In the cloud, efficient traffic management is crucial for ensuring security, performance and cost-effectiveness. OCI offers network security controls through Security Lists, which function like basic firewall rules and Network Security Groups (NSGs), which provide more advanced options. Together, they play vital roles in managing your Network Security. One common challenge many customers face is identifying essential traffic and ensuring that only legitimate traffic is permitted.
In this blog series, I will explore how you can use OCI services to build traffic context and apply techniques to Identify unwanted open ports in your Network Security Controls. The diagram below provides an overview of the solution.
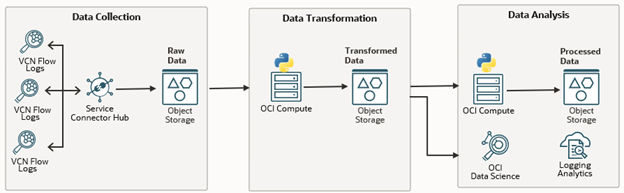
This introductory blog provides a high-level overview of the solution, which is comprised of three main steps.
- Data Collection: Gathering flow log data to understand baseline traffic patterns.
- Data Transformation: Enhancing flow logs to provide deeper insights.
- Data Analysis: Using enriched data for traffic analysis and security list optimization.
I will explore each one of these steps in detail in the following sub-posts.
Part 1: Data Collection – Gathering and Storing VCN Flow Logs
Flow logs are essential for understanding the types of traffic moving through your VCN subnets. By capturing this traffic data, you can see which IP addresses and ports are involved in the communication with your network. The first step is to collect and store this data for further enhancement and analysis.
In the upcoming blog post, we will cover.
- How to set up VCN Flow Logs to capture data within your subnets.
- Configuring Service Connector Hub to automatically route flow logs into OCI Object Storage for further processing.
- The value of flow logs in providing a high-level overview of traffic patterns.
Part 2: Data Transformation – Enhancing Flow Logs for Deeper Traffic Insights
Raw flow logs give us foundational traffic data, but they don’t provide the complete context required for in-depth analysis. To optimize your security lists and conduct analysis, we need to enhance the logs by adding critical information such as:
-
Traffic Direction: Is the traffic inbound (ingress) or outbound (egress)? Is it internal to the VCN or crossing subnet boundaries?
-
Protocol & Ports: Identifying specific protocols and ports involved in the traffic flows.
-
Correlating with Security Lists: Understanding which traffic is allowed or blocked by the security lists.
This transformation enriches the logs with necessary fields, providing insights into not just what traffic is occurring, but why and how it’s interacting with your network setup.
Part 3: Data Analysis – Applying Insights to Optimize Traffic
Once the flow log data has been enhanced, the next step is to analyze the traffic patterns in detail. We can now use this enriched data to:
-
Optimize Security Lists: Identify essential traffic patterns and minimize unnecessary traffic by tightening security list rules.
-
Machine Learning for Traffic Prediction: Leverage OCI Data Science to run machine learning models on your traffic data, detect anomalies, and anticipate security risks.
-
Visualizing Traffic Insights: Use tools such as Oracle Analytics Cloud to create reports and dashboards that provide a real-time view of traffic, allowing you to make informed decisions about which traffic should be allowed in the future.
Stay tuned for the detailed posts, where I will share best practices and code snippets for optimizing your network traffic.
