Introduction
This blog post is a continuation of a previous blog which explains the DNS options for this service.
In this blog we will configure the DNS resolution of the Oracle Database at AWS (OD@AWS) service:
- from AWS to the service (client to service). The clients in AWS will leverage Route53 Outbound Endpoint to resolve the OD@AWS DNS domain;
- from the service to the AWS (service to client). The EXAdb-D will leverage the OCI DNS forwarding endpoint to resolve a hosted zone in AWS Route53;
During this blog i will use an EXAdb-D VM cluster provisioned in an ODB Network configured with the default DNS domain. In the peered VPC i will provision an EC2 instance that will act as a bastion server to connect to the VM cluster. The provisioning of the: VPC, ODB Network, ODB Peering, VM cluster and the EC2 are beyond the scope of this blog.
Bellow is the diagram that we will use:
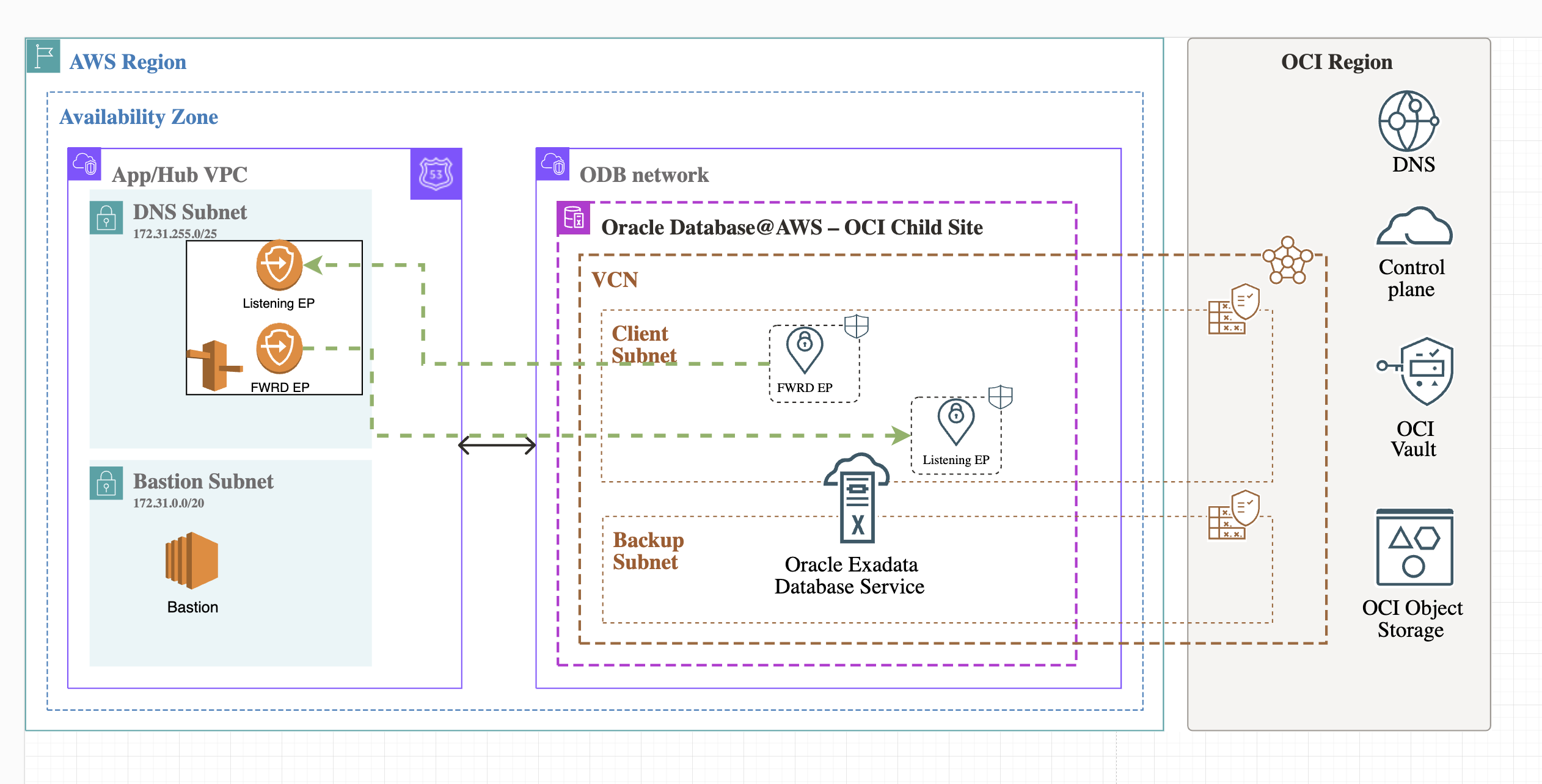
AWS Configuration
For this blog i will use the default domain in OD@AWS (oraclevcn.com) and a private hosted zone (oci.ateam-oracle.cloud) in Route53.
In order to resolve the oraclevcn.com or the custom domain name of the OD@AWS service from an EC2 instance in AWS, we need to configure an outbound DNS endpoint in Route53 and create a resolver rule to forward the DNS queries to the OCI DNS listener endpoint as described in the AWS documentation. You can read more about the AWS DNS resolution here.
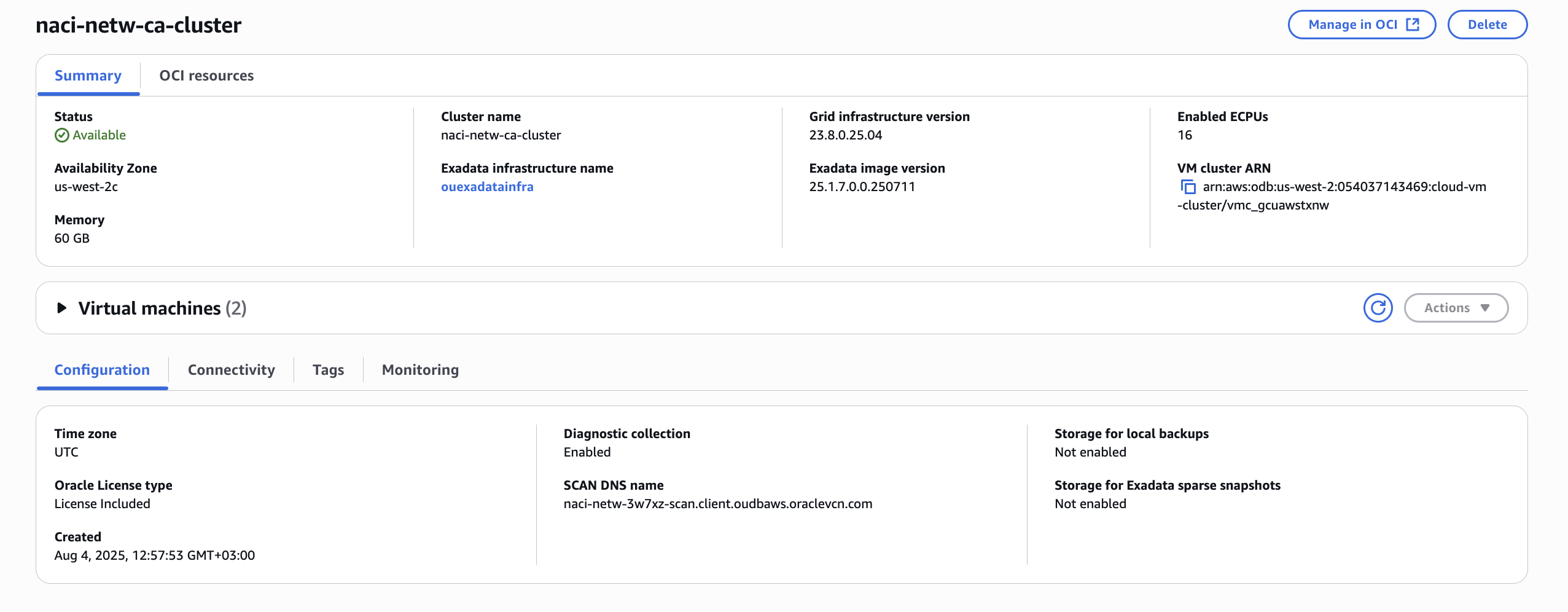
The ODB Network has the following details. Please notice the default DNS domain configured (client.oudbaws.oraclevcn.com) and the IP address of the OCI DNS listener endpoint (10.10.0.94).
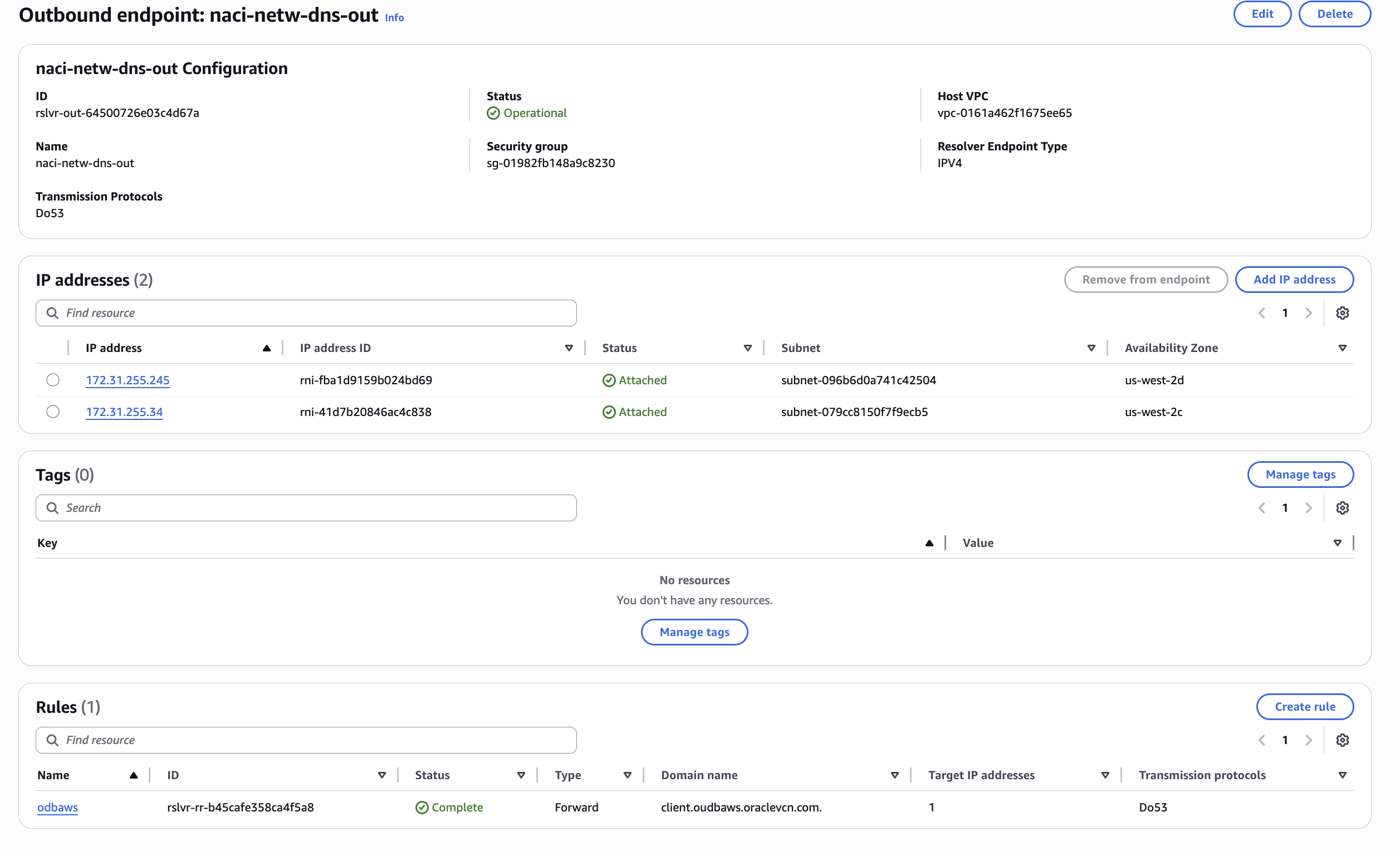
On the AWS side i configured:
- an Outbound endpoint (forwarder) with a rule to forward the requests for the client.oudbaws.oraclevcn.com domain to the DNS listener IP address in the ODB Network (10.10.0.94);
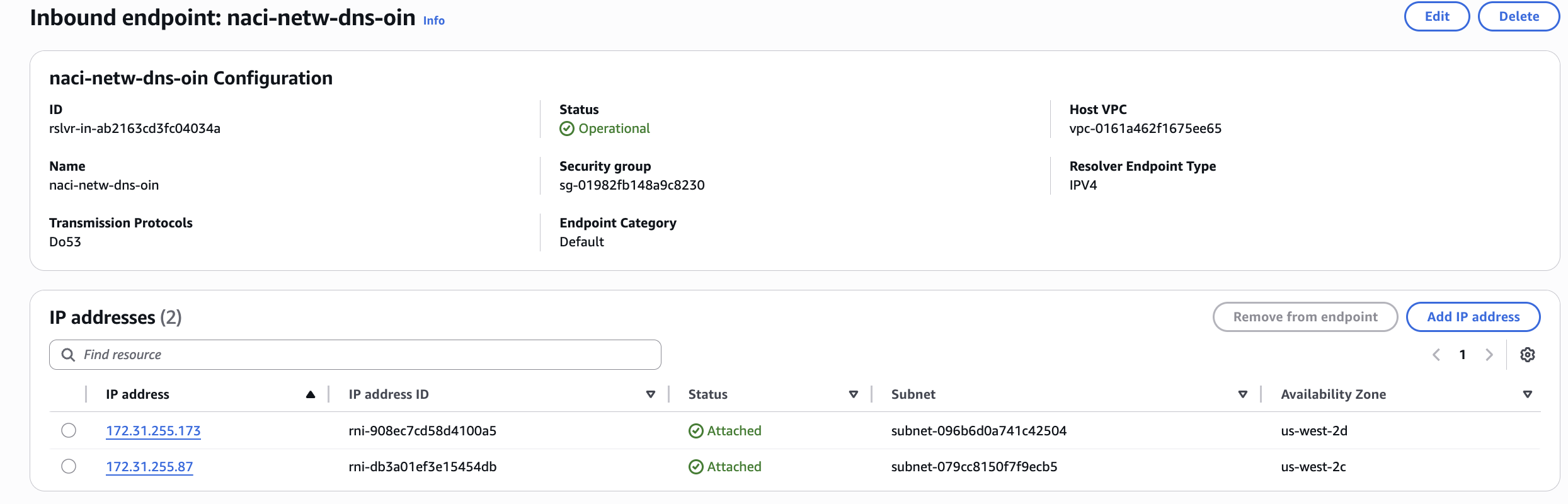
- an Inbound endpoint (listener);
- a hosted private DNS zone with a test record.
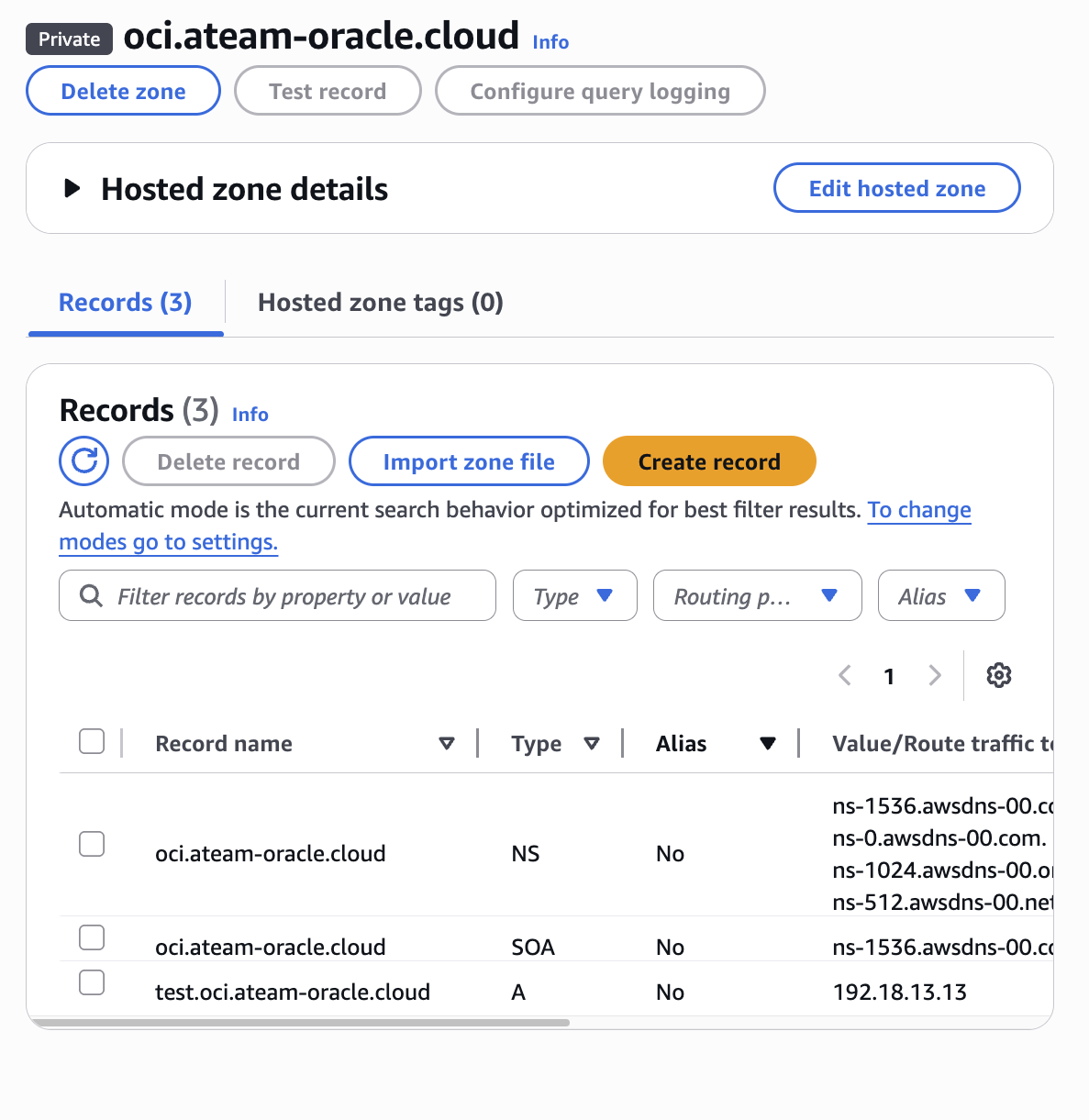
Client to Service DNS resolution configuration
When the service is provisioned a DNS listener endpoint is configured in OCI with all the required configurations to be able to resolve from the peered VPC to the OD@AWS DNS domains.
In AWS i will configure the forwarding rule that will point to the listener IP address from OCI.
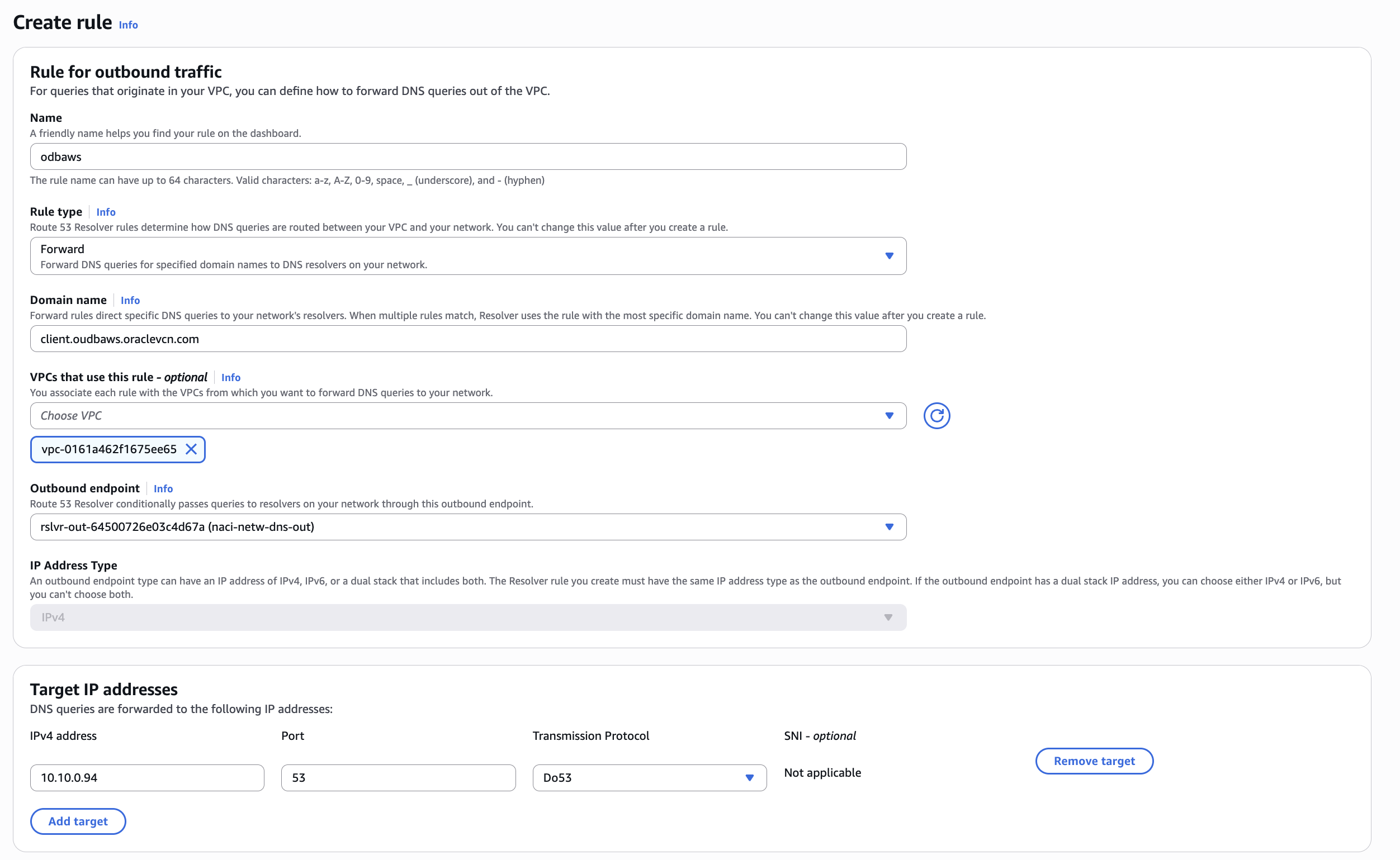
I will test this resolution using the SCAN and the dbServer-2 FQDNs:
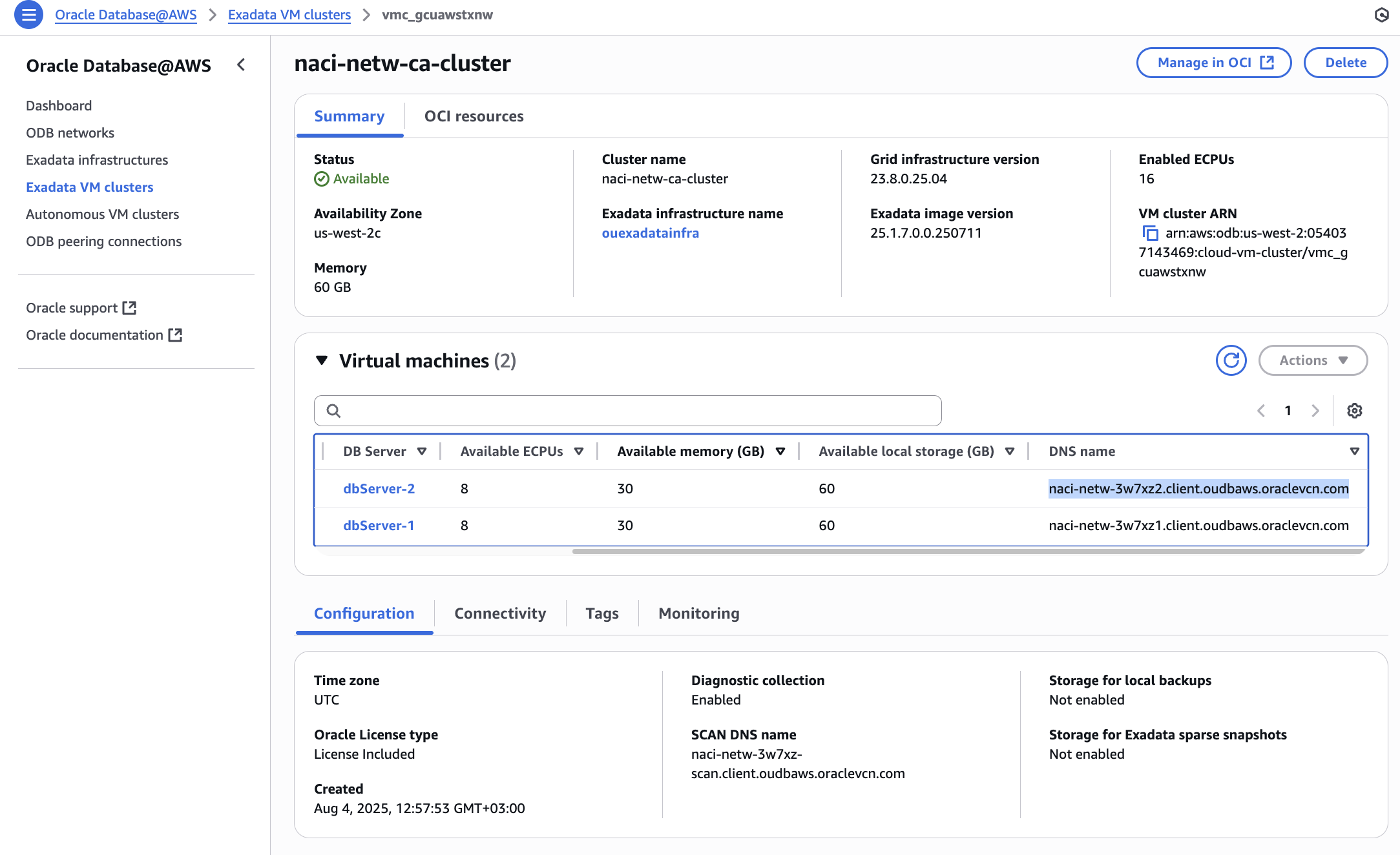
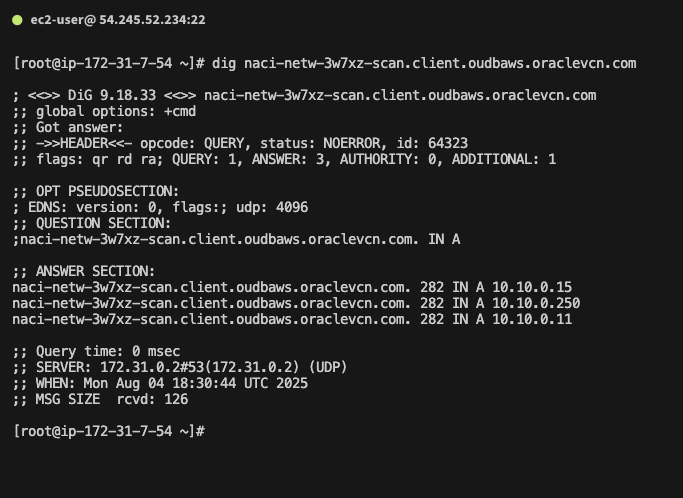
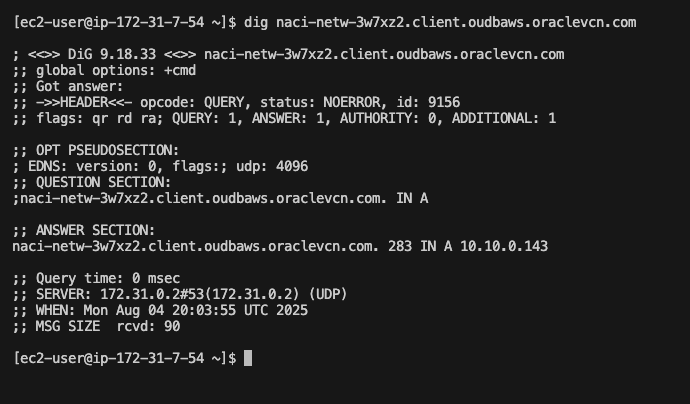
I successfully resolved the OD@AWS DNS records from an EC2 VM in AWS.
Service to Client DNS resolution configuration
When the service is provisioned, a forwarder DNS endpoint is created without an Network Security Group (NSG) attached to it and with no forwarding rule configured.
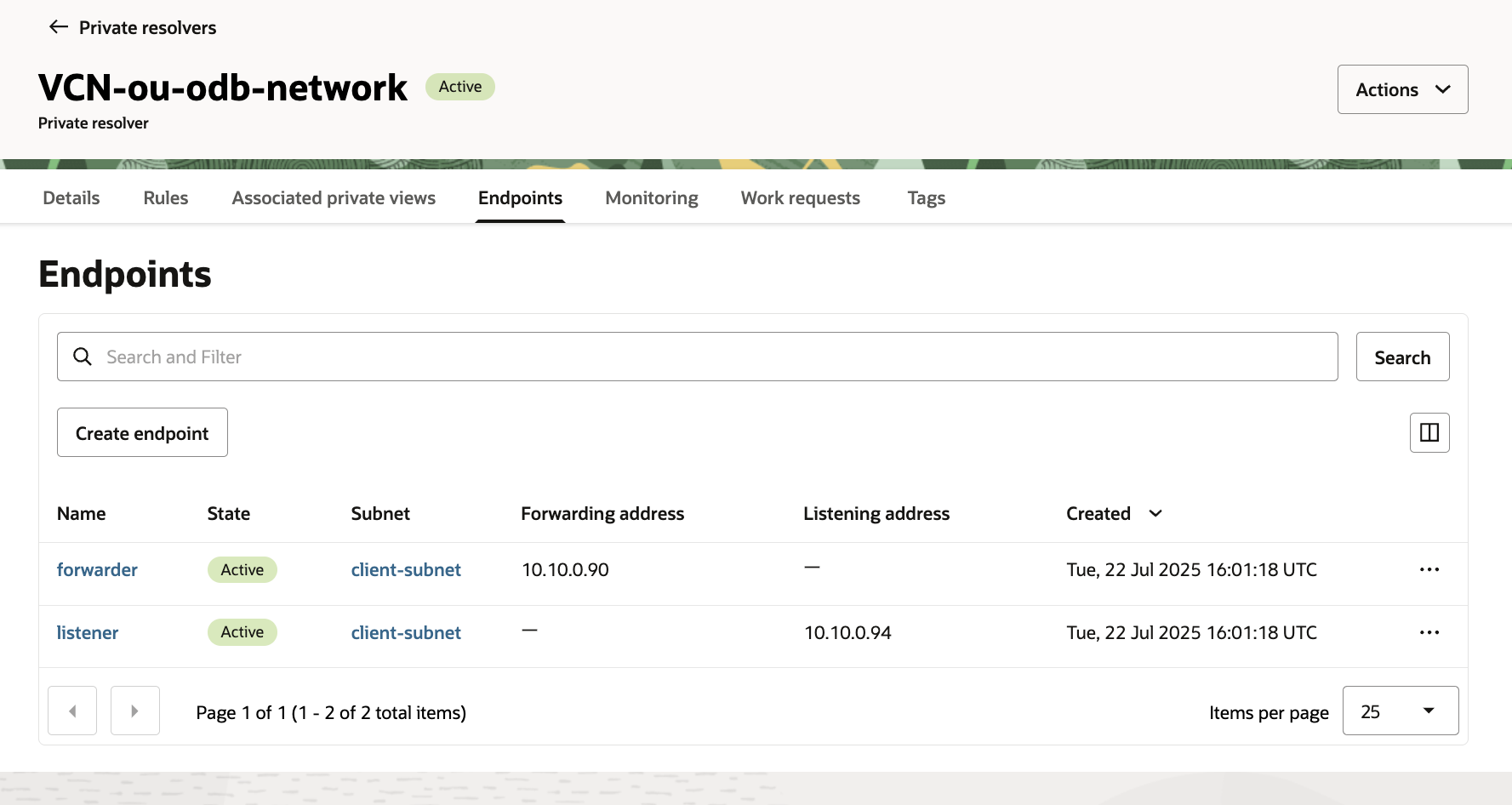
I will configure the following:
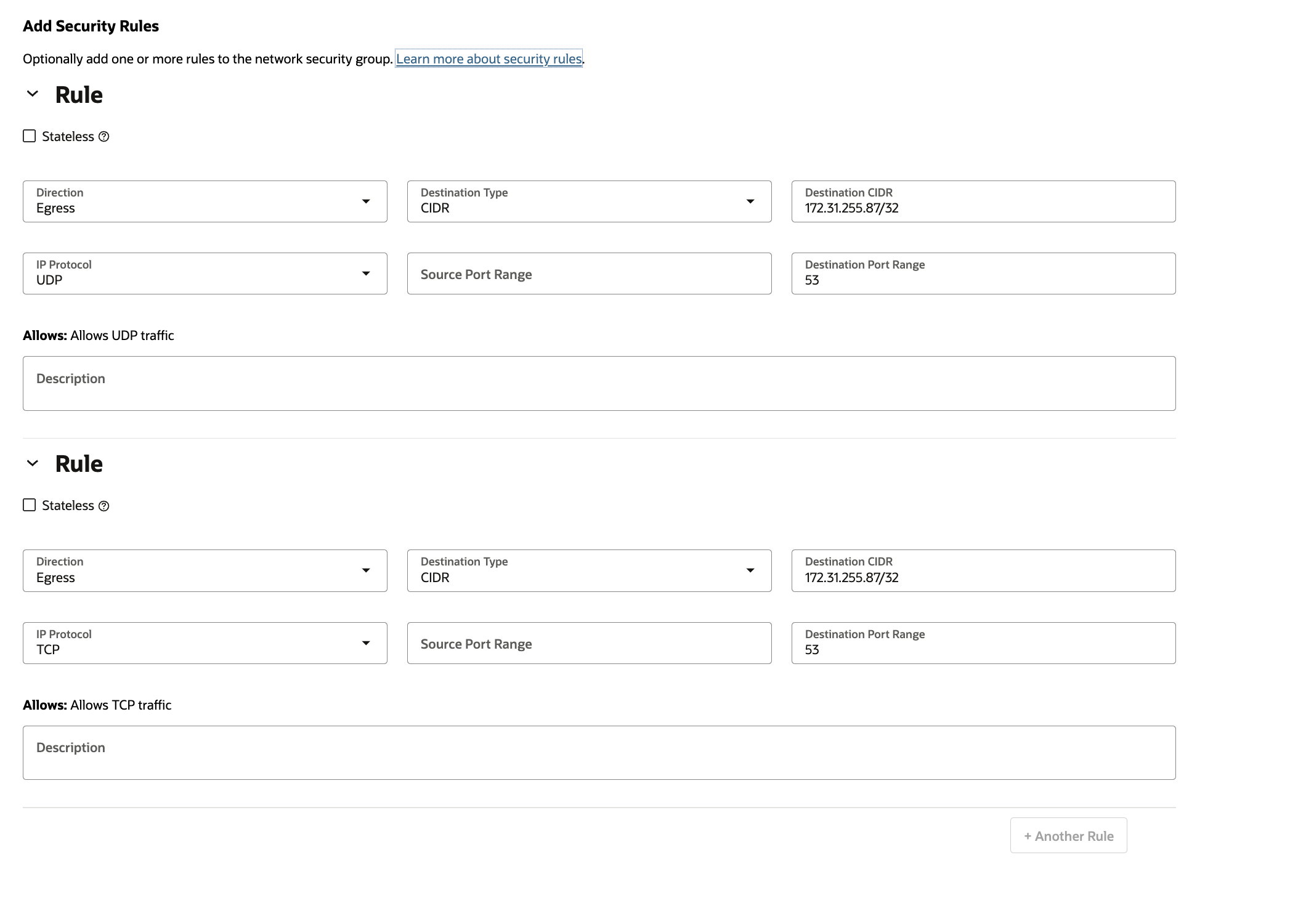
- an NSG that will allow connectivity from the OCI DNS forwarding endpoint to the Route53 Inbound endpoint. This NSG will be attached to the OCI DNS dorwarding endpoint.
- a Forwarding rule for the hosted DNS zone configured in Route53
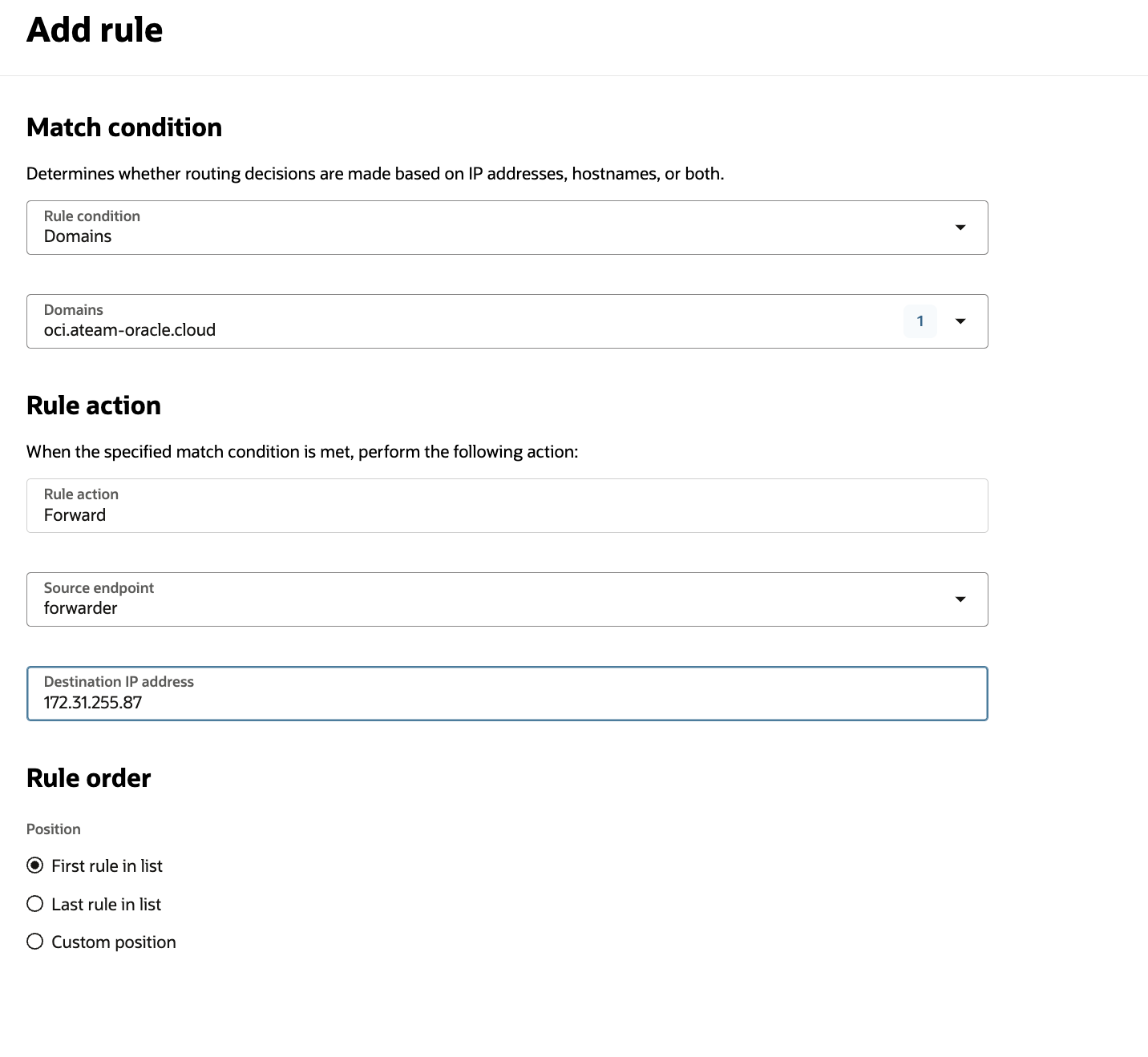
Please note that in AWS when configuring the Inbound endpoint it is mandatory to create two endpoints for High availability reasons. In OCI, the forwarding rules can have only IP address in the “Destination IP address” field. In the blog i have used the endpoint created in the same AZ as the ODB Network.
I will connect from the EC2 bastion VM to one VM from the EXAdb-D VM Cluster and resolve the DNS zone hosted in AWS:
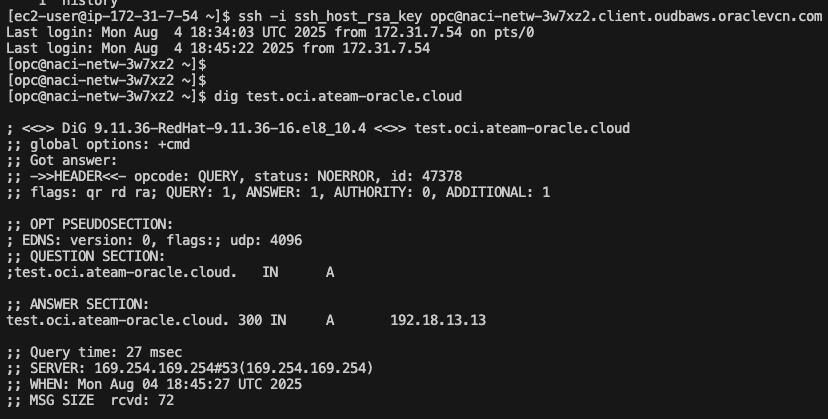
I resolved the hosted DNS zone in AWS from the VM in the OD@AWS EXAdb-D.
Conclusion
This blog showed the step by step configurations on both OCI and AWS for the DNS resolution.
