This Blog has been updated to reflect that all OIC instances now use OCI IAM Identity domains as the identity provider. References to the older service IDCS have been removed to avoid confusion (Nov 2025)
Introduction
In this blog we will see the scenarios under which we receive HTTP 429 errors with Oracle Integration and what is required to resolve the errors.
HTTP Response code 429 from Oracle Documentation –
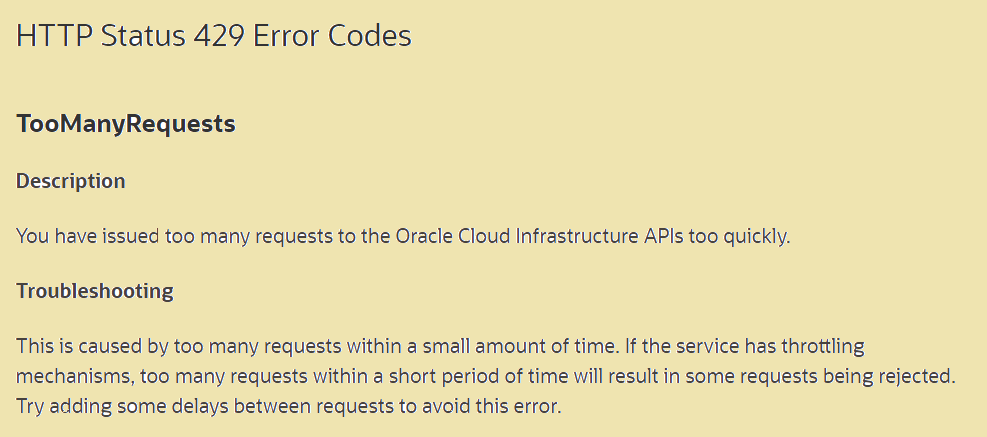
HTTP 429 Too many requests – Indicates that the user has sent too many requests in a given amount of time (rate limiting)
The rate of incoming requests has exceeded the threshold of rate limit for the server and the server is unable to process the concurrent requests.
It is recommended that clients implement request retries using exponential backoff periods to handle such HTTP 429 responses.
In an Oracle Integration context, let us look at the various scenarios that may encounter HTTP 429 errors.
Inbound into OIC
When you are invoking OIC integration endpoints from a client and you encounter a HTTP 429 “Too Many requests” error, it means that the rate of requests has exceeded either of the following thresholds
1. Identity Domain rate limit for authentication requests
2. OIC3 Service limits
Identity Domain rate limit for authentication requests
OIC instance use OCI IAM Identity Domains as an Identity provider, OIC validates the credentials/access tokens in the request against identity domain.
The 429 error arises due to the pre-set identity domain rate limit being breached by the rate of incoming requests.
IAM Identity domain rate limits for the different domain types are published in below link
https://docs.oracle.com/en-us/iaas/Content/Identity/sku/overview.htm#api-rate-limits
Possible Actions to resolve –
Upgrade the identity domain instance to a suitable type based on the expected concurrent request rate to be supported.
For example, upgrade from Identity Domain Free Type to Premium type to enhance this rate limit for authebntication requests
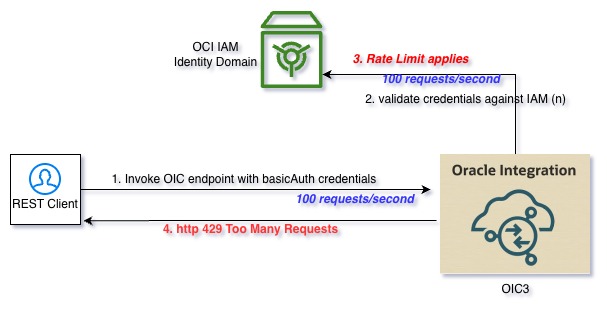
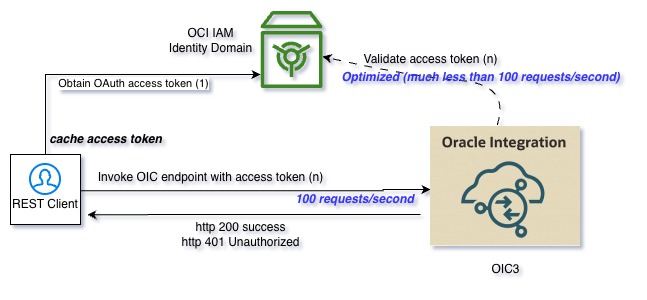
Also it is important to understand that if the requests to OIC use basicAuth scheme for authentication, potentially every incoming request will be authenticated against identity domain making it much more probable to exceed the rate limits. Ensure that the Integration endpoints use OAuth authentication and cache the access token at the client side while invoking OIC REST endpoints. OAuth Access token validations by OIC against identuty domain are highly optimized and efficient, reducing the possibilities of exceeding the rate limits.
Refer to diagrams below which show the authentication flows in case of BasicAuth and OAuth
OIC3 Service limits
The relevant service limits are –
- Concurrency – The maximum number of concurrent synchronous requests into OIC3 instance
- Tenant and user requests – Maximum allowed requests per second per user and also at tenant level
At the time of writing this blog, the limits are 100 concurrent synchronous requests per message pack with a maximum of 2000 concurrent requests.
Find the latest OIC3 service limits documented here – https://docs.oracle.com/en/cloud/paas/application-integration/oracle-integration-oci/service-limits.html
When this service limit is breached the incoming requests fail with HTTP 429 error.
It is recommeded that the clients invoking OIC endpoints implement a retry strategy using exponential backoff periods to handle HTTP 429 errors.
Outbound from OIC
For Outbound requests to external systems,
If you encounter HTTP 429 errors while invoking REST endpoints with the REST Adapter, ensure that you employ instance retries.
Refer here to understand how automatic retries can be designed easily during design time
https://docs.oracle.com/en/cloud/paas/application-integration/integrations-user/retry-invoke-connections-project.html
References
- Migration from older IDCS to the newer OCI IAM Identity Domains. What has chaged?
- OIC3 REST adapter Best practices – documentation
- Retry outbound invokes – Add Retry Logic to Invoke Connections in Project
- OIC3 Service Limits
- Identity Domain Rate Limits
