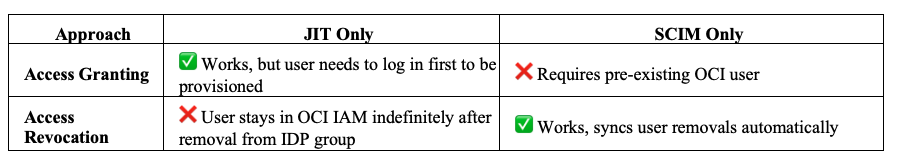
Traditionally, when integrating an Identity Provider (IDP) with Oracle Cloud Infrastructure (OCI), SCIM provisioning is used to synchronize user and group information from the Enterprise IDP. This method of access management typically assigns users to IAM groups with predefined permissions. However, in dynamic cloud environments, static group assignments may not be sufficient.
Imagine a scenario where a developer requires temporary administrator privileges in OCI for a specific deployment. Instead of manually granting and revoking access, you can leverage your IDP (e.g., Okta, Entra ID) to automate the provisioning process.
By combining Just-in-Time (JIT) provisioning, SCIM, and your existing IDP, you can create a dynamic, time-bound access model that enhances security and operational efficiency.
Key Components of This Approach
- Just-in-Time (JIT) Provisioning – Grants access to OCI resources only when requested and for a limited duration.
- SCIM (System for Cross-domain Identity Management) – Automates user and group provisioning/deprovisioning across systems, ensuring consistency while reducing manual intervention.
- Identity Provider (IDP) – Acts as the single source of truth for user identities and authentication, streamlining access management.
Why do we need JIT and SCIM provisioning for this solution?
- JIT Handles User Creation & Access Granting
- As soon as a developer is added to
OCI-Temp-Adminsin the IDP, they can log in, and JIT provisions the users on the spot into OCI with the appropriate group assignment. - Without JIT, we would have to pre-create users in OCI manually, increasing administrative overhead.
- SCIM Handles Group Synchronization & Access Revocation
- If a developer’s temporary elevated privilege expires (e.g., after 2 hours), SCIM removes them from the
OCI-Temp-Adminsgroup in OCI based on the IDP update. - This ensures that even if the user is still signed into OCI, they lose their elevated privileges automatically when SCIM syncs.
- Without SCIM, the admin would have to manually remove the user from the OCI group, increasing the risk of privilege persistence.
Why Just JIT or Just SCIM Alone Wouldn’t Work
Workflow: Automating Temporary Access to OCI
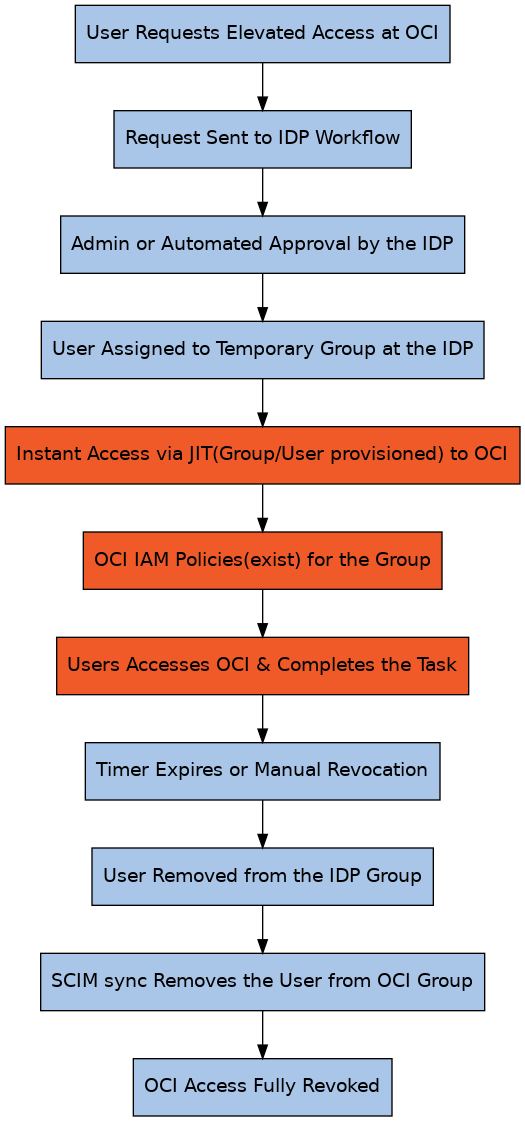
Step 1: User Requests Elevated Access
A developer or support engineer needs temporary administrative privileges in OCI. They initiate an access request through a custom application integrated with your IDP.
Step 2: Approval Process
The access request is reviewed and approved through one of the following methods:
- Manual Approval: An administrator manually adds the user to the OCI-Temp-Admins group in the IDP.
- Automated Workflow: A pre-defined workflow approves the request, assigns the user to the OCI-Temp-Admins group in the IDP, and sets a time limit (e.g., 1 hour, 2 hours) for access. Once the timer expires, the user is automatically removed from the group.
Step 3: JIT Provisioning in OCI
The OCI-Temp-Admins group is configured with JIT provisioning in OCI. When the user is added to this group in the IDP, they are instantly provisioned into the corresponding IAM group in OCI. JIT ensures that users are created in OCI dynamically when they log in.
Step 4: Assigning Temporary Privileges via OCI Policies
In OCI, an IAM policy grants necessary permissions to the OCI-Temp-Admins group. Example policy:
Allow group OCI-Temp-Admins to manage all-resources in compartment Temp
This ensures that this group has privilege to manage all resources on this compartment at OCI.
Step 5: Developer Performs Tasks
The developer or support engineer now has the required privileges and can execute the necessary tasks within OCI.
Step 6: Access Removal Process
Once the task is completed, the user’s access is revoked through one of the following approaches:
- Manual Removal: The developer or support engineer informs the administrator to remove the user account from the OCI-Temp-Admins group in the IDP.
- Automated Expiry: The workflow detects that the allotted time has expired and automatically removes the user from the IDP group.
Step 7: SCIM-Based Group Membership Revocation
Since the OCI-Temp-Admins group is also configured with SCIM provisioning to OCI, once the user is removed from the IDP, SCIM ensures that the user is also removed from the corresponding OCI group.
- For IDPs like Entra ID, SCIM runs on a schedule (e.g., every 40 minutes) and removes the user from the OCI group accordingly.
- This process ensures that temporary privileges are automatically revoked without manual intervention.
SCIM ensures that user group memberships are continuously synchronized between the IDP and OCI.
Benefits of This Approach
By combining JIT and SCIM, we create a fully automated lifecycle for temporary privileged access, ensuring both timely access granting and timely access revocation without manual intervention.
- Enhanced Security: Limits access by granting privileges only when needed, reducing the attack surface.
- Reduced Administrative Overhead: Automates user provisioning and deprovisioning, minimizing manual tasks.
- Improved Compliance: Enforces the principle of least privilege, aligning with security best practices.
- Streamlined User Experience: Provides a seamless access request process via your existing IDP.
- Centralized Access Control: Manages OCI access through a trusted enterprise identity provider.
Conclusion
Implementing JIT provisioning with SCIM in OCI is a game-changer for temporary privilege management. By automating access grants and revocations, organizations can strengthen security, optimize operations, and ensure compliance.
Taking the time to plan, test, and fine-tune this approach will result in a more secure, efficient, and scalable cloud access management model. Let your IDP handle identity, while OCI enforces secure access—the best of both worlds!
