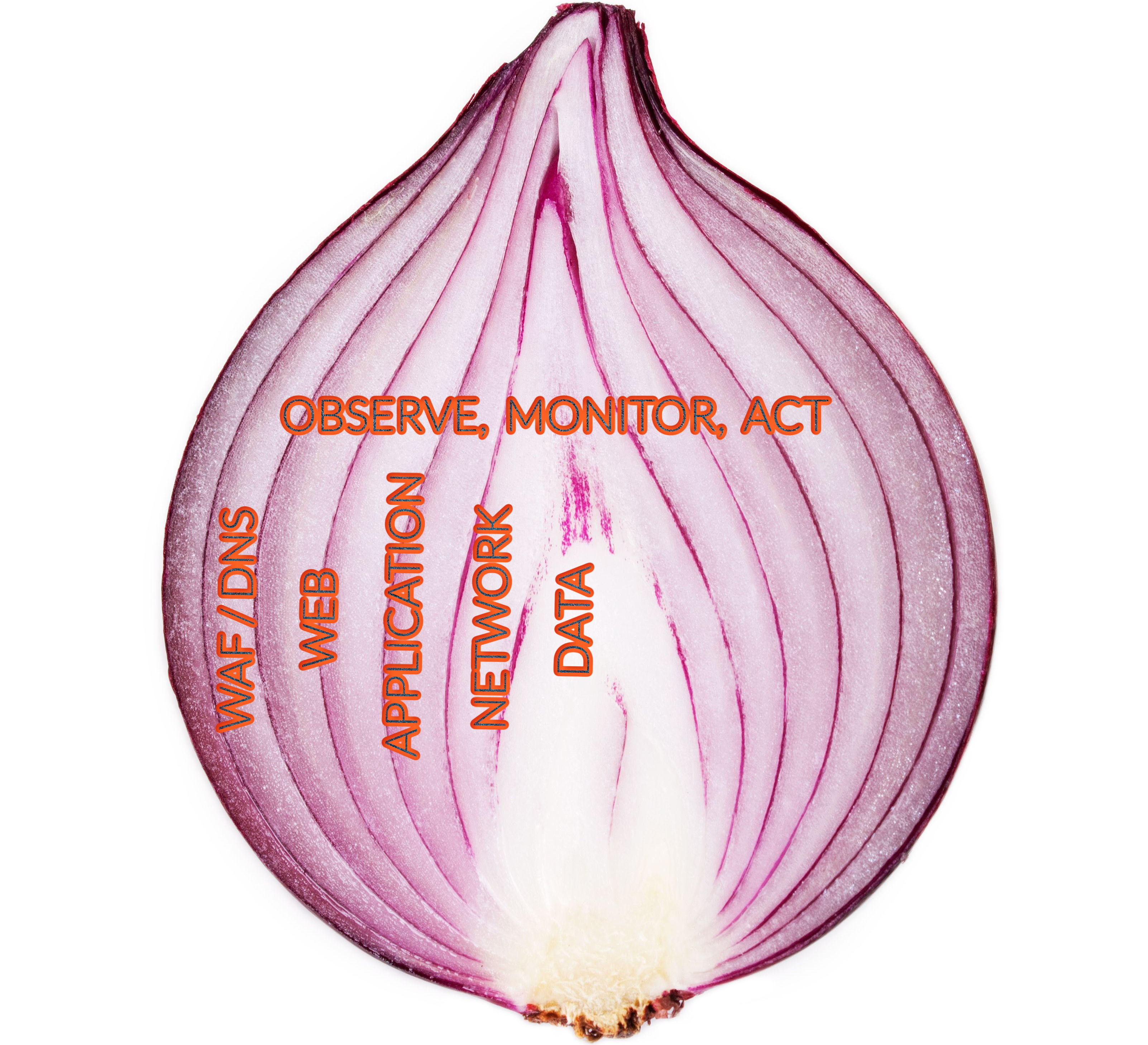
This blog is a continuation of the Security-Layers of Onion part-1 blog. This post will focus on Networking and Observability as security paradigms. Both are essential defense layers, as mentioned in the diagram below.
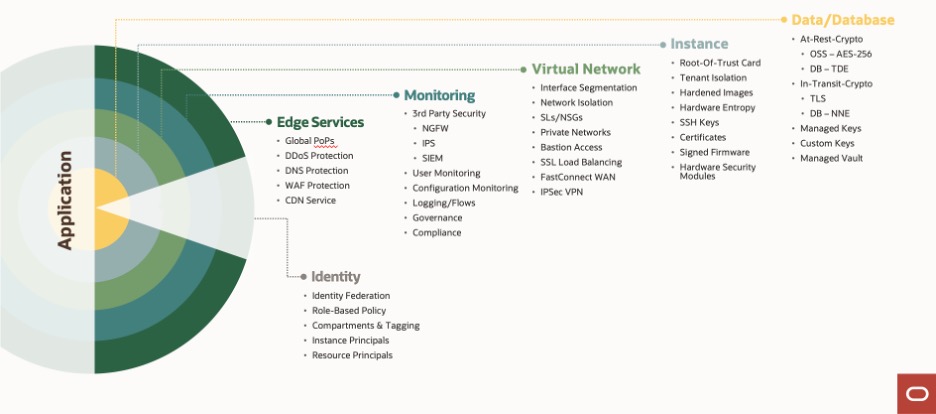
Network Security
Networking plays a fundamental role in ensuring cloud security by establishing a secure and reliable communication infrastructure between various components of the cloud environment. Networking in cloud security encompasses several important aspects that contribute to protecting data and resources. Here are some key roles of networking in cloud security:
- Segmentation and Isolation: Networking enables the segmentation and isolation of different components within the cloud environment. Organizations can create logical boundaries and control traffic flow between segments using virtual cloud networks, subnets, and network security groups. That prevents unauthorized access and limits the potential impact of security breaches.
- Secure Connectivity: Networking facilitates secure connectivity between on-premises infrastructure and cloud resources. Virtual private networks (VPNs), dedicated connections, or direct interconnections provide encrypted tunnels for data transmission, ensuring the confidentiality and integrity of data moving between the cloud and the organization’s network.
- Network Monitoring and Logging: Effective network security requires continuous monitoring and logging of network traffic within the cloud environment. That includes analyzing network flows, detecting anomalies, and identifying potential security incidents. Organizations can promptly detect and respond to security threats by leveraging network monitoring tools and techniques, minimizing the risk of data breaches or unauthorized access.
- Intrusion Detection and Prevention: Networking infrastructure incorporates intrusion detection and prevention systems (IDPS) that help identify and mitigate potential network attacks. IDPS solutions monitor network traffic, detect malicious activities, and enforce security policies to prevent unauthorized access, malware infiltration, or other malicious activities within the cloud environment.
- Load Balancing and Resilience: Networking is vital in distributing network traffic across multiple servers or instances in the cloud environment. Load balancing ensures that resources are efficiently utilized, enhances availability, and prevents single points of failure. Additionally, networking technologies like redundant network paths and failover mechanisms contribute to cloud services’ resilience and high availability.
By implementing robust networking practices and security controls, organizations can establish a strong foundation for protecting their cloud infrastructure, applications, and sensitive data from unauthorized access, attacks, and other security risks.
Observability and Management
The Observability and Management platform allows organizations to monitor, analyze, and understand the activities and events occurring within the cloud infrastructure and applications. Here are some critical functions of observability in cloud security:
- Threat Detection and Incident Response: Observability tools and techniques enable organizations to promptly detect and respond to security threats. By monitoring system logs, network traffic, and application behavior, observability helps identify suspicious activities, unauthorized access attempts, and potential security breaches. It facilitates real-time alerting, enabling security teams to rapidly investigate and respond to incidents.
- Vulnerability Assessment and Patch Management: Observability allows organizations to assess the vulnerabilities present in their cloud infrastructure and applications. It helps identify outdated software, misconfigurations, and other weaknesses attackers can exploit.
- Performance Optimization: Monitoring system performance helps optimize cloud resource usage by monitoring the performance and resource utilization of the cloud infrastructure. It allows organizations to identify bottlenecks, optimize configurations, and allocate resources efficiently. By ensuring that the cloud environment operates optimally, observability reduces the risk of security vulnerabilities due to performance issues or resource exhaustion.
By leveraging observability tools and practices, organizations can proactively identify and mitigate security risks, enhance their security posture, and ensure the confidentiality, integrity, and availability of their cloud infrastructure and data.
OCI has a robust platform of services fully managed and integrated to ensure security of workload in the cloud.

Implementing layers of security in the cloud is essential due to cybersecurity threats’ dynamic and evolving nature. Organizations can create a robust defense mechanism by utilizing multiple security measures at different levels, such as network, application, and data layers. This multi-layered approach reduces the likelihood of successful attacks, mitigates the impact of security breaches, and provides a comprehensive security posture. Each layer complements and reinforces the others, enhancing the overall resilience and protection of cloud environments, ensuring data confidentiality, integrity, and availability, and instilling confidence among users and stakeholders.
