As we know tenancy administrators (Administrators group) have extensive access to resources, configurations, and sensitive data across the entire tenancy. Tenancy administrators in Oracle Cloud Infrastructure (OCI) hold significant privileges and have the highest level of access within an OCI tenancy. Therefore, it is crucial to implement security best practices to minimize potential risks. One of these practices is to avoid using API keys for tenancy administrators. Compromise of an API key associated with a tenancy administrator can lead to catastrophic security breaches, including unauthorized access, data exfiltration, and destruction of resources.
OCI cloud guard has a recipe, which would let us know when user has API keys associated. Oracle documentation clearly states Compliance Standards Reference for this check for Administrators
- PCI-DSS 3.2.1: 8.6 – Where other authentication mechanisms are used, such as physical or logical security tokens, smart cards, or certificates, use of these mechanisms must be assigned as follows:
- Authentication mechanisms must be assigned to an individual account and not shared among multiple accounts.
- Physical or logical controls, or both, must be in place to ensure that only the intended account can use that mechanism to gain access.
- CIS 1.1: 1.11 – Ensure that API keys are not created for tenancy administrator users.
- CIS 1.0: 1.13 – Ensure that API keys are not created for tenancy administrator users.
How are API Keys Used:
API keys are used by developers, services and scripts for accessing OCI APIs directly or via SDKs/OCI CLI to search, create, update or delete OCI resources. The API key is an RSA key pair. The private key is used for signing the API requests and the public key is associated with a local or synchronized user’s profile.
Now coming to the requirement, how do we make sure that the current list of Tenancy Administrators don’t have API keys associated with them? We can enable cloud guard and check the results. Other than that, then there is no simple way of listing all the Tenancy Administrators with API keys. Here is a simple sample script, which would list all the Administrators that have API Keys associated with them:
import oci
import json
from oci.identity import IdentityClient
from oci.exceptions import ServiceError
import logging
config = oci.config.from_file("/Users/dmariche/Documents/ListDomainUsers/config")
#domain_url = input("Please enter your the domain URL: ") #pass the domain url in the format: https://idcs-xxxxxxxxxxxx.identity.oraclecloud.com
domain_url='https://idcs-xxxxxxx.identity.oraclecloud.com:443' #OCI Domain URL
identity_domains_client = oci.identity_domains.IdentityDomainsClient(config,domain_url)
identity_client = oci.identity.IdentityClient(config)
users_list = [] # Initialize a list to hold user details
compartment_id=config['tenancy'] # Compartment ID, we are passing the tenancy ID from the config file.
def list_AAPIusers_in_domain():
try:
list_users_response = identity_domains_client.list_users ()
while True:
users_list.extend(list_users_response.data.resources)
if list_users_response.has_next_page:
list_users_response = identity_domains_client.list_users(page=list_users_response.next_page)
else:
break
print("Tenancy Administrators with API Keys List in this domain:") # Print formatted user details API Keys
for user in users_list:
user_id = user.ocid
list_user_group_memberships_response = identity_client.list_user_group_memberships(compartment_id=compartment_id,user_id=user_id)
group_memberships = list_user_group_memberships_response.data
for membership in group_memberships:
group = identity_client.get_group(membership.group_id).data
if group.name == "Administrators" and user.urn_ietf_params_scim_schemas_oracle_idcs_extension_capabilities_user.can_use_api_keys == True: # Check if the user is part of the Administrators Group and if the user has API Keys
print(f"{'User Name':<20} {user.user_name:<40} ")
except ServiceError as error:
print(f"Error getting users: {error}")
return [] # Return empty list on error
list_AAPIusers_in_domain()
Note: We are using the default domain URL as input, and the config file is employed for authentication purposes. This script is a sample focused on identifying Tenancy administrators with API keys. You can easily extend this script to list all users who possess API keys, without needing to include group information. Feel free to adjust the script to meet your specific requirements.
Here is the sample output of the script:
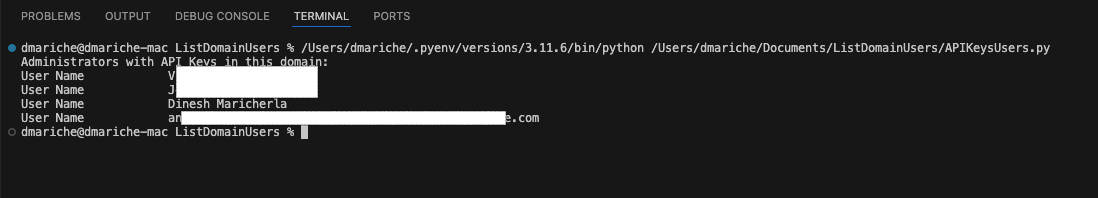
Using this script, we can effectively audit our tenancy administrators and implement necessary remediations. The script provided here offers a practical solution for the preliminary assessment and cleanup of the administrator user priveleges. After this initial step, we can enhance our approach by utilizing the functional methods described in this blog to streamline and optimize ongoing management. As explained earlier, API keys provide a straightforward way to authenticate API requests, but they pose significant security and operational risks, especially for tenancy administrators with broad and powerful permissions. Given the high-level privileges and the potential risks associated avoiding the use of API keys is a critical security measure. Administrators should log in using OCI Console access and enforce Multi-Factor Authentication (MFA) for an additional layer of security. They should adhere to the principle of least privilege and implement robust auditing and monitoring practices. By following these best practices, organizations can significantly enhance the security of their OCI environments and protect against unauthorized access and potential breaches.
