Introduction
OCI Audit is an OCI service that automatically records calls to all supported OCI APIs as OCI events. OCI Audit offers the following benefits:
- All audit data with multiple identity domains is available in one central place
- Provides a single source of truth for all actions in your cloud
- Tracking who did what, when, and from where
- Data can be pushed to external systems such as SIEMs
- OCI Audit stores event data for a year
In Oracle Cloud Infrastructure (OCI), there is standard system managed (Provided out-of-the-box by OCI) default log group – _Audit where all audit service log entries are automatically stored, it captures all audit events (e.g., API calls, CLI commands, Console actions, OCI resources, service activities, User Actions ) for whole tenancy.
This data can be extracted from _Audit log group for various governance, security monitoring , compliances (regulatory audits) & tracking user actions (login, MFA, password reset, provisioning changes) requirements, retention is 1 year, post that you can export to object storage.
In this blog we will explore methods & ways to fetch OCI Events using Standard – _Audit Log group into external systems like SIEM, below is decision tree when to use what scenario’s.
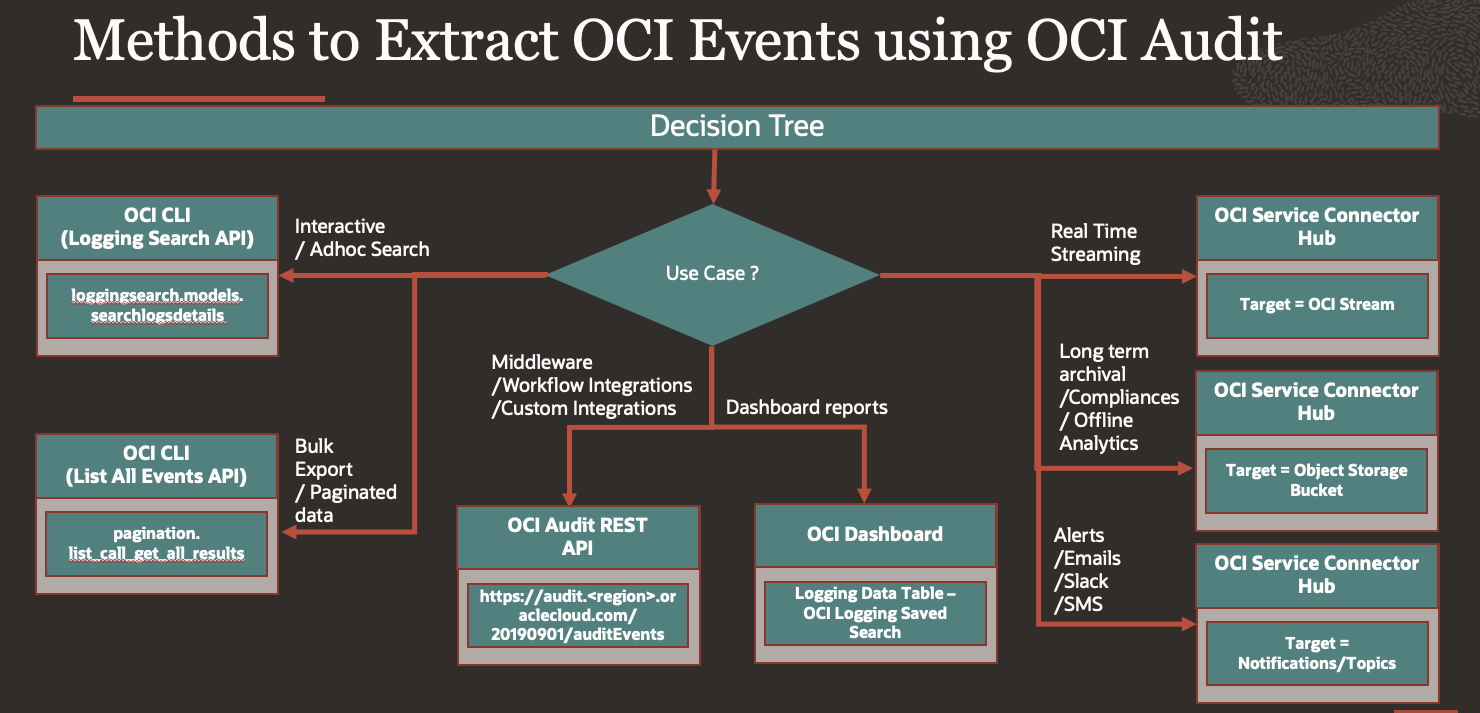
Each method serves different use cases based on performance, flexibility, integration, and scalability, we will discuss in detail.
Prerequisites
Following IAM Policies are required to enable Access to OCI Audit Logs & use OCI Logging features, you need to setup these policies accordingly to your OCI governance requirements.
- Enable Access to Log Analytics and Its resources
Policies to use Oracle Log Analytics - Viewing Audit Log Events
Polices to View audit events - Logging Search
Use the Logging Search page to search logs. - Connector Hub
Policies for Target Objects - Common IAM Polices
Eg – Access Object Storage
Details
OCI Audit provides multiple ways to access and analyze Audit logs & below are the key integration options available for extracting and processing audit data.
Connecting to OCI REST APIs using an SDK involves leveraging language-specific libraries provided by Oracle to interact with OCI services programmatically. This approach simplifies API calls by handling authentication, request signing, and response parsing.
You can refer below example to understand how it can be done – Manage Oracle Cloud Infrastructure REST APIs Programmatically using Shell and Java Code
OCI CLI commands wrapped inside scripts or Python code that run as serverless functions (OCI Functions). These functions can be triggered via API Gateway endpoints, enabling external systems to call them easily over REST APIs.
We will use Oracle Cloud Infrastructure SDK for Python
Below two methods can be used to fetch Audit logs –
-
- a – OCI Logging search API
Invoke oci.loggingsearch.models.SearchLogsDetails to perform log queries, as we search in OCI Logging UI Search.
- a – OCI Logging search API
Refer example – Export OCI Audit Logs in CSV format for a custom time range
You need to pass query statement as you can query in Logging UI along with start time & end time
Query variable contains – Compartment ID, User Principle, Events, Event Attributes etc., same way you query in Logging UI, this search provides more flexibility for adhoc searches.
| search_details = oci.loggingsearch.models.SearchLogsDetails( time_start=start_time, time_end=end_time, search_query=query, is_return_field_info=False ) |
Response variable will return JSON Payload response as per Audit REST API Schema.
-
- b – OCI Pagination API
Automatically fetches more data from the service until the no more records are available
Use oci.pagination.list_call_get_all_results to fetch complete results efficiently
Refer Sample Code using oci-python-sdk
- b – OCI Pagination API
You need to pass Compartment ID (tenancy ID), start time & end time & it will return all information till all pages are fetched recursively, this way you can export entire audit logs for provided time range.
| response = oci.pagination.list_call_get_all_results ( audit_client.list_events, compartment_id=compartment_id, start_time=start_time, end_time=end_time ) |
Response variable will return JSON Payload response as per Audit REST API Schema.
Service Connector in OCI Logging is used to stream log data from one OCI service (like Logging or Audit) to another destination (like Object Storage, Streaming, Functions, Topics, Monitoring, etc.)
We will use Standard Source – _Audit log group provided by OCI Audit.
We will cover below targets , you can refer for more scenarios
-
- a – Stream logs to Oracle Streaming for real-time processing or alerting.
Create Connector, Source as Log group – _Audit , Target as Stream
Filter on OCI Service Name & OCI Event Type which you want to capture.
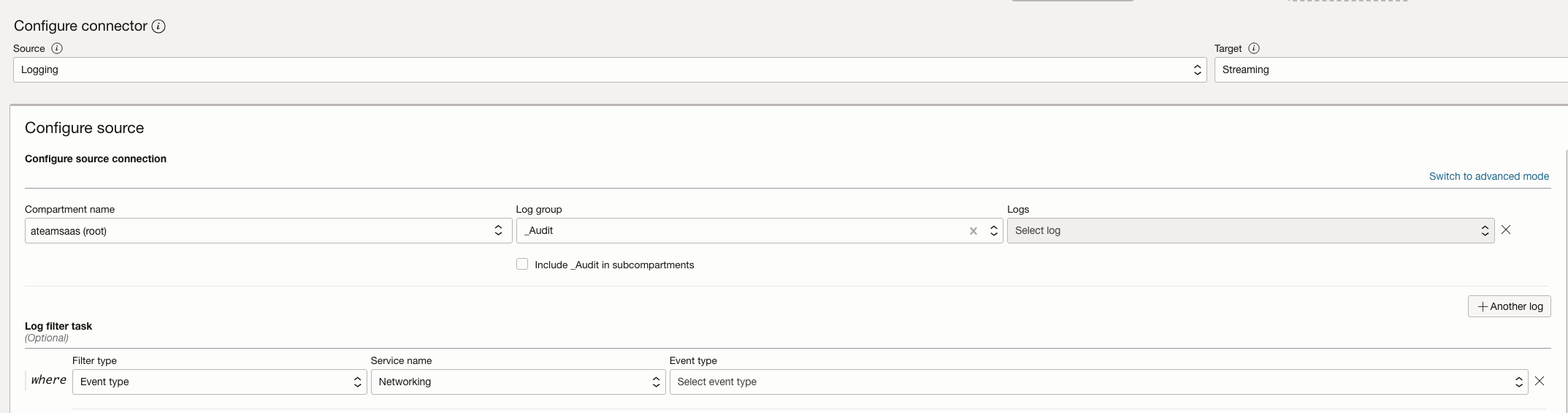
Define Oracle Stream & use that as Target

- a – Stream logs to Oracle Streaming for real-time processing or alerting.
-
- b- Export logs to Object Storage for long-term retention and analysis.
Create Connector, Source as Log group – _Audit , Target as Object Storage.
Filter on OCI Service Name & OCI Event Type which you want to capture.
- b- Export logs to Object Storage for long-term retention and analysis.
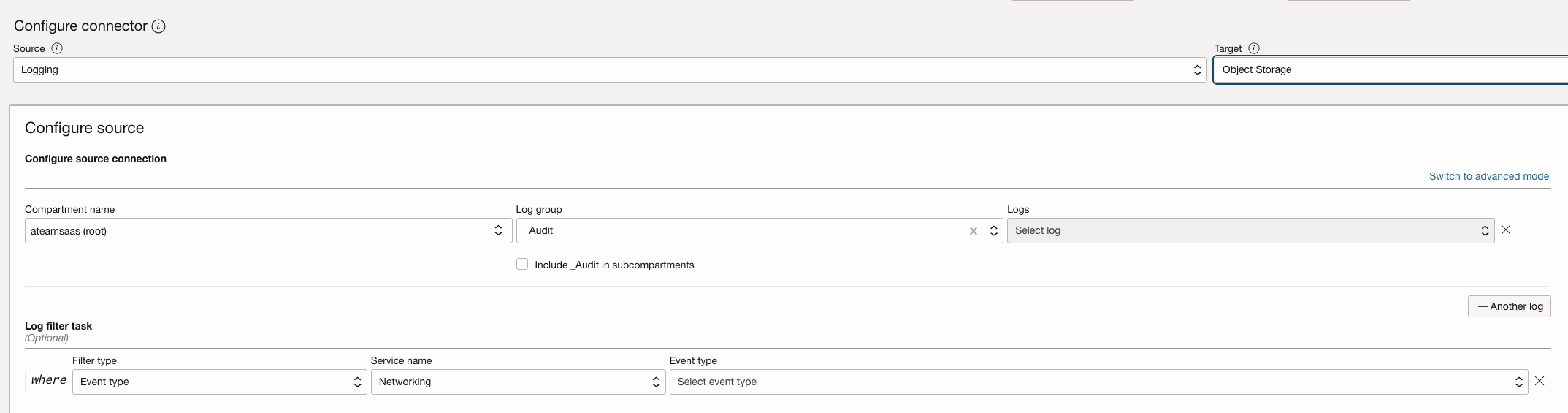
Define Object Storage Bucket & use that as Target
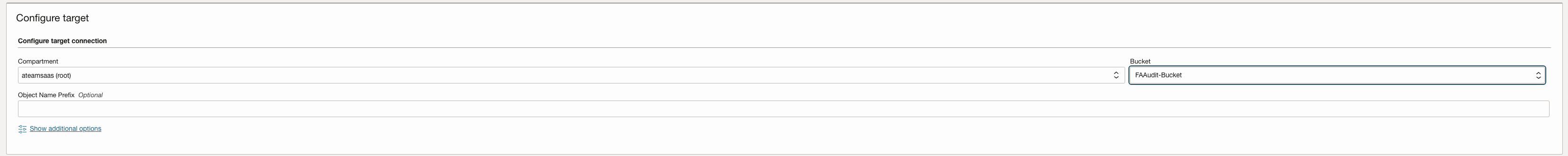
-
- c- Using Topics for Notifying external receipting using – Email, Slack, SMS
Create Connector, Source as Log group – _Audit , Target as Stream
Filter on OCI Service Name & OCI Event Type which you want to capture.
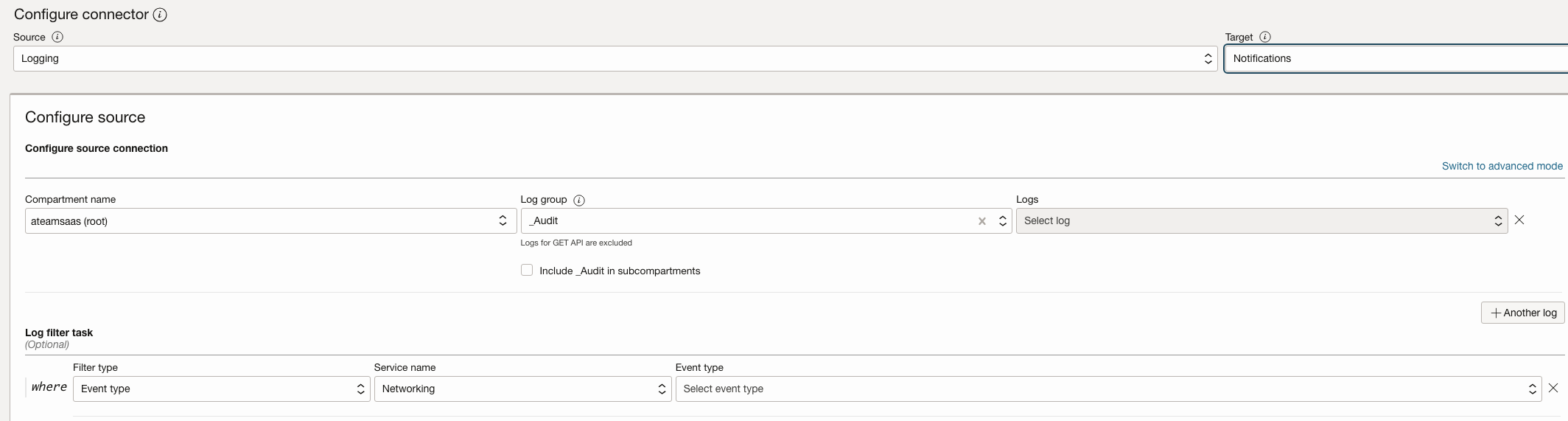
Define Topic & use that as Target
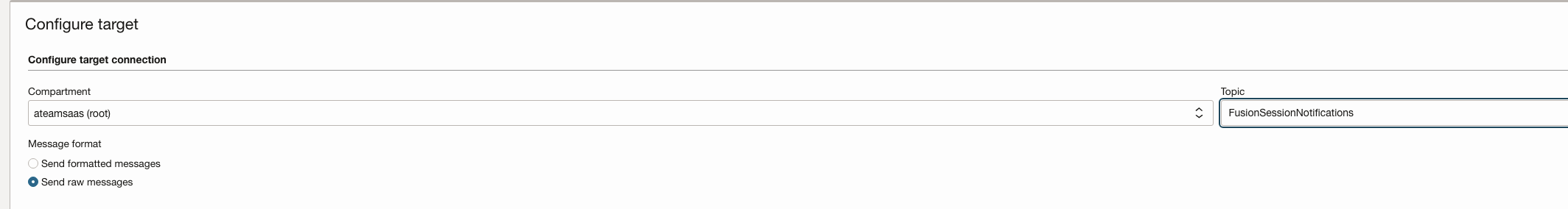
- c- Using Topics for Notifying external receipting using – Email, Slack, SMS
OCI Logging Saved Search – A predefined query in OCI Logging that filters and retrieves log data based on custom criteria for quick access and analysis
OCI Dashboard – A customizable visual interface in OCI that displays metrics, logs, and saved searches in a unified, interactive view for monitoring and insights
Create Saved Searches and build custom dashboards to visualize and monitor audit events interactively.
Refer this working example – Generate Identity and Access Management Reports from Oracle Cloud Infrastructure Audit
You can use OCI Audit API for the Audit Service. Use this API for compliance monitoring in your tenancy, these API are good for queries, but not bulk-export operations.
Since Oracle Cloud Infrastructure (OCI) REST APIs do not support Basic Authentication (username/password) — you must use OCI Signature-based authentication, Oracle Integration Cloud (OIC) Gen 3 and other OCI services enforce OCI Signature Version 1.
You need to setup OCI API keys for the user based on which REST APIs will connect to the OCI tenancy.
Use the REST Adapter with OCI Signature-based authentication to programmatically retrieve audit events into workflows or third-party tools.
Refer OCI Gen3 Connection Method – OCI Signature Version 1
Parameters used for /20190901/AuditEvent/ListEvents are limited to compartment ID, Start time & End time
Summary
Below is a comparison table explaining when to use what method and why.
1. OCI CLI (Logging Search API + Pagination)
| Method |
Use Case |
When to Use |
Why Use It |
|
|
Interactive search of logs using structured queries |
When you want real-time, ad-hoc, precise log filtering with conditions (event name, IP, etc.) |
Provides powerful querying using Logging Search Query Language |
|
|
Paginated retrieval of large search results |
When the query may return many rows over several pages |
Simplifies retrieving large result sets without manual pagination |
Ideal for: scripting, automation, monitoring user activities via specific event types (like AccessApp, ChangePassword).
Not ideal for: continuous real-time stream or dashboard visualization.
2. OCI Service Connector Hub
| Use Case |
When to Use |
Why Use It |
| Real-time processing and streaming of logs |
When you want to stream logs to Object Storage, Streaming, Functions, or Monitoring in near real-time |
Decouples the log ingestion from analysis; ideal for alerting, event-driven automation, or archival |
| Integration with external systems |
Stream logs to Kafka, SIEM, Splunk, or external consumers |
Enables event-driven microservices, external monitoring, or long-term storage |
Ideal for: Real-time processing, triggering workflows (e.g., send alert on login from suspicious IP).
Not ideal for: Ad-hoc exploration or historical queries.
3. OCI Logging UI (Saved Search + Dashboards)
| Use Case |
When to Use |
Why Use It |
| Visual reporting, audit dashboards, and saved searches |
For auditors, security teams, or non-technical users who want to explore login trends |
No-code, simple interface to build and share security reports |
| Scheduled log reports and analysis |
For daily login summaries, failed login, top users, IPs, etc. |
Persistent visual insights without needing scripting or API calls |
Ideal for: Visualization, executive reporting, compliance audit preparation.
Not ideal for: Real-time automation or fine-grained search conditions.
4. OCI Audit REST API (e.g., via OIC or middleware)
| Use Case |
When to Use |
Why Use It |
| When building integrations with OIC, Fusion SaaS, or other Oracle middleware |
Integrating audit data with workflows (e.g., provisioning, user deactivation) |
Native REST API with OCI Signature authentication, suitable for low-code platforms |
| Fetch audit events over HTTP |
Use within integration flows, alerts, custom connectors |
No CLI or SDK dependency, easier in enterprise middleware environments |
Ideal for: Integrations with SaaS or Fusion apps, policy enforcement, workflow automation.
Not ideal for: Bulk querying or large-scale log analysis.
Conclusion
Each method for accessing and analyzing OCI Audit logs offers distinct advantages based on use case, scalability, and integration needs:
- OCI CLI Methods
Useful for quick, scriptable access to logs during development or ad-hoc troubleshooting. SearchLogsDetails is ideal for targeted log queries, while list_call_get_all_results helps in retrieving paginated data efficiently.
- Service Connector Hub (via _Audit Log Group)
Best suited for real-time, event-driven pipelines. Forwarding logs to Streaming enables real-time processing, while Object Storage is ideal for long-term archival, compliance, or offline analytics.
- OCI Logging – Saved Search & Dashboards
Ideal for visualization and ongoing monitoring. Dashboards provide actionable insights for auditors, administrators, and security teams without needing to write queries repeatedly.
- OCI Audit REST API via Middleware (e.g., OIC)
Seamless integration with external systems or workflows. Using REST with OCI Signature ensures secure, controlled access and can be embedded in automation pipelines or low-code environments.
We will demonstrate how OCI Events can be extracted with one use case – Methods and ways to extract Session Information using OCI Audit and Integrate into external systems
Align the choice of method with your organization’s operational model, tooling maturity, and compliance requirements.
References:
- OCI Audit
- OCI Events
- OCI Service Connector
- OCI Logging
- OCI CLI
- OCI Dashboard
- OCI SDK
- OCI Audit API
- Manage Oracle Cloud Infrastructure REST APIs Programmatically using Shell and Java Code
- Export OCI Audit Logs in CSV format for a custom time range
- Implement multicloud security using OCI Audit to capture events from OCI Identity and Access Management
- Generate Identity and Access Management Reports from Oracle Cloud Infrastructure Audit
